Requirements and Prerequisites for the System Configuration
Model Support
FMC
Supported Domains
Global
User Roles
Admin
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices:
FMC
Global
Admin
System configuration settings apply to either a Firepower Management Center or a Classic managed device (ASA FirePOWER, NGIPSv):
For the Firepower Management Center these configuration settings are part of a "local" system configuration. Note that system configuration on the Firepower Management Center is specific to a single system, and changes to a FMC's system configuration affect only that system.
For a Classic managed device, you apply a configuration from the Firepower Management Center as part of a platform settings policy. You create a shared policy to configure a subset of the system configuration settings, appropriate for managed devices, that are likely to be similar across a deployment.
The system configuration identifies basic settings for a Firepower Management Center.
|
Step 1 |
Choose . |
|
Step 2 |
Use the navigation panel to choose configurations to change; see Table 1 for more information. |
Note that for managed devices, many of these configurations are handled by a platform settings policy applied from the FMC; see Platform Settings Policies.
|
Setting |
Description |
|---|---|
|
Access Control Preferences |
Configure the system to prompt users for a comment when they add or modify an access control policy; see Policy Change Comments. |
|
Access List |
Control which computers can access the system on specific ports; see Access List. |
|
Audit Log |
Configure the system to send an audit log to an external host; see Audit Logs. |
|
Audit Log Certificate |
Configure the system to secure the channel when streaming the audit log to an external host; see Audit Log Certificate . |
|
Change Reconciliation |
Configure the system to send a detailed report of changes to the system over the last 24 hours; see Change Reconciliation. |
|
Console Configuration |
Configure console access via VGA or serial port, or via Lights-Out Management (LOM); see Remote Console Access Management. |
|
Dashboard |
Enable Custom Analysis widgets on the dashboard; see Dashboard Settings. |
|
Database |
Specify the maximum number of each type of event that the Firepower Management Center can store; see Database Event Limits. |
|
DNS Cache |
Configure the system to resolve IP addresses automatically on event view pages; see DNS Cache. |
|
Email Notification |
Configure a mail host, select an encryption method, and supply authentication credentials for email-based notifications and reporting; see Email Notifications. |
|
External Database Access |
Enable external read-only access to the database, and provide a client driver to download; see External Database Access Settings. |
|
HTTPS Certificate |
Request an HTTPS server certificate, if needed, from a trusted authority and upload certificates to the system; see HTTPS Certificates. |
|
Information |
View current information about the appliance and edit the display name; see Appliance Information. |
|
Intrusion Policy Preferences |
Configure the system to prompt users for a comment when they modify an intrusion policy; see Policy Change Comments. |
|
Language |
Specify a different language for the web interface; see Language Selection. |
|
Login Banner |
Create a custom login banner that appears when users log in; see Login Banners. |
|
Management Interfaces |
Change options such as the IP address, hostname, and proxy settings of the appliance; see Management Interfaces. |
|
Network Analysis Policy Preferences |
Configure the system to prompt users for a comment when they modify a network analysis policy; see Policy Change Comments. |
|
Process |
Shut down, reboot, or restart Firepower processes; see Shut Down or Restart. |
|
Remote Storage Device |
Configure remote storage for backups and reports; see Remote Storage Management. |
|
REST API Preferences |
Enable or disable access to the Firepower Management Center via the Firepower REST API; see REST API Preferences. |
|
Shell Timeout |
Configure the amount of idle time, in minutes, before a user’s login session times out due to inactivity; see Session Timeouts. |
|
SNMP |
Enable Simple Network Management Protocol (SNMP) polling; see SNMP Polling. |
|
Time |
View and change the current time setting; see Time and Time Synchronization. |
|
Time Synchronization |
Manage time synchronization on the system; see Time and Time Synchronization. |
|
UCAPL/CC Compliance |
Enable compliance with specific requirements set out by the United States Department of Defense; see Enable Security Certifications Compliance. |
|
User Configuration |
Configure the Firepower Management Center to track successful login history and password history for all users, or enforce temporary lockouts on users who enter invalid login credentials; see Global User Configuration Settings |
|
VMware Tools |
Enable and use VMware Tools on a Firepower Management Center Virtual; see VMware Tools and Virtual Systems. |
|
Vulnerability Mapping |
Map vulnerabilities to a host IP address for any application protocol traffic received or sent from that address; see Vulnerability Mapping. |
|
Web Analytics |
Enable and disable collection of non-personally-identifiable information from your system. See (Optional) Opt Out of Web Analytics Tracking. |
The System > Configuration page of the web interface includes the information listed in the table below. Unless otherwise noted, all fields are read-only.
 Note |
See also the Help > About page, which includes similar but slightly different information. |
|
Field |
Description |
|---|---|
|
Name |
A descriptive name you assign to the FMCappliance. Although you can use the host name as the name of the appliance, entering a different name in this field does not change the host name. This name is used in certain integrations. For example, it appears in the Devices list for integrations with SecureX and Cisco SecureX threat response. |
|
Product Model |
The model name of the appliance. |
|
Serial Number |
The serial number of the appliance. |
|
Software Version |
The version of the software currently installed on the appliance. |
|
Operating System |
The operating system currently running on the appliance. |
|
Operating System Version |
The version of the operating system currently running on the appliance. |
|
IPv4 Address |
The IPv4 address of the default ( |
|
IPv6 Address |
The IPv6 address of the default ( |
|
Current Policies |
The system-level policies currently deployed. If a policy has been updated since it was last deployed, the name of the policy appears in italics. |
|
Model Number |
The appliance-specific model number stored on the internal flash drive. This number may be important for troubleshooting. |
Secure Sockets Layer (SSL)/TLS certificates enable Firepower Management Centers to establish an encrypted channel between the system and a web browser. A default certificate is included with all Firepower devices, but it is not generated by a certificate authority (CA) trusted by any globally known CA. For this reason, consider replacing it with a custom certificate signed by a globally known or internally trusted CA.
 Caution |
The FMC supports 4096-bit HTTPS certificates. If the certificate used by the FMC was generated using a public server key larger than 4096 bits, you will not be able to log in to the FMC web interface. If this happens, contact Cisco TAC. |
If you use the default server certificate provided with an appliance, do not configure the system to require a valid HTTPS client certificate for web interface access because the default server certificate is not signed by the CA that signs your client certificate.
The lifetime of the default server certificate depends on when the certificate was generated. To view your default server certificate expiration date, choose > HTTPS Certificate.
Note that some Firepower software upgrades can automatically renew the certificate. For more information, see the appropriate version of the Cisco Firepower Release Notes.
On the Firepower Management Center, you can renew the default certificate on the > HTTPS Certificate page.
You can use the Firepower Management Center web interface to generate a server certificate request based on your system information and the identification information you supply. You can use that request to sign a certificate if you have an internal certificate authority (CA) installed that is trusted by your browser. You can also send the resulting request to a certificate authority to request a server certificate. After you have a signed certificate from a certificate authority (CA), you can import it.
When you use HTTPS certificates to secure the connection between your web browser and the Firepower appliance web interface, you must use certificates that comply with the Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile (RFC 5280). When you import a server certificate to the appliance, the system rejects the certificate if it does not comply with version 3 (X.509 v3) of that standard.
Before importing an HTTPS server certificate, be certain it includes the following fields:
|
Certificate Field |
Description |
|---|---|
|
Version |
Version of the encoded
certificate. Use version |
|
Serial number |
A positive integer assigned to the certificate by the issuing CA. Issuer and serial number together uniquely identify the certificate. See RFC 5280, section 4.1.2.2. |
|
Signature |
Identifier for the algorithm used by the CA to sign the certificate. Must match the signatureAlgorithm field. See RFC 5280, section 4.1.2.3. |
|
Issuer |
Identifies the entity that signed and issued the certificate. See RFC 5280, section 4.1.2.4. |
|
Validity |
Interval during which the CA warrants that it will maintain information about the status of the certificate. See RFC 5280, section 4.1.2.5. |
|
Subject |
Identifies the entitity associated with the public key stored in the subject public key field; must be an X.500 disinguished name (DN). See RFC 5280, section 4.1.2.6. |
|
Subject Alternative Name |
Domain names and IP addresses secured by the certificate. Subject Alternative Name is defined in section RFC 5280, section 4.2.1.6. We recommend you use this field if the certificate is used for multiple domains or IP addresses. |
|
Subject Public Key Info |
Public key and an identifier for its algorithm. See RFC 5280, section 4.1.2.7. |
|
Authority Key Identifier |
Provides a means of identifying the public key corresponding to the private key used to sign a certificate. See RFC 5280, section 4.2.1.1. |
|
Subject Key Identifier |
Provides a means of identifying certificates that contain a particular public key. See RFC 5280, section 4.2.1.2. |
|
Key Usage |
Defines the purpose of the key contained in the certificates. See RFC 5280, section 4.2.1.3. |
|
Basic Constraints |
Identifies whether the certificate Subject is a CA, and the maximum depth of validation certification paths that include this
certificate. See RFC 5280, section 4.2.1.9. For server certificates used in Firepower appliances, use |
|
Extended Key Usage extension |
Indicates one or more purposes for which the certified public key may be used, in addition to or in place of the basic purposes indicated in the Key Usage extension. See RFC 5280, section 4.2.1.12. Be certain you import certificates that can be used as server certificates. |
|
signatureAlgorithm |
Identifier for the algorithm the CA used to sign the certificate. Must match the Signature field. See RFC 5280, section 4.1.1.2. |
|
signatureValue |
Digital signature. See RFC 5280, section 4.1.1.3. |
You can restrict access to the Firepower System web server using client browser certificate checking. When you enable user certificates, the web server checks that a user’s browser client has a valid user certificate selected. That user certificate must be generated by the same trusted certificate authority that is used for the server certificate. The browser cannot load the web interface under any of the following circumstances:
The user selects a certificate in the browser that is not valid.
The user selects a certificate in the browser that is not generated by the certificate authority that signed the server certificate.
The user selects a certificate in the browser that is not generated by a certificate authority in the certificate chain on the device.
To verify client browser certificates, configure the system to use the online certificate status protocol (OCSP) or load one or more certificate revocation lists (CRLs). Using the OCSP, when the web server receives a connection request it communicates with the certificate authority to confirm the client certificate's validity before establishing the connection. If you configure the server to load one or more CRLs, the web server compares the client certificate against those listed in the CRLs. If a user selects a certificate that is listed in a CRL as a revoked certificate, the browser cannot load the web interface.
 Note |
If you choose to verify certificates using CRLs, the system uses the same CRLs to validate both client browser certificates and audit log server certificates. |
|
Step 1 |
Choose . |
|
Step 2 |
Click HTTPS Certificate. |
If you install a certificate that is not signed by a globally known or internally trusted CA, the user's browser displays a security warning when they try to connect to the web interface.
