ASA Cisco IOS Device Configurations
Some types of devices store their configurations in a single configuration file, such as ASA Cisco IOS. For these devices, you can view the device configuration file on Security Cloud Control and perform a variety of operations on it depending on the device.
View a Device's Configuration File
For the devices which store their entire configurations in a single configuration file, such as ASA, SSH-managed devices, and devices running Cisco IOS, you can view the configuration file using Security Cloud Control.
 Note |
SSH-managed devices and Cisco IOS Devices have read-only configurations. |
Procedure
|
Step 1 |
In the left pane, click . |
|
Step 2 |
Click the Devices tab to locate the device or the Templates tab to locate the model device. |
|
Step 3 |
Click the appropriate device type tab. |
|
Step 4 |
Select the device or model whose configuration it is you want to view. |
|
Step 5 |
In the Management pane on the right, click Configuration. |

 to expand the history pane if it is not already expanded.
to expand the history pane if it is not already expanded.
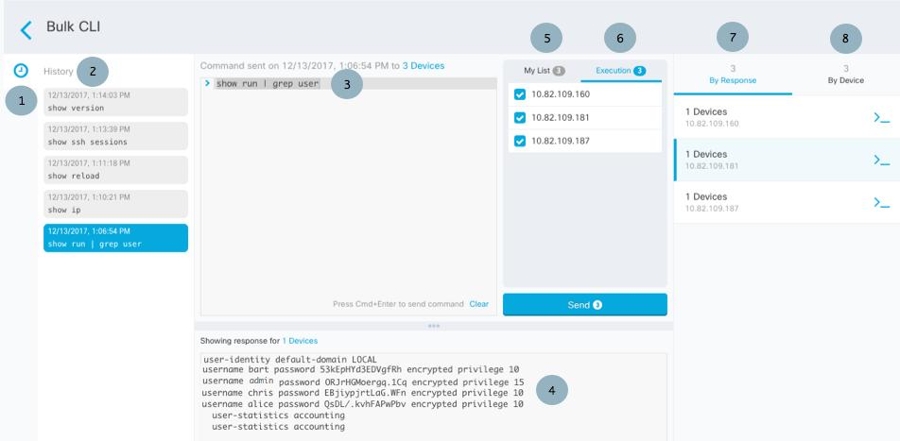



 to see what macros already exist.
to see what macros already exist.
 .
.
 . The command is now the basis for a new CLI macro.
. The command is now the basis for a new CLI macro.

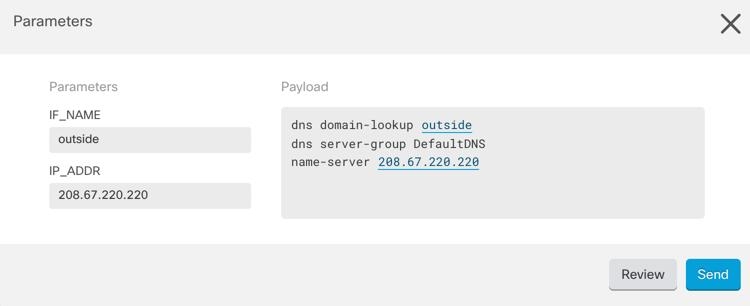

 in the CLI macro label.
in the CLI macro label.
 .
.

 . The devices affected by these changes show the status "Not Synced" in the Devices and
. The devices affected by these changes show the status "Not Synced" in the Devices and  on the details pane. Review any warnings and click
on the details pane. Review any warnings and click  in the navigation bar to view the results of the bulk deploy.
in the navigation bar to view the results of the bulk deploy.


 Feedback
Feedback