|
FDM support for the Firepower 4100/9300.
|
You can now use FDM to configure FTD on the Firepower 4100/9300. Only native instances are supported; container instances are not supported.
|
|
FDM support for FTDv for the Microsoft Azure Cloud.
|
You can configure on FTDv for the Microsoft Azure Cloud using FDM.
|
|
Support for the Firepower 1150.
|
We introduced the FTD for the Firepower 1150.
|
|
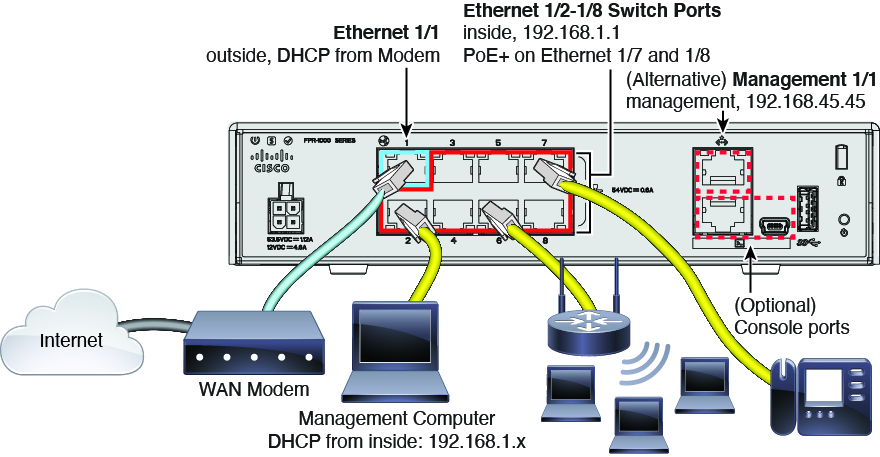
Firepower 1010 hardware switch support, PoE+ support.
|
The Firepower 1010 supports setting each Ethernet interface to be a
switch port or a regular firewall interface. Assign each switch port
to a VLAN interface. The Firepower 1010 also supports Power over
Ethernet+ (PoE+) on Ethernet1/7 and Ethernet 1/8.
The default configuration now sets Ethernet1/1 as outside, and
Ethernet1/2 through 1/8 as switch ports on the inside VLAN1
interface. Upgrading to version 6.5 retains the existing interface
configuration.
|
|
Interface scan and replace.
|
An interface scan detects any added, removed, or restored interfaces
on the chassis. You can also replace an old interface with a new
interface in the configuration, making interface changes
seamless.
|
|
Improved interfaces display.
|
The page has been reorganized. There are now separate
tabs for physical interfaces, bridge groups, EtherChannels, and
VLANs. For any given device model, only those tabs relevant for the
model are shown. For example, the VLANs tab is available on the
Firepower 1010 model only. In addition, the lists provide more
detailed information about the configuration and usage of each
interface.
|
|
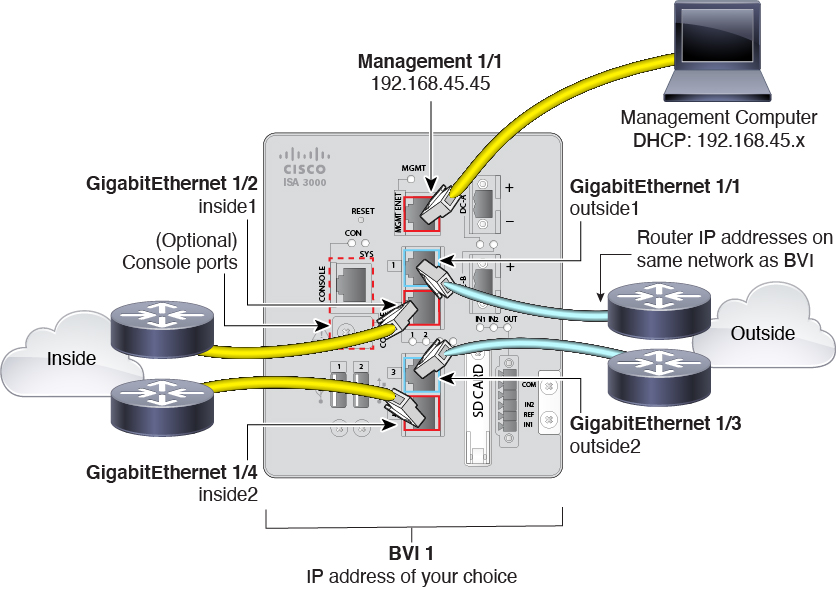
ISA 3000 new default configuration.