A certificate signing request (CSR) is unique to the appliance or device from which you generated it. You cannot generate a CSR for multiple devices from a single appliance. Although all fields are optional, we recommend entering values for the following: CN, Organization, Organization Unit, City/Locality, State/Province, Country/Region, and Subject Alternative Name.
The key generated for the certificate request is in Base-64 encoded PEM format.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click HTTPS Certificate. |
||
|
Step 3 |
Click Generate New CSR.  |
||
|
Step 4 |
Enter a country code in the Country Name (two-letter code) field. |
||
|
Step 5 |
Enter a state or province postal abbreviation in the State or Province field. |
||
|
Step 6 |
Enter a Locality or City. |
||
|
Step 7 |
Enter an Organization name. |
||
|
Step 8 |
Enter an Organizational Unit (Department) name. |
||
|
Step 9 |
Enter the fully qualified domain name of the server for which you want to request a certificate in the Common Name field.
|
||
|
Step 10 |
To request a certificate that secures multiple domain names or IP addresses, enter the folowing information in the Subject Alternative Name section:
|
||
|
Step 11 |
Click Generate. |
||
|
Step 12 |
Open a text editor. |
||
|
Step 13 |
Copy the entire block of text in the certificate request,
including the
|
||
|
Step 14 |
Save the file as
|
||
|
Step 15 |
Click Close. |
Submit the certificate request to the certificate authority.
When you receive the signed certificate, import it to the Firepower Management Center; see Importing HTTPS Server Certificates.
If the signing authority that generated the certificate requires you to trust an intermediate CA, you must also supply a certificate chain (or certificate path).
If you require client certificates, accessing an appliance via the web interface will fail when the server certificate does not meet either of the following criteria:
The certificate is signed by the same CA that signed the client certificate.
The certificate is signed by a CA that has signed an intermediate certificate in the certificate chain.
 Caution |
The Firepower Management Center supports 4096-bit HTTPS certificates. If the certificate used by the Firepower Management Center was generated using a public server key larger than 4096 bits, you will not be able to log in to the FMC web interface. For more information about updating HTTPS Certificates to Version 6.0.0, see "Update Management Center HTTPS Certificates to Version 6.0" in Firepower System Release Notes, Version 6.0. If you generate or import an HTTPS Certificate and cannot log in to the FMC web interface, contact Support. |
Generate a certificate signing request; see Generating an HTTPS Server Certificate Signing Request.
Upload the CSR file to the certificate authority where you want to request a certificate, or use the CSR to create a self-signed certificate.
Confirm that the certificate meets the requirements described in HTTPS Server Certificate Requirements.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click HTTPS Certificate. |
||
|
Step 3 |
Click Import HTTPS Server Certificate.
|
||
|
Step 4 |
Open the server certificate in a text editor, copy the entire block of text, including the |
||
|
Step 5 |
Whether you must supply a Private Key depends on how you generated the Certificate Signing Request:
|
||
|
Step 6 |
Open any required intermediate certificates, copy the
entire block of text for each, and paste it into the Certificate Chain field. If you received a
root certificate, paste it here. If you received an intermediate certificate,
paste it below the root certificate. In both cases, copy the entire block of
text, including the |
||
|
Step 7 |
Click Save. |
Use this procedure to require users connecting to the FMC web interface to supply a user certificate. The system supports validating HTTPS client certificates using either OCSP or imported CRLs in Privacy-enhanced Electronic Mail (PEM) format.
If you choose to use CRLs, to ensure that the list of revoked certificates stays current, you can create a scheduled task to update the CRLs. The system displays the most recent refresh of the CRLs.
 Note |
To access the web interface after enabling client certificates, you must have a valid client certificate present in your browser (or a CAC inserted in your reader). |
Import a server certificate signed by the same certificate authority that signed the client certificate to be used for the connection; see Importing HTTPS Server Certificates.
Import the server certificate chain if needed; see Importing HTTPS Server Certificates.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click HTTPS Certificate. |
||
|
Step 3 |
Choose Enable Client Certificates. If prompted, select the appropriate certificate from the drop-down list. |
||
|
Step 4 |
You have three options:
|
||
|
Step 5 |
Enter a valid URL to an existing CRL file and click Add CRL. Repeat to add up to 25 CRLs. |
||
|
Step 6 |
Click Refresh CRL to load the current CRL or CRLs from the specified URL or URLs.
|
||
|
Step 7 |
Verify that the client certificate is signed by the certificate authority loaded onto the appliance and the server certificate is signed by a certificate authority loaded in the browser certificate store. (These should be the same certificate authority.)
|
||
|
Step 8 |
Click Save. |
You can only view server certificates for the appliance you are logged in to.
|
Step 1 |
Choose . |
|
Step 2 |
Click HTTPS Certificate. The button appears only if your system is configured to use the default HTTPS server certificate. |
|
Step 3 |
Click Renew HTTPS Certificate. (This option appears on the display below the certificate information only if your system is configured to used the default HTTPS server certificate.) |
|
Step 4 |
(Optional) In the Renew HTTPS Certificate dialog box, select Generate New Key to generate a new key for the certificate. |
|
Step 5 |
In the Renew HTTPS Certificate dialog box, click Save. |
You can confirm that the certificate has been renewed by checking that that certificate validity dates displayed on the HTTPS Certificate page have updated.
You can configure the Firepower Management Center to allow read-only access to its database by a third-party client. This allows you to query the database using SQL using any of the following:
industry-standard reporting tools such as Actuate BIRT, JasperSoft iReport, or Crystal Reports
any other reporting application (including a custom application) that supports JDBC SSL connections
the Cisco-provided command-line Java application called RunQuery, which you can either run interactively or use to obtain comma-separated results for a single query
Use the Firepower Management Center's system configuration to enable database access and create an access list that allows selected hosts to query the database. Note that this access list does not also control appliance access.
You can also download a package that contains the following:
RunQuery, the Cisco-provided database query tool
InstallCert, a tool you can use to retrieve and accept the SSL certificate from the Firepower Management Center you want to access
the JDBC driver you must use to connect to the database
See the Firepower System Database Access Guide for information on using the tools in the package you downloaded to configure database access.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click External Database Access. |
||
|
Step 3 |
Select the Allow External Database Access check box. |
||
|
Step 4 |
Enter an appropriate value in the Server Hostname field. Depending on your third-party application requirements, this value can be either the fully qualified domain name (FQDN), IPv4 address, or IPv6 address of the Firepower Management Center.
|
||
|
Step 5 |
Next to
Client JDBC Driver, click
Download and follow your browser’s prompts to
download the
|
||
|
Step 6 |
To add database access for one or more IP addresses, click Add Hosts. An IP Address field appears in the Access List field. |
||
|
Step 7 |
In the
IP Address field, enter an IP address or address
range, or
|
||
|
Step 8 |
Click Add. |
||
|
Step 9 |
Click Save.
|
To manage disk space, the FMC periodically prunes the oldest intrusion events, audit records, Security Intelligence data, and URL filtering data from the event database. For each event type, you can specify how many records the FMC retains after pruning; never rely on the event database containing more records of any type than the retention limit configured for that type. To improve performance, tailor the event limits to the number of events you regularly work with. You can optionally choose to receive email notifications when pruning occurs. For some event types, you can disable storage.
To manually delete individual events, use the event viewer. (Note that in Versions 6.6.0+, you cannot manually delete connection or security Intelligence events in this way.)You can also manually purge the database; see Data Storage.
If you want to receive email notifications when events are pruned from the Firepower Management Center's database, you must configure an email server; see Configuring a Mail Relay Host and Notification Address.
|
Step 1 |
Choose . |
|
Step 2 |
Choose Database. |
|
Step 3 |
For each of the databases, enter the number of records you want to store. For information on how many records each database can maintain, see Database Event Limits. |
|
Step 4 |
Optionally, in the Data Pruning Notification Address field, enter the email address where you want to receive pruning notifications. |
|
Step 5 |
Click Save. |
The following table lists the minimum and maximum number of records for each event type that you can store on a Firepower Management Center.
|
Event Type |
Upper Limit |
Lower Limit |
|---|---|---|
|
Intrusion events |
10 million (FMC Virtual) 30 million (FMC1000, FMC1600) 60 million (FMC2500, FMC2600, FMCv 300) 300 million (FMC4500, FMC4600) |
10,000 |
|
Discovery events |
10 million (FMC Virtual) 20 million (FMC2500, FMC2600, FMC4500, FMC4600, FMCv 300) |
Zero (disables storage) |
|
Connection events Security Intelligence events |
50 million (FMC Virtual) 100 million (FMC1000, FMC1600) 300 million (FMC2500, FMC2600, FMCv 300) 1 billion (FMC4500, FMC4600) Limit is shared between connection events and Security Intelligence events. The sum of the configured maximums cannot exceed this limit. |
Zero (disables storage) Setting Maximum Connection Events to zero immediately purges existing connection events. Note that disabling connection event storage on the Firepower Management Center does not affect remote event storage, nor does it affect connection summaries or correlation. The system still uses connection event information for features like traffic profiles, correlation policies, and dashboard displays. |
|
Connection summaries (aggregated connection events) |
50 million (FMC Virtual) 100 million (FMC1000, FMC1600) 300 million (FMC2500, FMC2600, FMCv 300) 1 billion (FMC4500, FMC4600) |
Zero (disables storage) |
|
Correlation events and compliance white list events |
1 million (FMC Virtual) 2 million (FMC2500, FMC2600, FMC4500, FMC4600, FMCv 300) |
One |
|
Malware events |
10 million (FMC Virtual) 20 million (FMC2500, FMC2600, FMC4500, FMC4600, FMCv 300) |
10,000 |
|
File events |
10 million (FMC Virtual) 20 million (FMC2500, FMC2600, FMC4500, FMC4600, FMCv 300) |
Zero (disables storage) |
|
Health events |
1 million |
Zero (disables storage) |
|
Audit records |
100,000 |
One |
|
Remediation status events |
10 million |
One |
|
White list violation history |
a 30-day history of violations |
One day’s history |
|
User activity (user events) |
10 million |
One |
|
User logins (user history) |
10 million |
One |
|
Intrusion rule update import log records |
1 million |
One |
|
VPN Troubleshooting database |
10 million |
Zero (disables storage) |
After setup, you can change the management network settings, including adding more management interfaces, hostname, search domains, DNS servers, and HTTP proxy on the FMC.
By default, the FMC manages all devices on a single management interface. You can also perform initial setup on the management interface and log into the FMC on this interface as an administrator. The management interface is also used to communicate with the Smart Licensing server, to download updates, and to perform other management functions.
