Cisco IOS Release 15.8(3)M1 - Release Notes for Cisco IR800 Industrial Integrated Services Routers and Cisco CGR1000 Series Connected Grid Routers
Available Languages
Table of Contents
Image Information and Supported Platforms
Warning about Installing the Image
IR800 Series: GPS NMEA Multiple Stream
Examples for Enabling/Disabling GPS NMEA Multiple Stream
GPS Multiple NMEA Stream Information
show software authenticity file command
IR829: Client Information Signaling Protocol (CISP)
IR829: Dot1x Supplicant Support on the L2 interface
Sample Configuration to Support DOT1x Supplicant on the IR829
IR829: LLDP (Link Layer Discovery Protocol) Support for 3rd party PoE devices
Cisco IOS Release 15.8(3)M1 - Release Notes for Cisco IR800 Industrial Integrated Services Routers and Cisco CGR1000 Series Connected Grid Routers
The following release notes support the Cisco IOS 15.8(3)M1 release. These release notes are updated to describe new features, limitations, troubleshooting, recommended configurations, caveats, and provide information on how to obtain support and documentation.
Contents
This publication consists of the following sections:
■![]() Image Information and Supported Platforms
Image Information and Supported Platforms
■![]() Caveats
Caveats
Image Information and Supported Platforms
Note : You must have a Cisco.com account to download the software.
Cisco IOS Release 15.8(3)M1 includes the following Cisco IOS images:
Software Downloads
IR800 Series
The latest image files for the IR800 product family can be found here:
https://software.cisco.com/download/navigator.html?mdfid=286287045&flowid=75322
Click on the 807, 809 or 829 link to take you to the specific software you are looking for.
IR809
The IR809 link shows the following entries:
–![]() ir800-universalk9-bundle. <version>.bin
ir800-universalk9-bundle. <version>.bin
–![]() ir800-universalk9_npe-bundle. <version>.bin
ir800-universalk9_npe-bundle. <version>.bin
–![]() Yocto 1.7.2 Base Rootfs (ir800_yocto-1.7.2.tar)
Yocto 1.7.2 Base Rootfs (ir800_yocto-1.7.2.tar)
–![]() Python 2.7.3 Language Runtime (ir800_yocto-1.7.2_python-2.7.3.tar)
Python 2.7.3 Language Runtime (ir800_yocto-1.7.2_python-2.7.3.tar)
–![]() Azul Java 1.7 EJRE (ir800_yocto-1.7.2_zre1.7.0_65.7.6.0.7.tar)
Azul Java 1.7 EJRE (ir800_yocto-1.7.2_zre1.7.0_65.7.6.0.7.tar)
–![]() Azul Java 1.8 Compact Profile 3 (ir800_yocto-1.7.2_zre1.8.0_65.8.10.0.1.tar)
Azul Java 1.8 Compact Profile 3 (ir800_yocto-1.7.2_zre1.8.0_65.8.10.0.1.tar)
Software on Chassis
–![]() ir800-universalk9-bundle. <version>.bin
ir800-universalk9-bundle. <version>.bin
–![]() ir800-universalk9_npe-bundle. <version>.bin
ir800-universalk9_npe-bundle. <version>.bin
–![]() Yocto 1.7.2 Base Rootfs (ir800_yocto-1.7.2.tar)
Yocto 1.7.2 Base Rootfs (ir800_yocto-1.7.2.tar)
–![]() Python 2.7.3 Language Runtime (ir800_yocto-1.7.2_python-2.7.3.tar)
Python 2.7.3 Language Runtime (ir800_yocto-1.7.2_python-2.7.3.tar)
–![]() Azul Java 1.7 EJRE (ir800_yocto-1.7.2_zre1.7.0_65.7.6.0.7.tar)
Azul Java 1.7 EJRE (ir800_yocto-1.7.2_zre1.7.0_65.7.6.0.7.tar)
–![]() Azul Java 1.8 Compact Profile 3 (ir800_yocto-1.7.2_zre1.8.0_65.8.10.0.1.tar)
Azul Java 1.8 Compact Profile 3 (ir800_yocto-1.7.2_zre1.8.0_65.8.10.0.1.tar)
AP803 Access Point Module
–![]() WIRELESS LAN (ap1g3-k9w7-tar.153-3.JH1.tar)
WIRELESS LAN (ap1g3-k9w7-tar.153-3.JH1.tar)
–![]() WIRELESS LAN (ap1g3-k9w8-tar.153-3.JH1.tar)
WIRELESS LAN (ap1g3-k9w8-tar.153-3.JH1.tar)
–![]() WIRELESS LAN LWAPP RECOVERY (ap1g3-rcvk9w8-tar.153-3.JH1.tar)
WIRELESS LAN LWAPP RECOVERY (ap1g3-rcvk9w8-tar.153-3.JH1.tar)
Note : On the IR8x9 devices, the ir800-universalk9-bundle.SPA.158-3.M bundle can be copied via Trivial File Transfer Protocol (TFTP) or SCP to the IR800, and then installed using the bundle install flash: <image name> command. The ir800-universalk9-bundle.SPA.158-3.M.bin file can NOT be directly booted using the boot system flash:/image_name. Detailed instructions are found in the Cisco IR800 Integrated Services Router Software Configuration Guide.
