Information About Cisco Catalyst SD-WAN Firewall High Availability
High availability ensures the continuous operation of essential services such as Zone Based Firewall (ZBF) and Network Address Translation (NAT). High availability provides a seamless switchover of these services in the event of a device failure.
In a high-availability environment, firewall and NAT functionalities synchronize their operational states between two Cisco IOS XE Catalyst SD-WAN devices through redundancy groups. A redundancy group is a pairing of two Cisco IOS XE Catalyst SD-WAN devices where one is designated as the active device and the other as the standby. VPNs are associated with these redundancy groups. Cisco Catalyst SD-WAN supports two redundancy groups, allowing one set of traffic to be active on one device and another set of traffic to be active on the peer device.
The synchronization of stateful features such as firewall sessions and NAT mappings from the active device to the standby device ensures that the standby device has all the necessary information to maintain service continuity if the active device fails. This seamless transition prevents service disruption and ensures high availability.
 Note |
While high availability aims to provide seamless operation, certain features may not transition traffic as smoothly during failover scenarios. Support for Application Layer Gateway (ALG) and Application Inspection and Control (AIC) is on a best-effort basis, and the traffic switchover might not be seamless. Similarly, traffic flows involving TCP/TLS proxy (Unified Threat Defense) and Network-Based Application Recognition (NBAR)/Deep Packet Inspection (DPI) may experience disruptions during failover. |
Redundancy Groups
A redundancy group is a pairing of devices in a high-availability configuration in Cisco Catalyst SD-WAN that ensures continuous service. The devices in the redundancy group can operate either in an active or standby state. VPNs are associated with the redundancy groups, and the VPN traffic is processed by the active device in the redundancy group. Cisco Catalyst SD-WAN supports a maximum of two redundancy groups.
In an active-active configuration, both devices in the two redundancy groups simultaneously process traffic, providing load balancing and redundancy. In this setup, VPNs are distributed across two Cisco IOS XE Catalyst SD-WAN devices, resulting in the creation of two redundancy groups. Redundancy group configuration should have the preempt option configured for active-active (two redundancy groups) mode.
In an active-standby configuration, all the VPNs are assigned to a single Cisco IOS XE Catalyst SD-WAN device, creating one redundancy group. For active-standby (only one redundancy group configured) mode, the preempt option is not recommended
By correctly configuring redundancy groups, you can ensure high availability and continuous service in your Cisco Catalyst SD-WAN environment. VPNs that are not associated with a redundancy group do not have their traffic protected by high availability.
VPN Associations
You can associate VPNs with redundancy groups in Cisco Catalyst SD-WAN. To do this, you must manually assign each VPN to its redundancy group. If you configure route leaking between VPNs, it is contained within the same redundancy groups, and this is enforced by Cisco SD-WAN Manager for proper traffic management and high availability.
Redundancy Group Init Roles
Init roles are used while configuring redundancy groups on Cisco IOS XE Catalyst SD-WAN devices. These roles determine the initial state of a device within a redundancy group, specifying whether it should start as the active or standby device. Proper configuration of init roles ensures that one device takes on the responsibility of handling traffic (active) while the other remains in a ready state (standby) to take over in case of a failure.
The init-role active within redundancy groups helps you to select between active and standby options when both redundancy groups have equal priority. You must configure this role appropriately for each redundancy group. Designate one device as init-role active, and configure the other as init-role standby.
When preempt is set, the redundancy group with init-role active become actives if the redundancy group priorities of the peer devices are equal. This allows for automatic switchover to their initial state after faults have been addressed.
Implicit and Explicit Tracking
Redundancy groups use object tracking to determine their state. Examples of this include Cisco Catalyst SD-WAN session tracking, NAT endpoint tracking, and interface state tracking.
The redundancy groups can also be configured to create an object. Virtual Router Redundancy Protocol (VRRP) tracks the redundancy group object so that it can follow the redundancy group state. For example, if the redundancy group state is active, the VRRP state is primary; if the redundancy group state is standby, the VRRP state is backup.
State Synchronization
There are two types of state synchronization between the active and standby devices:
-
Periodic Sync: This occurs as soon as a session is established. For example, when a NAT entry is created or a firewall session is established, the state is immediately synchronized. Similarly, when a session is deleted, the corresponding state is also removed.