For information about device management interfaces, see About Device Management Interfaces.
The FMC uses the eth0 interface for initial setup, HTTP access for administrators, management of devices, as well as other management functions such as licensing and updates.
You can also configure additional management interfaces on the same network, or on different networks. When the FMC manages large numbers of devices, adding more management interfaces can improve throughput and performance. You can also use these interfaces for all other management functions. You might want to use each management interface for particular functions; for example, you might want to use one interface for HTTP administrator access and another for device management.
For device management, the management interface carries two separate traffic channels: the management traffic channel carries all internal traffic (such as inter-device traffic specific to managing the device), and the event traffic channel carries all event traffic (such as web events). You can optionally configure a separate event-only interface on the FMC to handle event traffic; you can configure only one event interface. Event traffic can use a large amount of bandwidth, so separating event traffic from management traffic can improve the performance of the FMC. For example, you can assign a 10 GigabitEthernet interface to be the event interface, if available, while using 1 GigabitEthernet interfaces for management. You might want to configure an event-only interface on a completely secure, private network while using the regular management interface on a network that includes Internet access, for example. You can also use both management and event interfaces on the same network if the goal is only to take advantage of increased throughput. Managed devices will send management traffic to the FMC management interface and event traffic to the FMCs event-only interface. If the managed device cannot reach the event-only interface, then it will fall back to sending events to the management interface.
 Note |
All management interfaces support HTTP administrator access as controlled by your Access List configuration (Configure an Access List). Conversely, you cannot restrict an interface to only HTTP access; management interfaces always support device management (management traffic, event traffic, or both). |
 Note |
Only the eth0 interface supports DHCP IP addressing. Other management interfaces only support static IP addresses. |
See the hardware installation guide for your model for the management interface locations.
See the following table for supported management interfaces on each FMC model.
|
Model |
Management Interfaces |
|---|---|
|
MC1000 |
eth0 (Default) eth1 |
|
MC2500, MC4500 |
eth0 (Default) eth1 eth2 eth3 |
|
MC1600, MC2600, MC4600 |
eth0 (Default) eth1 eth2 eth3 CIMC (Supported for Lights-Out Management only.) |
|
Firepower Management Center Virtual |
eth0 (Default) |
Management interfaces (including event-only interfaces) support only static routes to reach remote networks. When you set up your FMC, the setup process creates a default route to the gateway IP address that you specify. You cannot delete this route; you can only modify the gateway address.
You can configure multiple management interfaces on some platforms. The default route does not include an egress interface, so the interface chosen depends on the gateway address you specify, and which interface's network the gateway belongs to. In the case of multiple interfaces on the default network, the device uses the lower-numbered interface as the egress interface.
At least one static route is recommended per management interface to access remote networks. We recommend placing each interface on a separate network to avoid potential routing problems, including routing problems from other devices to the FMC. If you do not experience problems with interfaces on the same network, then be sure to configure static routes correctly. For example, on the FMC both eth0 and eth1 are on the same network, but you want to manage a different group of devices on each interface. The default gateway is 192.168.45.1. If you want eth1 to manage devices on the remote 10.6.6.0/24 destination network, you can create a static route for 10.6.6.0/24 through eth1 with the same gateway of 192.168.45.1. Traffic to 10.6.6.0/24 will hit this route before it hits the default route, so eth1 will be used as expected.
If you want to use two FMC interfaces to manage remote devices that are on the same network, then static routing on the FMC may not scale well, because you need separate static routes per device IP address.
Another example includes separate management and event-only interfaces on both the FMC and the managed device. The event-only interfaces are on a separate network from the management interfaces. In this case, add a static route through the event-only interface for traffic destined for the remote event-only network, and vice versa.
Network address translation (NAT) is a method of transmitting and receiving network traffic through a router that involves reassigning the source or destination IP address. The most common use for NAT is to allow private networks to communicate with the internet. Static NAT performs a 1:1 translation, which does not pose a problem for FMC communication with devices, but port address translation (PAT) is more common. PAT lets you use a single public IP address and unique ports to access the public network; these ports are dynamically assigned as needed, so you cannot initiate a connection to a device behind a PAT router.
Normally, you need both IP addresses (along with a registration key) for both routing purposes and for authentication: the FMC specifies the device IP address when you add a device, and the device specifies the FMC IP address. However, if you only know one of the IP addresses, which is the minimum requirement for routing purposes, then you must also specify a unique NAT ID on both sides of the connection to establish trust for the initial communication and to look up the correct registration key. The FMC and device use the registration key and NAT ID (instead of IP addresses) to authenticate and authorize for initial registration.
For example, you add a device to the FMC, and you do not know the device IP address (for example, the device is behind a PAT router), so you specify only the NAT ID and the registration key on the FMC; leave the IP address blank. On the device, you specify the FMC IP address, the same NAT ID, and the same registration key. The device registers to the FMC's IP address. At this point, the FMC uses the NAT ID instead of IP address to authenticate the device.
Although the use of a NAT ID is most common for NAT environments, you might choose to use the NAT ID to simplify adding many devices to the FMC. On the FMC, specify a unique NAT ID for each device you want to add while leaving the IP address blank, and then on each device, specify both the FMC IP address and the NAT ID. Note: The NAT ID must be unique per device.
The following example shows three devices behind a PAT IP address. In this case, specify a unique NAT ID per device on both the FMC and the devices, and specify the FMC IP address on the devices.
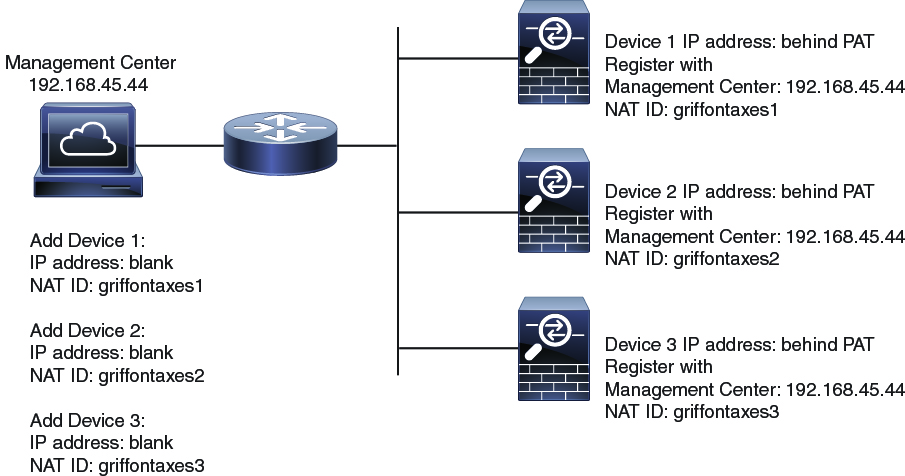
The following example shows the FMC behind a PAT IP address. In this case, specify a unique NAT ID per device on both the FMC and the devices, and specify the device IP addresses on the FMC.
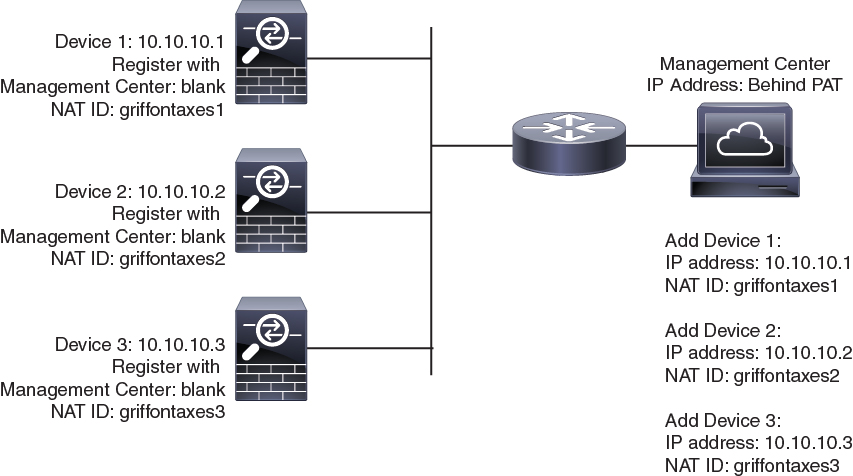
 Note |
If you use a data interface for management on an FTD, you cannot use separate management and event interfaces for that device. |
The following example shows the Firepower Management Center and managed devices using only the default management interfaces.

The following example shows the Firepower Management Center using separate management interfaces for devices; and each managed device using 1 management interface.

The following example shows the Firepower Management Center and managed devices using a separate event interface.

The following example shows a mix of multiple management interfaces and a separate event interface on the Firepower Management Center and a mix of managed devices using a separate event interface, or using a single management interface.

 Caution |
Do NOT push the FMC deployments over a VPN tunnel that is terminating directly on the Firepower Threat Defense. Pushing the FMC deployments can potentially inactivate the tunnel and disconnect the FMC and the Firepower Threat Defense. Recovering the device from this situation can be very disruptive and require executing the disaster recovery procedure. This procedure resets the Firepower Threat Defense configuration to factory defaults by changing manager from FMC to local and configuring the device from beginning. For more information, see Deploying the FMC Policy Configuration over VPN Tunnel. |
Modify the management interface settings on the Firepower Management Center. You can optionally enable additional management interfaces or configure an event-only interface.
 Caution |
Be careful when making changes to the management interface to which you are connected; if you cannot re-connect because of a configuration error, you need to access the FMC console port to re-configure the network settings in the Linux shell. You must contact Cisco TAC to guide you in this operation. |
 Note |
If you change the FMC IP address, then see Edit the FMC IP Address or Hostname on the Device. If you change the FMC IP address or hostname, you should also change the value at the device CLI so the configurations match. Although in most cases, the management connection will be reestablished without changing the FMC IP address or hostname on the device, in at least one case, you must perform this task for the connection to be reestablished: when you added the device to the FMC and you specified the NAT ID only. Even in other cases, we recommend keeping the FMC IP address or hostname up to date for extra network resiliency. |
 Note |
In a high availability configuration, when you modify the management IP address of a registered Firepower device from the device CLI or from Firepower Management Center, the secondary Firepower Management Center does not reflect the changes even after an HA synchronization. To ensure that the secondary Firepower Management Center is also updated, switch roles between the two Firepower Management Centers, making the secondary Firepower Management Center as the active unit. Modify the management IP address of the registered Firepower device on the device management page of the now active Firepower Management Center. |
For information about how device management works, see About Device Management Interfaces.
If you use a proxy:
Proxies that use NT LAN Manager (NTLM) authentication are not supported.