|
The ISA 3000 default configuration has changed so that:
-
All interfaces are bridge group members in BVI1, which is
unnamed so it does not participate in routing
-
GigabitEthernet1/1 and 1/3 are outside interfaces, and
GigabitEthernet1/2 and 1/4 are inside interfaces
-
Hardware bypass is enabled for each inside/outside pair, when
available
-
All traffic is allowed from inside to outside, and outside to
inside
Upgrading to version 6.5 retains the existing interface
configuration.
|
|
Support ends for the ASA 5515-X. The last supported release is FTD 6.4.
|
You cannot install FTD 6.5 on an ASA 5515-X. The last supported release for the ASA
5515-X is FTD 6.4.
|
|
Support for Common Industrial Protocol (CIP) and Modbus application
filtering in access control rules on Cisco ISA 3000 devices.
|
You can enable the Common Industrial Protocol (CIP) and Modbus
preprocessors on Cisco ISA 3000 devices, and filter on CIP and Modbus applications in access
control rules. All CIP application names start with “CIP,” such as
CIP Write. There is only one application for Modbus.
To enable the preprocessors, you must go into expert mode in a CLI
session (SSH or Console) and issue the sudo
/usr/local/sf/bin/enable_scada.sh {cip | modbus |
both} command. You must issue this command
after every deployment, as deployment turns off the
preprocessors.
|
|
Precision Time Protocol (PTP) configuration for ISA 3000 devices.
|
You can use FlexConfig to configure the Precision Time Protocol (PTP)
on ISA 3000 devices. PTP is a time-synchronization protocol developed to
synchronize the clocks of various devices in a packet-based network.
The protocol is designed specifically for industrial, networked
measurement and control systems.
We now allow you to include the ptp and igmp (interface mode) commands, and the global commands ptp mode e2etransparent and ptp domain , in FlexConfig objects. We also added the show ptp command to the FTD CLI.
|
|
EtherChannel (port channel) interfaces.
|
You can configure EtherChannel interfaces, which are also known as
port channels.
| Note
|
You can only add EtherChannels in FDM to the Firepower 1000 and 2100 series. The Firepower 4100/9300 supports EtherChannels, but you must perform all hardware configuration of EtherChannels in FXOS on the chassis. Firepower 4100/9300 EtherChannels appear in the FDM
Interfaces page alongside single physical interfaces.
|
We updated the page to allow the creation of EtherChannels.
|
|
Ability to reboot and shut down the system from FDM.
|
You can now reboot or shut down the system from the new Reboot/Shutdown system settings page. Previously, you needed to issue the reboot and shutdown commands through the CLI Console in FDM or from an SSH or console session. You must have Administrator privileges to use these commands.
|
|
Support for the failover command in the FDM CLI Console.
|
You can now issue the failover command in the FDM CLI Console.
|
|
Service Level Agreement (SLA) Monitor for static routes.
|
Configure Service Level Agreement (SLA) Monitor objects for use with
static routes. By using an SLA monitor, you can track the health of
a static route and automatically replace a failed route with a new
one. We added SLA Monitors to the
Objects page, and updated static routes
so you can select the SLA Monitor object.
|
|
Routing changes in Smart CLI and the FTD API.
|
This release includes some changes to routing configuration in Smart
CLI and the FTD API. In previous releases, there was a single Smart CLI template
for BGP. Now, there are separate templates for BGP (the routing
process configuration) and BGP General Settings (global settings).
In the FTD API, the paths for all methods have changed, with
“/virtualrouters” inserted in the paths, with the exception of the
new BGP general settings methods.
-
The path for static route methods was
/devices/default/routing/{parentId}/staticrouteentries, and
it is now
/devices/default/routing/virtualrouters/default/staticrouteentries.
-
BGP methods were split into two new paths:
/devices/default/routing/bgpgeneralsettings and
/devices/default/routing/virtualrouters/default/bgp.
-
OSPF paths are now
/devices/default/routing/virtualrouters/default/ospf and
/devices/default/routing/virtualrouters/default/ospfinterfacesettings.
If you are using the FTD API to configure any routing process, please examine your calls
and correct as necessary.
|
|
New URL category and reputation database.
|
The system uses a different URL database, from Cisco Talos. The new
database has some differences in URL categories. Upon upgrade, if
any access control or SSL decryption rules use categories that no
longer exist, the system will replace the category with an
appropriate new category. To make the change effective, deploy the
configuration after upgrade. The pending changes dialog will show
details about the category changes. You might want to examine your
URL filtering policies to verify that they continue to provide the
desired results.
