Automated Deployment
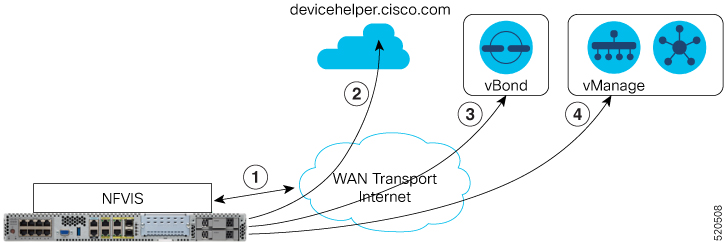
Automated deployment automates the day-zero experience of securely onboarding and deploying the NFVIS WAN Edge device, with default factory shipped settings, into the Cisco Catalyst SD-WAN network.
Automated deployment discovers the Cisco SD-WAN Validator IP address dynamically using the PnP process for the ENCS physical platform.
The following are the primary requirements to use this onboarding option:
-
The NFVIS WAN Edge device must be connected to a WAN transport that can provide a dynamic IP address, default-gateway and DNS information.
If you have a static IP address, you must configure the IP address using the following configuration example:
configure terminal bridges bridge wan-br no dhcp bridges bridge wan-br no dhcp system settings wan ip address 10.1.1.1 255.255.255.0 system settings default-gw 10.1.1.2 system settings dns-server 172.16.10.10 pnp