If you use or will use Smart Licensing, the proxy FQDN cannot have more than 64 characters.
|
Step 1 |
Choose , and then choose Management Interfaces. |
||||
|
Step 2 |
In the Interfaces area, click Edit next to the interface that you want to configure. All available interfaces are listed in this section. You cannot add more interfaces. You can configure the following options on each management interface:
|
||||
|
Step 3 |
In the Routes area, edit a static route by clicking Edit ( View the route table by clicking You need a static route for each additional interface to reach remote networks. For more information about when new routes are needed, see Network Routes on FMC Management Interfaces.
You can configure the following settings for a static route:
|
||||
|
Step 4 |
In the Shared Settings area, set network parameters shared by all interfaces.
You can configure the following shared settings:
|
||||
|
Step 5 |
In the ICMPv6 area, configure ICMPv6 settings.
|
||||
|
Step 6 |
In the Proxy area, configure HTTP proxy settings. The FMC is configured to directly-connect to the internet on ports TCP/443 (HTTPS) and TCP/80 (HTTP). You can use a proxy server, to which you can authenticate via HTTP Digest. See proxy requirements in the prerequisites to this topic. |
||||
|
Step 7 |
Click Save. |
||||
|
Step 8 |
If you change the FMC IP address, then see If you change the FMC IP address, then see Edit the FMC IP Address or Hostname on the Device. If you change the FMC IP address or hostname, you should also change the value at the device CLI so the configurations match. Although in most cases, the management connection will be reestablished without changing the FMC IP address or hostname on the device, in at least one case, you must perform this task for the connection to be reestablished: when you added the device to the FMC and you specified the NAT ID only. Even in other cases, we recommend keeping the FMC IP address or hostname up to date for extra network resiliency. |
Use the web interface to control the shut down and restart of processes on the FMC. You can:
Shut down: Initiate a graceful shutdown of the appliance.
 Caution |
Do not shut off Firepower appliances using the power button; it may cause a loss of data. Using the web interface (or CLI) prepares the system to be safely powered off and restarted without losing configuration data. |
Reboot: Shut down and restart gracefully.
Restart the console: Restart the communications, database, and HTTP server processes. This is typically used during troubleshooting.
 Tip |
For virtual devices, refer to the documentation for your virtual platform. For VMware in particular, custom power options are part of VMware Tools. |
|
Step 1 |
Choose . |
||||||||||
|
Step 2 |
Choose Process. |
||||||||||
|
Step 3 |
Do one of the following:
|
On Firepower Management Centers, you can use the following for local or remote storage for backups and reports:
Network File System (NFS)
Server Message Block (SMB)/Common Internet File System (CIFS)
Secure Shell (SSH)
You cannot send backups to one remote system and reports to another, but you can choose to send either to a remote system and store the other on the Firepower Management Center.
 Tip |
After configuring and selecting remote storage, you can switch back to local storage only if you have not increased the connection database limit. |
|
Mangement Center Version |
NFS Version |
SSH Version |
SMB Version |
|---|---|---|---|
|
6.4 |
V3/V4 |
openssh 7.3p1 |
V2/V3 |
|
6.5 |
V3/V4 |
ciscossh 1.6.20 |
V2/V3 |
|
6.6 |
V3/V4 |
ciscossh 1.6.20 |
V2/V3 |
|
6.7 |
V3/V4 |
ciscossh 1.6.20 |
V2/V3 |
Run the following commands as a root user to enable the protocol version:
NFS—/bin/mount -t nfs '10.10.4.225':'/home/manual-check' '/mnt/remote-storage' -o 'rw,vers=4.0'
SMB—/usr/bin/mount.cifs //10.10.0.100/pyallapp-share/testing-smb /mnt/remote-storage -o username=administrator,password=******,vers=3.0
|
Step 1 |
Choose . |
|
Step 2 |
Choose Remote Storage Device. |
|
Step 3 |
Choose Local (No Remote Storage) from the Storage Type drop-down list. |
|
Step 4 |
Click Save. |
Ensure that your external remote storage system is functional and accessible from your FMC.
|
Step 1 |
Choose . |
|
Step 2 |
Click Remote Storage Device. |
|
Step 3 |
Choose NFS from the Storage Type drop-down list. |
|
Step 4 |
Add the connection information:
|
|
Step 5 |
Optionally, check the Use Advanced Options check box and enter any required command line options; see Remote Storage Management Advanced Options. |
|
Step 6 |
Under System Usage:
|
|
Step 7 |
To test the settings, click Test. |
|
Step 8 |
Click Save. |
Ensure that your external remote storage system is functional and accessible from your FMC:
The system recognizes top-level SMB shares, not full file paths. You must use Windows to share the exact directory you want to use.
Make sure the Windows user you will use to access the SMB share from the FMC has ownership of and read/change access to the share location.
To ensure security, you should install SMB 2.0 or greater.
|
Step 1 |
Choose . |
|
Step 2 |
Click Remote Storage Device. |
|
Step 3 |
Choose SMB from the Storage Type drop-down list. |
|
Step 4 |
Add the connection information:
|
|
Step 5 |
Optionally, check the Use Advanced Options check box and enter any required command line options; see Remote Storage Management Advanced Options. |
|
Step 6 |
Under System Usage:
|
|
Step 7 |
To test the settings, click Test. |
|
Step 8 |
Click Save. |
Ensure that your external remote storage system is functional and accessible from your Firepower Management Center.
|
Step 1 |
Choose . |
|
Step 2 |
Click Remote Storage Device. |
|
Step 3 |
Choose SSH from the Storage Type drop-down list. |
|
Step 4 |
Add the connection information:
|
|
Step 5 |
Optionally, check the Use Advanced Options check box and enter any required command line options; see Remote Storage Management Advanced Options. |
|
Step 6 |
Under System Usage:
|
|
Step 7 |
If you want to test the settings, you must click Test. |
|
Step 8 |
Click Save. |
If you select the Network File System (NFS) protocol, Server Message Block (SMB) protocol, or SSH to use secure file transfer protocol (SFTP) to store your reports and backups, you can select the Use Advanced Options check box to use one of the mount binary options as documented in an NFS, SMB, or SSH mount main page.
If you select SMB or NFS storage type, you can specify the version number of the remote storage in the Command Line Option field using the following format:
vers=versionwhere version is the version number of SMB or NFS remote storage you want to use. For example, to select NFSv4, enter vers=4.0.
vers=3.0where you select encrypted SMBv3 to copy or save backup files from the FMC to the encrypted SMB file server.
To monitor the changes that users make and ensure that they follow your organization’s preferred standard, you can configure the system to send, via email, a detailed report of changes made over the past 24 hours. Whenever a user saves changes to the system configuration, a snapshot is taken of the changes. The change reconciliation report combines information from these snapshots to present a clear summary of recent system changes.
The following sample graphic displays a User section of an example change reconciliation report and lists both the previous value for each configuration and the value after changes. When users make multiple changes to the same configuration, the report lists summaries of each distinct change in chronological order, beginning with the most recent.
You can view changes made during the previous 24 hours.
Configure an email server to receive emailed reports of changes made to the system over a 24 hour period; see Configuring a Mail Relay Host and Notification Address for more information.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click Change Reconciliation. |
||
|
Step 3 |
Check the Enable check box. |
||
|
Step 4 |
Choose the time of day you want the system to send out the change reconciliation report from the Time to Run drop-down lists. |
||
|
Step 5 |
Enter email addresses in the Email to field.
|
||
|
Step 6 |
If you want to include policy changes, check the Include Policy Configuration check box. |
||
|
Step 7 |
If you want to include all changes over the past 24 hours, check the Show Full Change History check box. |
||
|
Step 8 |
Click Save. |
The Include Policy Configuration option controls whether the system includes records of policy changes in the change reconciliation report. This includes changes to access control, intrusion, system, health, and network discovery policies. If you do not select this option, the report will not show changes to any policies. This option is available on Firepower Management Centers only.
The Show Full Change History option controls whether the system includes records of all changes over the past 24 hours in the change reconciliation report. If you do not select this option, the report includes only a consolidated view of changes for each category.
 Note |
The change reconciliation report does not include changes to Firepower Threat Defense interfaces and routing settings. |
You can configure the Firepower System to track several policy-related changes using the comment functionality when users modify access control, intrusion, or network analysis policies.
With policy change comments enabled, administrators can quickly assess why critical policies in a deployment were modified. Optionally, you can have changes to intrusion and network analysis policies written to the audit log.
You can configure the Firepower System to prompt users for comments when they modify an access control policy, intrusion policy, or network analysis policy. You can use comments to track users’ reasons for policy changes. If you enable comments on policy changes, you can make the comment optional or mandatory. The system prompts the user for a comment when each new change to a policy is saved.
|
Step 1 |
Choose . The system configuration options appear in the left navigation panel. |
|
Step 2 |
Configure the policy comment preferences for any of the following:
|
|
Step 3 |
You have the following choices for each policy type:
|
|
Step 4 |
Optionally for intrusion or network analysis policy comments:
|
|
Step 5 |
Click Save. |
You can limit access to the FMC by IP address and port. By default, the following ports are enabled for any IP address:
443 (HTTPS) for web interface access.
22 (SSH) for CLI access.
You can also add access to poll for SNMP information over port 161. Because SNMP is disabled by default, you must first enable SNMP before you can add SNMP access rules. For more information, see Configure SNMP Polling.
 Caution |
By default, access is not restricted. To operate in a more secure environment, consider adding access for specific IP addresses and then deleting the default any option. |
This access list does not control external database access. See Enabling External Access to the Database.
 Caution |
If you delete access for the IP address that you are currently using to connect
to the FMC, and there is no entry for “ |
To configure access lists for Classic devices, use device platform settings. See Configure Access Lists for Classic Devices.
By default, the access list includes rules for HTTPS and SSH. To add SNMP rules to the access list, you must first enable SNMP. For more information, see Configure SNMP Polling.
|
Step 1 |
Choose . |
|
Step 2 |
(Optional) Click SNMP to configure SNMP if you want to add SNMP rules to the access list. By default, SNMP is disabled; see Configure SNMP Polling. |
|
Step 3 |
Click Access List. |
|
Step 4 |
To add access for one or more IP addresses, click Add Rules. |
|
Step 5 |
In the IP Address field, enter an IP address or address range, or |
|
Step 6 |
Choose SSH, HTTPS, SNMP, or a combination of these options to specify which ports you want to enable for these IP addresses. |
|
Step 7 |
Click Add. |
|
Step 8 |
Click Save. |
The Firepower Management Center records user activity in read-only audit logs. You can review audit log data in several ways:
Use the web interface: Auditing the System.
