Centralized Policy
 Note |
To achieve simplification and consistency, the Cisco SD-WAN solution has been rebranded as Cisco Catalyst SD-WAN. In addition, from Cisco IOS XE SD-WAN Release 17.12.1a and Cisco Catalyst SD-WAN Release 20.12.1, the following component changes are applicable: Cisco vManage to Cisco Catalyst SD-WAN Manager, Cisco vAnalytics to Cisco Catalyst SD-WAN Analytics, Cisco vBond to Cisco Catalyst SD-WAN Validator, Cisco vSmart to Cisco Catalyst SD-WAN Controller, and Cisco Controllers to Cisco Catalyst SD-WAN Control Components. See the latest Release Notes for a comprehensive list of all the component brand name changes. While we transition to the new names, some inconsistencies might be present in the documentation set because of a phased approach to the user interface updates of the software product. |
The topics in this section provide overview information about the different types of centralized policies, the components of centralized policies, and how to configure centralized policies using Cisco SD-WAN Manager or the CLI.
Configure Centralized Policy Based on Prefixes and IP Headers
A centralized data policy based on source and destination prefixes and on headers in IP packets consists of a series of numbered (ordered) sequences of match-action pair that are evaluated in order, from lowest sequence number to highest sequence number. When a packet matches one of the match conditions, the associated action is taken and policy evaluation on that packets stops. Keep this in mind as you design your policies to ensure that the desired actions are taken on the items subject to policy.
If a packet matches no parameters in any of the sequences in the policy configuration, it is dropped and discarded by default.
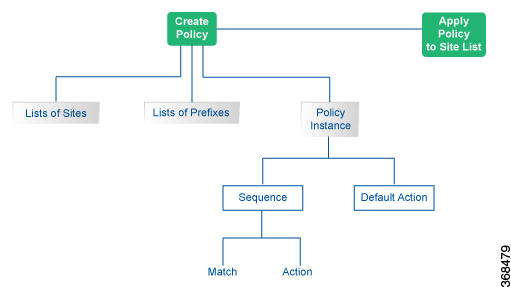
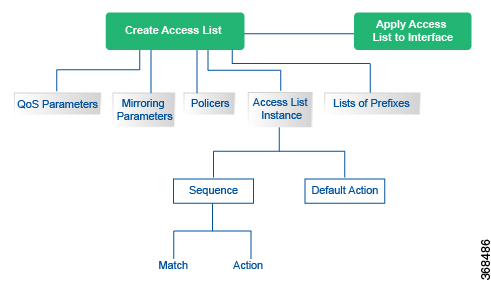
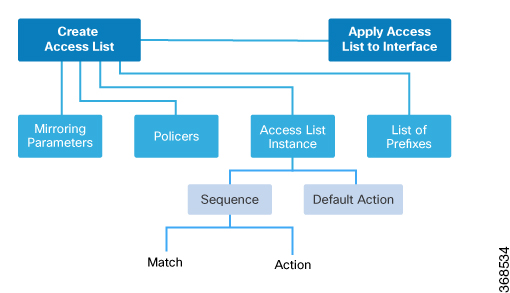
Configuration Components
The following figure illustrates the configuration components for a centralized data policy:
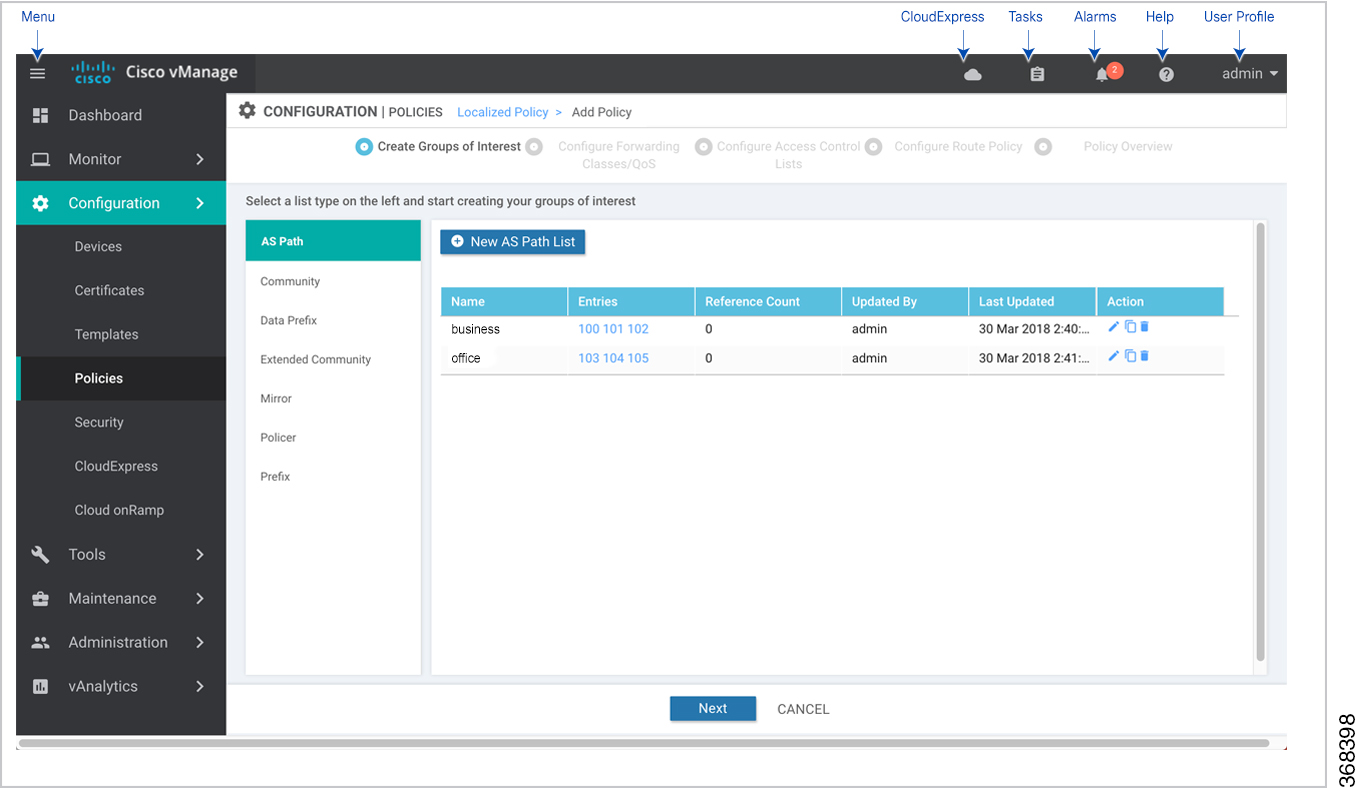
Start the Policy Configuration Wizard
To start the policy configuration wizard:
Procedure
|
Step 1 |
In Cisco SD-WAN Manager, select the screen. |
|
Step 2 |
ClickCentralized Policy. |
|
Step 3 |
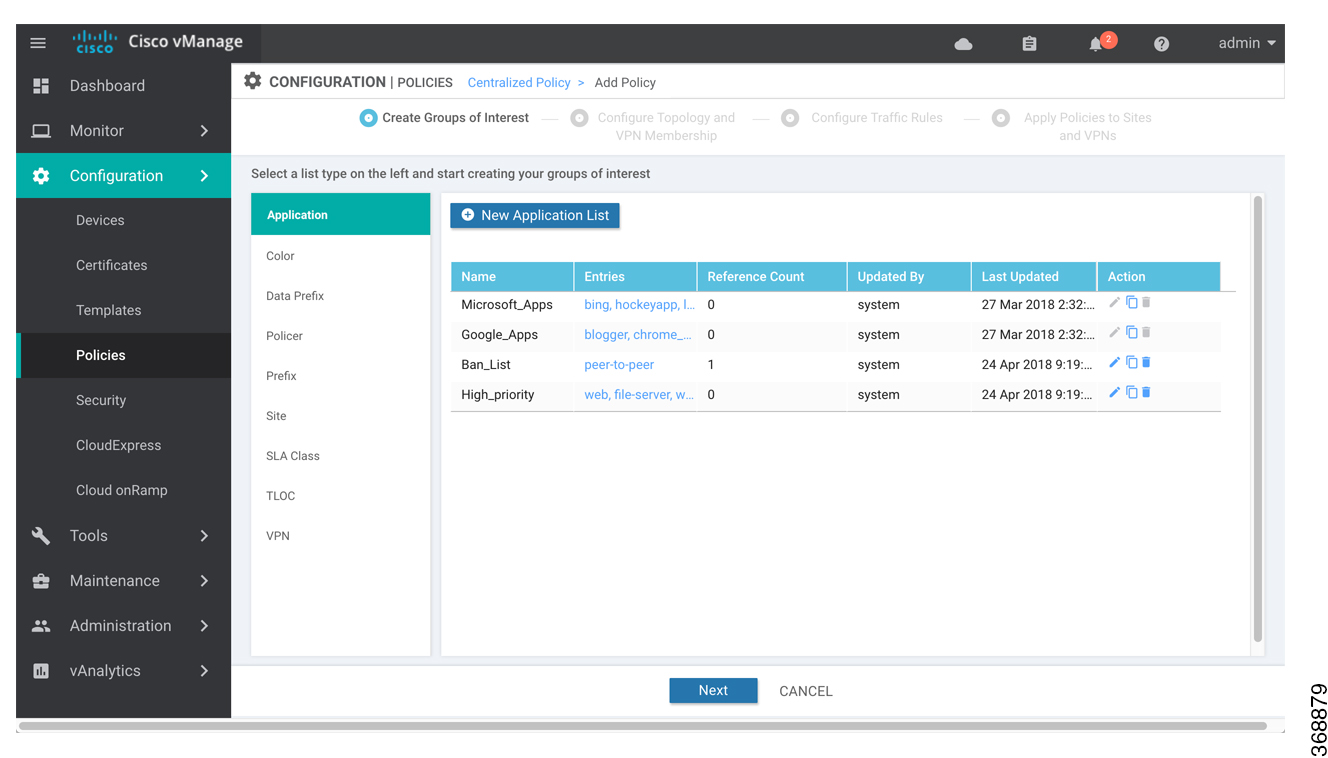
Click Add Policy. The policy configuration wizard opens, and the Create Groups of Interest screen displays. |
Step 1: Create Policy Lists
You can create lists of groups to use in a centralized policy.