automatic dhcp disable pnp automatic dns disable pnp automatic cco enable commit -
The NFVIS WAN Edge device can DNS resolve devicehelper.cisco.com for the Plug-and-Play Connect server.
-
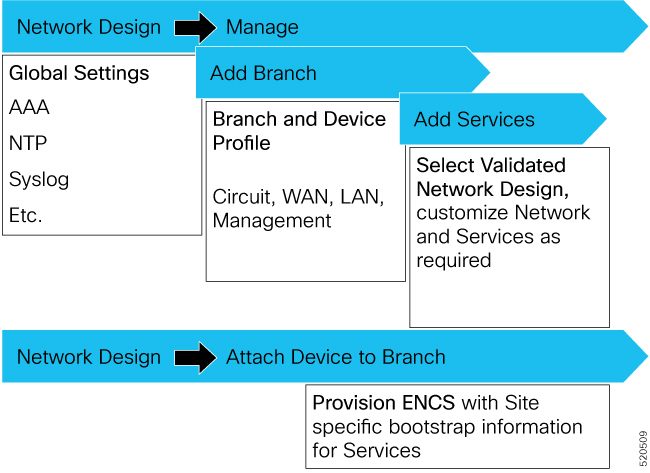
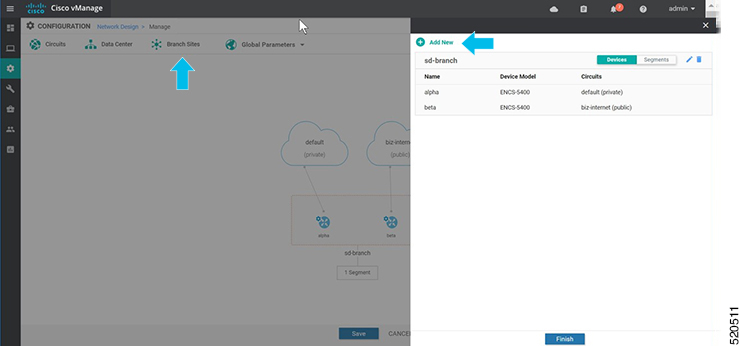
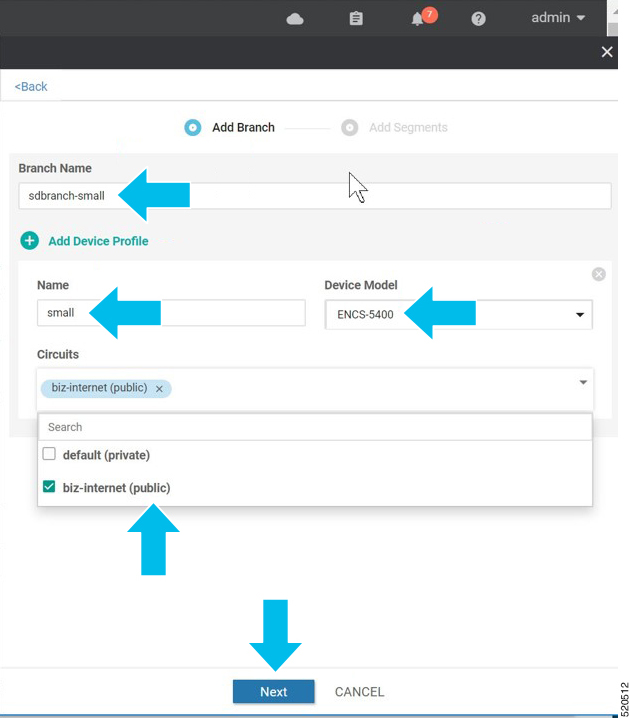
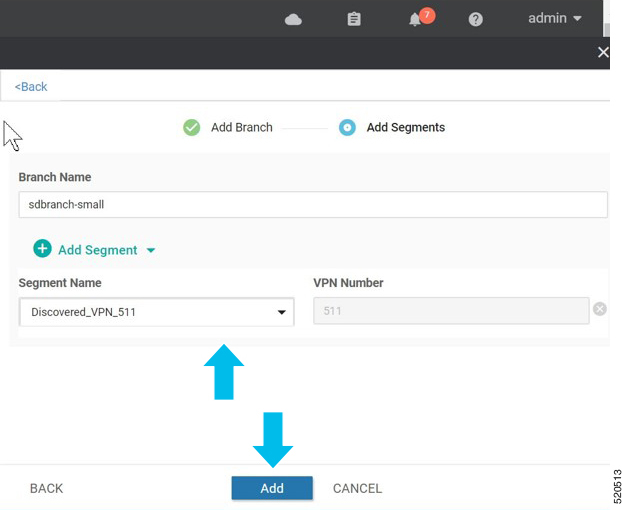
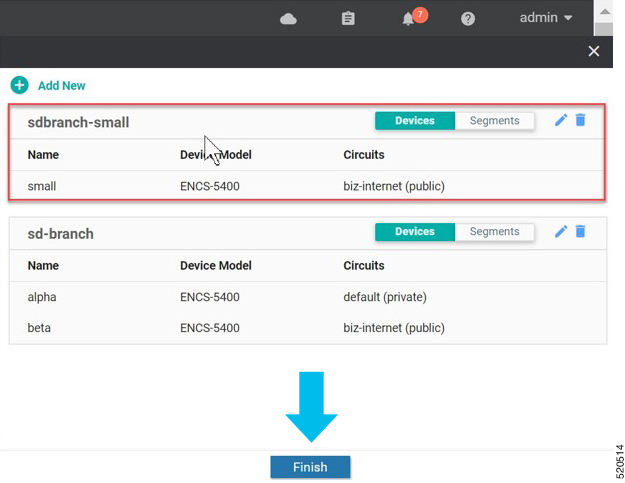
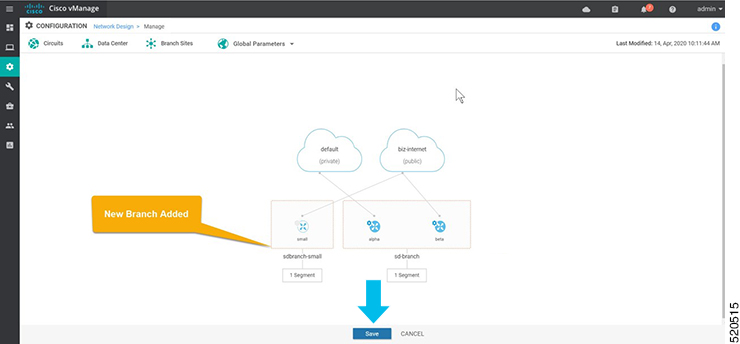
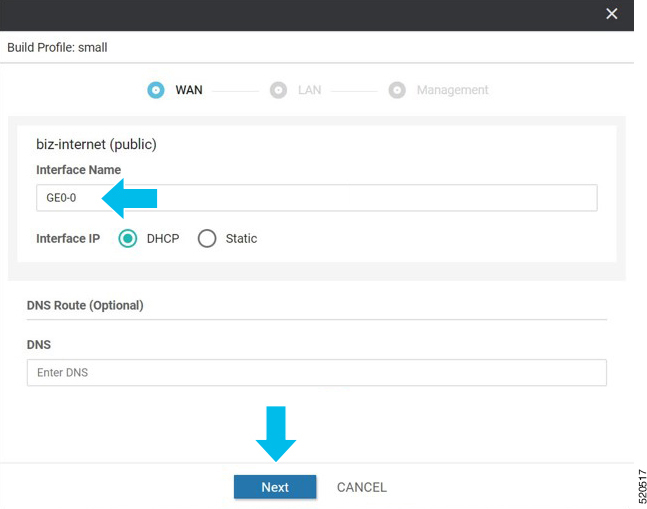