Audit logs are presented in a standard event view where you can view, sort, and filter audit log messages based on any item in the audit view. You can easily delete and report on audit information and you can view detailed reports of the changes that users make.
Stream audit log messages to the syslog: Stream Audit Logs to Syslog..
Stream audit log messages to an HTTP server: Stream Audit Logs to an HTTP Server.
Streaming audit log data to an external server allows you to conserve space on the FMC. Note that sending audit information to an external URL may affect system performance.
Optionally, you can secure the channel for audit log streaming, enable TLS and mutual authentication using TLS certificates; see Audit Log Certificate.
Streaming to Multiple Syslog Servers
You can stream audit log data to a maximum of five syslog servers. However, if you have enabled TLS for secured audit log streaming, you can stream only to a single syslog server.
Classic devices also maintain audit logs. To stream audit logs from a Classic devices, see Stream Audit Logs from Classic Devices.
When this feature is enabled, audit log records appear in the syslog in the following format :
Date
Time
Host [Tag] Sender: User_Name@User_IP, Subsystem, Action
Where the local date, time, and originating hostname precede the bracketed optional tag, and the sending device name precedes the audit log message.
For example, if you specify a tag of FMC-AUDIT-LOG for audit log messages from your management center, a sample audit log message from your FMC could appear as follows:
Mar 01 14:45:24 localhost [FMC-AUDIT-LOG] Dev-MC7000: admin@10.1.1.2, Operations > Monitoring, Page View
If you specify a severity and facility, these values do not appear in syslog messages; instead, they tell the system that receives the syslog messages how to categorize them.
To stream audit logs from Classic devices, use device platform settings: Stream Audit Logs from Classic Devices.
Make sure the FMC can communicate with the syslog server. When you save your configuration, the system uses ICMP/ARP and TCP SYN packets to verify that the syslog server is reachable. Then, the system uses port 514/UDP to stream audit logs. If you secure the channel (optional, see Audit Log Certificate), you must manually configure port 1470 for TCP.
|
Step 1 |
Choose . |
||||||||||||
|
Step 2 |
Click Audit Log. |
||||||||||||
|
Step 3 |
Choose Enabled from the Send Audit Log to Syslog drop-down menu. |
||||||||||||
|
Step 4 |
The following fields are applicable only for audit logs sent to syslog:
|
||||||||||||
|
Step 5 |
(Optional) To test whether the IP address of the syslog servers are valid, click Test Syslog Server. The system sends the following packets to verify whether the syslog server is reachable:
|
||||||||||||
|
Step 6 |
Click Save. |
When this feature is enabled, the appliance sends audit log records to an HTTP server in the following format:
Date
Time
Host [Tag] Sender: User_Name@User_IP, Subsystem, Action
Where the local date, time, and originating hostname precede the bracketed optional tag, and the sending appliance or device name precedes the audit log message.
For example, if you specify a tag of FROMMC, a sample audit log message could appear as follows:
Mar 01 14:45:24 localhost [FROMMC] Dev-MC7000: admin@10.1.1.2, Operations > Monitoring, Page View
To stream audit logs from Classic devices, use device platform settings: Stream Audit Logs from Classic Devices.
Make sure the device can communicate with the HTTP server. Optionally, secure the channel; see Audit Log Certificate.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click Audit Log. |
||
|
Step 3 |
Optionally, in the Tag field, enter the tag name that you want to appear with the message. For example, if you want all audit log records to be
preceded with |
||
|
Step 4 |
Choose Enabled from the Send Audit Log to HTTP Server drop-down list. |
||
|
Step 5 |
In the URL to Post Audit field, designate the URL where you want to send the audit information. Enter a URL that corresponds to a Listener program that expects the HTTP POST variables as listed:
|
||
|
Step 6 |
Click Save. |
You can use Transport Layer Security (TLS) certificates to secure communications between Firepower appliances and a trusted audit log server.
For each appliance (client certificates are unique), you must generate a certificate signing request (CSR), submit it to a Certificate Authority (CA) for signing, then import the signed certificate onto the appliance.
You cannot use the FMC to import audit log certificates onto its managed devices. These certificates are unique to each appliance, and you must log into each appliance to import them locally:
For the FMC, use the local system configuration: Obtain a Signed Audit Log Client Certificate for the FMC and Import an Audit Log Client Certificate into the FMC.
For ASA FirePOWER and NGIPSv, generate a CSR with a tool like OpenSSL, then use the CLI to import the signed certificate: configure audit_cert import .
For additional security, we recommend you require mutual authentication between Firepower appliances and the audit log server. To accomplish this, load one or more certificate revocation lists (CRLs). You cannot stream audit logs to servers with revoked certificates listed in those CRLs.
Firepower supports CRLs encoded in Distinguished Encoding Rules (DER) format. Note that these are the same CRLs that the system uses to validate HTTPS client certificates for the FMC web interface.
To require valid audit log server certificates, use the FMC web interface:
For the FMC, use the local system configuration: Require Valid Audit Log Server Certificates.
For Classic devices, use device platform settings: Require Valid Audit Log Server Certificates for Classic Devices.
If you stream the audit log to a trusted HTTP server or syslog server, you can use Transport Layer Security (TLS) certificates to secure the channel between the FMC and the server. You must generate a unique client certificate for each appliance you want to audit.
To securely stream audit logs to Classic devices, see Stream Audit Logs from Classic Devices.
See ramifications of requiring client and server certificates at Audit Log Certificate.
|
Step 1 |
Obtain and install a signed client certificate on the FMC: |
|
Step 2 |
Configure the communication channel with the server to use Transport Layer Security (TLS) and enable mutual authentication. |
|
Step 3 |
Configure audit log streaming if you have not yet done so. |
 Important |
The Audit Log Certificate page is not available on a standby Firepower Management Center in a high availability setup. You cannot perform this task from a standby Firepower Management Center. |
The system generates certificate request keys in Base-64 encoded PEM format.
Keep the following in mind:
To ensure security, use a globally recognized and trusted Certificate Authority (CA) to sign your certificate.
If you will require mutual authentication between the appliance and the audit log server, the same Certificate Authority must sign both the client certificate and the server certificate.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click Audit Log Certificate. |
||
|
Step 3 |
Click Generate New CSR. |
||
|
Step 4 |
Enter a country code in the Country Name (two-letter code) field. |
||
|
Step 5 |
Enter a state or province postal abbreviation in the State or Province field. |
||
|
Step 6 |
Enter a Locality or City. |
||
|
Step 7 |
Enter an Organization name. |
||
|
Step 8 |
Enter an Organizational Unit (Department) name. |
||
|
Step 9 |
Enter the fully qualified domain name of the server for which you want to request a certificate in the Common Name field.
|
||
|
Step 10 |
Click Generate. |
||
|
Step 11 |
Open a new blank file with a text editor. |
||
|
Step 12 |
Copy the entire block of text in the certificate request,
including the
|
||
|
Step 13 |
Save the file as
|
||
|
Step 14 |
Click Close. |
Submit the certificate signing request to the certificate authority that you selected using the guidelines in the "Before You Begin" section of this procedure.
When you receive the signed certificate, import it to the appliance; see Import an Audit Log Client Certificate into the FMC.
In an FMC high availability setup, you must use the active peer.
For ASA FirePOWER and NGIPSv, use the CLI to import a signed certificate: configure audit_cert import .
Make sure you are importing the signed certificate for the correct appliance. Each certificate is unique to a specific appliance or device.
If the signing authority that generated the certificate requires you to trust an intermediate CA, be prepared to provide the necessary certificate chain (or certificate path). The CA that signed the client certificate must be the same CA that signed any intermediate certificates in the certificate chain.
|
Step 1 |
On the FMC, choose . |
|
Step 2 |
Click Audit Log Certificate. |
|
Step 3 |
Click Import Audit Client Certificate. |
|
Step 4 |
Open the client certificate in a text editor, copy the entire
block of text, including the
|
|
Step 5 |
To upload a private key, open the private key file and copy the
entire block of text, including the
|
|
Step 6 |
Open any required intermediate certificates, copy the entire block of text for each, and paste it into the Certificate Chain field. |
|
Step 7 |
Click Save. |
The system supports validating audit log server certificates using imported CRLs in Distinguished Encoding Rules (DER) format.
 Note |
If you choose to verify certificates using CRLs, the system uses the same CRLs to validate both audit log server certificates and certificates used to secure the HTTP connection between an appliance and a web browser. |
 Important |
You cannot perform this procedure on the standby Firepower Management Center in a high availablity pair. |
Understand the ramifications of requiring mutual authentication and of using certificate revocation lists (CRLs) to ensure that certificates are still valid. See Audit Log Certificate.
Obtain and import the client certificate following the steps in Securely Stream Audit Logs and the topics referenced in that procedure.
|
Step 1 |
On the FMC, choose . |
|
Step 2 |
Click Audit Log Certificate. |
|
Step 3 |
To use Transport Layer Security to securely stream the audit log to an external server, choose Enable TLS. |
|
Step 4 |
If you want to accept server certificates without verification (not recommended):
|
|
Step 5 |
To verify the certificate of the audit log server, choose Enable Mutual Authentication. |
|
Step 6 |
(If you enabled mutual authentication) To automatically recognize certificates that are no longer valid: |
|
Step 7 |
Verify that you have a valid server certificate generated by the same certificate authority that created the client certificate. |
|
Step 8 |
Click Save. |
(Optional) Set the frequency of CRL updates. See Configuring Certificate Revocation List Downloads.
You can view the audit log client certificate only for the appliance that you are logged in to. In FMC high availability pairs, you can view the certificate only on the active peer.
To view audit log certificates on Classic devices, use show audit_cert .
|
Step 1 |
Choose . |
|
Step 2 |
Click Audit Log Certificate. |
Dashboards provide you with at-a-glance views of current system status through the use of widgets: small, self-contained components that provide insight into different aspects of the Firepower System. The Firepower System is delivered with several predefined dashboard widgets.
You can configure the Firepower Management Center so that Custom Analysis widgets are enabled on the dashboard.
Use Custom Analysis dashboard widgets to create a visual representation of events based on a flexible, user-configurable query.
|
Step 1 |
Choose . |
|
Step 2 |
Click Dashboard. |
|
Step 3 |
Check the Enable Custom Analysis Widgets check box to allow users to add Custom Analysis widgets to dashboards. |
|
Step 4 |
Click Save. |
You can configure the system to resolve IP addresses automatically on the event view pages. You can also configure basic properties for DNS caching performed by the appliance. Configuring DNS caching allows you to identify IP addresses you previously resolved without performing additional lookups. This can reduce the amount of traffic on your network and speed the display of event pages when IP address resolution is enabled.