Procedure
|
Step 1 |
Create new lists as described in the following table:
|
||||||||||||||||||||
|
Step 2 |
Click Next to move to Configure Topology and VPN Membership in the wizard. |
Step 2: Configure Traffic Rules
| Feature Name |
Release Information |
Description |
|---|---|---|
|
Policy Matching with ICMP Message |
Cisco SD-WAN Release 20.4.1 Cisco vManage Release 20.4.1 |
This feature provides support for a new match condition that you can use to specify a list of ICMP messages for centralized data policies, localized data policies and Application-Aware Routing policies. |
When you first open the Traffic Rules screen, the Application-Aware Routing tab is selected by default. To configure traffic rules for deep packet inspection, see Configure Deep Packet Inspection.
To configure traffic rules for centralized data policy:
Procedure
|
Step 1 |
Click the Traffic Data tab. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 2 |
Click the Add Policy drop-down. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 3 |
Click Create New. The Add Data Policy screen displays. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 4 |
Enter a name and description for the data policy. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 5 |
In the right pane, click Sequence Type. The Add Data Policy popup opens. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 6 |
Select the type of data policy you want to create. Choices are: Application Firewall, QoS, Service Chaining, Traffic Engineering, and Custom. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 7 |
A policy sequence containing the text string Application Firewall, QoS, Service Chaining, Traffic Engineering, or Custom is added in the left pane |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 8 |
Double-click the text string, and enter a name for the policy sequence. The name you type is displayed both in the Sequence Type list in the left pane and in the right pane. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 9 |
In the right pane, click Sequence Rule. The Match/Action box opens, and Match is selected by default. The available policy match conditions are listed below the box. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 10 |
For QoS and Traffic Engineering data policies: From the Protocol drop-down list, select IPv4 to apply the policy only to IPv4 address families. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 11 |
To select one or more Match conditions, click its box and set the values as described in the following table. Note that not all match conditions are available for all policy sequence types.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 12 |
To select actions to take on matching data traffic, click the Actions box. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 13 |
To drop matching traffic, click Drop. The available policy actions are listed to the right of the button. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 14 |
To accept matching traffic, click Accept. The available policy actions are listed to the right of the button. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 15 |
Set the policy action as described in the following table. Note that not all actions are available for all match conditions
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 16 |
Create additional sequence rules as desired. Drag and drop to re-arrange them. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 17 |
Click Save Data Policy. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Step 18 |
Click Next to move to Apply Policies to Sites and VPNs in the wizard. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Step 3: Apply Policies to Sites and VPNs
In Apply Policies to Sites and VPNs, apply a policy to overlay network sites and VPNs.
Procedure
|
Step 1 |
In the Policy Name field, enter a name for the policy. This field is mandatory and can contain only uppercase and lowercase letters, the digits 0 through 9, hyphens (–), and underscores (_). It cannot contain spaces or any other characters. |
|
Step 2 |
In the Policy Description field, enter a description of the policy. It can contain up to 2048 characters. This field is mandatory, and it can contain any characters and spaces. |
|
Step 3 |
From the Topology bar, select the tab that corresponds to the type of policy block—Topology, Application-Aware Routing, Traffic Data, or Cflowd. The table then lists policies that you have created for that type of policy block. |
|
Step 4 |
Associate the policy with VPNs and sites. The choice of VPNs and sites depends on the type of policy block:
|
|
Step 5 |
Click Preview to view the configured policy. The policy is displayed in CLI format. |
|
Step 6 |
Click Save Policy. The screen appears, and the policies table includes the newly created policy. |
Step 4: Activate a Centralized Data Policy
Activating a centralized data policy sends that policy to all connected Cisco Catalyst SD-WAN Controllers. To activate a centralized policy:
Procedure
|
Step 1 |
In Cisco SD-WAN Manager, select the screen. |
|
Step 2 |
Select a policy from the policy table. |
|
Step 3 |
Click the More Actions icon to the right of the row, and click Activate. The Activate Policy popup opens. It lists the IP addresses of the reachable Cisco Catalyst SD-WAN Controllers to which the policy is to be applied. |
|
Step 4 |
Click Activate. |
Configure Centralized Data Policy Using CLI
Following are the high-level steps for configuring a VPN membership data policy:
-
Create a list of overlay network sites to which the VPN membership policy is to be applied (in the apply-policy command):
vSmart(config)# policy vSmart (config-policy)# lists site-list list-name vSmart(config-lists-list-name)# site-id site-idThe list can contain as many site IDs as necessary. Include one site-id command for each site ID. For contiguous site IDs, you can specify a range of numbers separated with a dash (–). Create additional site lists, as needed.
-
Create lists of IP prefixes and VPNs, as needed:
vSmart(config)# policy lists vSmart(config-lists)# data-prefix-list list-name vSmart(config-lists-list-name)# ip-prefix prefix/lengthvSmart(config)# policy lists vSmart(config-lists)# vpn-list list-name vSmart(config-lists-list-name)# vpn vpn-id -
Create lists of TLOCs, as needed. vSmart(config)# policy vSmart(config-policy)# lists tloc-list list-name vSmart(config-lists-list-name)# tloc ip-address color color encap encapsulation [preference number} -
Define policing parameters, as needed:
vSmart(config-policy)# policer policer-name vSmart(config-policer)# rate bandwidth vSmart(config-policer)# burst bytes vSmart(config-policer)# exceed action -
Create a data policy instance and associate it with a list of VPNs:
vSmart(config)# policy data-policy policy-name vSmart(config-data-policy-policy-name)# vpn-list list-name -
Create a series of match–pair sequences:
vSmart(config-vpn-list)# sequence number vSmart(config-sequence-number)#The match–action pairs are evaluated in order, by sequence number, starting with the lowest numbered pair and ending when the route matches the conditions in one of the pairs. Or if no match occurs, the default action is taken (either rejecting the route or accepting it as is).
-
Define match parameters for packets:
vSmart(config-sequence-number)# match parameters -
Define actions to take when a match occurs:
vSmart(config-sequence-number)# action (accept | drop) [count counter-name] [log] [tcp-optimization] vSmart(config-sequence-number)# action acccept nat [pool number] [use-vpn 0] vSmart(config-sequence-number)# action accept redirect-dns (host | ip-address) vSmart(config-sequence-number)# action accept set parameters -
Create additional numbered sequences of match–action pairs within the data policy, as needed.
