Rule latency thresholding measures elapsed time, not just
processing time, in order to more accurately reflect the actual time required
for the rule to process a packet. However, latency thresholding is a
software-based latency implementation that does not enforce strict timing.
The trade-off for the performance and latency benefits derived from latency thresholding is that uninspected packets could
contain attacks. A timer measures the processing time each time a packet is processed against a group of rules. Any time
the rule processing time exceeds a specified rule latency threshold, the system increments a counter. If the number of consecutive
threshold violations reaches a specified number, the system takes the following actions:
-
suspends the rules for the specified period
-
triggers an event indicating the rules have been suspended
-
re-enables the rules when the suspension expires
-
triggers an event indicating the rules have been re-enabled
The system zeroes the counter when the group of rules has been
suspended, or when rule violations are not consecutive. Permitting some
consecutive violations before suspending rules lets you ignore occasional rule
violations that might have negligible impact on performance and focus instead
on the more significant impact of rules that repeatedly exceed the rule latency
threshold.
The following example shows five consecutive rule processing
times that do not result in rule suspension.
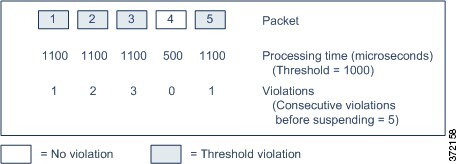
In the above example, the time required to process each of the
first three packets violates the rule latency threshold of 1000 microseconds,
and the violations counter increments with each violation. Processing of the
fourth packet does not violate the threshold, and the violations counter resets
to zero. The fifth packet violates the threshold and the violations counter
restarts at one.
The following example shows five consecutive rule processing
times that do result in rule suspension.
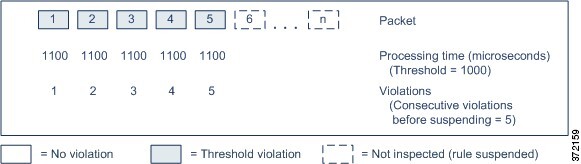
In the second example, the time required to process each of the
five packets violates the rule latency threshold of 1000 microseconds. The
group of rules is suspended because the rule processing time of 1100
microseconds for each packet violates the threshold of 1000 microseconds for
the specified five consecutive violations. Any subsequent packets, represented
in the figure as packets 6 through n, are not examined against suspended rules
until the suspension expires. If more packets occur after the rules are
re-enabled, the violations counter begins again at zero.
Rule latency thresholding has no effect on intrusion events
triggered by the rules processing the packet. A rule triggers an event for any
intrusion detected in the packet, regardless of whether the rule processing
time exceeds the threshold. If the rule detecting the intrusion is a drop rule
in an inline deployment, the packet is dropped. When a drop rule detects an
intrusion in a packet that results in the rule being suspended, the drop rule
triggers an intrusion event, the packet is dropped, and that rule and all
related rules are suspended.

Note
|
Packets are not evaluated against suspended rules. A suspended
rule that would have triggered an event cannot trigger that event and, for drop
rules, cannot drop the packet.
|
Rule latency thresholding can improve system performance in both
passive and inline deployments, and can reduce latency in inline deployments,
by suspending rules that take the most time to process packets. Packets are not
evaluated again against suspended rules until a configurable time expires,
giving the overloaded device time to recover. These performance benefits might
occur when, for example:
-
hastily written, largely untested rules require an excessive
amount of processing time
-
a period of poor network performance, such as when someone
downloads an extremely large file, causes slow packet inspection








 Feedback
Feedback