About Threat Defense Management by Security Cloud Control
About the Cloud-delivered Firewall Management Center
The cloud-delivered Firewall Management Center offers many of the same functions as an on-premises management center and has the same look and feel. When you use Security Cloud Control as the primary manager, you can use an on-prem management center for analytics only. The on-prem management center does not support policy configuration or upgrading.
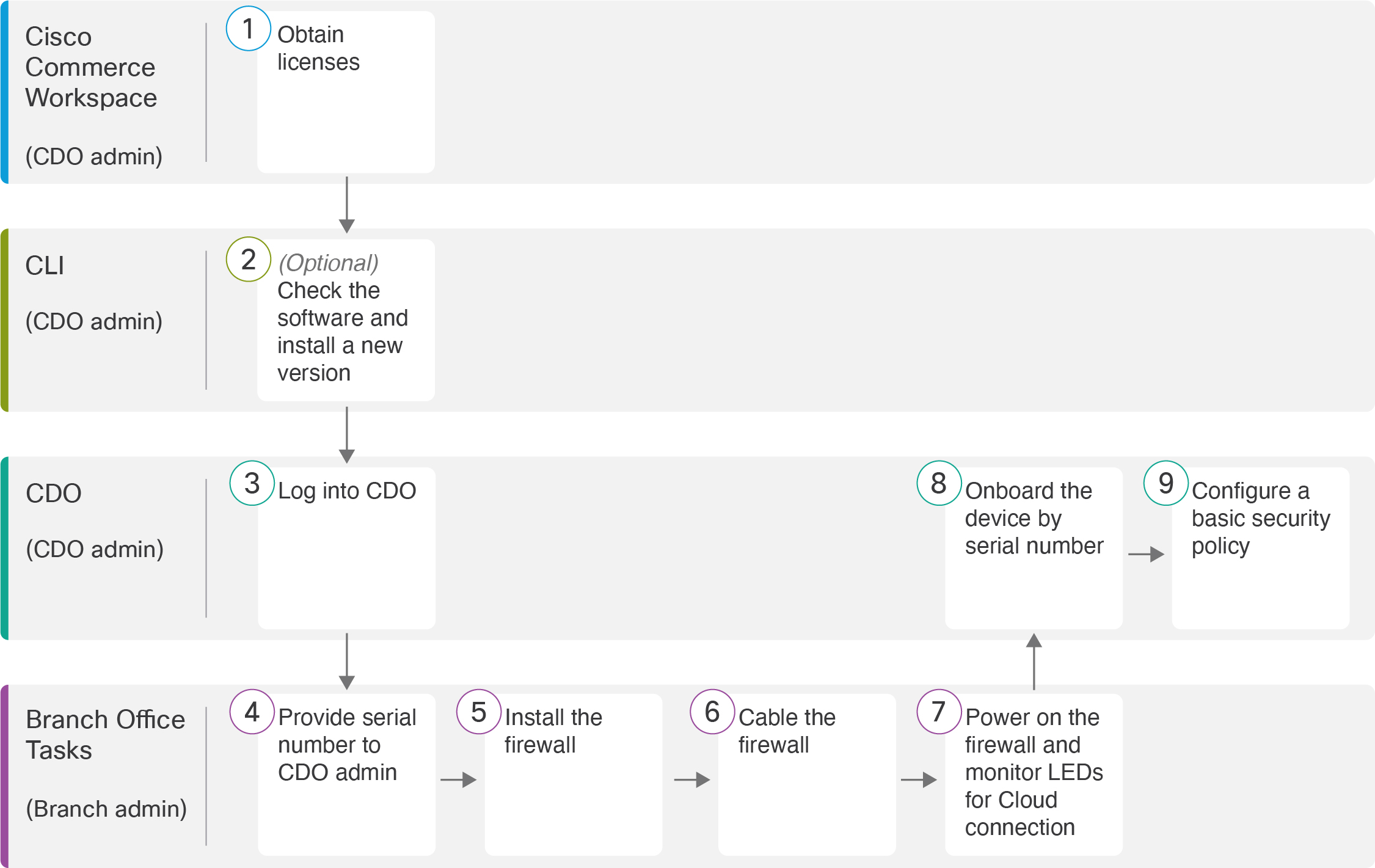
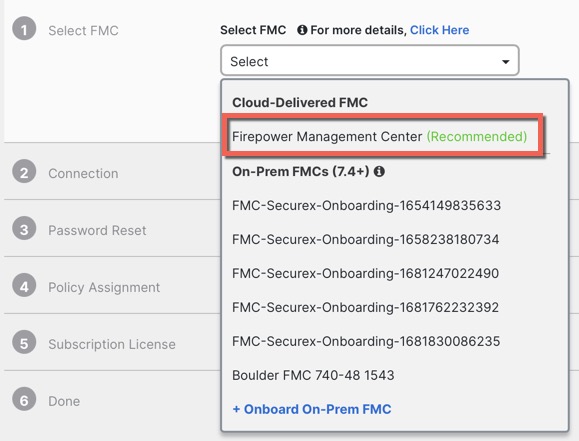
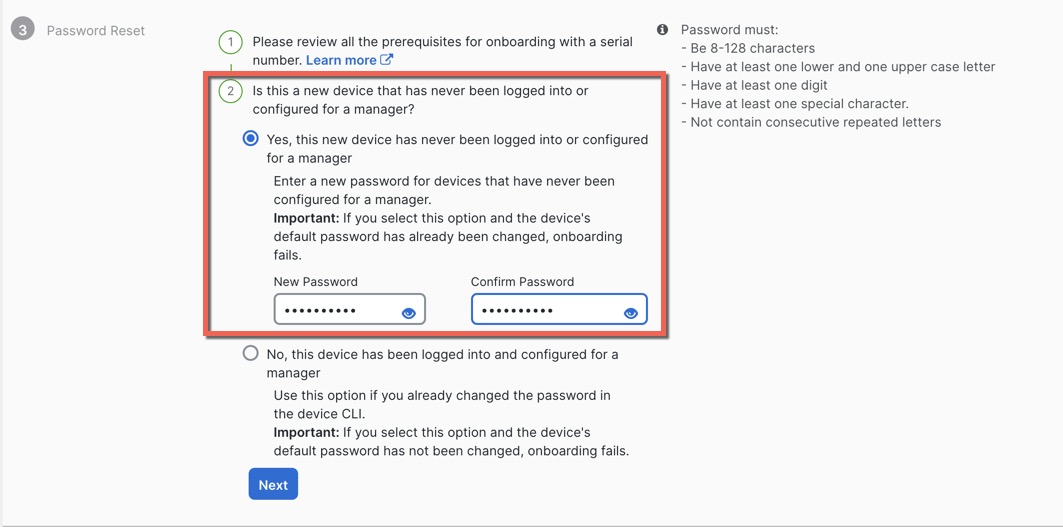
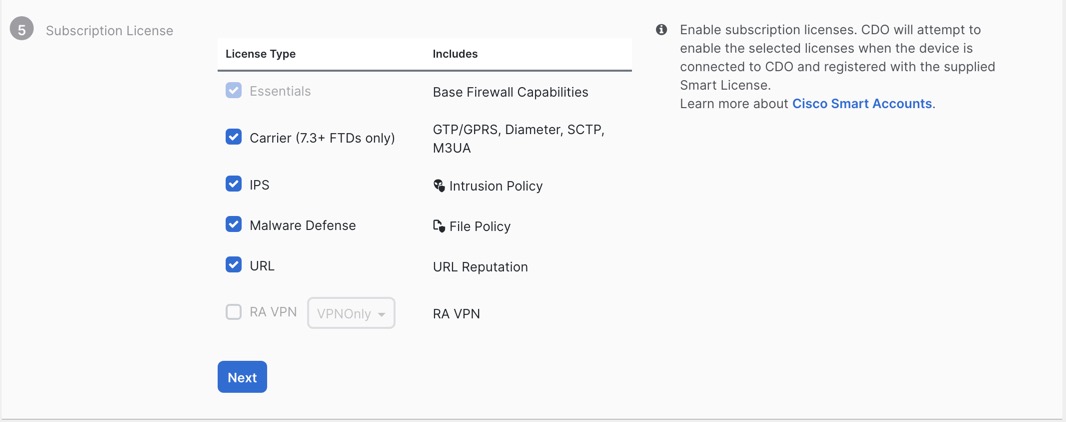
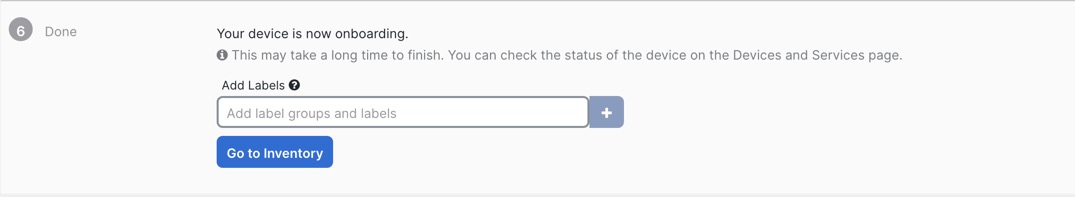
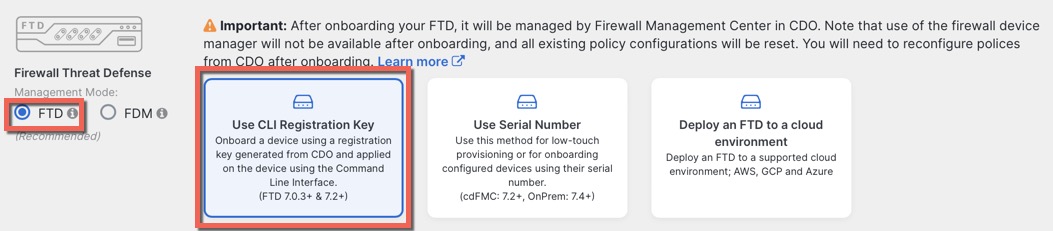
Security Cloud Control Onboarding Methods
Use one of the following methods to onboard a device.