-
If a route does not match any of the conditions in one of the sequences, it is rejected by default. To accept nonmatching prefixed, configure the default action for the policy:
vSmart(config-policy-name)# default-action accept -
Apply the policy to one or more sites in the overlay network:
vSmart(config)# apply-policy site-list list-name data-policy policy-name (all |from-service | from-tunnel)
Structural Components of Policy Configuration for Centralized Data Policy
The following commands are the structural components required to configure VPN membership policy. Each one is explained in more detail in the sections that follow.
policy
lists
app-list list-name
(app applications | app-family application-families)
data-prefix-list list-name
ip-prefix prefix
site-list list-name
site-id site-id
tloc-list list-name
tloc ip-address color color encap encapsulation [preference value]
vpn-list list-name
vpn vpn-id
policer policer-name
burst bytes
exceed action
rate bandwidth
data-policy policy-name
vpn-list list-name
sequence number
match
app-list list-name
destination-data-prefix-list list-name
destination-ip prefix/length
destination-port port-numbers
dscp number
dns-app-list list-name
dns (request | response)
packet-length number
protocol number
icmp-msg
icmp6-msg
source-data-prefix-list list-name
source-ip prefix/length
source-port port-numbers
tcp flag
action
cflowd (not available for deep packet inspection)
count counter-name
drop
log
redirect-dns (dns-ip-address | host)
tcp-optimization
accept
nat [pool number] [use-vpn 0]
set
dscp number
forwarding-class class
local-tloc color color [encap encapsulation] [restrict]
next-hop ip-address
policer policer-name
service service-name local [restrict] [vpn vpn-id]
service service-name [tloc ip-address | tloc-list list-name] [vpn vpn-id]
tloc ip-address color color [encap encapsulation]
tloc-list list-name
vpn vpn-id
default-action
(accept | drop)
apply-policy site-list list-name
data-policy policy-name (all | from-service | from-tunnel)Lists
A centralized data policy for deep packet inspection uses the following types of lists to group related items.
-
-
.
| List Type | Description |
Cisco SD-WAN Manager |
CLI Command |
|---|---|---|---|
| Applications and application families |
List of one or more applications or application families running on the subnets connected to the device. application-names can be the names of one or more applications. The Cisco vEdge devices support about 2300 different applications. To list the supported applications, use the ? in the CLI. application-families can be one or more of the following: antivirus, application-service, audio_video, authentication, behavioral, compression, database, encrypted, erp, file-server, file-transfer, forum, game, instant-messaging, mail, microsoft-office, middleware, network-management, network-service, peer-to-peer, printer, routing, security-service, standard, telephony, terminal, thin-client, tunneling, wap, web, and webmail. |
or |
app-list list-name (app applications | app-family application-families ) |
|
Colors |
List of one or more TLOC colors. color can be 3g, biz-internet, blue, bronze, custom1 through custom3, default, gold, green, lte, metro-ethernet, mpls, private1 through private6, public-internet, red, and silver. To configure multiple colors in a single list, include multiple color options, specifying one color in each option. |
color-list list-name color color |
|
| Prefixes |
List of one or more IP prefixes. Specify the IP prefixes as follows: prefix/length—Exactly match a single prefix–length pair. 0.0.0.0/0—Match any prefix–length pair. 0.0.0.0/0 le length—Match any IP prefix whose length is less than or equal to length. For example, ip-prefix 0.0.0.0/0 le 16 matches all IP prefixes with lengths from /1 through /16. 0.0.0.0/0 ge length—Match any IP prefix whose length is greater than or equal to length. For example, ip-prefix 0.0.0.0 ge 25 matches all IP prefixes with lengths from /25 through /32. 0.0.0.0/0 ge length1 le length2, or 0.0.0.0 le length2 ge length1—Match any IP prefix whose length is greater than or equal to length1 and less than or equal to length2. For example, ip-prefix 0.0.0.0/0 ge 20 le 24 matches all /20, /21, /22, /23, and /24 prefixes. Also, ip-prefix 0.0.0.0/0 le 24 ge 20 matches the same prefixes. If length1 and length2 are the same, a single IP prefix length is matched. For example, ip-prefix 0.0.0.0/0 ge 24 le 24 matches only /24 prefixes. To configure multiple prefixes in a single list, include multiple ip-prefix options, specifying one prefix in each option. |
or |
prefix-list list-name ip-prefix prefix/length |
| Sites | List of one or more site identifiers in the overlay network. You can specify a single site identifier (such as site-id 1) or a range of site identifiers (such as site-id 1-10). |
or |
site-list list-name site-id site-id |
| TLOCs |
List of one or more TLOCs in the overlay network. For each TLOC, specify its address, color, and encapsulation. address is the system IP address. color can be one of 3g, biz-internet, blue, bronze, custom1, custom2, custom3, default, gold, green, lte, metro-ethernet, mpls, mpls-restricted, private1 through private6, public-internet, red, and silver. encapsulation can be gre or ipsec. Optionally, set a preference value (from 0 to 232 – 1) to associate with the TLOC address. When you apply a TLOC list in an action accept condition, when multiple TLOCs are available and satisfy the match conditions, the TLOC with the highest preference value is used. If two or more of TLOCs have the highest preference value, traffic is sent among them in an ECMP fashion. |
or |
tloc-list list-name tloc ip-address color color encap encapsulation [preference number] |
| VPNs |
List of one or more VPNs in the overlay network. For data policy, you can configure any VPNs except for VPN 0 and VPN 512. To configure multiple VPNs in a single list, include multiple vpn options, specifying one VPN number in each option. You can specify a single VPN identifier (such as vpn 1) or a range of VPN identifiers (such as vpn 1-10). |
or |
vpn-list list-name vpn vpn-id |
VPN Lists
Each centralized data policy is associated with a VPN list. You configure VPN lists with the policy data-policy vpn-list command. The list you specify must be one that you created with a VPN Group of Interest or List in the Cisco SD-WAN Manager policy configuration wizard or with the policy lists vpn-list command.
For a centralized data policy, you can include any VPNs except for VPN 0 and VPN 512. VPN 0 is reserved for control traffic, so never carries any data traffic, and VPN 512 is reserved for out-of-band network management, so also never carries any data traffic. Note that while the CLI allows you to include these two VPNs in a data policy configuration, the policy is not applied to these two VPNs.
Policer Parameters
To configure policing parameters, create a policer that specifies the maximum bandwidth and burst rate for traffic on an interface, and how to handle traffic that exceeds these values.
In Cisco SD-WAN Manager, you configure policer parameters from:
In the CLI, you configure policer parameters as follows:
vSmart(config)# policy policer policer-name
vSmart(config-policer)# rate bps
vSmart(config-policer)# burst bytes
vSmart(config-policer)# exceed actionrate is the maximum traffic rate. It can be a value from 0 through 264 – 1 bits per second.
burst is the maximum traffic burst size. It can be a value from 15000 to 1000000 bytes.
exceed is the action to take when the burst size or traffic rate is exceeded. action can be drop (the default) or remark. The drop action is equivalent to setting the packet loss priority (PLP) bit to low. The remark action sets the PLP bit to high. In a centralized data policy, access lists, and application-aware routing policy, you can match the PLP with the match plp option.
Sequences - VPN List
Each VPN list consists of sequences of match–action pairs. The sequences are numbered to set the order in which data traffic is analyzed by the match–action pairs in the policy.
In Cisco SD-WAN Manager, you configure sequences from:
In the CLI, you configure sequences with the policy data-policy vpn-list sequence command.
Each sequence can contain one match condition and one action condition.
 Note |
Sequence can have either match app-list or dns-app-list configured for a policy, but not both. Configuring both match app-list and dns-app-list for a policy is not supported. |
Match Parameters - Data Policy
A centralized data policy can match IP prefixes and fields in the IP headers, as well as applications. You can also enable split DNS.
