Cisco vSmart Policy Components
The Cisco vSmart policies that implement overlay network-wide policies are implemented on a Cisco vSmart Controller. Because Cisco vSmart Controllers are centralized devices, you can manage and maintain Cisco vSmart policies centrally, and you can ensure consistency in the enforcement of policy across the overlay network.
The implementation of Cisco vSmart policy is done by configuring the entire policy on the Cisco vSmart Controller. Cisco vSmart policy configuration is accomplished with three building blocks:
-
Lists define the targets of policy application or matching.
-
Policy definition, or policies, controls aspects of control and forwarding. There are different types of policy, including:
-
app-route-policy (for application-aware routing)
-
cflowd-template (for cflowd flow monitoring)
-
control-policy (for routing and control plane information)
-
data-policy (for data traffic)
-
vpn-membership-policy (for limiting the scope of traffic to specific VPNs)
-
-
Policy application controls what a policy is applied towards. Policy application is site-oriented, and is defined by a specific list called a site-list.
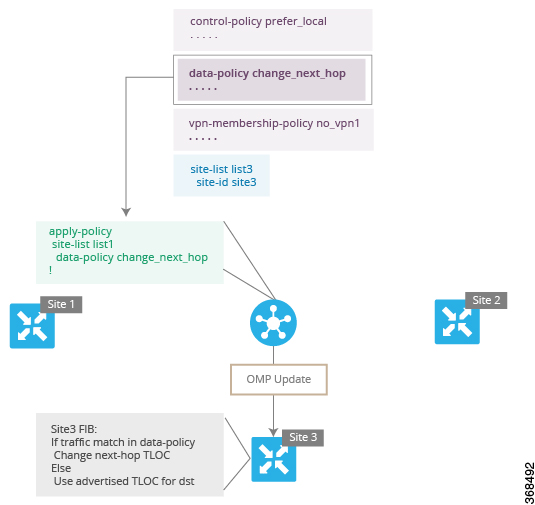
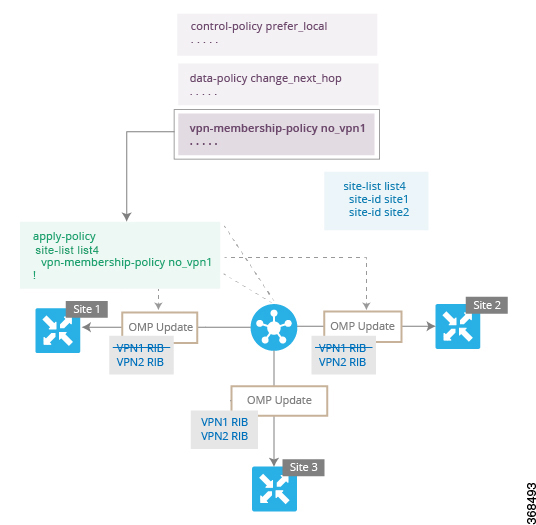
You assemble these three building blocks to Cisco vSmart policy. More specifically, policy is the sum of one or more lists, one policy definition, and at least one policy applications, as shown in the table below.
|
Lists |
Policy Definition |
Policy Application |
||
|---|---|---|---|---|
|
|
+ |
|
+ |
|
|
= |
||||
|
Complete policy definition configured on Cisco vSmart and enforced either on Cisco vSmart or on Cisco IOS XE SD-WAN devices. |
||||
Lists
Lists are how you group related items so that you can reference them all together. Examples of items you put in lists are prefixes, TLOCs, VPNs, and overlay network sites. In the Cisco vSmart Controller policy, you invoke lists in two places: when you create a policy definition and when you apply a policy. Separating the definition of the related items from the definition of policy means that when you can add or remove items from a lists, you make the changes only in a single place: You do not have to make the changes through the policy definition. So if you add ten sites to your network and you want to apply an existing policy to them, you simply add the site identifiers to the site list. You can also change policy rules without having to manually modify the prefixes, VPNs, or other things that the rules apply to.
