Secure Overlay
An overlay is a virtualized network layer on top of the physical network with the support of its infrastructure to provide additional security to the newtork. IPSec is a framework with protocols and algorithms to provide secured data transimission over unprotected or untrusted networks. IPSec secure tunnel is created between two networks to ensure virtual private network communication.
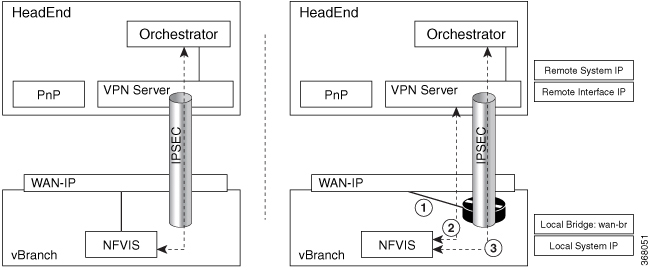
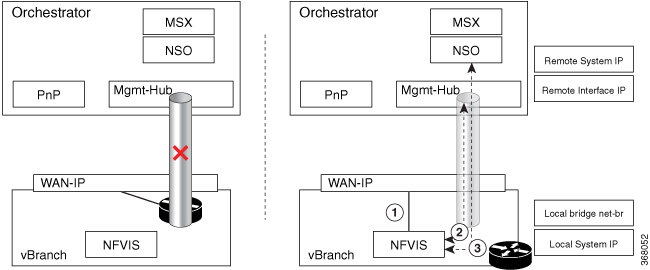
Secure overlay in NFVIS allows IPSec tunnel establishment between NFVIS supporting the vBranch platform and a VPN server and allows the orchestrator to manage NFVIS over the IPSec tunnel.
Supported Features on Secure Overlay
The following features are supported on NFVIS 3.10.x and later releases:
-
IPSec IKEv2
-
IPv4
-
Authentication:
-
Pre-shared-key authentication
-
Introduced in NFVIS 3.12.3 release - EAP authentication
-
-
IKE cipher:
-
aes128-sha1-mopd1536
-
Introduced in NFVIS 3.12.3 release - aes256-sha512-modp2048
-
Introduced in NFVIS 3.12.3 release - aes256-sha512-modp4096
-
-
ESP cipher:
-
aes128-sha1
-
Introduced in NFVIS 3.12.3 release - aes256-sha512
-
-
Local system IP address:
-
Unique tunnel IP address for each NFVIS system.
-
Introduced in NFVIS 3.11.1 release - Internal management network bridge (int-mgmt-net-br) gateway IP address is allowed to be used as local system IP address. In this case, the local system IP bridge much be set to internal management network (int-mgmt-net).
-
-
Local bridge for NFVIS reaching out to remote VPN server:
-
wan-br by default
-
wan2-br
-
-
Introduced in NFVIS 3.12.1 release - Secure overlay is support on NFVIS Dual WAN feature. DHCP client toggles between wan and wan2 to request for an IP address. When IP address and default gateway are obtained from an interface with DHCP configuration, the toggling stops. If dual-local-bridge is configured, to start overlay, NFVIS selects the interface between local-bridge and dual-local-bridge, in the following order:
-
Interface with DHCP configuration.
-
Interface having static IP address.
-
If both interfaces have static IP address, local-bridge interface.
-
-
Local identity:
-
IP address or FQDN
-
Introduced in NFVIS 3.12.3 release - email domain
-
-
Remote identity:
-
IP address or FQDN
-
Introduced in NFVIS 3.12.3 release - Distinguish Name
-
Introduced in NFVIS 3.12.3 release - email domain
-
Example for Secure Overlay with Zero Touch Deployment
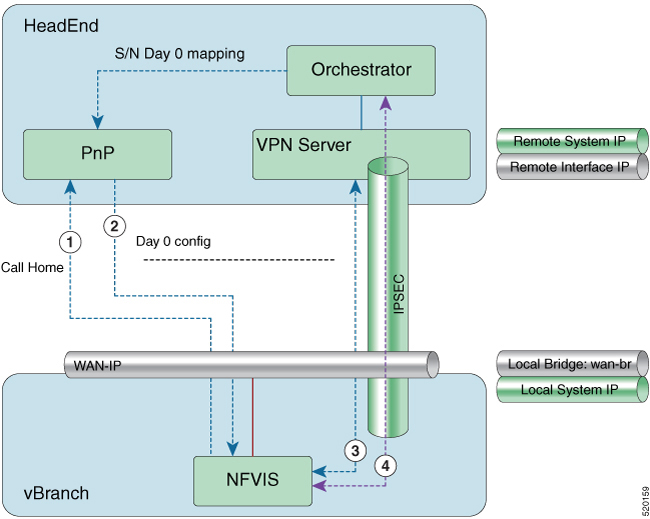
-
NFVIS has WAN IP address, static IP address or DHCP IP address. NFVIS calls home PnP server.
