Overview
With the Cisco Secure Firewall Management Center (FMC) Remediation Module for Cisco Secure Workload (formerly known as Tetration), when an attack on your network from an infected host is detected by the FMC, the offending host can be quarantined by a Secure Workload enforcement agent so that no further traffic is allowed to go in or out of that host. The following illustration shows the relationship between the FMC and Secure Workload when the remediation module is installed:
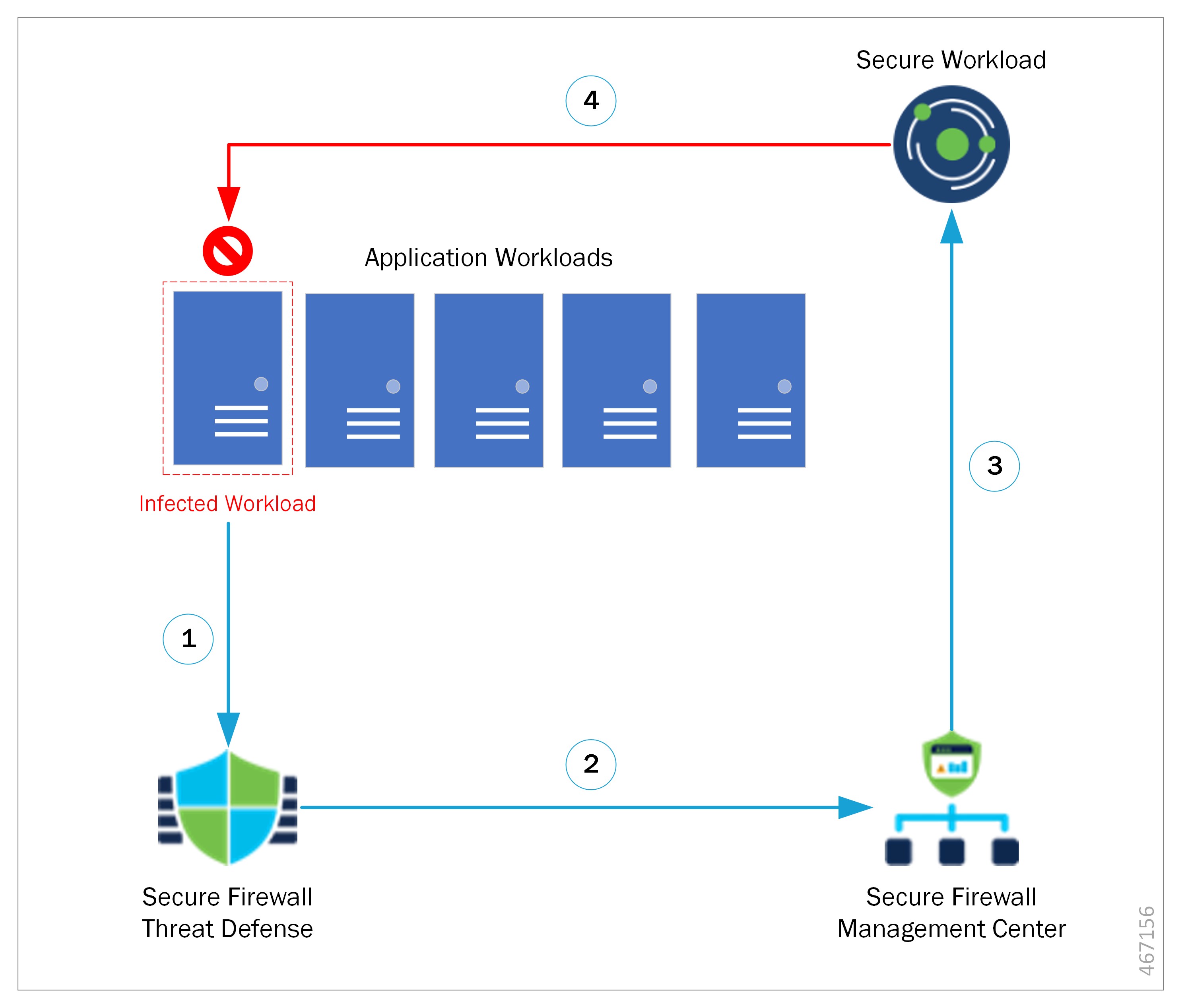
|
|
Threat Defense detects malicious traffic from infected workload. |
|
|
Threat Defense sends an event with malicious traffic details to the Management Center. |
|
|
Remediation module is triggered to quarantine infected workload. |
|
|
Secure Workload sends quarantine request to the enforcement agent on workload. |
The process of quarantining the network attack is as follows:
Procedure
| Step 1 |
An infected workload sends malicious traffic within the network. The malicious traffic is detected by Secure Firewall Threat Defense (FTD) running on a Secure Firewall device (physical or virtual). |
| Step 2 |
An event that includes information about the malicious traffic is generated and reported to the FMC managing the FTD. |
| Step 3 |
The action triggers the remediation module on the FMC to use the Secure Workload REST API to request that Secure Workload quarantine the infected workload. |
| Step 4 |
Secure Workload quickly contains the infected workload by sending a quarantine request to the enforcement agent on the infected workload. |




 Feedback
Feedback