DNS resolution caching is a system-wide setting that allows the caching of previously resolved DNS lookups.
|
Step 1 |
Choose . |
|
Step 2 |
Choose DNS Cache. |
|
Step 3 |
From the DNS Resolution Caching drop-down list, choose one of the following:
|
|
Step 4 |
In the DNS Cache Timeout (in minutes) field, enter the number of minutes a DNS entry remains cached in memory before it is removed for inactivity. The default setting is 300 minutes (five hours). |
|
Step 5 |
Click Save. |
Configure a mail host if you plan to:
Email event-based reports
Email status reports for scheduled tasks
Email change reconciliation reports
Email data-pruning notifications
Use email for discovery event, impact flag, correlation event alerting, intrusion event alerting, and health event alerting
When you configure email notification, you can select an encryption method for the communication between the system and mail relay host, and can supply authentication credentials for the mail server if needed. After configuring, you can test the connection.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click Email Notification. |
||
|
Step 3 |
In the Mail Relay Host field, enter the hostname or IP address of the mail server you want to use. The mail host you enter must allow access from the appliance. |
||
|
Step 4 |
In the Port Number field, enter the port number to use on the email server. Typical ports include:
|
||
|
Step 5 |
Choose an Encryption Method:
|
||
|
Step 6 |
In the From Address field, enter the valid email address you want to use as the source email address for messages sent by the appliance. |
||
|
Step 7 |
Optionally, to supply a user name and password when connecting to the mail server, choose Use Authentication. Enter a user name in the Username field. Enter a password in the Password field. |
||
|
Step 8 |
To send a test email using the configured mail server, click Test Mail Server Settings. A message appears next to the button indicating the success or failure of the test. |
||
|
Step 9 |
Click Save. |
You can use the Language page to specify a different language for the web interface.
The language you specify here is used for the web interface for every user. You can choose from:
English
Chinese (simplified)
Chinese (traditional)
Japanese
Korean
|
Step 1 |
Choose . |
|
Step 2 |
Click Language. |
|
Step 3 |
Choose the language you want to use. |
|
Step 4 |
Click Save. |
You can use the Login Banner page to specify session, login, or custom message banners for a security appliance or shared policy.
You can use ASCII characters and carriage returns to create a custom login banner. The system does not preserve tab spacing. If your login banner is too large or causes errors, Telnet or SSH sessions can fail when the system attempts to display the banner.
To customize login banners for Classic devices, use device platform settings. See Customize the Login Banner for Classic Devices.
|
Step 1 |
Choose . |
|
Step 2 |
Choose Login Banner. |
|
Step 3 |
In the Custom Login Banner field, enter the login banner text you want to use. |
|
Step 4 |
Click Save. |
You can enable Simple Network Management Protocol (SNMP) polling. This feature supports use of versions 1, 2, and 3 of the SNMP protocol. This feature allows access to the standard management information base (MIB), which includes system details such as contact, administrative, location, service information, IP addressing and routing information, and transmission protocol usage statistics.
 Note |
When selecting SNMP versions for the SNMP protocol, note that SNMPv2 only supports read-only communities and SNMPv3 only supports read-only users. SNMPv3 also supports encryption with AES128. |
Enabling SNMP polling does not cause the system to send SNMP traps; it only makes the information in the MIBs available for polling by your network management system.
To configure SNMP polling on Classic managed devices, use the device platform settings. See Configure SNMP Polling on Classic Devices.
Add SNMP access for each computer you plan to use to poll the system. See Configure an Access List.
 Note |
The SNMP MIB contains information that could be used to attack your deployment. We recommend that you restrict your access list for SNMP access to the specific hosts that will be used to poll for the MIB. We also recommend you use SNMPv3 and use strong passwords for network management access. |
|
Step 1 |
Choose . |
||
|
Step 2 |
Click SNMP. |
||
|
Step 3 |
From the SNMP Version drop-down list, choose the SNMP version you want to use:
|
||
|
Step 4 |
Enter a Username. |
||
|
Step 5 |
Choose the protocol you want to use for authentication from the Authentication Protocol drop-down list. |
||
|
Step 6 |
Enter the password required for authentication with the SNMP server in the Authentication Password field. |
||
|
Step 7 |
Re-enter the authentication password in the Verify Password field. |
||
|
Step 8 |
Choose the privacy protocol you want to use from the Privacy Protocol list, or choose None to not use a privacy protocol. |
||
|
Step 9 |
Enter the SNMP privacy key required by the SNMP server in the Privacy Password field. |
||
|
Step 10 |
Re-enter the privacy password in the Verify Password field. |
||
|
Step 11 |
Click Add. |
||
|
Step 12 |
Click Save. |
Synchronizing the system time on your Firepower Management Center (FMC) and its managed devices is essential to successful operation of your Firepower System. We recommend that you specify NTP servers during FMC initial configuration, but you can use the information in this section to establish or change time sychronization settings after intial configuration is complete.
Use a Network Time Protocol (NTP) server to synchronize system time on the FMC and all devices. The FMC supports secure communications with NTP servers using MD5 or SHA-1 symmetric key authentication; for system security, we recommend using this feature.
The FMC can also be configured to connect solely with authenticated NTP servers; using this option improves security in a mixed-authentication environment, or when migrating your system to different NTP servers. It is redundant to use this setting in an environment where all reachable NTP servers are authenticated.
 Note |
If you specified an NTP server for the FMC during initial configuration, the connection with that NTP server is not secured. You must edit the configuration for that connection to specify MD5 or SHA-1 keys. |
 Caution |
Unintended consequences can occur when time is not synchronized between the FMC and managed devices. |
To synchronize time on FMC and managed devices, see:
Recommended: Synchronize Time on the FMC with an NTP Server
This topic provides instructions for configuring your FMC to synchronize with an NTP server or servers and includes links to instructions on configuring managed devices to synchronize with the same NTP server or servers.
Otherwise: Synchronize Time Without Access to a Network NTP Server
This topic provides instructions for setting the time on your FMC, configuring your FMC to serve as an NTP server, and links to instructions on configuring managed devices to synchronize with the FMC NTP server.
Time synchronization among all of the components of your system is critically important.
The best way to ensure proper time synchronization between FMC and all managed devices is to use an NTP server on your network.
The FMC supports NTPv4.
You must have Admin or Network Admin privileges to do this procedure.
Note the following:
If your FMC and managed devices cannot access a network NTP server, do not use this procedure. Instead, see Synchronize Time Without Access to a Network NTP Server.
Do not specify an untrusted NTP server.
If you plan to establish a secure connection with an NTP server (recommended for system security), obtain an SHA-1 or MD5 key number and value configured on that NTP server.
Connections to NTP servers do not use configured proxy settings.
Firepower 4100 Series devices and Firepower 9300 devices cannot use this procedure to set the system time. Instead, configure those devices to use the same NTP server(s) that you configure using this procedure. For instructions, see the documentation for your hardware model.
 Caution |
If the FMC is rebooted and your DHCP server sets an NTP server record different than the one you specify here, the DHCP-provided NTP server will be used instead. To avoid this situation, configure your DHCP server to use the same NTP server. |
|
Step 1 |
Choose . |
|
Step 2 |
Click Time Synchronization. |
|
Step 3 |
If Serve Time via NTP is Enabled, choose Disabled to disable the FMC as an NTP server. |
|
Step 4 |
For the Set My Clock option, choose Via NTP. |
|
Step 5 |
Click Add. |
|
Step 6 |
In the Add NTP Server dialog box, enter the host name or IPv4 or IPv6 address of an NTP server. |
|
Step 7 |
(Optional) To secure communication between your FMC and the NTP server:
|
|
Step 8 |
Click Add. |
|
Step 9 |
To add more NTP servers, repeat Steps 5 through 8. |
|
Step 10 |
(Optional) To force the FMC to use only an NTP server that successfully authenticates, check the Use the authenticated NTP server only check box. |
|
Step 11 |
Click Save. |
Set managed devices to synchronize with the same NTP server or servers:
Configure device platform settings: Configure NTP Time Synchronization for Threat Defense and Synchronize Time on Classic Devices with an NTP Server.
Note that even if you force the FMC to make a secure connection with an NTP server (Use the authenticated NTP server only), device connections to that server do not use authentication.
Deploy configuration changes; see Deploy Configuration Changes.
If your devices cannot directly reach the network NTP server, or your organization does not have a network NTP server, a physical-hardware FMC can serve as an NTP server.
 Important |
|
To change the time manually after configuring the FMC as an NTP server, you must disable the NTP option, change the time manually, and then re-enable the NTP option.
|
Step 1 |
Manually set the system time on the FMC:
|
|
Step 2 |
Set the FMC to serve as an NTP server:
|
|
Step 3 |
Set managed devices to synchronize with the FMC NTP server:
For instructions:
|
Your Firepower Management Center and its managed devices are heavily dependent on accurate time. The system clock is a system facility that maintains the time of the Firepower System. The system clock is set to Universal Coordinated Time (UTC), which is the primary time standard by which the world regulates clocks and time.
DO NOT ATTEMPT TO CHANGE THE SYSTEM TIME. Changing the system time zone from UTC is NOT supported, and doing so will require you to reimage the device to recover from an unsupported state.
If you configure the FMC to serve time using NTP, and then later disable it, the NTP service on managed devices still attempts to synchronize time with the FMC. You must update and redeploy any applicable platform settings policies to establish a new time source.
To change the time manually after configuring the Firepower Management Center as an NTP server, you must disable the NTP option, change the time manually, and then re-enable the NTP option.
Time settings are displayed on most pages in local time using the time zone you set on the Time Zone page in User Preferences (the default is America/New York), but are stored on the appliance using UTC time.
 Restriction |
The Time Zone function (in User Preferences) assumes that the default system clock is set to UTC time. DO NOT ATTEMPT TO CHANGE THE SYSTEM TIME. Be advised that changing the system time from UTC is NOT supported, and doing so will require you to reimage the device to recover from an unsupported state. |
|
Step 1 |
Choose . |
|
Step 2 |
Click Time. The current time is displayed using the time zone specified for your account in User Preferences. If your appliance uses an NTP server: For information about the table entries, see NTP Server Status. |
If you are synchronizing time from an NTP server, you can view connection status on the Time page (choose System > Configuration).
|
Column |
Description |
|---|---|
|
NTP Server |
The IP address or name of the configured NTP server. |
|
Status |
The status of the NTP server time synchronization:
|
|
Authentication |
The authentication status for communication between the FMC and the NTP server:
If authentication has been configured, the system displays the key number and key type (SHA-1 or MD5) following the status value. For example: bad, key 2, MD5. |
|
Offset |
The number of milliseconds of difference between the time on the appliance and the configured NTP server. Negative values indicate that the appliance is behind the NTP server, and positive values indicate that it is ahead. |
|
Last Update |
The number of seconds that have elapsed since the time was last synchronized with the NTP server. The NTP daemon automatically adjusts the synchronization times based on a number of conditions. For example, if you see larger update times such as 300 seconds, that indicates that the time is relatively stable and the NTP daemon has determined that it does not need to use a lower update increment. |
Global User Configuration settings affect all users on the Firepower Management Center. Configure these settings on the User Configuration page ():
Password Reuse Limit: The number of passwords in a user’s most recent history that cannot be reused. This limit applies to web interface access
for all users. For the admin user, this applies to CLI access as well; the system maintains separate password lists for each form of access. Setting the
limit to zero (the default) places no restrictions on password reuse. See Set Password Reuse Limit.