-
The PnP server pushes NFVIS Day-0 configurations including the secure overlay configuration.
-
NFVIS establishes IPSec connection between NFVIS and the headend management hub which has IPSec VPN configurations. On NFVIS side, the tunnel end point has NFVIS local system IP address.
-
After the IPSec tunnel is up, the headend can connect to NFVIS through the system IP address and manage NFVIS over the IPSec tunnel.
To configure secure overlay:
configure terminal
secure-overlay mgmthub
remote-interface-ip-addr 10.85.189.36
local-bridge wan-br
remote-system-ip-addr 10.19.18.251
remote-id mgmt-hub.cloudvpn.com
local-system-ip-addr 14.14.14.4
psk local-psk Cisco1234Admin
remote-psk Cisco1234Admin
commit
confirgure terminal
secure-overlay myconn
local-system-ip-addr 12.12.12.1
local-system-ip-bridge int-mgmt-net
remote-interface-ip-addr 172.19.160.75
remote-system-ip-addr 192.168.1.90
ike-cipher aes256-sha512-modp2048
esp-cipher aes256-sha512
remote-id "CN=vbranch, unstructuredAddress=172.19.160.75, unstructuredName=Headend.headendvpn"
local-id AxxxY@cisco.com
commit
configure terminal
secure-overlay myconn eap
username admin
password Cisco123#
cacert intdatastore:uploads/csr.pem
commit
To get the secure overlay state:
nfvis# show secure-overlay
ACTIVE SELECTED
LOCAL STATE LOCAL
NAME STATE BRIDGE DETAILS BRIDGE
--------------------------------------------------------
MYCONN UP wan-br wan-br
Examples for Configuring Secure Overlay
 Note |
Secure overlay configuration on NFVIS must match with VPN configuration on the VPN server. The secure overlay tunnel will not be established successfully if the configurations do not match. |
Secure Overlay over WAN with pre-shared-key and fqdn-remote-id
<secure-overlay>
<name>mgmthub</name>
<local-bridge>wan-br</local-bridge>
<local-system-ip-addr>14.14.14.4</local-system-ip-addr>
<remote-interface-ip-addr>10.85.189.36</remote-interface-ip-addr>
<remote-system-ip-addr>10.19.18.251</remote-system-ip-addr>
<remote-id>mgmt-hub.cloudvpn.com</remote-id>
<psk>
<local-psk>Cisco1234Admin</local-psk>
<remote-psk>Cisco1234Admin</remote-psk>
</psk>
</secure-overlay>
VPN configuration on VPN server:
crypto ikev2 authorization policy default
route set interface
route set access-list Inject
crypto ikev2 profile default
match identity remote any
identity local fqdn mgmt-hub.cloudvpn.com
authentication local pre-share key Cisco1234Admin
authentication remote pre-share key Cisco1234Admin
dpd 60 2 on-demand
nat keepalive 25
aaa authorization group psk list default default
virtual-template 1
crypto ipsec transform-set NO-ENCR esp-aes esp-sha-hmac
mode tunnel
crypto ipsec profile default
set transform-set NO-ENCR
set ikev2-profile default
interface Loopback1
description for IKEv2
ip address 10.253.254.1 255.255.255.255
interface GigabitEthernet0/0/1
description Corp_Network
ip address 10.85.189.36 255.255.255.0
negotiation auto
interface GigabitEthernet0/0/2
ip address 10.19.18.250 255.255.255.0
negotiation auto
interface Virtual-Template1 type tunnel
ip unnumbered Loopback1
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source GigabitEthernet0/0/1
tunnel mode ipsec ipv4
tunnel protection ipsec profile default
ip access-list extended Inject
remark restricts customer mgmt addresses
permit ip 10.254.0.0 0.0.255.255 any
Internal management network bridge IP address as local system IP address
 Note |
NFVIS internal management network has gateway IP address 12.12.12.1. |
<secure-overlay>
<name>mgmthub</name>
<local-bridge>wan-br</local-bridge>
<local-system-ip-addr>12.12.12.1</local-system-ip-addr>
<local-system-ip-bridge>int-mgmt-net</local-system-ip-bridge>
<remote-interface-ip-addr>10.85.189.36</remote-interface-ip-addr>
<remote-system-ip-addr>10.19.18.251</remote-system-ip-addr>
<remote-id>mgmt-hub.cloudvpn.com</remote-id>
<psk>
<local-psk>Cisco1234Admin</local-psk>
<remote-psk>Cisco1234Admin</remote-psk>
</psk>
</secure-overlay>
dual-local-bridge and int-mgmt-net-br IP as local system IP
<secure-overlay>
<name>mgmthub</name>
<local-bridge>wan-br</local-bridge>
<dual-local-bridge>wan2-br</dual-local-bridge.