Zero-Touch Provisioning
-
Send the threat defense to the remote branch office. Do not configure anything on the device, because zero-touch provisioning may not work with pre-configured devices.

Note
You can preregister the threat defense on Security Cloud Control using the threat defense serial number before sending the device to the branch office.
-
At the branch office, cable and power on the threat defense.
-
Finish onboarding the threat defense using Security Cloud Control.
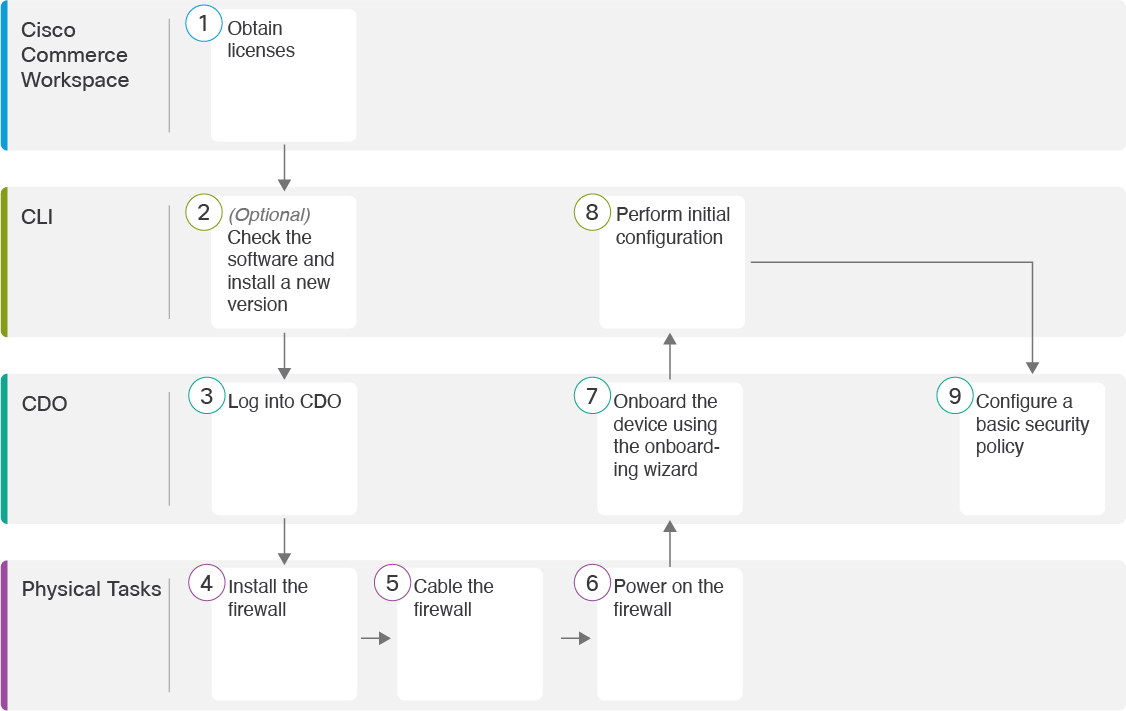
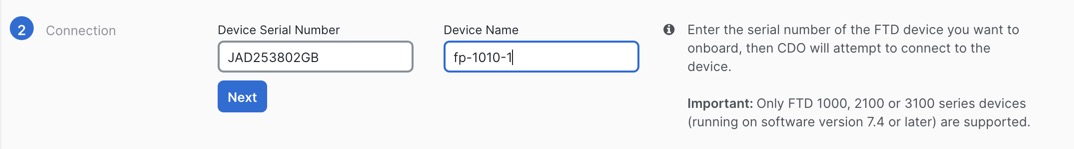
Manual Provisioning
Use the manual onboarding wizard and CLI registration if you need to perform any pre-configuration or if you are using a manager interface that zero-touch provisioning does not support.