Track Successful Logins: The number of days that the system tracks successful logins to the Firepower Management Center, per user, per access method (web interface or CLI). When users log in, the system displays their successful login count for the interface being used. When Track Successful Logins is set to zero (the default), the system does not track or report successful login activity. See Track Successful Logins.
Max Number of Login Failures: The number of times in a row that users can enter incorrect web interface login credentials before the system temporarily blocks the account from access for a configurable time period. If a user continues login attempts while the temporary lockout is in force:
The system refuses access for that account (even with a valid password) without informing the user that a temporary lockout is in force.
The system continues to increment the failed login count for that account with each login attempt.
If the user exceeds the Maximum Number of Failed Logins configured for that account on the individual User Configuration page, the account is locked out until an admin user reactivates it.
Set Time in Minutes to Temporarily Lockout Users: The duration in minutes for a temporary web interface user lockout if Max Number of Failed Logins is non-zero.
Max Concurrent Sessions Allowed: The number of sessions of a particular type (read-only or read/write) that can be open at the same time. The type of session is determined by the roles assigned to a user. If a user is assigned only read-only roles, that user's session is counted toward the (Read Only) session limit. If a user has any roles with write privileges, the session is counted toward the Read/Write session limit. For example, if a user is assigned the Admin role and the Maximum sessions for users with Read/Write privileges/CLI users is set to 5, the user will not be allowed to log in if there are already five other users logged in that have read/write privileges.
 Note |
Predefined user roles and custom user roles that the system considers read-only for the purposes of concurrent session limits, are labeled with (Read Only) in the role name on the and the . If a user role does not contain (Read Only) in the role name, the system considers the role to be read/write. The system automatically applies (Read Only) to roles that meet the required criteria. You cannot make a role read-only by adding that text string manually to the role name. |
For each type of session, you can set a maximum limit ranging from 1 to 1024. When Max Concurrent Sessions Allowed is set to zero (the default), the number of concurrent sessions is unlimited.
If you change the concurrent session limit to a value more restrictive, the system will not close any currently open sessions; it will, however, prevent new sessions beyond the number specified from being opened.
If you enable the Password Reuse Limit, the system keeps encrypted password histories for FMC users. Users cannot reuse passwords in their histories. You can specify the number of stored passwords for each user, per access method (web interface or CLI). A user's current password counts towards this number. If you lower the limit, the system deletes older passwords from the history. Increasing the limit does not restore deleted passwords.
|
Step 1 |
Choose . |
|
Step 2 |
Click User Configuration. |
|
Step 3 |
Set the Password Reuse Limit to the number of passwords you want to maintain in the history (maximum 256). To disable password reuse checking, enter 0. |
|
Step 4 |
Click Save. |
Use this procedure to enable tracking successful logins for each user for a specified number of days. When this tracking is enabled, the system displays the successful login count when users log into the web interface or the CLI.
 Note |
If you lower the number of days, the system deletes records of older logins. If you then increase the limit, the system does not restore the count from those days. In that case, the reported number of successful logins may be temporarily lower than the actual number. |
|
Step 1 |
Choose . |
|
Step 2 |
Click User Configuration. |
|
Step 3 |
Set Track Successful Login Days to the number of days to track successful logins (maximum 365). To disable login tracking, enter 0. |
|
Step 4 |
Click Save. |
Enable the temporary timed lockout feature by specifying the number of failed login attempts in a row that the system allows before the lockout goes into effect.
|
Step 1 |
Choose . |
|
Step 2 |
Click User Configuration. |
|
Step 3 |
Set the Max Number of Login Failures to the maximum number of consecutive failed login attempts before the user is temporarily locked out. To disable the temporary lockout, enter zero. |
|
Step 4 |
Set the Time in Minutes to Temporarily Lockout Users to the number of minutes to lock out users who have triggered a temporary lockout. When this value is zero, users do not have to wait to retry to log in, even if the Max Number of Login Failures is non-zero. |
|
Step 5 |
Click Save. |
You can specify the maximum number of sessions of a particular type (read-only or read/write) that can be open at the same time. The type of session is determined by the roles assigned to a user. If a user is assigned only read-only roles, that user's session is counted toward the Read Only session limit. If a user has any roles with write privileges, the session is counted toward the Read/Write session limit.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click User Configuration. |
||
|
Step 3 |
For each type of session (Read Only and Read/Write), set the Max Concurrent Sessions Allowed to the maximum number of sessions of that type that can be open at the same time. To apply no limits on concurrent users by session type, enter zero.
|
||
|
Step 4 |
Click Save. |
Unattended login sessions may be security risks. You can configure the amount of idle time before a user’s login session times out due to inactivity.
Note that you can exempt specific web interface users from timeout, for scenarios where you plan to passively, securely monitor the system for long periods of time. Users with the Administrator role, whose complete access to menu options poses an extra risk if compromised, cannot be made exempt from session timeouts.
To configure session timeouts for Classic devices, use device platform settings. See Configure Session Timeouts for Classic Devices.
|
Step 1 |
Choose . |
|
Step 2 |
Click CLI Timeout. |
|
Step 3 |
Configure session timeouts:
|
|
Step 4 |
Click Save. |
The Firepower System automatically maps vulnerabilities to a host IP address for any application protocol traffic received or sent from that address, when the server has an application ID in the discovery event database and the packet header for the traffic includes a vendor and version.
For any servers which do not include vendor or version information in their packets, you can configure whether the system associates vulnerabilities with server traffic for these vendor and versionless servers.
For example, a host serves SMTP traffic that does not have a vendor or version in the header. If you enable the SMTP server on the Vulnerability Mapping page of a system configuration, then save that configuration to the Firepower Management Center managing the device that detects the traffic, all vulnerabilities associated with SMTP servers are added to the host profile for the host.
Although detectors collect server information and add it to host profiles, the application protocol detectors will not be used for vulnerability mapping, because you cannot specify a vendor or version for a custom application protocol detector and cannot select the server for vulnerability mapping.
This procedure requires any Smart License or the Protection classic license.
|
Step 1 |
Choose . |
||
|
Step 2 |
Choose Vulnerability Mapping. |
||
|
Step 3 |
You have the following choices:
|
||
|
Step 4 |
Click Save. |
You can use a Linux system console for remote access on supported systems via either the VGA port (which is the default) or the serial port on the physical appliance. Use the Console Configuration page to choose the option most suitable to the physical layout of your organization’s Firepower deployment.
On supported physical-hardware-based Firepower systems, you can use Lights-Out Management (LOM) on a Serial Over LAN (SOL) connection to remotely monitor or manage the system without logging into the management interface of the system. You can perform limited tasks, such as viewing the chassis serial number or monitoring such conditions as fan speed and temperature, using a command line interface on an out-of-band management connection. The cable connection to support LOM varies by FMC model:
For FMC models MC1600, MC2600, and MC4600, use a connection with the CIMC port to support LOM. See the Cisco Firepower Managemenet Center 1600, 2600, and 4600 Getting Started Guide for more information.
For all other FMC hardware models, use a connection with the default (eth0) management port to support LOM. See the Cisco Firepower Management Center Getting Started Guide for your hardware model.
You must enable LOM for both the system and the user you want to manage the system. After you enable the system and the user, you use a third-party Intelligent Platform Management Interface (IPMI) utility to access and manage your system.
You must be an Admin user to perform this procedure.
Disable Spanning Tree Protocol (STP) on any third-party switching equipment connected to the device’s management interface.
If you plan to enable Lights-Out Management see the Getting Started Guide for your appliance for information about installing and using an Intelligent Platform Management Interface (IPMI) utility.
|
Step 1 |
Choose . |
||
|
Step 2 |
Click Console Configuration. |
||
|
Step 3 |
Choose a remote console access option:
|
||
|
Step 4 |
To configure LOM via SOL:
|
||
|
Step 5 |
Click Save. |
||
|
Step 6 |
The system displays the following warning: "You will have to reboot your system for these changes to take effect." Click OK to reboot now or Cancel to reboot later. |
If you configured serial access, be sure the rear-panel serial port is connected to a local computer, terminal server, or other device that can support remote serial access over ethernet as described in the Getting Started Guide for your FMC model.
If you configured Lights-Out Management, enable a Lights-Out Management user; see Lights-Out Management User Access Configuration.
You must explicitly grant Lights-Out Management permissions to users who will use the feature. LOM users also have the following restrictions:
You must assign the Administrator role to the user.
The username may have up to 16 alphanumeric characters. Hyphens and longer user names are not supported for LOM users.
A user’s LOM password is the same as that user’s system password. The password must comply with the requirements described in User Passwords. Cisco recommends that you use a complex, non-dictionary-based password of the maximum supported length for your appliance and change it every three months.
Physical Firepower Management Centers can have up to 13 LOM users.
Note that if you deactivate, then reactivate, a user with LOM while a
that user is logged in, or restore a user from a backup during that user’s login
session, that user may need to log back into the web interface to regain access to
impitool commands.
You must be an Admin user to perform this procedure.
Use this task to grant LOM access to an existing user. To grant LOM access to a new user, see Add an Internal User.
|
Step 1 |
Choose . |
|
Step 2 |
To grant LOM user access to an existing user, click Edit ( |
|
Step 3 |
Under User Configuration, enable the Administrator role. |
|
Step 4 |
Check the Allow Lights-Out Management Access check box. |
|
Step 5 |
Click Save. |
You use a third-party IPMI utility on your computer to create a Serial Over LAN connection to the appliance. If your computer uses a Linux-like or Mac environment, use IPMItool; for Windows environments, you can use IPMIutil or IPMItool, depending on your Windows version.
 Note |
Cisco recommends using IPMItool version 1.8.12 or greater. |
IPMItool is standard with many distributions and is ready to use.