Each sequence in a policy can contain one or more match conditions.
| Match Condition | Description | ||
|---|---|---|---|
|
Omit |
Match all packets. | ||
|
Applications/Application Family List |
Applications or application families. |
||
|
Destination Data Prefix |
Group of destination prefixes, IP prefix and prefix length. The range is 0 through 65535; specify a single port number, a list of port numbers (with numbers separated by a space), or a range of port numbers (with the two numbers separated with a hyphen [-]). | ||
|
Destination Region |
Choose one of the following:
|
||
| DNS Application List | Enables split DNS, to resolve and process DNS requests and responses on an application-by-application basis. Name of an app-list list . This list specifies the applications whose DNS requests are processed. | ||
|
DNS |
Specify the direction in which to process DNS packets. To process DNS requests sent by the applications (for outbound DNS queries), specify dns request . To process DNS responses returned from DNS servers to the applications, specify dns response . | ||
|
DSCP |
Specifies the DSCP value. | ||
|
Packet length |
Specifies the packet length. The range is 0 through 65535; specify a single length, a list of lengths (with numbers separated by a space), or a range of lengths (with the two numbers separated with a hyphen [-]). | ||
| Packet Loss Priority (PLP) | Specifies the packet loss priority. By default, packets have a PLP value of low . To set the PLP value to high , apply a policer that includes the exceed remark option. | ||
|
Protocol |
Specifies Internet protocol number. The range is 0 through 255. | ||
|
ICMP Message |
For Protocol IPv4 when you enter a Protocol value as 1, the ICMP Message field displays where you can select an ICMP message to apply to the data policy. Likewise, the ICMP Message field displays for Protocol IPv6 when you enter a Protocol value as 58. When you select Protocol as Both, the ICMP Message or ICMPv6 Message field displays.
|
||
|
Source Data Prefix |
Specifies the group of source prefixes or an individual source prefix. | ||
|
Source Port |
Specifies the source port number. The range is 0 through 65535; specify a single port number, a list of port numbers (with numbers separated by a space), or a range of port numbers (with the two numbers separated with a hyphen [-]). | ||
|
TCP Flag |
Specifies the TCP flag, syn. | ||
|
Traffic To |
In a Multi-Region Fabric architecture, match border router traffic flowing to the access region that the border router is serving, the core region, or a service VPN.
|
 Note |
If IPv4 packet contains non-initial fragment of UDP or TCP datagram, it has no L4 ports information available because there is no UDP or TCP header. For such fragments destination-port or source-port match is ignored. In the following example, all the UDP packets to destination port 161 and any other IPv4 packets having protocol ID field in IPv4 header set to 17 with IPv4 header having fragment-offset set will be dropped. |
|
Type |
Code |
Enumeration |
| 0 | 0 | echo-reply |
| 3 | unreachable | |
| 0 | net-unreachable | |
| 1 | host-unreachable | |
| 2 | protocol-unreachable | |
| 3 | port-unreachable | |
| 4 | packet-too-big | |
| 5 | source-route-failed | |
| 6 | network-unknown | |
| 7 | host-unknown | |
| 8 | host-isolated | |
| 9 | dod-net-prohibited | |
| 10 | dod-host-prohibited | |
| 11 | net-tos-unreachable | |
| 12 | host-tos-unreachable | |
| 13 | administratively-prohibited | |
| 14 | host-precedence-unreachable | |
| 15 | precedence-unreachable | |
| 5 | redirect | |
| 0 | net-redirect | |
| 1 | host-redirect | |
| 2 | net-tos-redirect | |
| 3 | host-tos-redirect | |
| 8 | 0 | echo |
| 9 | 0 | router-advertisement |
| 10 | 0 | router-solicitation |
| 11 | time-exceeded | |
| 0 | ttl-exceeded | |
| 1 | reassembly-timeout | |
| 12 | parameter-problem | |
| 0 | general-parameter-problem | |
| 1 | option-missing | |
| 2 | no-room-for-option | |
| 13 | 0 | timestamp-request |
| 14 | 0 | timestamp-reply |
| 40 | 0 | photuris |
| 42 | 0 | extended-echo |
| 43 | extended-echo-reply | |
| 0 | echo-reply-no-error | |
| 1 | malformed-query | |
| 2 | interface-error | |
| 3 | table-entry-error | |
| 4 | multiple-interface-match |
| Type | Code | Enumeration |
| 1 | unreachable | |
| 0 | no-route | |
| 1 | no-admin | |
| 2 | beyond-scope | |
| 3 | destination-unreachable | |
| 4 | port-unreachable | |
| 5 | source-policy | |
| 6 | reject-route | |
| 7 | source-route-header | |
| 2 | 0 | packet-too-big |
| 3 | time-exceeded | |
| 0 | hop-limit | |
| 1 | reassembly-timeout | |
| 4 | parameter-problem | |
| 0 | Header | |
| 1 | next-header | |
| 2 | parameter-option | |
| 128 | 0 | echo-request |
| 129 | 0 | echo-reply |
| 130 | 0 | mld-query |
| 131 | 0 | mld-report |
| 132 | 0 | mld-reduction |
| 133 | 0 | router-solicitation |
| 134 |
0 |
router-advertisement |
| 135 | 0 | nd-ns |
| 136 | 0 | nd-na |
| 137 | 0 | redirect |
|
138 |
router-renumbering | |
| 0 | renum-command | |
| 1 | renum-result | |
| 255 | renum-seq-number | |
| 139 | ni-query | |
| 0 | ni-query-v6-address | |
| 1 | ni-query-name | |
| 2 | ni-query-v4-address | |
| 140 | ni-response | |
| 0 | ni-response-success | |
| 1 | ni-response-refuse | |
| 2 |
ni-response-qtype-unknown |
|
| 141 | 0 | ind-solicitation |
| 142 | 0 |
ind-advertisement |
| 143 | mldv2-report | |
| 144 | 0 | dhaad-request |
| 145 | 0 | dhaad-reply |
| 146 | 0 | mpd-solicitation |
| 147 | 0 |
mpd-advertisement |
| 148 | 0 | cp-solicitation |
| 149 | 0 |
cp-advertisement |
| 151 | 0 |
mr-advertisement |
| 152 | 0 | mr-solicitation |
| 153 | 0 | mr-termination |
| 155 | 0 | rpl-control |
Action Parameters - Data Policy
|
Feature Name |
Release Information |
Description |
|---|---|---|
|
Path Preference Support for Cisco IOS XE Catalyst SD-WAN Devices |
Cisco IOS XE Catalyst SD-WAN Release 17.2.1r |
This feature extends to Cisco IOS XE Catalyst SD-WAN devices, support for selecting one or more local transport locators (TLOCs) for a policy action. |
|
Traffic Redirection to SIG Using Data Policy |
Cisco SD-WAN Release 20.4.1 Cisco vManage Release 20.4.1 |
With this feature, while creating a data policy, you can define an application list along with other match criteria and redirect the application traffic to a Secure Internet Gateway (SIG). |
|
Next Hop Action Enhancement in Data Policies |
Cisco SD-WAN Release 20.5.1 Cisco vManage Release 20.5.1 |
This feature enhances match action conditions in a centralized data policy for parity with the features configured on Cisco vEdge devices. When you are setting up next-hop-loose action, this feature helps to redirect application traffic to an available route when next-hop address is not available. |
When data traffic matches the conditions in the match portion of a centralized data policy, the packet can be accepted or dropped. Then, you can associate parameters with accepted packets.
In the CLI, you configure the action parameters with the policy data-policy vpn-list sequence action command.
Each sequence in a centralized data policy can contain one action condition.
In the action, you first specify whether to accept or drop a matching data packet, and whether to count it:
|
Action Condition |
Description | ||||||
|---|---|---|---|---|---|---|---|
| Click Accept | Accepts the packet. An accepted packet is eligible to be modified by the additional parameters configured in the action portion of the policy configuration. | ||||||
|
Cflowd |
Enables cflowd traffic monitoring. | ||||||
|
Counter |
Counts the accepted or dropped packets. Specifies the name of a counter. Use the show policy access-lists counters command on the Cisco vEdge device. | ||||||
|
Click Drop |
Discards the packet. This is the default action. | ||||||
|
Log |
Minimum release: Cisco IOS XE Catalyst SD-WAN Release 17.11.1a and Cisco vManage Release 20.11.1 Click Log to enable logging. When (DP, AAR or ACL) data policy packets are configured with log action, logs generated and logged to syslog. Due to the global log-rate-limit, not all logs are logged. A syslog message is generated the first time a packet header is logged and then every 5 minutes thereafter, as long as the flow is active. For information on policy log-rate-limit CLI, see policy log-rate-limit command in the Cisco Catalyst SD-WAN Qualified Command Reference Guide. |
||||||
|
Redirect DNS |
Redirects DNS requests to a particular DNS server. Redirecting requests is optional, but if you do so, you must specify both
actions.