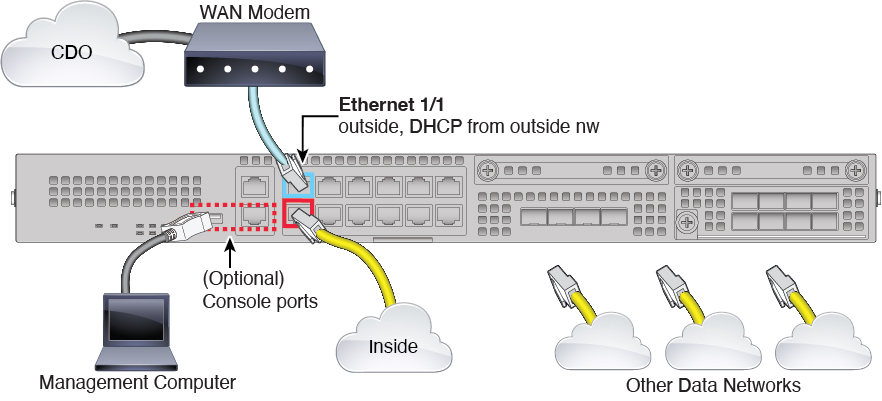
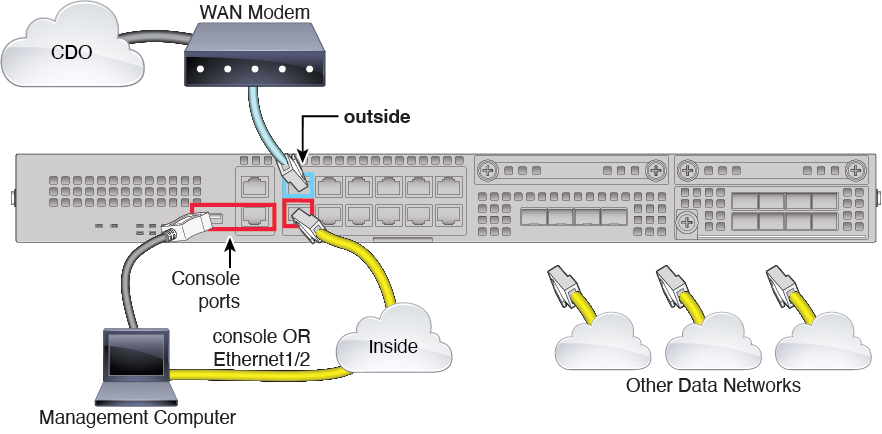
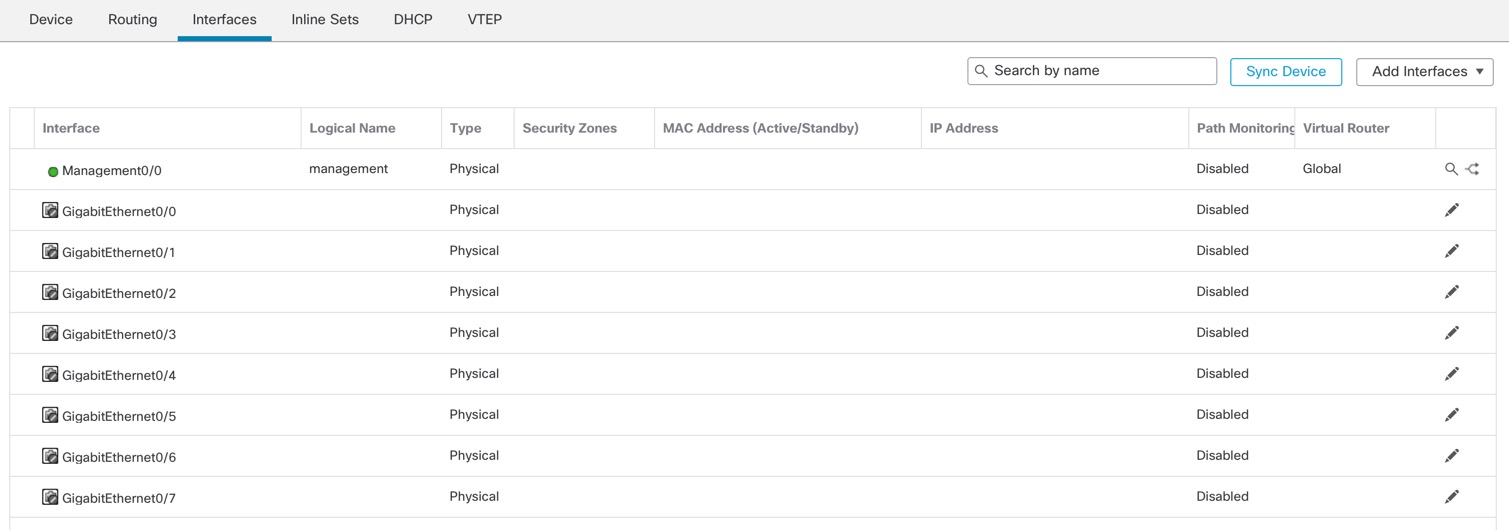
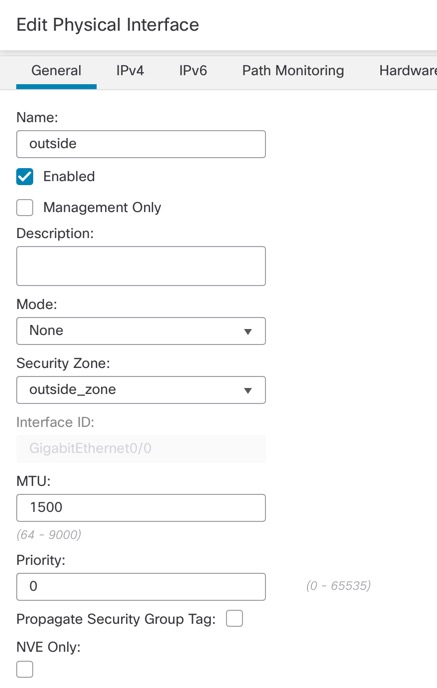
Threat Defense Manager Access Interface
This guide covers outside interface access because it is the most likely scenario for remote branch offices. Although manager access occurs on the outside interface, the dedicated Management interface is still relevant. The Management interface is a special interface configured separately from the threat defense data interfaces, and it has its own network settings.
-
The Management interface network settings are still used even though you are enabling manager access on a data interface.
-
All management traffic continues to be sourced from or destined to the Management interface.
-
When you enable manager access on a data interface, the threat defense forwards incoming management traffic over the backplane to the Management interface.
-
For outgoing management traffic, the Management interface forwards the traffic over the backplane to the data interface.
Manager Access Requirements
Manager access from a data interface has the following limitations:
-
You can only enable manager access on a physical, data interface. You cannot use a subinterface or EtherChannel, nor can you create a subinterface on the manager access interface. You can also use the management center to enable manager access on a single secondary interface for redundancy.
