Configure
To configure the remediation module installed on the FMC, complete the following procedure:
Procedure
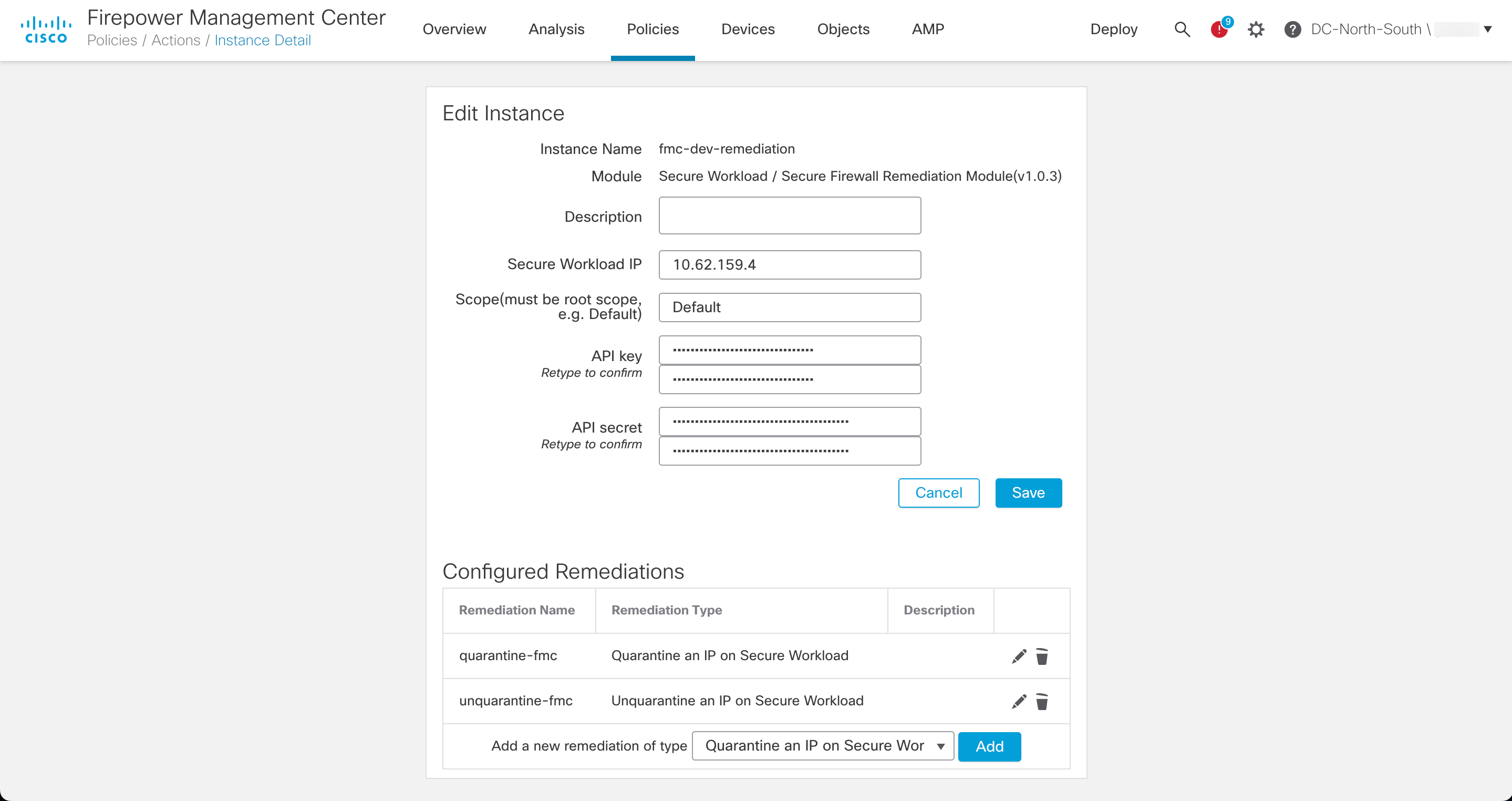
| Step 1 |