For an inbound policy, redirect-dns host allows the DNS response to be correctly forwarded back to the requesting service VPN. For an outbound policy, specify the IP address of the DNS server.
|
||||||
|
TCP Optimization |
Fine-tune TCP to decrease round-trip latency and improve throughout for matching TCP traffic. | ||||||
| Secure Internet Gateway |
Redirect application traffic to a SIG.
|
Then, for a packet that is accepted, the following parameters can be configured:
|
Action Condition |
Description | ||
|---|---|---|---|
|
Cflowd |
Enables cflowd traffic monitoring. | ||
|
NAT Pool or NAT VPN |
Enables NAT functionality, so that traffic can be redirected directly to the internet or other external destination. | ||
|
DSCP |
DSCP value. The range is 0 through 63. | ||
|
Forwarding Class |
Name of the forwarding class. | ||
|
Local TLOC |
Enables sending packets to one of the TLOCs that matches the color and encapsulation. The available colors are: 3g, biz-internet, blue, bronze, custom1,custom2, custom3, default, gold, green, lte, metro-ethernet, mpls, private1 through private6, public-internet, red and silver. The encapsulation options are: ipsec and gre. By default, if the TLOC is not available, traffic is forwarded using an alternate TLOC. To drop traffic if a TLOC is unavailable, include the restrict option. By default, encapsulation is ipsec. |
||
|
Next Hop |
Sets the next hop IP address to which the packet should be forwarded.
|
||
|
Policer |
Applies a policer. Specifies the name of policer configured with the policy policer command. | ||
|
Service |
Specifies a service to redirect traffic to before delivering the traffic to its destination. The TLOC address or list of TLOCs identifies the remote TLOCs to which the traffic should be redirected to reach the service. In the case of multiple TLOCs, the traffic is load-balanced among them. The VPN identifier is where the service is located. Standard services: FW, IDS, IDP Custom services: netsvc1, netsvc2,netsvc3, netsvc4 TLOC list is configured with a policy lists tloc-list list. Configure the services themselves on the Cisco vEdge devices that are collocated with the service devices, using the vpn service command. |
||
|
TLOC |
Direct traffic to a remote TLOC that matches the IP address, color, and encapsulation of one of the TLOCs in the list. If a preference value is configured for the matching TLOC, that value is assigned to the traffic. | ||
|
Click Accept, then action VPN. |
Set the VPN that the packet is part of. The range is 0 through 65530. |
 Note |
Data policies are applicable on locally generated packets, including routing protocol packets, when the match conditions are generic. Example configuration: In such situations, it may be necessary to add a sequence in the data policy to escape the routing protocol packets. For example to skip OSPF, use the following configuration: |
The following table describes the IPv4 and IPv6 actions.
|
IPv4 Actions |
IPv6 Actions |
|---|---|
|
drop, dscp, next-hop (from-service only)/vpn, count, forwarding class, policer (only in interface ACL), App-route SLA (only) |
N/A |
| App-route preferred color, app-route sla strict, cflowd, nat, redirect-dns |
N/A |
|
N/A |
drop, dscp, next-hop/vpn, count, forwarding class, policer (only in interface ACL) App-route SLA (only), App-route preferred color, app-route sla strict |
|
policer (DataPolicy), tcp-optimization, fec-always, |
policer (DataPolicy) |
|
tloc, tloc-list (set tloc, set tloc-list) |
tloc, tloc-list (set tloc, set tloc-list) |
|
App-Route backup-preferred color, local-tloc, local-tloc-list |
App-Route backup-preferred color, local-tloc, local-tloc-list |
Default Action - VPN List
If a data packet being evaluated does not match any of the match conditions in a data policy, a default action is applied to the packet. By default, the data packet is dropped
In Cisco SD-WAN Manager, you modify the default action from:
-
-
.
In the CLI, you modify the default action with the policy data-policy vpn-list default-action accept command.
Apply Centralized Data Policy in the CLI
To apply a centralized data policy in the CLI:
vSmart(config)# apply-policy site-list list-name data-policy policy-name (all | from-service | from-tunnel)By default, data policy applies to all data traffic passing through the device: the policy evaluates all data traffic going from the local site (that is, from the service side of the router) into the tunnel interface, and it evaluates all traffic entering to the local site through the tunnel interface. You can explicitly configure this behavior by including the all option. To have the data policy apply only to traffic coming from the service site and exiting from the local site through the tunnel interface, include the from-service option. To have the policy apply only to traffic entering from the tunnel interface and traveling to the service site, include the from-tunnel option. You can apply different data policies in each of the two traffic directions.
For all data-policy policies that you apply with apply-policy commands, the site IDs across all the site lists must be unique. That is, the site lists must not contain overlapping site IDs. An example of overlapping site IDs are those in the two site lists site-list 1 site-id 1-100 and site-list 2 site-id 70-130 . Here, sites 70 through 100 are in both lists. If you were to apply these two site lists to two different data-policy policies, the attempt to commit the configuration on the Cisco Catalyst SD-WAN Controller would fail.
The same type of restriction also applies to the following types of policies:
-
Application-aware routing policy (app-route-policy )
-
Centralized control policy (control-policy )
-
Centralized data policy used for cflowd flow monitoring (data-policy that includes a cflowd action and apply-policy that includes a cflowd-template command)
You can, however, have overlapping site IDs for site lists that you apply for different types of policy. For example, the sites lists for control-policy and data-policy policies can have overlapping site IDs. So for the two example site lists above, site-list 1 site-id 1-100 and site-list 2 site-id 70-130 , you could apply one to a control policy and the other to a data policy.
As soon as you successfully activate the configuration by issuing a commit command, the Cisco Catalyst SD-WAN Controller pushes the data policy to the devices located in the specified sites. To view the policy as configured on the Cisco Catalyst SD-WAN Controllers, use the show running-config command on the Cisco Catalyst SD-WAN Controller:
vSmart# show running-config policy
vSmart# show running-config apply-policyTo view the policy that has been pushed to the Cisco vEdge device, use the show policy from-vsmart command on the Cisco vEdge device.
vEdge# show policy from-vsmartCisco Catalyst SD-WAN Application Intelligence Engine Flow Overview
The Cisco Catalyst SD-WAN Application Intelligence Engine (SAIE) flow provides the ability to look into the packet past the basic header information. The SAIE flow determines the contents of a particular packet, and then either records that information for statistical purposes or performs an action on the packet.
 Note |
In Cisco vManage Release 20.7.1 and earlier releases, the SAIE flow is called the deep packet inspection (DPI) flow. |
Benefits include increased visibility into the network traffic, which enables network operators to understand usage patterns and to correlate network performance information along with providing usage base billing or even acceptable usage monitoring. The SAIE flow can also reduce the overall costs on the network.
You can configure the SAIE flow using a centralized data policy. You define the applications of interest in a Cisco SD-WAN Manager policy list or with the policy lists app-list CLI command, and you call these lists in a policy data-policy command. You can control the path of the application traffic through the network by defining, in the action portion of the data policy, the local TLOC or the remote TLOC, or for strict control, you can define both.
The following list of protocols are not supported in SAIE flow:
-
Open Shortest Path First (OSPF)
-
Border Gateway Protocol (BGP)
-
Internet Control Message Protocol (ICMP)
-
Bidirectional Forwarding Detection (BFD)
Configure Cisco Catalyst SD-WAN Application Intelligence Engine Flow Using Cisco SD-WAN Manager
To configure the Cisco Catalyst SD-WAN Application Intelligence Engine (SAIE) flow, use the Cisco SD-WAN Manager policy configuration wizard. The wizard consists of the following sequential screens that guide you through the process of creating and editing policy components:
-
Create Applications or Groups of Interest—Create lists that group together related items and that you call in the match or action components of a policy. For configuration details, see Configure Groups of Interest.
-
Configure Traffic Rules—Create the match and action conditions of a policy. For configuration details, see Configure Traffic Rules.
-
Apply Policies to Sites and VPNs—Associate policy with sites and VPNs in the overlay network.
Configure SD-WAN Application Intelligence Engine Flow Using the CLI
Following are the high-level steps for configuring a centralized data policy for the SD-WAN Application Intelligence Engine (SAIE) flow.
 Note |
In Cisco vManage Release 20.7.x and earlier releases, the SAIE flow is called the deep packet inspection (DPI) flow. |
-
Create a list of overlay network sites to which the data policy is to be applied using the apply-policy command:
vSmart(config)# policy vSmart(config-policy)# lists site-list list-name vSmart(config-lists-list-name)# site-id site-idThe list can contain as many site IDs as necessary. Include one site-id command for each site ID. For contiguous site IDs, you can specify a range of numbers separated with a dash (–).
Create additional site lists, as needed.