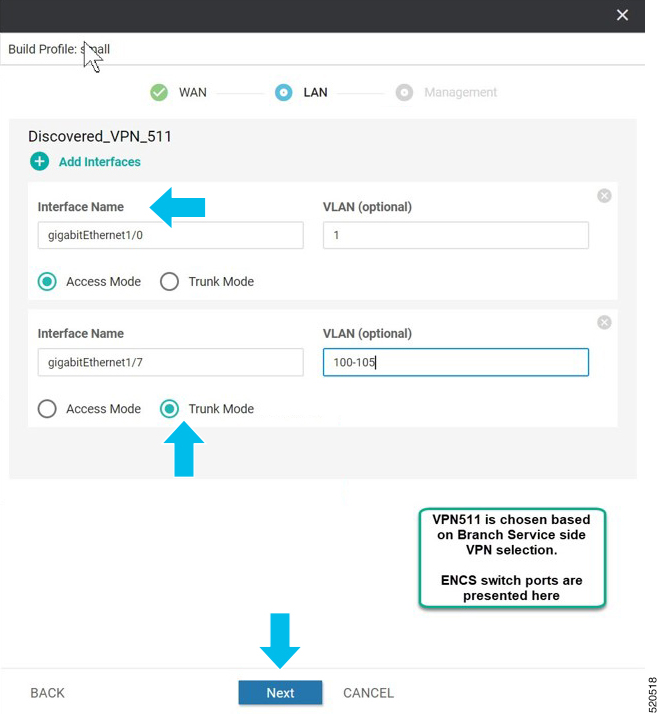
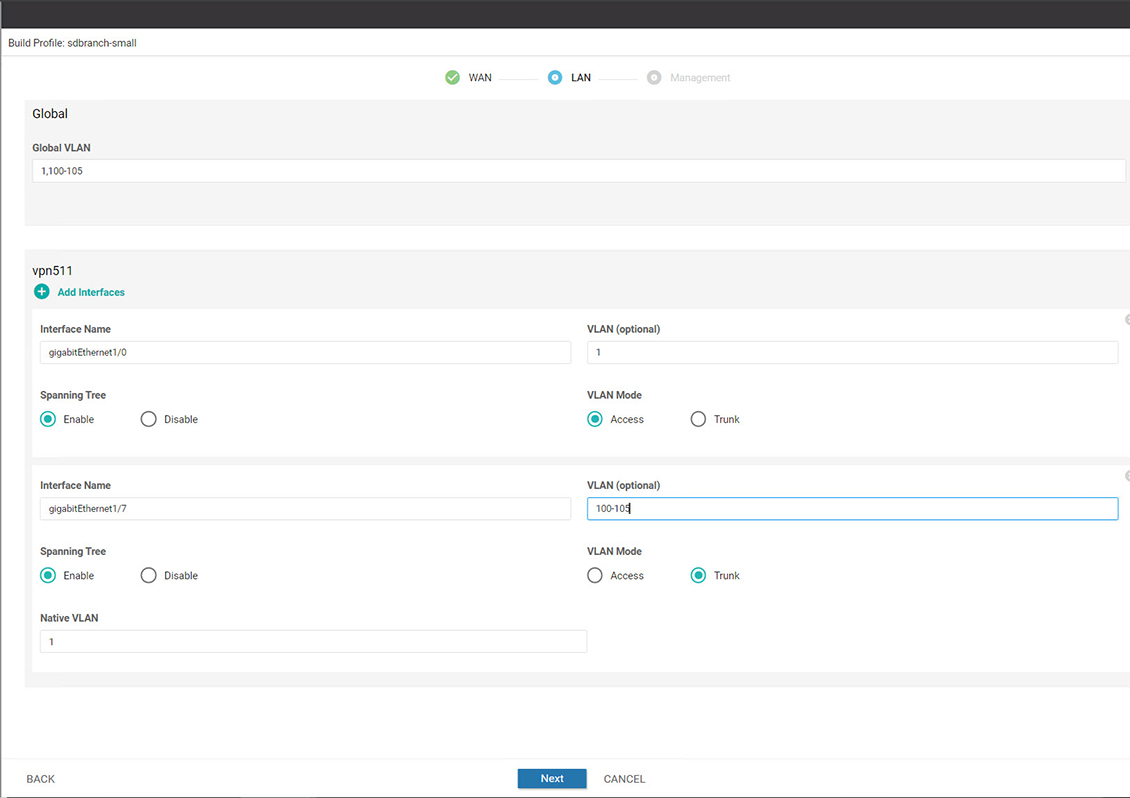
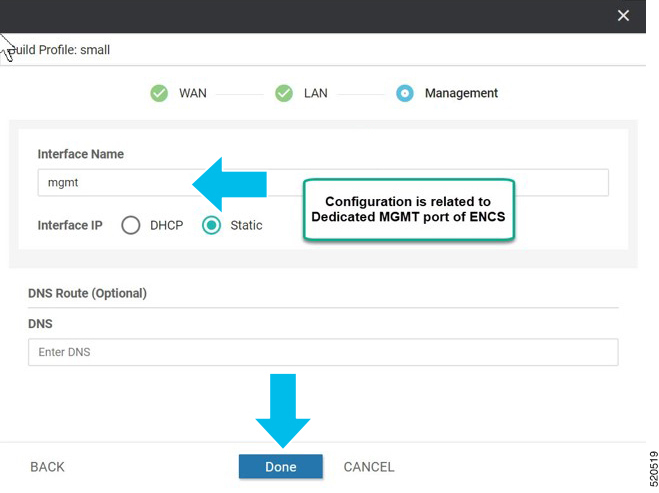
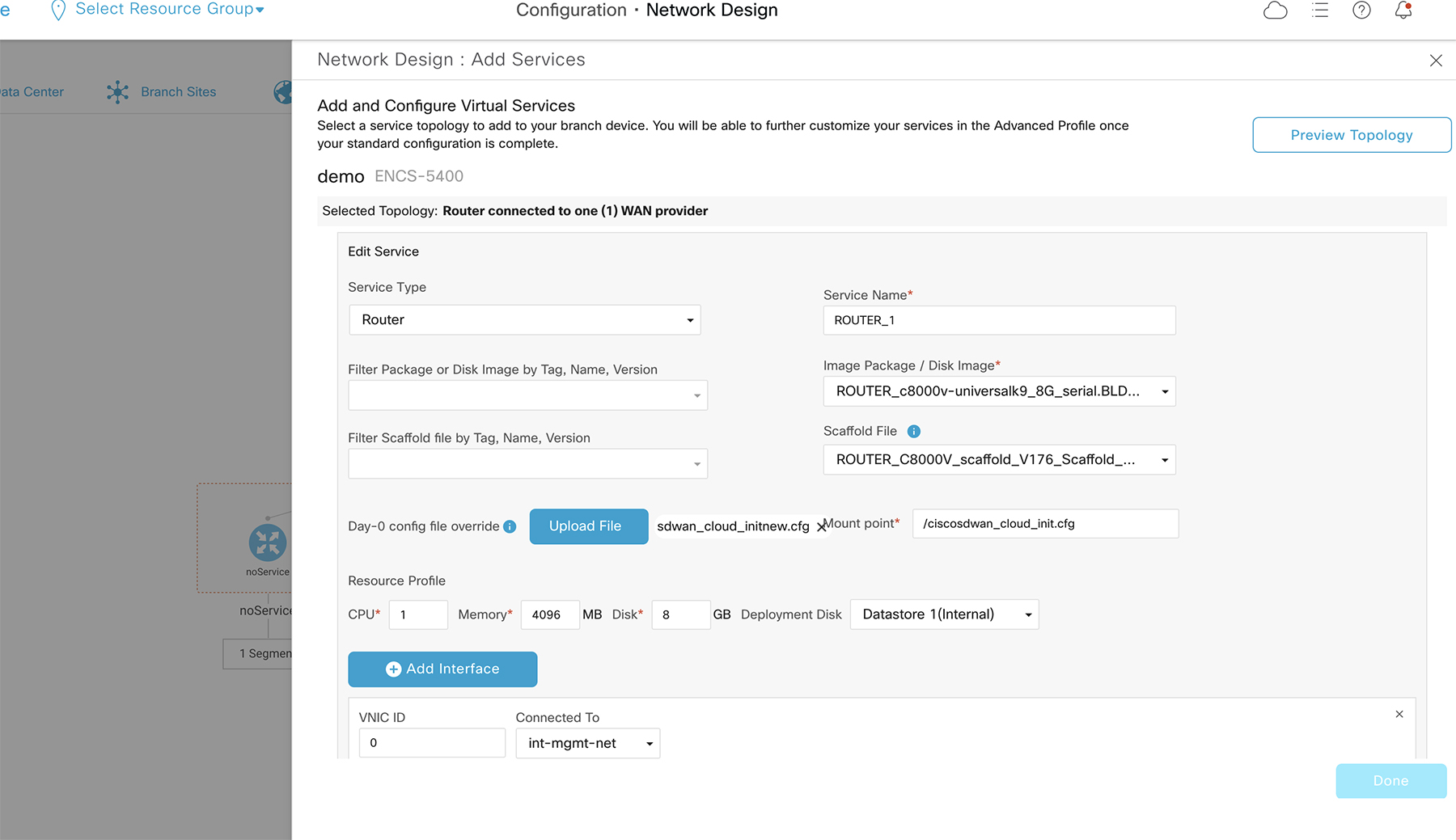
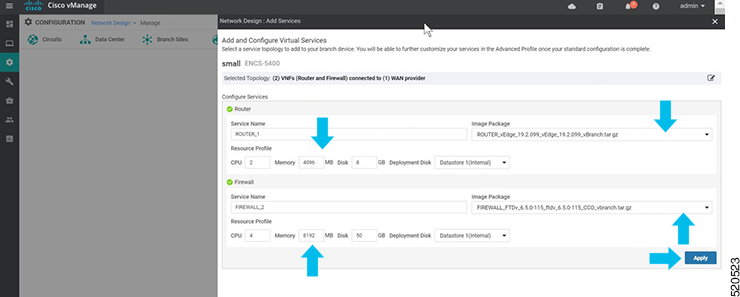
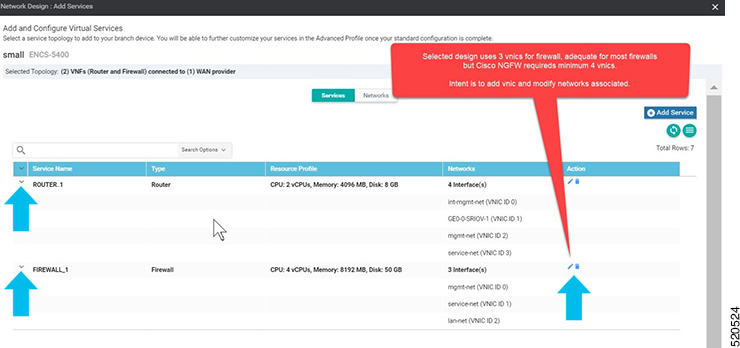
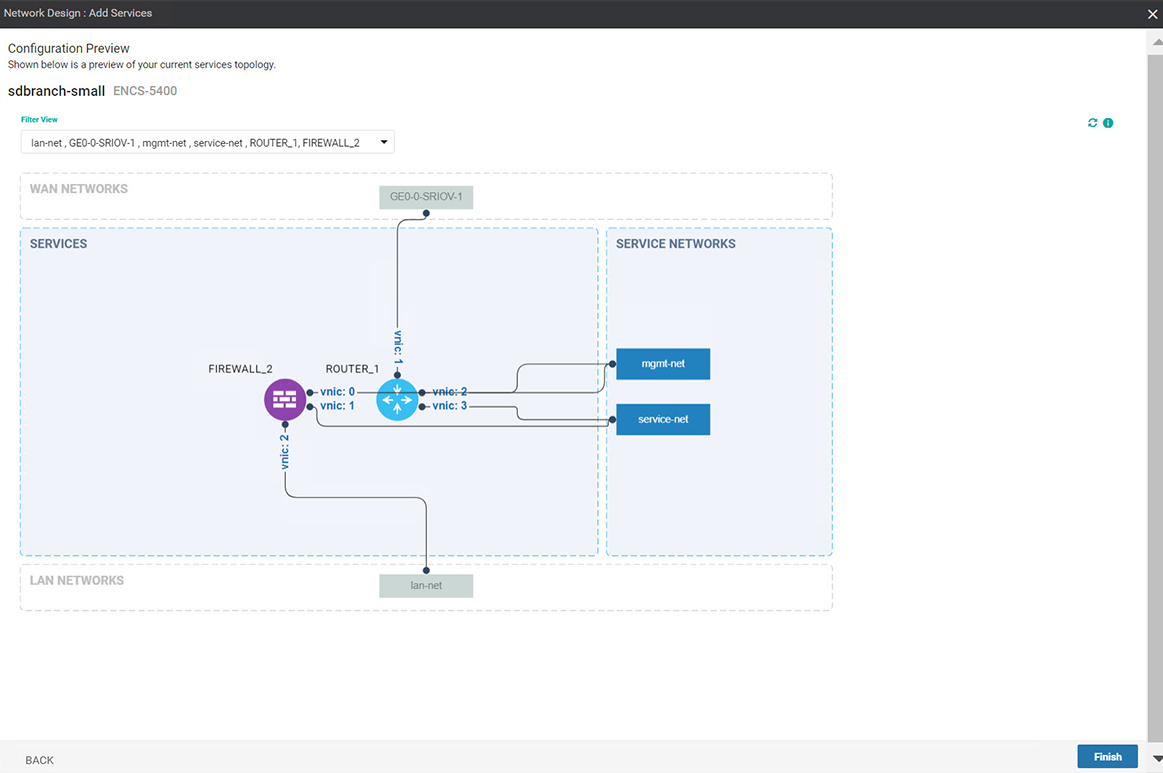
In Cisco SD-WAN Manager, a device configuration must be built and attached to the WAN Edge device to successfully onboard the device.
Use the show pnp status command to view the progress of PnP redirection to Cisco SD-WAN Validator.
Device# show pnp status
pnp status response PnP Agent is not running
server-connection
status: Success
time: 22:22:20 Dec 09
device-info
status: Success
time: 22:09:19 Dec 09
capability
status: Success
time: 22:06:17 Dec 09
redirection
status: Success
time: 22:25:46 Dec 09
certificate-install
status: Success
time: 22:51:26 Dec 09
device-auth
status: Success
time: 22:01:29 Dec 09
pnp status ip-address ""
pnp status ipv6-address ""
pnp status port ""
pnp status transport ""
pnp status cafile ""
pnp status created_by user
pnp status dhcp_opt43 0
pnp status dns_discovery 0
pnp status cco_discovery 0
pnp status dhcp-ipv6 0
pnp status dns-ipv6 0
pnp status cco-ipv6 0
pnp status timeout 0
In case of any failure, you can use the pnp action command stop , pnp action command start or pnp action command restart command to start, stop or restart the process.

 Feedback
Feedback