-
This interface cannot be management-only.
-
Routed firewall mode only, using a routed interface.
-
PPPoE is not supported. If your ISP requires PPPoE, you will have to put a router with PPPoE support between the threat defense and the WAN modem.
-
The interface must be in the global VRF only.
-
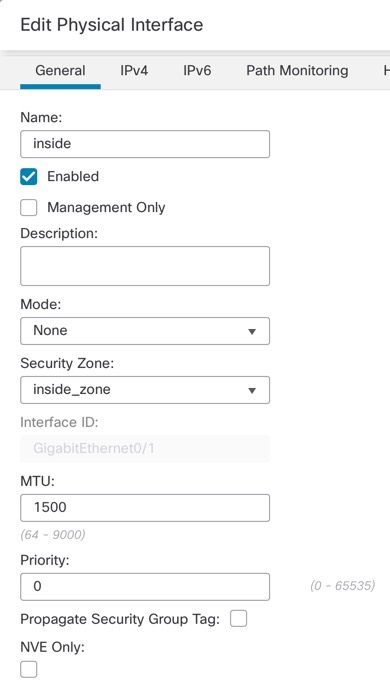
SSH is not enabled by default for data interfaces, so you will have to enable SSH later using the management center. Because the Management interface gateway will be changed to be the data interfaces, you also cannot SSH to the Management interface from a remote network unless you add a static route for the Management interface using the configure network static-routes command.
High Availability Requirements
When using a data interface with device high availability, see the following requirements.
-
Use the same data interface on both devices for manager access.
-
Redundant manager access data interface is not supported.
-
You cannot use DHCP; only a static IP address is supported. Features that rely on DHCP cannot be used, including DDNS and zero-touch provisioning.
-
Have different static IP addresses in the same subnet.
-
Use either IPv4 or IPv6; you cannot set both.
-
Use the same manager configuration (configure manager add command) to ensure that the connectivity is the same.
-
You cannot use the data interface as the failover or state link.





 Feedback
Feedback