-
Create lists of applications and application families that are to be subject to the data policy. Each list can contain one or more application names, or one or more application families. A single list cannot contain both applications and application families.
vSmart(config)# policy lists vSmart(config-lists)# app-list list-name vSmart(config-app-list)# app application-name vSmart(config)# policy lists vSmart(config-lists)# app-list list-name vSmart(config-applist)# app-family family-name -
Create lists of IP prefixes and VPNs, as needed:
vSmart(config)# policy lists vSmart(config-lists)# data-prefix-list list-name vSmart(config-lists-list-name)# ip-prefix prefix/length vSmart(config)# policy lists vSmart(config-lists)# vpn-list list-name vSmart(config-lists-list-name)# vpn vpn-id -
Create lists of TLOCs, as needed:
vSmart(config)# policy vSmart(config-policy)# lists tloc-list list-name vSmart(config-lists-list-name)# tloc ip-address color color encap encapsulation [preference number] -
Define policing parameters, as needed:
vSmart(config-policy)# policer policer-name vSmart(config-policer)# rate bandwidth vSmart(config-policer)# burst bytes vSmart(config-policer)# exceed action -
Create a data policy instance and associate it with a list of VPNs:
vSmart(config)# policy data-policy policy-name vSmart(config-data-policy-policy-name)# vpn-list list-name -
Create a series of match–pair sequences:
vSmart(config-vpn-list)# sequence number vSmart(config-sequence-number)#The match–action pairs are evaluated in order, by sequence number, starting with the lowest numbered pair and ending when the route matches the conditions in one of the pairs. Or if no match occurs, the default action is taken (either rejecting the route or accepting it as is).
-
Define match parameters based on applications:
vSmart(config-sequence-number)# match app-list list-name -
Define additional match parameters for data packets:
vSmart(config-sequence-number)# match parameters -
Define actions to take when a match occurs:
vSmart(config-sequence-number)# action (accept | drop) [count] -
For packets that are accepted, define the actions to take. To control the tunnel over which the packets travels, define the remote or local TLOC, or for strict control over the tunnel path, set both:
vSmart(config-action)# set tloc ip-address color color encap encapsulation vSmart(config-action)# set tloc-list list-name vSmart(config-action)# set local-tloc color color encap encapsulation vSmart(config-action)# set local-tloc-list color color encap encapsulation [restrict] -
Define additional actions to take.
-
Create additional numbered sequences of match–action pairs within the data policy, as needed.
-
If a route does not match any of the conditions in one of the sequences, it is rejected by default. If you want nonmatching prefixes to be accepted, configure the default action for the policy:
vSmart(config-policy-name)# default-action accept -
Apply the policy to one or more sites in the overlay network:
vSmart(config)# apply-policy site-list list-name data-policy policy-name (all | from-service | from-tunnel)
vEdge(config)# policy app-visibilityUse the following show commands for visibility in to traffic classification:
-
show app dpi flows
-
show support dpi flows active detail
-
show app dpi application
-
show support dpi flows expired detail
-
show support dpi statistics
Components of Policy Configuration for Deep Packet Inspection
Following are the components required to configure a centralized data policy for deep packet inspection. Each one is explained in more detail in the sections below.
On the vSmart controller:
policy
lists
app-list list-name
(app applications | app-family application-families)
data-prefix-list list-name
ip-prefix prefix
site-list list-name
site-id site-id
tloc-list list-name
tloc ip-address color color encap encapsulation [preference value]
vpn-list list-name
vpn vpn-id
policer policer-name
burst bytes
exceed action
rate bps
data-policy policy-name
vpn-list list-name
sequence number
match
app-list list-name
destination-data-prefix-list list-name
destination-ip ip-addresses
destination-port port-numbers
dscp number
packet-length number
protocol protocol
source-data-prefix-list list-name
source-ip ip-addresses
source-port port-numbers
tcp flag
action
drop
count counter-name
log
accept
nat [pool number] [use-vpn 0]
set
dscp number
forwarding-class class
local-tloc color color [encap encapsulation] [restrict]
next-hop ip-address
policer policer-name
service service-name local [restrict] [vpn vpn-id]
service service-name (tloc ip-address | tloc-list list-name) [vpn vpn-id]
tloc ip-address color color encap encapsulation
tloc-list list-name
vpn vpn-id
default-action
(accept | drop)
apply-policy site-list list-name
data-policy policy-name (all | from-service | from-tunnel)
On the vEdge router:
policy
app-visibilityAction Parameters for Configuring SD-WAN Application Intelligence Engine Flow
When data traffic matches the conditions in the match portion of a centralized data policy, the packet can be accepted or dropped, and it can be counted. Then, you can associate parameters with accepted packets.
From the Cisco SD-WAN Manager menu, you can configure match parameters from:
-
-
.
In the CLI, you configure the action parameters under the policy data-policy vpn-list sequence action command.
Each sequence in a centralized data policy can contain one action condition.
In the action, you first specify whether to accept or drop a matching data packet, and whether to count it:
| Description | Cisco SD-WAN Manager |
CLI Command |
Value or Range |
|---|---|---|---|
| Accept the packet. An accepted packet is eligible to be modified by the additional parameters configured in the action portion of the policy configuration. |
Click Accept. |
accept |
— |
| Count the accepted or dropped packets. |
Action Counter Click Accept, then action Counter |
count counter-name |
Name of a counter. Use the show policy access-lists counters command on the Cisco device. |
| Discard the packet. This is the default action. |
Click Drop |
drop |
— |
| Log the packet. Packets are placed into the messages and vsyslog system logging (syslog) files. |
Action Log Click Accept, then action Log |
log |
To view the packet logs, use the show app log flows and show log commands. |
To view the packet logs, use the show app log flow and show log commands.
Then, for a packet that is accepted, the following parameters can be configured.
| Description | Cisco SD-WAN Manager | CLI Command | Value or Range |
|---|---|---|---|
| DSCP value. |
Click Accept, then action DSCP. |
set dscp value |
0 through 63 |
| Forwarding class. |
Click Accept, then action Forwarding Class. |
set forwarding-class value |
Name of forwarding class |
|
Direct matching packets to a TLOC that matches the color and encapsulation By default, if the TLOC is not available, traffic is forwarded using an alternate TLOC. |
Click Accept, then action Local TLOC. |
set local-tloc color color [encap encapsulation] |
color can be: 3g, biz-internet, blue, bronze, custom1, custom2, custom3, default, gold, green lte, metro-ethernet mpls, private1 through private6, public-internet, red, and silver. By default, encapsulation is ipsec. It can also be gre. |
|
Direct matching packets to one of the TLOCs in the list if the TLOC matches the color and encapsulation By default, if the TLOC is not available, traffic is forwarded using an alternate TLOC. To drop traffic if a TLOC is unavailable, include the restrict option. |
Click Accept, then action Local TLOC |
set local-tloc-list color color encap encapsulation [restrict] |
|
| Set the next hop to which the packet should be forwarded. |
Click Accept, then action Next Hop. |
set next-hop ip-address |
IP address |
| Apply a policer. |
Click Accept, then action Policer. |
set policer policer-name |
Name of policer configured with a policy policer command. |
|
Direct matching packets to the name service, before delivering the traffic to its ultimate destination. The TLOC address or list of TLOCs identifies the remote TLOCs to which the traffic should be redirected to reach the service. In the case of multiple TLOCs, the traffic is load-balanced among them. The VPN identifier is where the service is located. Configure the services themselves on the Cisco devices that are collocated with the service devices, using the vpn service configuration command. |
Click Accept, then action Service. |
set service service-name [tloc ip-address | tloc-list list-name] [vpn vpn-id] |
Standard services: FW, IDS, IDP Custom services: netsvc1, netsvc2,netsvc3, netsvc4 TLOC list is configured with a policy lists tloc-list list. |
| Direct matching packets to the named service that is reachable using a GRE tunnel whose source is in the transport VPN (VPN 0). If the GRE tunnel used to reach the service is down, packet routing falls back to using standard routing. To drop packets when a GRE tunnel to the service is unreachable, include the restrict option. In the service VPN, you must also advertise the service using the service command. You configure the GRE interface or interfaces in the transport VPN (VPN 0). |
Click Accept, then action Service. |
set service service-name [tloc ip-address | tloc-list list-name] [vpn vpn-id] |
Standard services: FW, IDS, IDP Custom services: netsvc1, netsvc2,netsvc3, netsvc4 |
| Direct traffic to a remote TLOC. The TLOC is defined by its IP address, color, and encapsulation. |
Click Accept, then action TLOC. |
set local-tloc color color [encap encapsulation] |
TLOC address, color, and encapsulation |
|
Direct traffic to one of the remote TLOCs in the TLOC list. |
Click Accept, then action TLOC. |
set tloc-list list-name |
Name of a policy lists tloc-list list |
| Set the VPN that the packet is part of. |
Click Accept, then action VPN. |
set vpn vpn-id |
0 through 65530 |
Default Action
If a data packet being evaluated does not match any of the match conditions in a data policy, a default action is applied to the packet. By default, the data packet is dropped.