We also added a URL lookup feature to the URL tabs in the access
control and SSL decryption policies, and on the page. You can use this feature to check which
category a particular URL is assigned to. If you disagree, there is
also a link to submit a category dispute. Both of these features
take you to an external web site, which will provide detailed
information about the URL.
|
|
Security Intelligence uses the IP address reputation for URL requests
that use IP addresses instead of hostnames.
|
If an HTTP/HTTPS request is to a URL that uses an IP address instead
of a hostname, the system looks up the IP address reputation in the
network address lists. You do not need to duplicate IP addresses in
the network and URL lists. This makes it harder for end users to use
proxies to avoid Security Intelligence reputation blocking.
|
|
Support for sending connection and high-priority intrusion, file, and
malware events to the Cisco Cloud.
|
You can send events to the Cisco cloud server. From there, various
Cisco cloud services can access the events. You can then use these
cloud applications, such as Cisco Threat Response, to analyze the
events and to evaluate threats that the device might have
encountered. When you enable this service, the device will send
connection and high-priority intrusion, file, and malware events to
the Cisco cloud.
We renamed the Cisco Threat Response item on to “Send Events to the Cisco Cloud.”
|
|
Cisco Cloud Services region support.
|
You are now asked to select the Cisco Cloud Services region when you
register with smart licensing. This region is used for Cisco Defense
Orchestrator, Cisco Threat Response, Cisco Success Network, and any
cloud feature that goes through the Cisco Cloud. If you upgrade a
registered device from a previous release, you are automatically
assigned to the US Region; you must unregister from Smart Licensing,
then reregister and select a new region, if you need to change
regions.
We added a step to the license registration process on the Smart
License page and in the initial device setup wizard. You can also
see the region on the page.
|
|
FTD REST API version 4 (v4).
|
The FTD REST API for software version 6.5 has been incremented to version 4. You must replace v1/v2/v3 in the API URLs with v4. The
v4 API includes many new resources that cover all features added in software version 6.5. Please re-evaluate all existing
calls, as changes might have been mode to the resource models you are using. To open the API Explorer, where you can view
the resources, log into FDM, then click the more options button ( ) and choose API Explorer. ) and choose API Explorer.
|
|
FTD API support for TrustSec security groups as matching criteria for
source and destination in access control rules.
|
You can use the FTD API to configure access control policy rules that use TrustSec
security groups for source or destination traffic matching criteria.
The system downloads the list of security group tags (SGTs) from
ISE. You can configure the system to listen for SXP updates to
obtain static SGT-to-IP address mappings.
You can view the list of downloaded tags using the GET
/object/securitygrouptag method, and create dynamic objects for one
or more tags using the SGTDynamicObject resource. It is the dynamic
objects that you can use in access control rules to define traffic
matching criteria based on source or destination security group.
Note that any changes you make to the ISE object or access control rules related to security group are preserved if you edit
those objects in FDM. However, you cannot see the security group criteria in an access rule if you edit the rule in FDM. If you configure security-group-based access rules using the API, please be careful when subsequently editing rules in the
access control policy using FDM.
We added or modified the following FTD API resources: AccessRule (sourceDynamicObjects and
destinationDynamicObjects attributes), IdentityServicesEngine
(subscribeToSessionDirectoryTopic and subscribeToSxpTopic
attributes), SecurityGroupTag, SGTDynamicObject.
We added source and destination security group tag and name as
columns in Event Viewer.
|
|
Configuration import/export using the FTD API.
|
You can use the FTD API to export the device configuration and to import a
configuration file. You can edit the configuration file to change
values, such as the IP addresses assigned to interfaces. Thus, you
can use import/export to create a template for new devices, so that
you can quickly apply a baseline configuration and get new devices
online more quickly. You can also use import/export to restore a
configuration after you reimage a device. Or you can simply use it
to distribute a set of network objects or other items to a group of
devices.
We added the ConfigurationImportExport resources and methods
(/action/configexport, /jobs/configexportstatus,
/action/downloadconfigfile, /action/uploadconfigfile,
/action/configfiles, /action/configimport,
/jobs/configimportstatus).
|
|
Creation and selection of custom file policies.
|
You can use the FTD API to create custom file policies, and then select these policies on access control rules using FDM.
