Introduction to Traffic Profiles
A traffic profile is a graph of network traffic based on connection data collected over a profiling time window (PTW). This measurement presumably represents normal network traffic. After the learning period, you can detect abnormal network traffic by evaluating new traffic against your profile.
The default PTW is one week, but you can change it to be as short as an hour or as long as several weeks. By default, traffic profiles generate statistics on connection events generated by the system over five-minute intervals. However, you can increase this sampling rate to as long as an hour.
 Tip |
Cisco recommends that the PTW include at least 100 data points. Configure your PTW and sampling rate so that your traffic profiles contain enough data to be statistically meaningful. |
The following graphic shows a traffic profile with a PTW of one day and a sampling rate of five minutes.
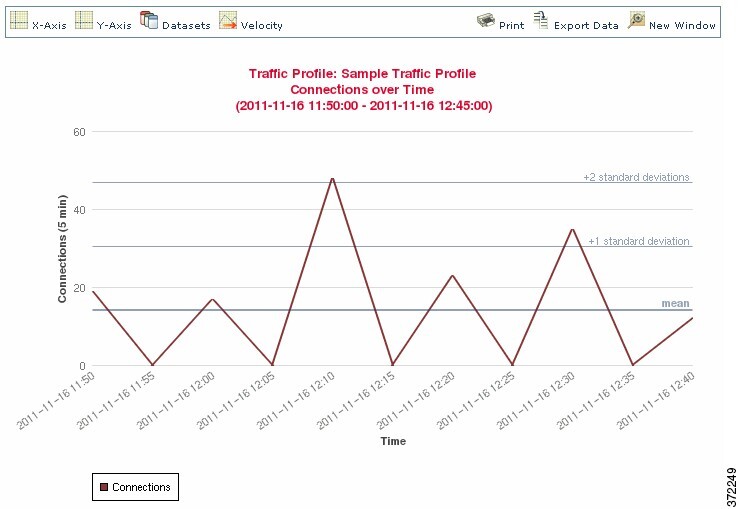
You can also set up inactive periods in traffic profile. Traffic profiles collect data during inactive periods, but do not use that data when calculating profile statistics. Traffic profile graphs plotted over time show inactive periods as a shaded region.
For example, consider a network infrastructure where all the workstations are backed up at midnight every night. The backup takes about 30 minutes and spikes the network traffic. You could configure recurring inactive period for your traffic profile to coincide with the scheduled backups.
 Note |
The system uses end-of-connection data to create connection graphs and traffic profiles. To use traffic profiles, make sure you log end-of-connection events to the Firepower Management Center database. |
Implementing Traffic Profiles
When you activate a traffic profile, the system collects and evaluates connection data for the learning period (PTW) you configured. After the learning period, the system evaluates correlation rules written against the traffic profile.
For example, you could write a rule that triggers if the amount of data traversing your network (measured in packets, KBytes, or number of connections) suddenly spikes to three standard deviations above the mean amount of traffic, which could indicate an attack or other security policy violation. Then, you could include that rule in a correlation policy to alert you of the traffic spike or to perform a remediation in response.
Targeting Traffic Profiles
Profile conditions and host profile qualifications constrain traffic profiles.
Using profile conditions, you can profile all network traffic, or you can restrict the traffic profile to monitoring a domain, subnets within or across domains, or individual hosts. In a multidomain deployment:
-
Leaf-domain administrators can profile network traffic within their leaf domains.
-
Higher-level domain administrators can profile traffic within or across domains.
Profile conditions can also constrain traffic profiles using criteria based on connection data. For example, you could set the profile conditions so that the traffic profile only profiles sessions using a specific port, protocol, or application.
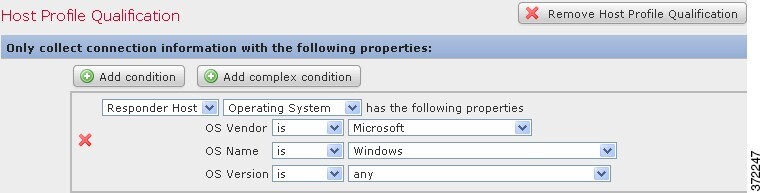
Finally, you can also constrain traffic profiles using information about the tracked hosts. This constraint is called a host profile qualification. For example, you could collect connection data only for hosts with high criticality.