From the Cisco SD-WAN Manager menu, you modify the default action from .
In the CLI, you modify the default action with the policy data-policy vpn-list default-action accept command.
Apply Centralized Policy for SD-WAN Application Intelligence Engine Flow
To ensure that a centralized data policy for the SD-WAN Application Intelligence Engine (SAIE) flow takes effect, you must apply it to a list of sites in the overlay network.
To apply a centralized policy in Cisco SD-WAN Manager, see Configure Centralized Policy Using Cisco SD-WAN Manager.
To apply a centralized policy in the CLI:
vSmart(config)# apply-policy site-list list-name data-policy policy-name (all | from-service | from-tunnel)By default, data policy applies to all data traffic passing through the Cisco Catalyst SD-WAN Controller: the policy evaluates all data traffic going from the local site (that is, from the service side of the router) into the tunnel interface, and it evaluates all traffic entering to the local site through the tunnel interface. You can explicitly configure this behavior by including the all option. To have the data policy apply only to policy exiting from the local site, include the from-service option. To have the policy apply only to incoming traffic, include the from-tunnel option.
You cannot apply the same type of policy to site lists that contain overlapping site IDs. That is, all data policies cannot have overlapping site lists among themselves. If you accidentally misconfigure overlapping site lists, the attempt to commit the configuration on the Cisco Catalyst SD-WAN Controller fails.
As soon as you successfully activate the configuration by issuing a commit command, the Cisco Catalyst SD-WAN Controller pushes the data policy to the Cisco vEdge devices located in the specified sites. To view the policy as configured on the Cisco Catalyst SD-WAN Controller, use the show running-config command on the Cisco Catalyst SD-WAN Controller:
vSmart# show running-config policy
vSmart# show running-config apply-policyTo view the policy that has been pushed to the Cisco vEdge device, use the show policy from-vsmart command on the Cisco vEdge device.
vEdge# show policy from-vsmartCentralized Policies Configuration Examples
This topic provides some examples of configuring a centralized data policy to influence traffic flow across the Cisco Catalyst SD-WAN domain and to configure a Cisco Catalyst SD-WAN device to be an internet exit point.
General Centralized Policy Example
This section shows a general example of a centralized data policy to illustrate that you configure centralized data policy on a Cisco Catalyst SD-WAN Controller and that after you commit the configuration, the policy itself is pushed to the required Cisco Catalyst SD-WAN device.
Here we configure a simple data policy on the Cisco Catalyst SD-WAN Controller vm9:
vm9# show running-config policy
policy
data-policy test-data-policy
vpn-list test-vpn-list
sequence 10
match
destination-ip 209.165.201.0/27
!
action drop
count test-counter
!
!
default-action drop
!
!
lists
vpn-list test-vpn-list
vpn 1
!
site-list test-site-list
site-id 500
!
!
!Immediately, after you activate the configuration on the Cisco Catalyst SD-WAN Controller, it pushes the policy configuration to the Cisco vEdge devices in site 500. One of these devices is vm5, where you can see that the policy has been received:
vm5# show policy from-vsmart
policy-from-vsmart
data-policy test-data-policy
vpn-list test-vpn-list
sequence 10
match
destination-ip 209.165.201.0/27
!
action drop
count test-counter
!
!
default-action drop
!
!
lists
vpn-list test-vpn-list
vpn 1
!
!
!Control Access
This example shows a data policy that limits the type of packets that a source can send to a specific destination. Here, the host at source address 192.0.2.1 in site 100 and VPN 100 can send only TCP traffic to the destination host at 203.0.113.1. This policy also specifies the next hop for the TCP traffic sent by 192.0.2.1, setting it to be TLOC 209.165.200.225, color gold. All other traffic is accepted as a result of the default-action statement.
policy
lists
site-list north
site-id 100
vpn-list vpn-north
vpn 100
!
data-policy tcp-only
vpn-list vpn-north
sequence 10
match
source-ip 192.0.2.1/32
destination-ip 198.51.100.1/32
protocol tcp
action accept
set tloc 203.0.113.1 gold
!
default-action accept
!
!
apply-policy
site north data-policy tcp-onlyRestrict Traffic
This examples illustrates how to disallow certain types of data traffic from being sent from between VPNs. This policy drops data traffic on port 25, which carries SMTP mail traffic, that originates in 209.165.201.0/27. However, the policy accepts all other data traffic, including non-SMTP traffic from 209.165.201.0/27.
policy
lists
data-prefix-list north-ones
ip-prefix 209.165.201.0/27
port 25
vpn-list all-vpns
vpn 1
vpn 2
site-list north
site-id 100
!
data-policy no-mail
vpn-list all-vpns
sequence 10
match
source-data-prefix-list north-ones
action drop
!
default-action accept
!
!
apply-policy
site north data-policy no-mailAllow Traffic to Exit from a Cisco vEdge Device to the Internet
The following example allows data traffic destined for two prefixes on the Internet to exit directly from the local Cisco vEdge device to the internet destination. Configure this policy on the Cisco Catalyst SD-WAN Controller.
polcy
lists
vpn-list vpn-1
vpn 1
!
site-list nat-sites
site-id 100,200
!
data-policy accept-nat
vpn-list vpn-1
sequence 100
match
source-ip 10.20.24.0/24
destination-ip 10.0.12.12/32
!
action accept
count nat
nat use-vpn 0
!
!
sequence 101
match
source-ip 10.20.24.0/24
destination-ip 10.1.15.13/32
!
action accept
count nat_inet
nat use-vpn 0
!
!
default-action accept
!
!
apply-policy
site-list nat-sites data-policy accept-nat Using the destination port instead of a destination IP prefix allows greater flexibility for traffic exiting to the internet. Here, traffic can go to all HTTP and HTTPS sites (ports 80 and 443, respectively). Configure this policy on a Cisco Catalyst SD-WAN Controller.
data-policy accept-nat
vpn-list vpn-1
sequence 100
match
source-ip 10.20.24.0/24
destination-port 80
!
action accept
count nat
nat use-vpn 0
!
!
sequence 101
match
source-ip 10.20.24.0/24
destination-port 443
!
action accept
count nat_inet
nat use-vpn 0
!
!
default-action accept
!
!Traffic Engineering
This example of traffic engineering forces all traffic to come to a Cisco SD-WAN device using a device hub instead of directly.
One common way to design a domain in a Cisco SD-WAN overlay network is to route all traffic destined for branches through a hub router, which is typically located in a data center, rather than sending the traffic directly from one Cisco SD-WAN device to another. You can think of this as a hub-and-spoke design, where one device is acting as a hub and the devices are the spokes. With such a design, traffic between local branches travels over the IPsec connections that are established between the spoke routers and the hub routers when the devices are booted up. Using established connections means that the devices do not need to expend time and CPU cycles to establish IPsec connections with each other. If you were to imagine that this were a large network with many devices, having a full mesh of connections between each pair of routers would require a large amount of CPU from the routers. Another attribute of this design is that, from an administrative point of view, it can be simpler to institute coordinated traffic flow policies on the hub routers, both because there are fewer of them in the overlay network and because they are located in a centralized data center.
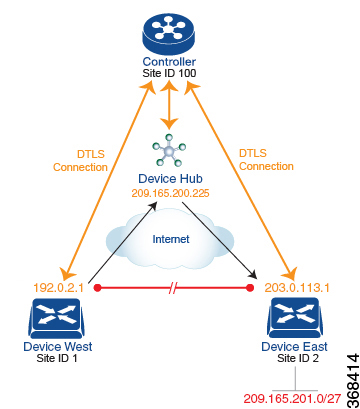
This topology has two devices in different branches:
-
The Device West in site ID 1. The TLOC for this device is defined by its IP address (192.0.2.1), a color (gold), and an encapsulation (here, IPsec). We write the full TLOC address as {192.0.2.1, gold, ipsec}. The color is simply a way to identify a flow of traffic and to separate it from other flows.
-
The Device East in site ID 2 has a TLOC address of {203.0.113.1, gold, ipsec}.
The devices West and East learn each other’s TLOC addresses from the OMP routes distributed to them by the Cisco Catalyst SD-WAN Controller. In this example, the Device East advertises the prefix 209.165.201.0/27 as being reachable at TLOC {203.0.113.1, gold, }. In the absence of any policy, the Device West could route traffic destined for 209.165.201.0/27 to TLOC {203.0.113.1, gold, ipsec}, which means that the Device West would be sending traffic directly to the Device East.