We added the following FTD API FileAndMalwarePolicies resources: filepolicies, filetypes,
filetypecategories, ampcloudconfig, ampservers, and
ampcloudconnections.
We also removed two pre-defined policies, “Block Office Document and
PDF Upload, Block Malware Others” and “Block Office Documents
Upload, Block Malware Others.” If you are using these policies,
during upgrade they are converted to user-defined policies so that
you can edit them.
|
|
Security Intelligence DNS policy configuration using the FTD API.
|
You can configure the Security Intelligence DNS policy using the FTD API. This policy does not appear in FDM.
We added the following SecurityIntelligence resources:
domainnamefeeds, domainnamegroups, domainnamefeedcategories,
securityintelligencednspolicies.
|
|
Remote access VPN two-factor authentication using Duo LDAP.
|
You can configure Duo LDAP as the second authentication source for a remote access VPN connection profile to provide two-factor
authentication using Duo passcode, push notification, or phone call. Although you must use the FTD API to create the Duo LDAP identity source object, you can use FDM to select that object as the authentication source for the RA VPN connection profile.
We added the duoldapidentitysources resource and methods to the FTD API.
|
|
FTD API support for LDAP attribute maps used in authorizing remote
access VPN connections.
|
You can augment LDAP authorization for remote access VPN using custom LDAP attribute maps. An LDAP attribute map equates customer-specific
LDAP attribute names and values with Cisco attribute names and values. You can use these mappings to assign group policies
to users based on LDAP attribute values. You can configure these maps using the FTD API only; you cannot configure them using FDM. However, if you set these options using the API, you can subsequently edit the Active Directory identity source in FDM and your settings are preserved.
We added or modified the following FTD API object models: LdapAttributeMap, LdapAttributeMapping,
LdapAttributeToGroupPolicyMapping, LDAPRealm,
LdapToCiscoValueMapping, LdapToGroupPolicyValueMapping,
RadiusIdentitySource.
|
|
FTD API support for site-to-site VPN connection reverse route
injection and security association (SA) lifetime.
|
You can use the FTD API to enable reverse route injection for a site-to-site VPN
connection. Reverse route injection (RRI) is the ability for static
routes to be automatically inserted into the routing process for
those networks and hosts protected by a remote tunnel endpoint. By
default, static RRI, where routes are added when you configure the
connection is enabled. Dynamic RRI, where routes are inserted only
when the security association (SA) is established, and then are
deleted when the SA is torn down, is disabled. Note that dynamic RRI
is supported for IKEv2 connections only.
You can also set the security association (SA) lifetime (in seconds
or in kilobytes transmitted) for the connection. You can also set an
unlimited lifetime. The default lifetimes are 28,800 seconds (eight
hours) and 4,608,000 kilobytes (10 megabytes per second for one
hour). When the lifetime is reached, the endpoints negotiate a new
security association and secret key.
You cannot configure these features using FDM. However, if you set these options using the API, you can subsequently edit the connection profile in FDM and your settings are preserved.
We added the following attributes to the SToSConnectionProfile
resource: dynamicRRIEnabled, ipsecLifetimeInSeconds,
ipsecLifetimeInKiloBytes, ipsecLifetimeUnlimited, rriEnabled.
|
|
Support for Diffie-Hellman groups 14, 15, and 16 in IKE policies.
|
You can now configure IKEv1 policies to use DH group 14, and IKEv2
policies to use DH groups 14, 15, and 16. If you are using IKEv1,
please upgrade all your policies to DH group 14, as groups 2 and 5
will be removed in a future release. In addition, you should avoid
using DH group 24 in IKEv2 policies, and MD5 in any IKE version, as
these will also be removed in a future release.
|
|
Performance improvements when deploying changes.
|
If you add, edit, or delete access control rules, the system has been
enhanced to deploy your changes more quickly than was done in
previous releases.
For systems configured in a high availability group for failover, the
process for synchronizing the deployed changes to the standby device
has been improved so that the synchronization completes more
quickly.
|
|
Improved CPU and memory usage calculations on the System
dashboard.
|
The method for calculating CPU and memory usage has been improved so
that the information shown on the System dashboard more accurately
reflects the actual state of the device.
|
|
When upgrading to FTD 6.5, historical report data is no longer available.
|
When you upgrade an existing system to FTD 6.5, historical report data will not be available due to a
database schema change. Thus, you will not see usage data in the
dashboards for times prior to the upgrade.
|



 Feedback
Feedback