-
Bulk Sync: This occurs whenever the high availability state is re-initialized, or when a Cisco IOS XE Catalyst SD-WAN device is reloaded or comes back online. During this process, the standby device requests the active device to push the sessions and translations to it. After this synchronization is complete, the active device issues a bulk sync done notification to the standby device. At this point, standby device transitions to hot standby. When the bulk sync is fully completed, the standby device is considered to be in a hot standby state.
Figure 1. State Synchronization 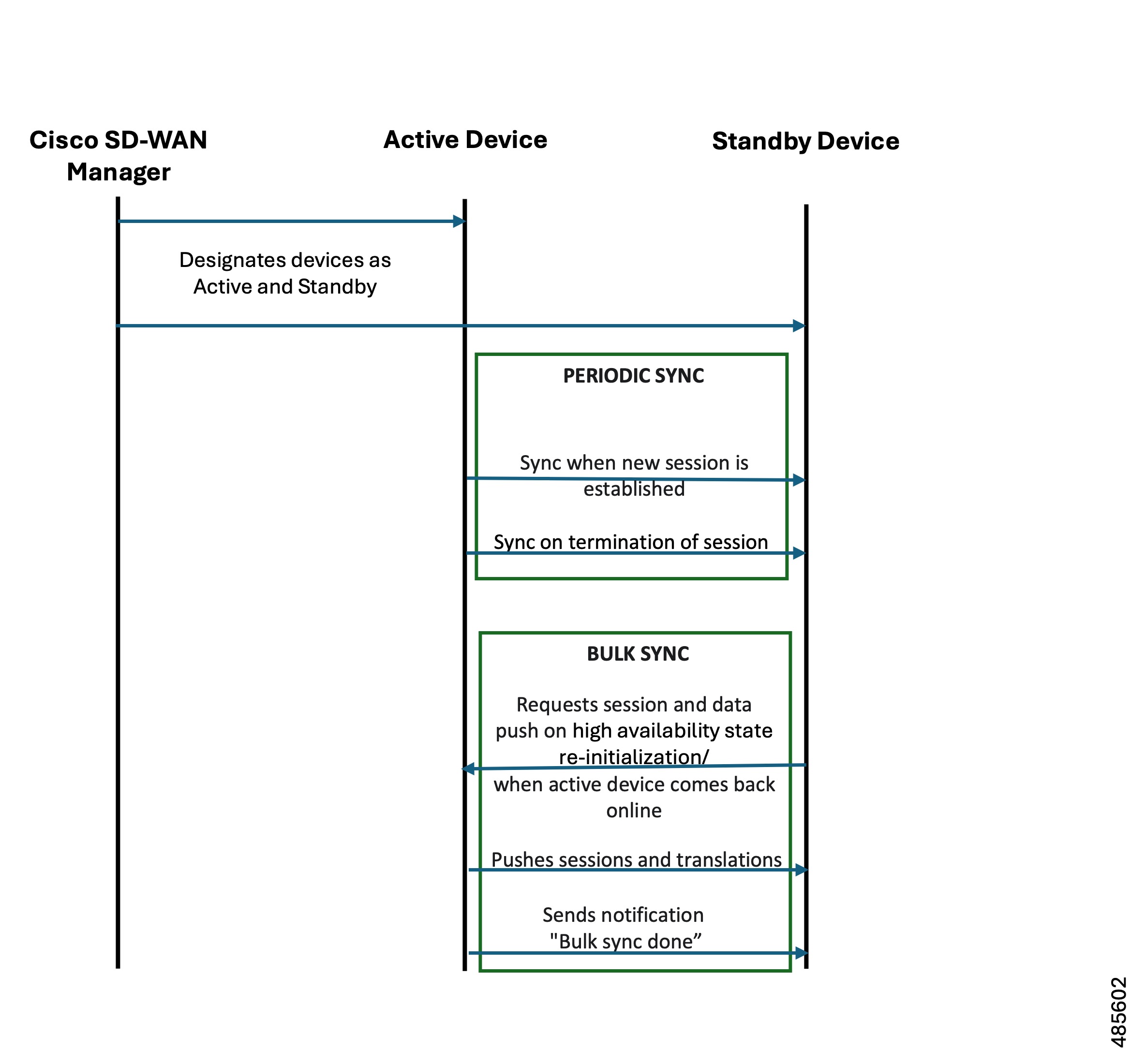
Path Optimization
Path optimization in Cisco Catalyst SD-WAN ensures that WAN traffic is always directed to the active Cisco IOS XE Catalyst SD-WAN device, thereby avoiding traffic redirection, also known as peer diversion, and ensuring efficient traffic flow. When you enable path optimization, WAN traffic consistently flows to the active Cisco IOS XE Catalyst SD-WAN device, eliminating the need for peer diversion, where traffic would otherwise be redirected from the standby device to the active device.