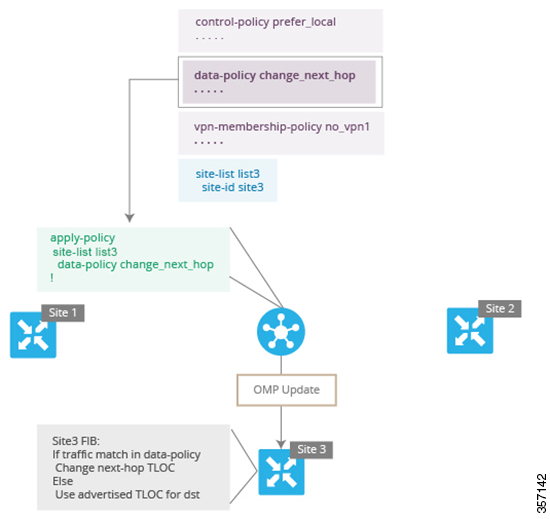
However, our design requires that all traffic from West to East be routed through the hub router, whose TLOC address is {209.165.200.225, gold, ipsec}, before going to the Device East. To effect this traffic flow, you define a policy that changes the route's TLOC. So, for the prefix 209.165.201.0/27, you create a policy that changes the TLOC associated with the prefix 209.165.201.0/27 from {203.0.113.1, gold, ipsec}, which is the TLOC address of the Device East, to {209.165.200.225, gold, ipsec}, which is the TLOC address of the hub router. The result is that the OMP route for the prefix 209.165.201.0/27 that the Cisco Catalyst SD-WAN Controller advertises to the Device West that contains the TLOC address of the hub router instead of the TLOC address of the Device East. From a traffic flow point of view, the Device West then sends all traffic destined for 209.165.201.0/27 to the hub router.
The device also learns the TLOC addresses of the West and East devices from the OMP routes advertised by the Cisco Catalyst SD-WAN Controller. Because, devices must use these two TLOC addresses, no policy is required to control how the hub directs traffic to the devices.
Here is a policy configuration on the Cisco Catalyst SD-WAN Controller that directs the Device West (and any other devices in the network domain) to send traffic destined to prefix 209.165.201.0/27 to TLOC 209.165.200.225, gold, which is the device:
policy
lists
prefix-list east-prefixes
ip-prefix 209.165.201.0/27
site-list west-sites
site-id 1
control-policy change-tloc
sequence 10
match route
prefix-list east-prefixes
site-id 2
action accept
set tloc 209.165.200.225 color gold encap ipsec
apply-policy
site west-sites control-policy change-tloc outA rough English translation of this policy is:
Create a list named “east-prefixes” that contains the IP prefix “209.165.201.0/27”
Create a list named “west-sites” that contains the site-id “1”
Define a control policy named “change-tloc”
Create a policy sequence element that:
Matches a prefix from list “east-prefixes”, that is, matches “209.165.201.0/27”
AND matches a route from site-id “2”
If a match occurs:
Accept the route
AND change the route’s TLOC to “209.165.200.225” with a color of "gold" and an encapsulation of "ipsec"
Apply the control policy “change-tloc” to OMP routes sent by the vSmart
controller to “west-sites”, that is, to site ID 1This control policy is configured on the Cisco Catalyst SD-WAN Controller as an outbound policy, as indicated by the out option in the apply-policy site command. This option means the Cisco Catalyst SD-WAN Controller applies the TLOC change to the OMP route after it distributes the route from its route table. The OMP route for prefix 209.165.201.0/27 that the Cisco Catalyst SD-WAN Controller distributes to the Device West associates 209.165.201.0/27 with TLOC 209.165.200.225, gold. This is the OMP route that the Device West installs it in its route table. The end results are that when the Device West sends traffic to 209.165.201.0/27, the traffic is directed to the hub; and the Device West does not establish a DTLS tunnel directly with the Device East.
If the West side of the network had many sites instead of just one and each site had its own device, it would be straightforward to apply this same policy to all the sites. To do this, you simply add the site IDs of all the sites in the site-list west-sites list. This is the only change you need to make in the policy to have all the West-side sites send traffic bound for the prefix 209.165.201.0/27 through the device. For example:
policy
lists
prefix-list east-prefixes
ip-prefix 209.165.201.0/27
site-list west-sites
site-id 1
site-id 11
site-id 12
site-id 13
control-policy change-tloc
sequence 10
match route
prefix-list east-prefixes
site-id 2
action accept
set tloc 209.165.200.225 color gold encap ipsec
apply-policy
site west-sites control-policy change-tloc outCreating Arbitrary Topologies
To provide redundancy in the hub-and-spoke-style topology discussed in the previous example, you can add a second Cisco hub to create a dual-homed hub site. The following figure shows that site ID 100 now has two Device hubs. We still want all inter-branch traffic to be routed through a device hub. However, because we now have dual-homed hubs, we want to share the data traffic between the two hub routers.
-
Device Hub West, with TLOC 209.165.200.225, gold. We want all data traffic from branches on the West side of the overlay network to pass through and be processed by this device.
-
Device Hub East, with TLOC 198.51.100.1, gold. Similarly, we all East-side data traffic to pass through the Device Hub East.
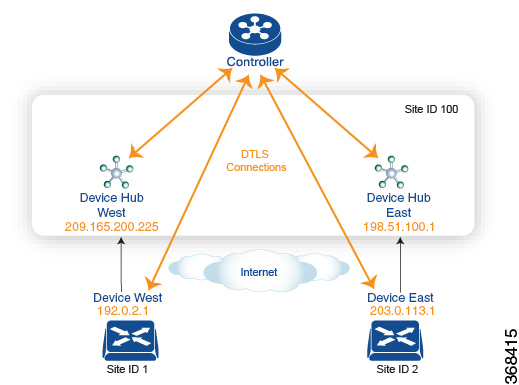
Here is a policy configuration on the Cisco Catalyst SD-WAN Controller that would send West-side data traffic through the Cisco hub, and West and East-side traffic through the Device Hub East:
policy
lists
site-list west-sites
site-id 1
site-list east-sites
site-id 2
tloc-list west-hub-tlocs
tloc-id 209.165.200.225 gold
tloc-list east-hub-tlocs
tloc-id 198.51.100.1 gold
control-policy prefer-west-hub
sequence 10
match tloc
tloc-list west-hub-tlocs
action accept
set preference 50
control-policy prefer-east-hub
sequence 10
match tloc
tloc-list east-hub-tlocs
action accept
set preference 50
apply-policy
site west-sites control-policy prefer-west-hub out
site east-sites control-policy prefer-east-hub outHere is an explanation of this policy configuration:
Create the site lists that are required for the apply-policy configuration command:
-
site-list west-sites lists all the site IDs for all the devices in the West portion of the overlay network.
-
site-list east-sites lists the site IDs for the devices in the East portion of the network.
Create the TLOC lists that are required for the match condition in the control policy:
-
west-hub-tlocs lists the TLOC for the Device West Hub, which we want to service traffic from the West-side device.
-
east-hub-tlocs lists the TLOC for the Device East Hub, to service traffic from the East devices.
Define two control policies:
-
prefer-west-hub affects OMP routes destined to TLOC 209.165.200.225, gold, which is the TLOC address of the Device West hub router. This policy modifies the preference value in the OMP route to a value of 50, which is large enough that it is likely that no other OMP routes will have a larger preference. So setting a high preference value directs traffic destined for site 100 to the Device West hub router.
-
Similarly, prefer-east-hub sets the preference to 50 for OMP routes destined TLOC 198.51.100.1, gold, which is the TLOC address of the Device East hub router, thus directing traffic destined for site 100 site to the Device East hub 198.51.100.1 router.
Apply the control policies:
-
The first line in the apply-policy configuration has the Cisco Catalyst SD-WAN Controller apply the prefer-west-hub control policy to the sites listed in the west-sites list, which here is only site ID 1, so that the preference in their OMP routes destined to TLOC 209.165.200.225 is changed to 50 and traffic sent from the Device West to the hub site goes through the Device West hub router.
-
The Cisco Catalyst SD-WAN Controller applies the prefer-east-hub control policy to the OMP routes that it advertises to the devices in the east-sites list, which changes the preference to 50 for OMP routes destined to TLOC 198.51.100.1, so that traffic from the Device East goes to the Device East hub router.
 Feedback
Feedback