|
List type |
Usage |
|---|---|
| data-prefix-list |
Used in data-policy to define prefix and upper layer ports, either individually or jointly, for traffic matching. |
| prefix-list |
Used in control-policy to define prefixes for matching RIB entries. |
| site-list |
Used in control-policy to match source sites, and in apply-policy to define sites for policy application. |
| tloc-list |
Used in control-policy to define TLOCs for matching RIB entries and to apply redefined TLOCs to vRoutes. |
| vpn-list |
Used in control-policy to define prefixes for matching RIB entries, and in data-policy and app-route-policy to define VPNs for policy application. |
The following configuration shows the types of Cisco vSmart Controller policy lists:
policy
lists
data-prefix-list app1
ip-prefix 209.165.200.225/27 port 100
!
prefix-list pfx1
ip-prefix 209.165.200.225/27
!
site-list site1
site-id 100
!
tloc-list site1-tloc
tloc 209.165.200.225 color mpls
vpn-list vpn1
vpn1
!
!
Policy Definition
The policy definition is where you create the policy rules. You specify match conditions (route-related properties for control policy and data-related fields for data policy) and actions to perform when a match occurs. A policy contains match–action pairings that are numbered and that are examined in sequential order. When a match occurs, the action is performed, and the policy analysis on that route or packet terminates. Some types of policy definitions apply only to specific VPNs.
|
Policy type |
Usage |
|---|---|
| policy-type |
Can be control-policy, data-policy, or vpn-menbership—dictates the type of policy. Each type has a particular syntax and a particular set of match conditions and settable actions. |
| vpn-list |
Used by data-policy and app-route-policy to list the VPNs for which the policy is applicable. |
| sequence |
Defines each sequential step of the policy by sequence number. |
| match |
Decides what entity to match on in the specific policy sequence. |
| action |
Determines the action that corresponds to the preceding match statement. |
| default-action |
Action to take for any entity that is not matched in any sequence of the policy. By default, the action is set to reject. |
The following configuration shows the components of the Cisco vSmart Controller policy definition. These items are listed in the logical order you should use when designing policy, and this order is also how the items are displayed in the configuration, regardless of the order in which you add them to the configuration.
policy
policy-type name
vpn-list vpn-list
sequence number
match
<route | tloc vpn | other>
!
action <accept reject drop>
set attribute value
!
default-action <reject accept>
!
!
!Policy Application
The following are the configuration components:
|
Component |
Usage |
|---|---|
| site-list |
Determines the sites to which a given policy is applies. The direction (in | out) applies only to control-policy. |
| policy-type |
The policy type can be control-policy, data-policy, or vpn-membership—and name refer to an already configured policy to be applied to the sites specified in the site-list for the section. |
For a policy definition to take effect, you associate it with sites in the overlay network.
apply-policy
site-list name
control-policy name <inout>
!
site-list name
data-policy name
vpn-membership name
!
!Policy Example
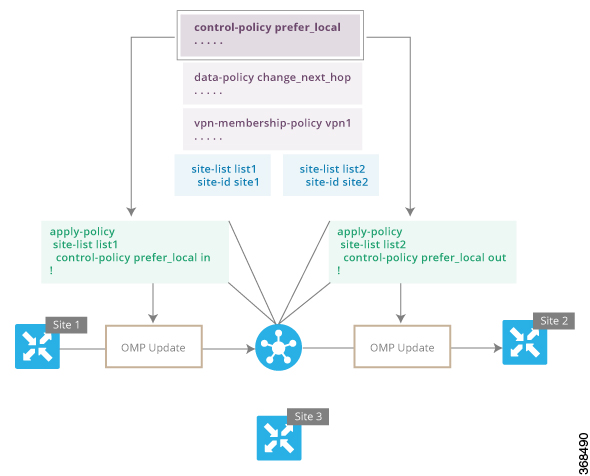
For a complete policy, which consists of lists, policy definition, and policy application. The example illustrated below creates two lists (a site-list and a tloc-list), defines one policy (a control policy), and applies the policy to the site-list. In the figure, the items are listed as they are presented in the node configuration. In a normal configuration process, you create lists first (group together all the things you want to use), then define the policy itself (define what things you want to do), and finally apply the policy (specify the sites that the configured policy affects).