For LAN traffic, you can direct traffic to the active Cisco IOS XE Catalyst SD-WAN device using Interior Gateway Protocol (IGP) rewrite or Virtual Router Redundancy Protocol (VRRP) following the redundancy group.
For WAN traffic, path optimization directs the traffic to the active device, preventing it from reaching the standby device.
IGP Rewrite
IGP Rewrite is a technique used to ensure that LAN-side traffic is directed to the active Cisco IOS XE Catalyst SD-WAN device within a redundancy group. Interior Gateway Protocols (IGPs) such as Open Shortest Path First (OSPF) or Border Gateway Protocol (BGP) dynamically route traffic within a network.
By adjusting the IGP metrics or routes, you can configure the network to prefer the active Cisco IOS XE Catalyst SD-WAN device for routing LAN traffic. This ensures that the active device handles the majority of the traffic, providing efficient traffic flow and minimizing the chances of traffic being redirected to the standby device.
VRRP Following Redundancy Group State
In the context of a redundancy group, you can configure VRRP to follow the state of the redundancy group. This means that the VRRP primary role is assigned to the Cisco IOS XE Catalyst SD-WAN device with the active redundancy group, ensuring that LAN-side traffic is directed to the active redundancy group. If the active redundancy group fails, VRRP reassigns the primary role to the device with the new active redundancy group, ensuring continuous service.
You can assign only one VPN to an interface, and the VRRP for that interface must follow the redundancy group associated with the same VPN. You can configure both VRRP and the redundancy group on the same Cisco IOS XE Catalyst SD-WAN device.
IGP Rewrite and VRRP following the redundancy group state are techniques used to attract LAN-side traffic to the device with the active redundancy group. By using these techniques, you can ensure that LAN-side traffic is consistently directed to the active redundancy group associated with the Cisco IOS XE Catalyst SD-WAN device. Combined with path optimization for WAN traffic, this ensures that all traffic is efficiently routed to the active redundancy group associated with the Cisco IOS XE Catalyst SD-WAN device until it fails. In such a setup, the states of firewall and NAT services are continuously synchronized between the two Cisco IOS XE Catalyst SD-WAN devices. In the event of a failover, the standby redundancy group associated with the Cisco IOS XE Catalyst SD-WAN device takes over, and these services will continue to run seamlessly, maintaining high availability and continuous service.
In this sample topology for path optimization, VPN traffic flows through the active device, SD-WAN Edge 1, in both directions—from LAN to WAN and from WAN to LAN.
SD-WAN Edge 1, as the active device, modifies the routing parameters for LAN traffic and the OMP affinity for WAN traffic to attract traffic in both directions (LAN to WAN and WAN to LAN).
