Layer 2 VPN
|
Feature Name |
Release Information |
Description |
|---|---|---|
|
Layer 2 (L2) VPN |
Cisco IOS XE Catalyst SD-WAN Release 17.14.1a Cisco Catalyst SD-WAN Control Components Release 20.14.x |
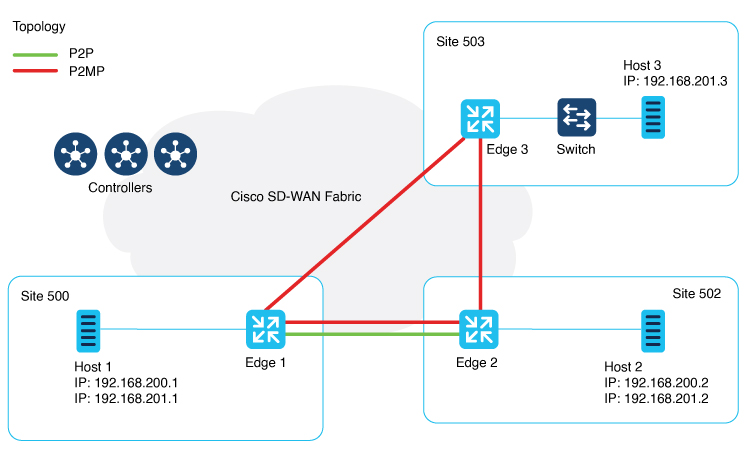
The feature adds Layer 2 VPN support on the Cisco Catalyst SD-WAN overlay network. It allows you to configure Layer 2 point-to-point and point-to-multipoint connections within the Cisco Catalyst SD-WAN fabric. |
|
Layer 2 (L2) VPN Multihoming and Hub-and-Spoke Support |
Cisco IOS XE Catalyst SD-WAN Release 17.15.1a Cisco Catalyst SD-WAN Manager Release 20.15.x |
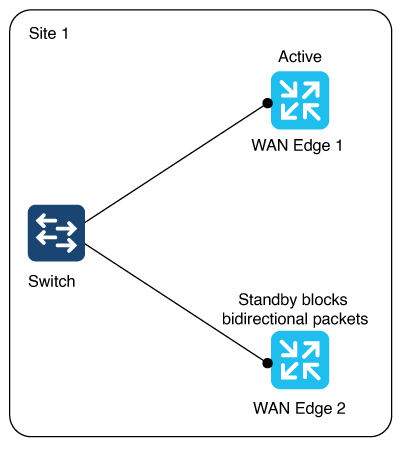
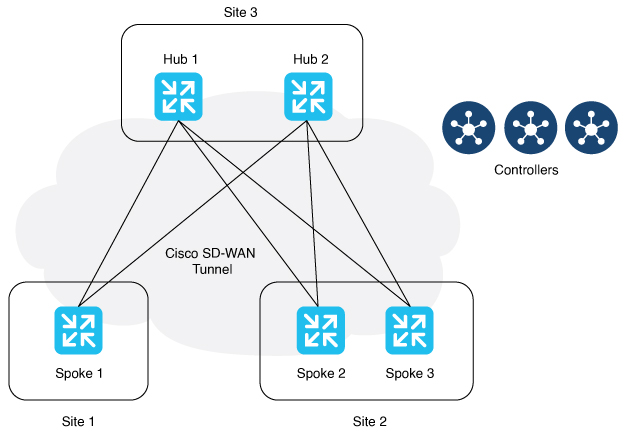
With this feature, you can configure Layer 2 VPN on multiple devices on the same site in an active-standby configuration. This feature also enables Layer 2 connections using an indirect path, such as a hub, for point-to-multipoint connections within the Cisco Catalyst SD-WAN fabric. |

 Feedback
Feedback