In FMC, create an instance of the remediation module for each Secure Workload cluster in your network:
|
||
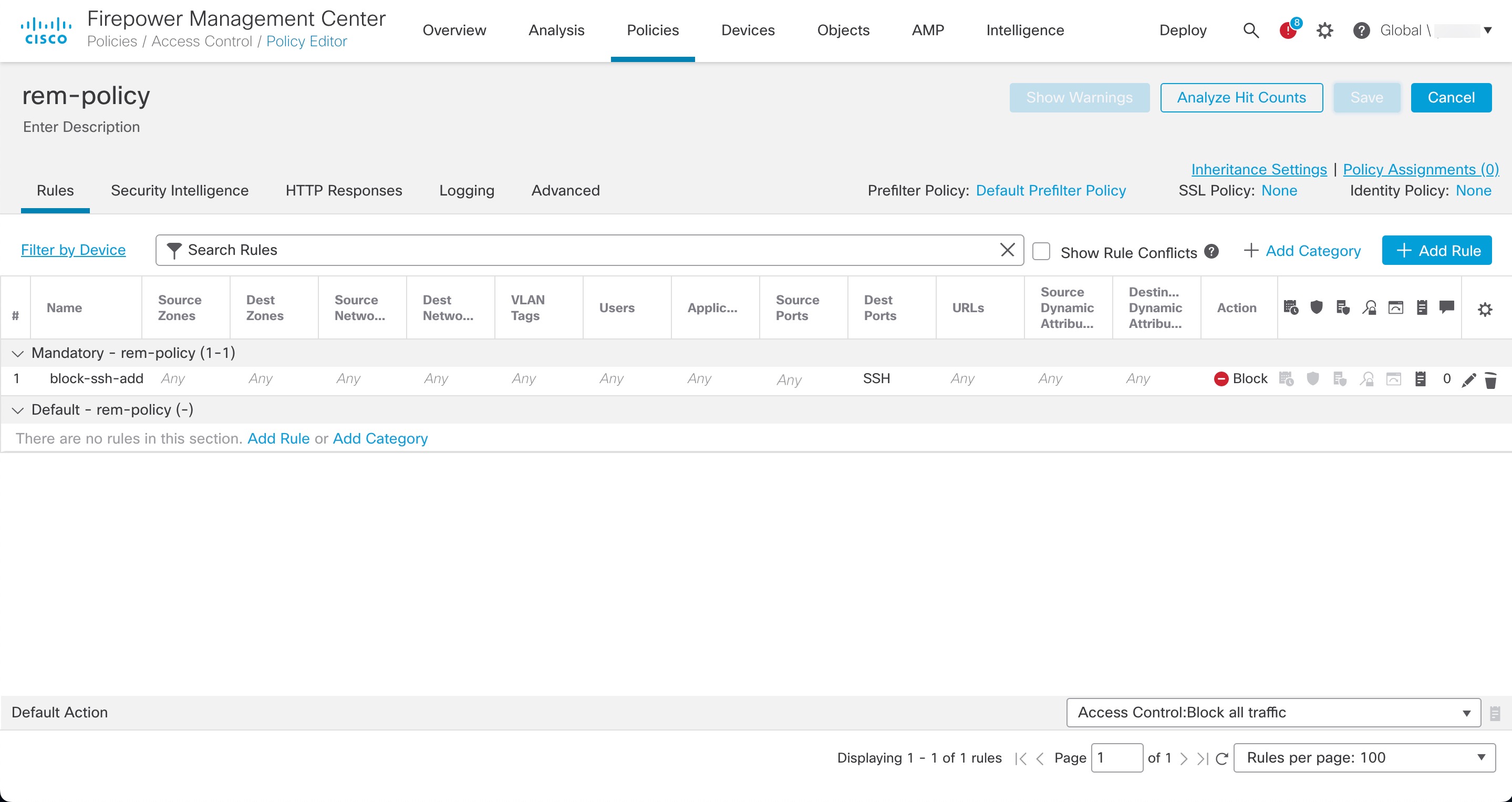
| Step 2 |