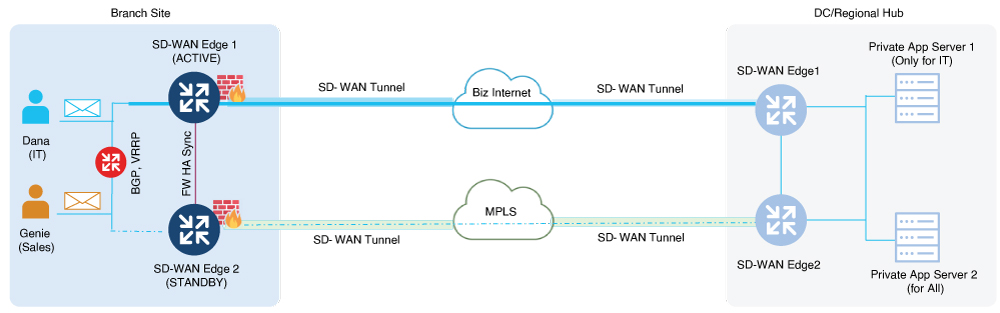
Peer Diversion
Peer diversion is a mechanism where traffic arriving on a Cisco IOS XE Catalyst SD-WAN device with an associated redundancy group in a standby state is diverted to the peer device in the redundancy group. The peer device refers to the other device in the redundancy group.
Redundancy group configuration should include the asymmetric-routing always-divert enable command when setting up high availability in a redundancy group. This option ensures that when traffic reaches the standby device, it is diverted to the active device regardless of the type of traffic.
There are two methods of Peer diversion:
-
LAN Divert
-
WAN Divert
LAN Diversion
For the LAN traffic, based on VPN-to-redundancy group mapping, if the device is in the standby state for the traffic in a specific VPN, the traffic is diverted to the active device.
WAN Diversion
For the WAN traffic, if traffic is directed to a device in a standby state, Peer diversion uses session information from Cisco Catalyst SD-WAN to identify and redirect the traffic to the active device in the redundancy group.
Peer diversion efficiently manages traffic by diverting it to the active redundancy group associated with the Cisco IOS XE Catalyst SD-WAN device when it arrives at a standby device. This mechanism is crucial for maintaining seamless traffic management and high availability in Cisco Catalyst SD-WAN environments. It ensures that features like Application Aware Routing and stateful services, such as firewall and NAT, are processed only on the active redundancy group.
VPN Homing
VPN homing is a technique used to manage and optimize the routing of VPN traffic through specific Cisco IOS XE Catalyst SD-WAN devices. This involves mapping VPNs to redundancy groups to determine which Cisco IOS XE Catalyst SD-WAN device will be active for the corresponding VPN traffic. Multiple VPNs can be mapped to a single redundancy group, allowing for flexible and efficient traffic management.
For seamless failover and consistent traffic routing, both the active and standby Cisco IOS XE Catalyst SD-WAN devices must have the same VPN to redundancy group mapping. This ensures that the network can maintain high availability and continuous service.
In this sample topology for VPN homing, two redundancy groups are configured for devices SD-WAN Edge 1 and SD-WAN Edge 2 in an active-active setup. As part of VPN homing, Service Side VPNs, VPN 1 and VPN 2, are associated with RG1, while VPN 3 and VPN 4 are associated with RG2.
As a result of this active-active setup, traffic is load-balanced across both devices, with SD-WAN Edge 1 handling traffic for VPN 1 and VPN 2, and SD-WAN Edge 2 handling traffic for VPN 3 and VPN 4. This configuration ensures efficient traffic management and high availability.
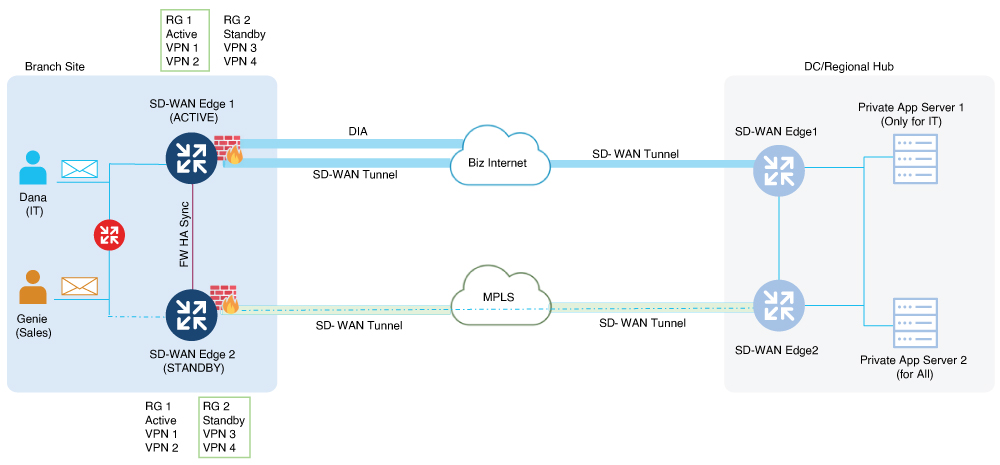
High Availability Interconnect
An interconnect is a dedicated connection between peer Cisco IOS XE Catalyst SD-WAN devices. It facilitates communication and synchronization between devices, allowing the high availability infrastructure to determine which redundancy group is active or standby. The interconnect also enables the transfer of session data to the standby redundancy group and provides a path for peer-diverted traffic.
