Feature Information for VxLAN Static Routing
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
VxLAN Static Routing |
Cisco IOS XE Gibraltar 16.10.1 |
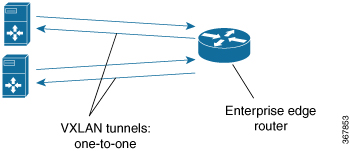
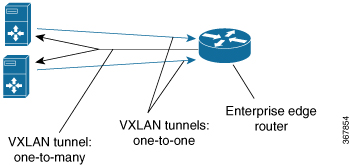
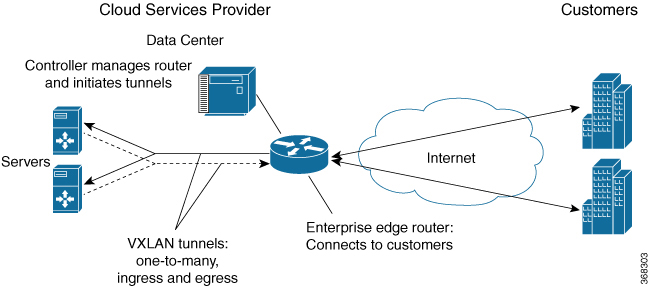
VxLAN static routing configures P2MP underlay tunnels between the router and multiple servers, and overlay routing within those tunnels. VxLAN static routing supports GPE and dummy-L2 P2MP tunnels. The prefix supports only IPv4. The next hop supports IPv4 and IPv6. The following commands were modified or added by this feature: vxlan route-profile , show vxlan route-profile all, show vxlan static-route, show vxlan static-route next-hop bind-label. |
|
VxLAN Static Routing |
Cisco IOS XE Gibraltar 16.11.1 |
Added point-to-many point “ingress” tunnels from multiple servers to the router. Added ability to specify a range of numbers for naming the tunnels, such as beginning with Tunnel100 and ending with Tunnel1000. The number is incremented by 1 for each new tunnel. Added show commands that provide packet/byte statistics. |
|
IPv6 Prefix for VxLAN Static Route |
Cisco IOS XE Gibraltar 16.12.x |
The VxLAN tunnels that operate at more than 10 gbps provide different types of encapsulations- IPv4-over-IPv4, IPv4-over-IPv6, IPv6-over-IPv4, and IPv6-over-IPv6. |
|
VNET/VNI VRF Policing and Accounting |
Cisco IOS XE Amsterdam 17.1 |
Added information on VNET/VNI per-vrf policing and accounting. Added the following commands:
|
|
Ingress and Egress Accounting MIB |
Cisco IOS XE Amsterdam 17.2 |
newly added per VNI/VNET per VRF ingress and engress accounting MIB allows the user to access the counts by SNMP |


 Feedback
Feedback