Note : On the IR8x9 devices, the cipher dhe-aes-256-cbc-sha (which is used with the commands ip http client secure-ciphersuite and ip http secure-ciphersuite) is no longer available in IOS 15.6(3)M and later as part of the weak cipher removal process. This cipher was flagged as a security vulnerability.
CGR1K Series
The latest image file for the CGR 1000 Series Cisco IOS image is:
https://software.cisco.com/download/navigator.html?mdfid=284165761&flowid=75122
For details on the CGR1000 installation, please see:
http://www.cisco.com/c/en/us/td/docs/routers/connectedgrid/cgr1000/ios/release/notes/OL-31148-05.html#pgfId-9
Major Enhancements
This section provides details on new features and functionality available in this release. Each new feature is proceeded by the platform which it applies to.
IR800 Series: GPS NMEA Multiple Stream
Feature applies to the IR807, IR809, and IR829.
Previous versions of IOS only allowed for a GPS NMEA Stream for one device. This release has support for up to 6 devices at one time. The existing CLI lte gps nmea ip udp <src ip> <dest ip> <dest portno> under controller configuration has been enhanced.
Setting up the Configuration
Examples for Enabling/Disabling GPS NMEA Multiple Stream
Warning Messages
If the destination ip address and port number already exists:
Please use different destination ip address and port number.
If the stream number already exists:
Please remove stream number configuration before creating it with different destination ip address and port number.
IR8x9 and CGR1K: Display digital signature and software authenticity-related information for a specific image file from image header.
Feature applies to the IR809, IR829, CGR1120, and CGR1240
Updates have been made to CLI commands due to unsupported file format errors:
■![]() show software authenticity file <IOS image/SRP image/bundle image/GOS image>
show software authenticity file <IOS image/SRP image/bundle image/GOS image>
■![]() verify <IOS image/SRP image/bundle image/GOS image>
verify <IOS image/SRP image/bundle image/GOS image>
These commands would return the error:
With this feature enhancement, users will now be able to run these CLIs to display and verify digital signature and software authenticity information for these types of signed files present in flash: partition only (IOS image, Hypervisor image, bundle image and Guest-OS image) supported on IR8x9 and CGR1000 platform.
show software authenticity file command
show software authenticity file flash: <bundle image> | <ios image> | <srp image> | <gos image>
Displays digital signature and software authenticity-related information for a specific image file from image header.