In a high availability set up, the interconnect interface enables synchronization of services, such as Firewall and NAT, between two Cisco IOS XE Catalyst SD-WAN devices. This setup enables features to synchronize their state, such as sessions and translations, which is essential for seamless failover and high availability.
High Availability Configuration Options
When configuring the interconnect for high availability, you have the following options:
-
Single Interface: A single physical interface or a subinterface can be used as the interconnect.
-
Port Channel: A port channel can be used to provide redundancy and increased bandwidth for the interconnect.
Only a single interconnect interface may be configured. If multiple interfaces are required to meet throughput requirements, use a port channel.
On interconnect interfaces, default Quality of Service (QoS) configurations are applied to prioritize traffic. These QoS policies ensure that critical synchronization and management traffic is handled efficiently and without delay. High availability protocol traffic receives the highest precedence, followed by session management traffic, while peer divert traffic utilizes the remaining bandwidth.
Redundant Interface IDs
Redundant Interface IDs (RII) enable high-availability peer Cisco IOS XE Catalyst SD-WAN devices to be mapped and associated with each other. Cisco SD-WAN Manager automatically generates a unique RII for each interface on a Cisco IOS XE Catalyst SD-WAN device, and this RII must be replicated on the peer device. LAN and WAN interfaces must be configured with RII to ensure that each interface on one device corresponds to the redundant interface on another device. This includes configuring RII for the SD-WAN tunnel for service-side NAT.
By assigning matching RIIs to interfaces on both the active and standby Cisco IOS XE Catalyst SD-WAN devices, we logically pair the interfaces, forming a singular interface.
In a sample high availability interconnect topology, interconnect links (logical links) are set up between the active device (SD-WAN Edge 1) and the standby device (SD-WAN Edge 2). The high availability protocol uses keepalive messages to determine which device is active and which is standby. The state synchronization mechanism synchronizes the states of high availability features such as firewall and NAT between the active and standby devices. The peer diversion link ensures that traffic arriving on the standby device is diverted to the active device. The RII is essential to identify and manage of interfaces across active and standby devices.
 Note |
Interfaces that do not have an RII assigned will not support high availability. |
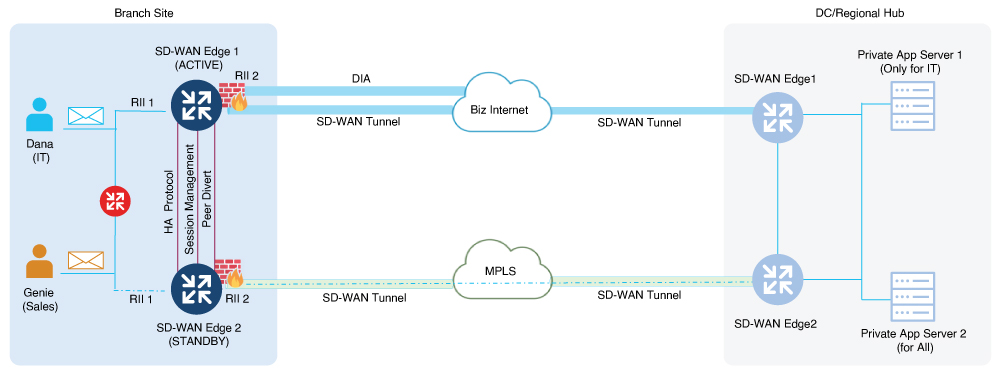
NAT Pool Assignments
In Cisco Catalyst SD-WAN, NAT pools can be associated with redundancy groups to ensure high availability and efficient traffic management.