 Note |
Constraining a traffic profile to a higher-level domain aggregates and profiles the same type of traffic in each of the descendant leaf domains. The system builds a separate network map for each leaf domain. In a multidomain deployment, profiling traffic across domains can have unexpected results. |
Traffic Profile Conditions
You can create simple traffic profile conditions and host profile qualifications, or you can create more elaborate constructs by combining and nesting conditions.
Conditions have three parts: a category, an operator, and a value:
-
The categories you can use depend on whether you are building traffic profile conditions or a host profile qualification.
-
The operators you can use depend on the category you choose.
-
The syntax you can use to specify a condition’s value depends on the category and operator. Sometimes you must enter the value in a text field. Other times, you can pick one or more values from a drop-down list.
For a host profile qualification, you must also specify whether you are constraining the traffic profile using information data about the initiating or responding hosts.
When your construct includes more than one condition, you must link them with an AND or an OR operator. Conditions on the same level are evaluated together:
-
The AND operator requires that all conditions on the level it controls must be met.
-
The OR operator requires that at least one of the conditions on the level it controls must be met.
Unconstrained Traffic Profile
If you want to create a traffic profile that collects data for your entire monitored network segment, you can create a very simple profile with no conditions, as shown in the following graphic.
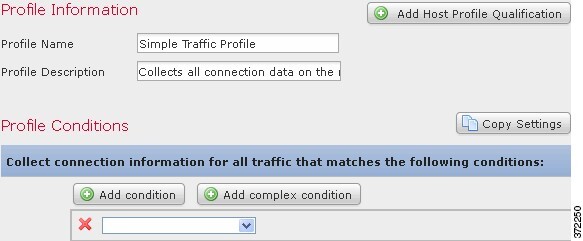
Simple Traffic Profile
If you wanted to constrain the profile and collect data only for a subnet, you can add a single condition, as shown in the following graphic.
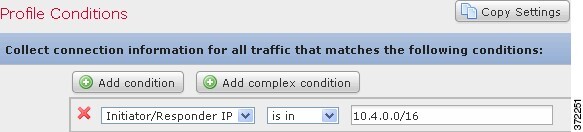
Complex Traffic Profile
The following traffic profile contains two conditions linked by AND. This means that the traffic profile collects connection data only if both conditions are true. In this example, it collects HTTP connections for all hosts with IP addresses in a specific subnet.
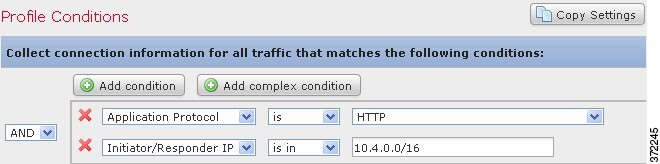
In contrast, the following traffic profile, which collects connection data for HTTP activity in either of two subnets, has three conditions, with the last constituting a complex condition.
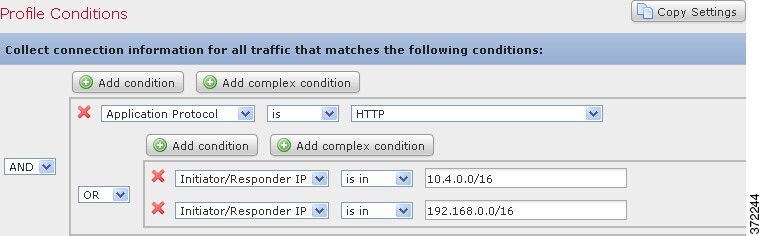
Logically, the above traffic profile is evaluated as follows:
(A and (B or C))
|
Where... |
Is the condition that states... |
|---|---|
|
|
Application Protocol Name is HTTP |
|
|
IP Address is in 10.4.0.0/16 |
|
|
IP Address is in 192.168.0.0/16 |
 )
) )
) )
) )
)
 Feedback
Feedback