apply-policy
site-list site1 ––––––––→ Apply the defined policy towards the sites in site-list
control-policy prefer_local out
!
policy
lists
site-list site1
site-id 100
tloc-list prefer_site1 –––→ Define the lists required for apply-policy and for use within the policy
tloc 192.0.2.1 color mols encap ipsec preference 400
control-policy prefer_local
sequence 10
match route
site-list sitele ––––––->Lists previously defined used within policy
!
action accept
set
tloc-list prefer_site
!
!
!
TLOC Attributes Used in Policies
A transport location, or TLOC, defines a specific interface in the overlay network. Each TLOC consists of a set of attributes that are exchanged in OMP updates among the Cisco SD-WAN devices. Each TLOC is uniquely identified by a 3-tuple of IP address, color, and encapsulation. Other attributes can be associated with a TLOC.
The TLOC attributes listed below can be matched or set in Cisco vSmart Controller policies.
|
TLOC Attribute |
Function |
Application Point Set By |
Application Point Modify By |
|---|---|---|---|
|
Address (IP address) |
system-ip address of the source device on which the interface is located. |
Configuration on source device |
control-policy data-policy |
|
Carrier |
Identifier of the carrier type. It primarily indicates whether the transport is public or private. |
Configuration on source device |
control-policy |
|
Color |
Identifier of the TLOC type. |
Configuration on source device |
control-policy data-policy |
|
Domain ID |
Identifier of the overlay network domain. |
Configuration on source device |
control-policy |
|
Encapsulation |
Tunnel encapsulation, either IPsec or GRE. |
Configuration on source device |
control-policy data-policy |
|
Originator |
system-ip address of originating node. |
Configuration on any originator |
control-policy |
|
Preference |
OMP path-selection preference. A higher value is a more preferred path. |
Configuration on source device |
control-policy |
|
Site ID |
Identification for a give site. A site can have multiple nodes or TLOCs. |
Configuration on source device |
control-policy |
|
Tag |
Identifier of TLOC on any arbitrary basis. |
Configuration on source device |
control-policy |
vRoute Attributes Used in Policies
A Cisco SD-WAN route, or vRoute, defines a route in the overlay network. A vRoute, which is similar to a standard IP route, has a number attributes such as TLOC and VPN. The Cisco IOS XE SD-WAN devices exchange vRoutes in OMP updates.
The vRoutes attributes listed below can be matched or set in Cisco vSmart Controller policies.
|
vRoute Attribute |
Function |
Application Point Set By |
Application Point Modify By |
|---|---|---|---|
|
Origin |
Source of the route, either BGP, OSPF, connected, static. |
Source device |
control-policy |
|
Originator |
Source of the update carrying the route. |
Any originator |
control-policy |
|
Preference |
OMP path-selection preference. A higher value is a more preferred path. |
Configuration on source device or policy |
control-policy |
|
Service |
Advertised service associated with the vRoute. |
Configuration on source device |
control-policy |
|
Site ID |
Identifier for a give site. A site can have multiple nodes or TLOCs. |
Configuration on source device |
control-policy |
|
Tag |
Identification on any arbitrary basis. |
Configuration on source device |
control-policy |
|
TLOC |
TLOC used as next hop for the vRoute. |
Configuration on source device or policy |
control-policy data-policy |
|
VPN |
VPN to which the vRoute belongs. |
Configuration on source device or policy |
control-policy data-policy |

 Feedback
Feedback