Configure an access control policy (in this example, rem-policy):
 |
||
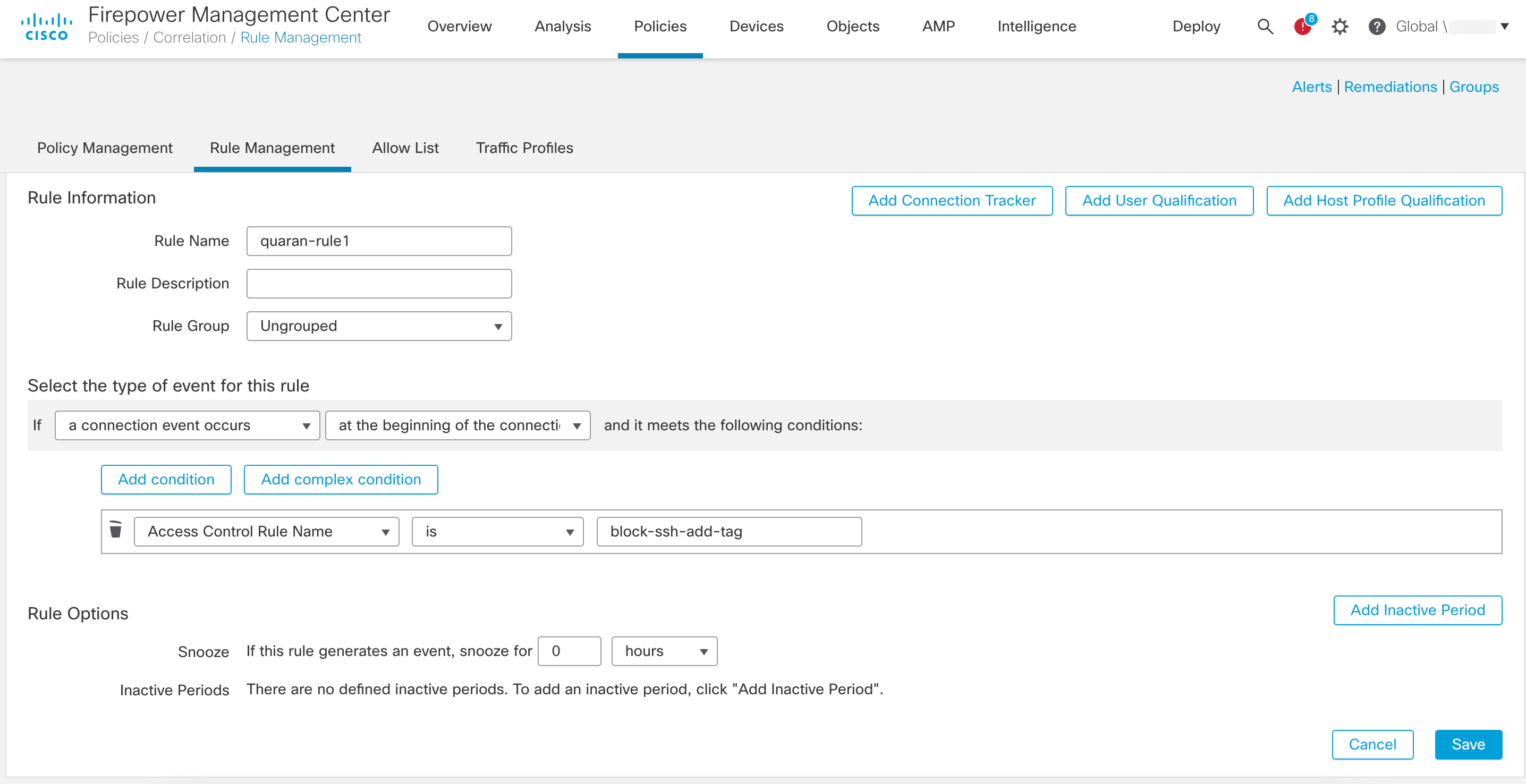
| Step 3 |
Configure a correlation rule:
|
||
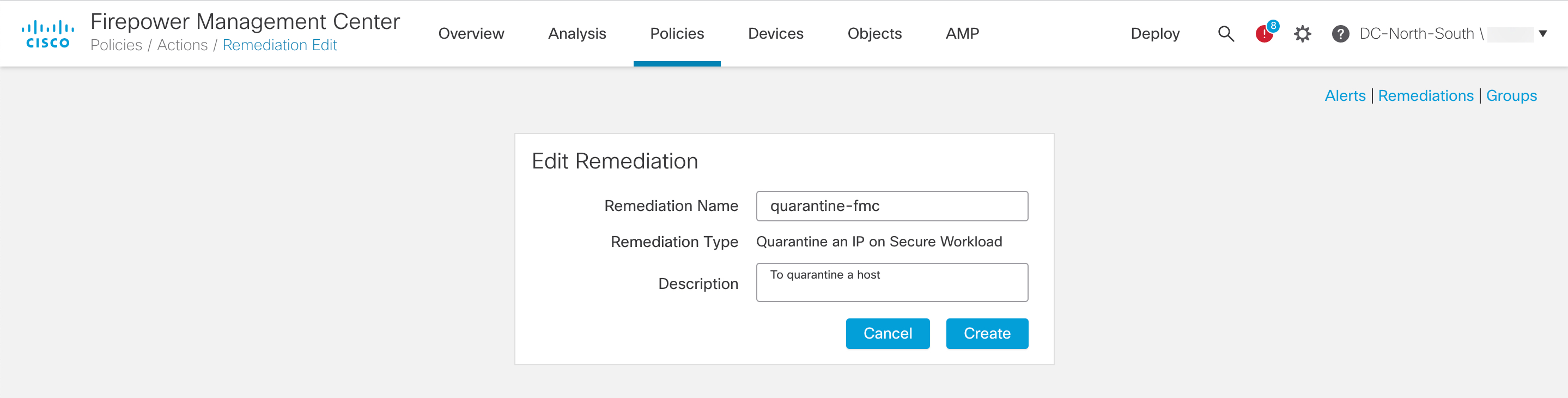