For additional information on this command, please see:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/fundamentals/command/cf_command_ref/show_protocols_through_showmon.html#wp9122926510
Note : It may take several minutes for the command to perform the image authentication.
verify command
verify flash: <bundle image> | <ios image> | <srp image> | <gos image>
IR829: Client Information Signaling Protocol (CISP)
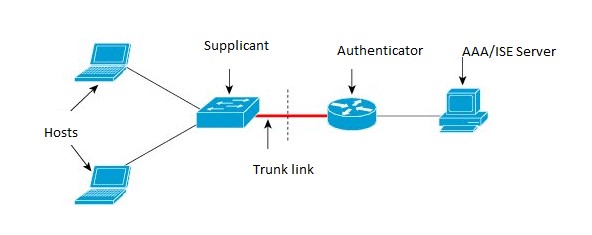
CISP is a generic protocol used by Network Edge Authentication Topology (NEAT) scenario in order to propagate client MAC addresses and VLAN information between supplicant and authenticator. CISP was already available in Cisco IOS, but is new to the IR829 platform. Complete details on this feature are available here:
https://www.cisco.com/c/en/us/support/docs/lan-switching/8021x/116681-config-neat-cise-00.html
Cisp in NEAT illustrates how the CISP feature works in NEAT in a simple scenario.
CISP Commands
The following commands have been added to the IR829:
■![]() show cisp [client]/[interface]/[registrations]/[summary]
show cisp [client]/[interface]/[registrations]/[summary]
■![]() show authentication [interface] / [method] / [registrations]/ [sessions] / [statistic]
show authentication [interface] / [method] / [registrations]/ [sessions] / [statistic]
■![]() debug cisp [all]/[errors]/[events]/[packets]/[sync]
debug cisp [all]/[errors]/[events]/[packets]/[sync]
Details on the commands follow:
Used to enable the CISP protocol on Authenticator as well as on Supplicants. In config mode CISP enable cli globally enable the CISP protocol on L2 interface.
■![]() In exec mode, show cisp client displays all the information for authorized host mac address and VLAN details.
In exec mode, show cisp client displays all the information for authorized host mac address and VLAN details.
■![]() In exec mode, show cisp registrations displays all the details of Interface(s) with CISP registered user(s).
In exec mode, show cisp registrations displays all the details of Interface(s) with CISP registered user(s).
■![]() In exec mode, show cisp interface <> displays information whether the device is supplicant or authenticator, version details, and peer mode.
In exec mode, show cisp interface <> displays information whether the device is supplicant or authenticator, version details, and peer mode.
CISP Prerequisites
■![]() 802.1x Authentication is already supported on IR829.
802.1x Authentication is already supported on IR829.
■![]() No support for CISP has been added to the IR809 platform, or for L3 ports on the IR829.
No support for CISP has been added to the IR809 platform, or for L3 ports on the IR829.
■![]() Before CISP is enabled, the 802.1x authentication must be completed as both supplicant and authenticator.
Before CISP is enabled, the 802.1x authentication must be completed as both supplicant and authenticator.
Flow Diagrams
■![]() On Successful authentication response from authenticator, it will start registration with Authenticator CISP.
On Successful authentication response from authenticator, it will start registration with Authenticator CISP.
■![]() Once End host is authorized or unauthorized, it will update (Add / Delete) to the authenticator CISP.
Once End host is authorized or unauthorized, it will update (Add / Delete) to the authenticator CISP.
■![]() If Access links or trunk uplink goes up or down, it will clear off the local CISP Client. Table and the Authenticator CISP will clear its Client Table.
If Access links or trunk uplink goes up or down, it will clear off the local CISP Client. Table and the Authenticator CISP will clear its Client Table.
■![]() If there is New MAC is learned or aged out, CISP will update on both sides.
If there is New MAC is learned or aged out, CISP will update on both sides.
■![]() If there is no response to CISP request frames, it will retransmit the CISP frames.
If there is no response to CISP request frames, it will retransmit the CISP frames.
■![]() Authentication Switch ACKs CISP frame after completing desired action.
Authentication Switch ACKs CISP frame after completing desired action.
Host Disconnect/Power down/Logoff
■![]() NEAT (Supplicant and Authenticator) utilizes the CISP protocol that securely transports authenticated hosts MAC addresses from a downstream Supplicant device to an upstream Authenticator device. CISP must be enabled on both ends.
NEAT (Supplicant and Authenticator) utilizes the CISP protocol that securely transports authenticated hosts MAC addresses from a downstream Supplicant device to an upstream Authenticator device. CISP must be enabled on both ends.