For NAT Direct Internet Access (DIA) configuration in active-active mode, two redundancy groups are configured, and NAT pools are assigned in a round-robin manner across these groups.You can use the CLI Add-on profile to assign a specific a redundancy group to a NAT pool. The mapping of NAT pools to redundancy groups should be the same as the mapping of VPNs to redundancy groups. For NAT translations to be synchronized, NAT mapping must belong to a redundancy group.
For NAT DIA configuration in active-standby mode, only one redundancy group is configured. When you associate a redundancy group with a NAT pool, the configured redundancy group is assigned to the NAT pool.
For service-side NAT configuration, NAT pools can be assigned to a VPN using service-side NAT mapping. Cisco SD-WAN Manager ensures that the redundancy group associated with the NAT pool matches the redundancy group the VPN is mapped to in the redundancy group configuration.
For more information, see NAT Deployment Models.
NAT Deployment Models
Cisco Catalyst SD-WAN includes the following types of NAT configurations:
-
NAT DIA: Allows remote sites to route traffic directly to the internet rather than routing the traffic to a central site or data center.
-
Service-Side NAT: Allows you to configure internal NAT on data traffic traveling to and from the service hosts of the network overlay. Service-Side NAT translates data traffic of internal host addresses that match a configured centralized data policy.
NAT DIA
You can configure NAT DIA to allow direct internet access in high availability setups, ensuring continuous service and efficient traffic management. In a NAT DIA high availability configuration, policies must be configured, and NAT mapping must be associated with redundancy groups to ensure high availability.
Configure a pair of Cisco IOS XE Catalyst SD-WAN devices with a redundancy group. Both devices must be connected to the same set of hosts on the LAN side. When you configure one redundancy group, one device operates as the active device while the other remains in standby mode. You can connect the WAN interfaces of each device to the same or different internet service providers (ISPs) and place them on different subnets. Despite subnet differences, you can successfully divert stateful traffic because you configure the same RII on both interfaces. For more information about RII, see the section Redundant Interface IDs in High Availability Interconnect.
Configure the WAN interfaces of both Cisco IOS XE Catalyst SD-WAN devices with an IGP routing protocol such as Internal Border Gateway Protocol (iBGP) or OSPF to install the NAT pool subnet into the ISP router along with other routes. During a switchover, the standby router becomes active and traffic is diverted to it as the sessions were previously synchronized.
For NAT DIA, match the reduncy group ID in the NAT mapping to the VPN traffic. Multiple VPNs belonging to the same redundancy group can share the same DIA mapping. NAT mappings configured without a redundancy group ID are used by control traffic on the device, and sessions created through this mapping are not synchronized.
You can configure NAT DIA for high availablility in Cisco SD-WAN Manager using configuration groups or by using the CLI Add-On Profile. For information see, Configure NAT DIA for Cisco Catalyst SD-WAN Firewall High Availability, CLI Add-On Profile.
Service-Side NAT
A Service-Side NAT configuration is a used in high availability setups to ensure continuous service and efficient traffic management for overlay traffic.
In a service-side NAT for high availability configuration, configure policies and associate VPNs to redundancy group for high availability. In a Service-Side NAT high availability configuration set up, Cisco SD-WAN Manager checks whether a VPN is associated with any redundancy group and if NAT pools are configured as part of the VPN configuration. If the VPN is already associated with an redundancy group, the configured NAT pools for that VPN is considered for high availability. For information on configuring service-side NAT in Cisco SD-WAN Manager, see Configure Service-Side NAT.
Alarms and Notifications
Cisco SD-WAN Manager provides a way to monitor and log events related to redundancy group roles. When you navigate to in Cisco SD-WAN Manager, the page displays device-generated events, including those triggered by the toggling of redundancy group roles during a high availability failover.
Toggling of redundancy group roles occurs when the state of an redundancy group changes from active to standby or vice versa. This ensures continuous service during an high availability failover. The Logs page in Cisco SD-WAN Manager allows you to monitor and track these changes, displaying any failover events so that you can take appropriate action if necessary.
 Feedback
Feedback