| Step 4 |
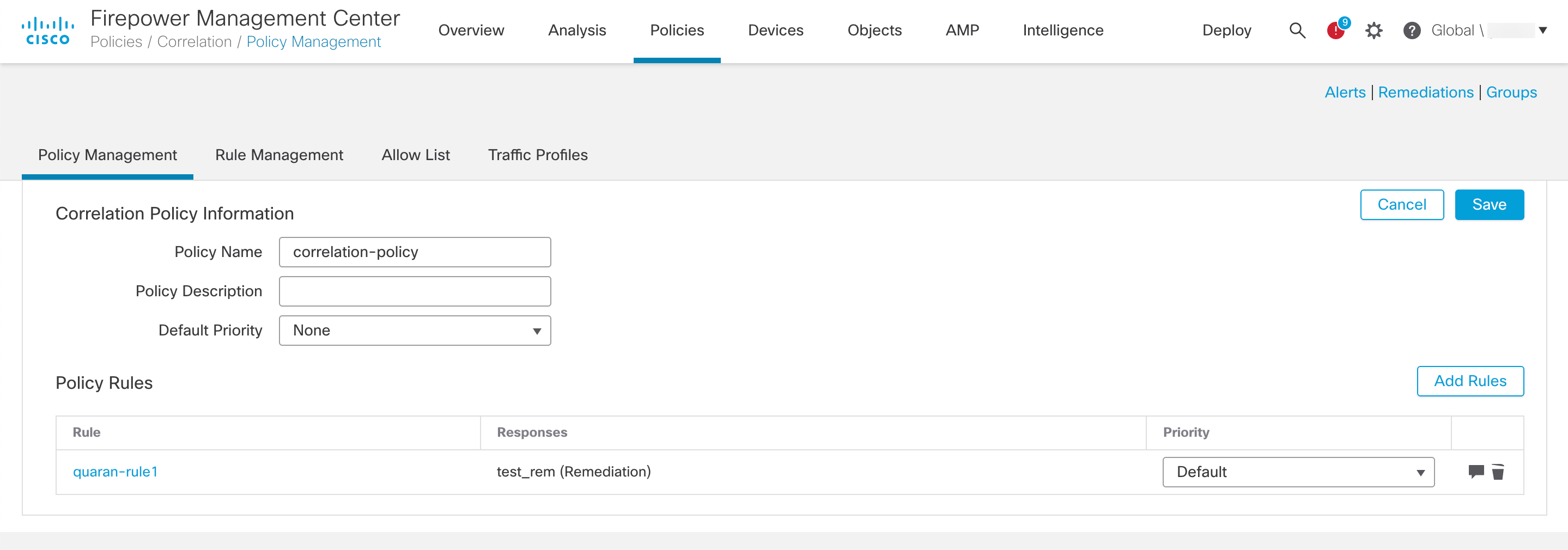
Associate the instance of the remediation module as a response with a correlation rule:
|
 Feedback
Feedback