<local-system-ip-addr>12.12.12.1</local-system-ip-addr>
<local-system-ip-bridge>int-mgmt-net</local-system-ip-bridge>
<remote-interface-ip-addr>10.85.189.36</remote-interface-ip-addr>
<remote-system-ip-addr>10.19.18.251</remote-system-ip-addr>
<remote-id>mgmt-hub.cloudvpn.com</remote-id>
<psk>
<local-psk>Cisco1234Admin</local-psk>
<remote-psk>Cisco1234Admin</remote-psk>
</psk>
</secure-overlay>
EAP authentication
<secure-overlay>
<name>mgmthub</name>
<local-bridge>wan-br</local-bridge>
<local-system-ip-addr>12.12.12.1</local-system-ip-addr>
<local-system-ip-bridge>int-mgmt-net</local-system-ip-bridge>
<local-id>branch101@cisco.com</local-id>
<remote-interface-ip-addr> 172.19.160.75</remote-interface-ip-addr>
<remote-system-ip-addr> 192.168.1.90</remote-system-ip-addr>
<remote-id>CN=vbranch, unstructuredAddress=172.19.160.75, unstructuredName=Headend.headendvpn</remote-id>
<ike-cipher>aes256-sha512-modp2048</ike-cipher>
<esp-cipher>aes256-sha51</esp-cipher>
<eap>
<username>admin</username>
<password>Cisco123#</password>
<cacert>https://cert/csr.pem</cacert>
</eap>
</secure-overlay>
The following is an example of the VPN configuration on VPN server:
aaa group server radius radius-group
server-private 172.19.160.190 auth-port 1812 acct-port 1813 key Cisco123#
ip radius source-interface GigabitEthernet
aaa authentication login default group radius-group
aaa authentication login ucpe-authen group radius-group
ip domain name headendvpn
crypto pki server ca-server
database level names
no database archive
hash sha512
lifetime certificate 3650
lifetime ca-certificate 7305 23 59
auto-rollover 365
eku server-auth client-auth
database url flash:ca
crypto pki trustpoint ca-server
revocation-check crl
rsakeypair ca-server
crypto pki trustpoint router
enrollment url http://172.19.160.75:80
ip-address 172.19.160.75
subject-name CN=vbranch
revocation-check crl
rsakeypair router
auto-enroll regenerate
hash sha512
crypto ikev2 authorization policy uCPE-athor-pol
pfs
route set interface
no crypto ikev2 authorization policy default
crypto ikev2 proposal uCPE-proposal
encryption aes-cbc-256
integrity sha512
group 16 14
no crypto ikev2 policy default
crypto ikev2 policy uCPE-policy
match address local 172.19.160.75
proposal uCPE-proposal
crypto ikev2 profile uCPE-profile
description uCPE profile
match identity remote email domain cisco.com
identity local dn
authentication local rsa-sig
authentication remote eap query-identity
pki trustpoint router
dpd 60 2 on-demand
aaa authentication eap ucpe-authen
aaa authorization group eap list default uCPE-athor-pol
virtual-template 1 mode auto
crypto ipsec transform-set tset_aes_256_sha512 esp-aes 256 esp-sha512-hmac
mode tunnel
crypto ipsec profile uCPE-ips-prof
set security-association lifetime seconds 28800
set security-association idle-time 1800
set transform-set tset_aes_256_sha512
set pfs group16
set ikev2-profile uCPE-profile
interface Loopback1
ip address 192.168.254.1 255.255.255.0
interface GigabitEthernet1
ip address 172.19.160.75 255.255.255.0
negotiation auto
no mop enabled
no mop sysid
interface GigabitEthernet2
ip address 192.168.1.90 255.255.255.0
negotiation auto
no mop enabled
no mop sysid
interface Virtual-Template1 type tunnel
description uCPE virt template
ip unnumbered Loopback1
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source GigabitEthernet1
tunnel mode ipsec ipv4
tunnel protection ipsec profile uCPE-ips-prof
 Feedback
Feedback