You must install IPMItool on a Mac. First, confirm that your Mac has Apple's XCode Developer tools installed, making sure that the optional components for command line development are installed (UNIX Development and System Tools in newer versions, or Command Line Support in older versions). Then you can install macports and the IPMItool. Use your favorite search engine for more information or try these sites:
https://developer.apple.com/technologies/tools/
http://www.macports.org/
http://github.com/ipmitool/ipmitool/
For Windows Versions 10 and greater with Windows Subsystem for Linux (WSL) enabled, as well as some older versions of Windows Server, you can use IPMItool. Otherwise, you must compile IPMIutil on your Windows system; you can use IPMIutil itself to compile. Use your favorite search engine for more information or try this site:
http://ipmiutil.sourceforge.net/man.html#ipmiutil
Commands used for IPMI utilities are composed of segments as in the following example for IPMItool on Mac:
ipmitool -I lanplus -H IP_address -U user_name command
where:
ipmitool invokes the utility.
-I lanplus specifies to use an
encrypted IPMI v2.0 RMCP+ LAN Interface for the session.
-H
IP_address indicates the IP address you have
configured for Lights-Out Management on the appliance you want to
access.
-U
user_name is the name of an authorized remote
session user.
command is the name of the command you want to
use.
 Note |
Cisco recommends using IPMItool version 1.8.12 or greater. |
The same command for IMPIutil on Windows looks like this:
ipmiutil command -V 4 -J 3 -N IP_address -Uuser_name
This command connects you to the command line on the appliance where you can log in as if you were physically present at the appliance. You may be prompted to enter a password.
You must be an Admin user with LOM access to perform this procedure.
|
Using IPMItool, enter the following command, and a password if prompted: |
You must be an Admin user with LOM access to perform this procedure.
|
Using IPMIutil, enter the following command, and a password if prompted: |
Lights-Out Management (LOM) provides the ability to perform a limited set of actions over an SOL connection on the default
(eth0) management interface without the need to log into the system. You use the command to create a SOL connection followed by
one of the LOM commands. After the command is completed, the connection ends.
 Caution |
In rare cases, if your computer is on a different subnet than the system's management interface and the system is configured for DHCP, attempting to access LOM features can fail. If this occurs, you can either disable and then re-enable LOM on the system, or use a computer on the same subnet as the system to ping its management interface. You should then be able to use LOM. |
 Caution |
Cisco is aware of a vulnerability inherent in the Intelligent Platform Management Interface (IPMI) standard (CVE-2013-4786). Enabling Lights-Out Management (LOM) on an system exposes this vulnerability. To mitigate this vulnerability, deploy your systems on a secure management network accessible only to trusted users and use a complex, non-dictionary-based password of the maximum supported length for your system and change it every three months. To prevent exposure to this vulnerability, do not enable LOM. |
If all attempts to access your system have failed, you can use LOM to restart your system remotely. Note that if a system is restarted while the SOL connection is active, the LOM session may disconnect or time out.
 Caution |
Do not restart your system unless it does not respond to any other attempts to restart. Remotely restarting does not gracefully reboot the system and you may lose data. |
|
IPMItool |
IPMIutil |
Description |
|---|---|---|
|
(not applicable) |
|
Enables admin privileges for the IPMI session |
|
|
|
Enables encryption for the IPMI session |
|
|
|
Indicates the LOM IP address or hostname for the FMC |
|
|
|
Indicates the username of an authorized LOM account |
|
|
|
Starts the SOL session |
|
|
|
Ends the SOL session |
|
|
|
Restarts the appliance |
|
|
|
Powers up the appliance |
|
|
|
Powers down the appliance |
|
|
|
Displays appliance information, such as fan speeds and temperatures |
For example, to display a list of appliance information, the IPMItool command is:
ipmitool -I lanplus -H IP_address -U user_name sdr
 Note |
Cisco recommends using IPMItool version 1.8.12 or greater. |
The same command with the IPMIutil utility is:
ipmiutil sensor -V 4 -J 3 -N IP_address -U user_name
You must be an Admin user with LOM access to perform this procedure.
|
Enter the following command for IPMItool and a password if prompted: |
You must be an Admin user with LOM access to perform this procedure.
|
Enter the following command for IPMIutil and a password if prompted: |
The Firepower REST API provides a lightweight interface for third-party applications to view and manage appliance configuration using a REST client and standard HTTP methods. For more information on the Firepower REST API, see the Firepower REST API Quick Start Guide.
By default, the Firepower Management Center allows requests from applications using the REST API. You can configure the Firepower Management Center to block this access.
 Note |
In deployments using the FMC high availability, this feature is available only in the active FMC. |
|
Step 1 |
Choose the Cog ( |
|
Step 2 |
Click REST API Preferences. |
|
Step 3 |
To enable or disable REST API access to the FMC, check or uncheck the Enable REST API check box. |
|
Step 4 |
Click Save. |
|
Step 5 |
Access the REST API Explorer at:
|
VMware Tools is a suite of performance-enhancing utilities intended for virtual machines. These utilities allow you to make full use of the convenient features of VMware products. Firepower virtual appliances running on VMware support the following plugins:
guestInfo
powerOps
timeSync
vmbackup
You can also enable VMware Tools on all supported versions of ESXi. For a list of supported versions, see the Cisco Firepower NGIPSv Quick Start Guide for VMware. For information on the full functionality of VMware Tools, see the VMware website (http://www.vmware.com/).
|
Smart License |
Classic License |
Supported Devices |
Supported Domains |
Access |
|---|---|---|---|---|
|
Any |
Any |
Firepower Management Center |
Global only |
Admin |
Because NGIPSv does not have a web interface, you must use the CLI to enable VMware Tools on that platform; see the Cisco Firepower NGIPSv Quick Start Guide for VMware.
|
Step 1 |
Choose . |
|
Step 2 |
Click VMware Tools. |
|
Step 3 |
Click Enable VMware Tools. |
|
Step 4 |
Click Save. |
By default, in order to improve Firepower products, Cisco collects non-personally-identifiable usage data, including but not limited to page interactions, browser versions, product versions, user location, and management IP addresses or hostnames of your Firepower Management Center appliances.
Data collection begins after you accept the End User License Agreement. If you do not want Cisco to continue to collect this data, you can opt out using the following procedure.
|
Step 1 |
Choose System > Configuration. |
|
Step 2 |
Click Web Analytics. |
|
Step 3 |
Make your choice and click Save. |
(Optional) Determine whether to share data via the Cisco Success Network.
|
Feature |
Version |
Details |
||
|---|---|---|---|---|
|
Subject Alternative Name (SAN) |
6.6 |
When creating an HTTPS certificate for the FMC, you can specify SAN fields. We recommend you use SAN if the certificate secures multiple domain names or IP addresses. For more information about SAN, see RFC 5280, section 4.2.1.6. New/modified screens:
Supported platforms: FMC |
||
|
HTTPS Certificates |
6.6 |
The default HTTPS server certificate provided with the system now expires in 800 days. If your appliance uses a default certificate that was generated before you upgraded to Version 6.6, the certificate lifetime varies depending on the Firepower version being used when the certificate was generated. See Default HTTPS Server Certificates for more information. New/modified screens: None. Supported platforms: Hardware FMCs. |
||
|
Secure NTP |
6.5 |
The FMC supports secure communications with NTP servers using SHA1 or MD5 symmetric key authentication. New/modified screens:
Supported platforms: FMC |
||
|
Web analytics |
6.5 |
Web analytics data collection begins after you accept the EULA. As previously, you can opt not to continue to share data. See (Optional) Opt Out of Web Analytics Tracking. |
||
|
Automatic CLI access for the FMC |
6.5 |
When you use SSH to log into the FMC, you automatically access the CLI. Although strongly discouraged, you can then use the CLI expert command to access the Linux shell.
|
||
|
Configurable session limits for read-only and read/write access |
6.5 |
Added the Max Concurrent Sessions Allowed setting. This setting allows the administrator to specify the maximum number of sessions of a particular type (read-only or read/write) that can be open at the same time.
New/modified screens:
Supported Platforms: FMC |
||
|
Ability to disable Duplicate Address Detection (DAD) on management interfaces |
6.4 |
When you enable IPv6, you can disable DAD. You might want to disable DAD because the use of DAD opens up the possibility of denial of service attacks. If you disable this setting, you need check manually that this interface is not using an already-assigned address. New/modified screens: dialog box > IPv6 DAD check box Supported Platforms: FMC |
||
|
Ability to disable ICMPv6 Echo Reply and Destination Unreachable messages on management interfaces |
6.4 |
When you enable IPv6, you can now disable ICMPv6 Echo Reply and Destination Unreachable messages. You might want to disable these packets to guard against potential denial of service attacks. Disabling Echo Reply packets means you cannot use IPv6 ping to the device management interfaces for testing purposes. New/modified screens:
New/modified commands: configure network ipv6 destination-unreachable , configure network ipv6 echo-reply Supported Platforms: FMC (web interface only), Firepower Threat Defense (CLI only), ASA FirePOWER module (CLI only), NGIPSv (CLI only) |
||
|
Global User Configuration Settings |
6.3 |
Added the Track Successful Logins setting. The system can track the number of successful logins each FMC account has performed within a selected number of days. When this feature is enabled, on log in users see a message reporting how many times they have successfully logged in to the system in the past configured number of days. (Applies to web interface as well as shell/CLI access.) Added the Password Reuse Limit setting. The system can track the password history for each account for a configurable number of previous passwords. The system prevents all users from re-using passwords that appear in that history. (Applies to web interface as well as shell/CLI access.) Added the Max Number of Login Failures and Set Time in Minutes to Temporarily Lockout Users settings. These allow the administrator to limit the number of times in a row a user can enter incorrect web interface login credentials before the system temporarily blocks the account for a configurable period of time. New screen: Supported Platforms: FMC |
||
|
HTTPS Certificates |
6.3 |
The default HTTPS server certificate provided with the system now expires in three years. If your appliance uses a default server certificate that was generated before you upgraded to Version 6.3, the server certificate will expire 20 years from when it was first generated. If you are using the default HTTPS server certificate the system now provides the ability to renew it. New/modified screens: page > Renew HTTPS Certificate. Supported platforms: FMC |
||
|
Ability to enable and disable CLI access for the FMC |
6.3 |
New/Modified screens: New check box available to administrators in FMC web interface: Enable CLI Access on the > Console Configuration page.
Previous to Version 6.3, there was only one setting on the Console Configuration page, and it applied to physical devices only. So the Console Configuration page was not available on virtual FMCs. With the addition of this new option, the Console Configuration page now appears on virtual FMCs as well as physical. However, for virtual FMCs, this check box is the only thing that appears on the page. Supported platforms: FMC |