■![]() On a successful authentication response from the authenticator, it will start registration with Authenticator CISP. Once the authenticator authenticates the supplicant’s registration packet transfer between the supplicant and the authenticator. The following are examples of the CISP packet transfer after enable the debug cisp all:
On a successful authentication response from the authenticator, it will start registration with Authenticator CISP. Once the authenticator authenticates the supplicant’s registration packet transfer between the supplicant and the authenticator. The following are examples of the CISP packet transfer after enable the debug cisp all:
Once the End host is authorized or unauthorized, it will update (Add / Delete) to the authenticator CISP. The following shows an example:
IR829: Dot1x Supplicant Support on the L2 interface
IEEE 802.1X authentication enables the access point to gain access to a secured wired network. You can enable the access point as an 802.1X supplicant (client) on the wired network. A user name and password that are encrypted using the MD5 (IR8x9 platform supports only md5 method) algorithm can be configured to allow the access point to authenticate using 802.1X. Supplicant Topology illustrates the Supplicant Topology.
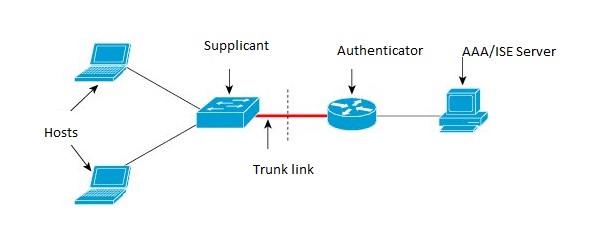
Refer to Workflow for the workflow.
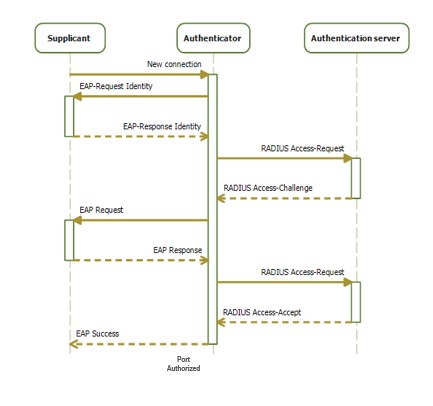
■![]() On networks that use IEEE 802.1X port-based network access control, a supplicant cannot gain access to the network until the 802.1X authenticator grants access. If your network uses 802.1X, you must configure 802.1X authentication information on the WAP device, so that it can supply it to the authenticator.
On networks that use IEEE 802.1X port-based network access control, a supplicant cannot gain access to the network until the 802.1X authenticator grants access. If your network uses 802.1X, you must configure 802.1X authentication information on the WAP device, so that it can supply it to the authenticator.
■![]() Supplicant starts with EAPOL start request to the Authenticator
Supplicant starts with EAPOL start request to the Authenticator
■![]() In Supplicant Request Authenticator send EAP request to supplicant.
In Supplicant Request Authenticator send EAP request to supplicant.
■![]() Supplicant sends the EAP response (W/MD5 Credentials) to Authenticator
Supplicant sends the EAP response (W/MD5 Credentials) to Authenticator
■![]() Authenticator sends the relay request to AAA via radius to Authenticate the supplicants
Authenticator sends the relay request to AAA via radius to Authenticate the supplicants
■![]() If the supplicant entry is already defined there, Radius sends accept to the Authenticator and the Supplicant port gets authorized by the authenticator
If the supplicant entry is already defined there, Radius sends accept to the Authenticator and the Supplicant port gets authorized by the authenticator
■![]() Now the supplicant works as Authenticator for the host connected to it. Same flow happens when host connects to the Supplicant
Now the supplicant works as Authenticator for the host connected to it. Same flow happens when host connects to the Supplicant
Sample Configuration to Support DOT1x Supplicant on the IR829
Note : More details can be found here:
https://www.cisco.com/c/en/us/support/docs/lan-switching/8021x/116681-config-neat-cise-00.html#anc14
The connection of the supplicant to the authenticator is already configured to be a trunk port (in contrast to access port configuration on the authenticator). At this stage, this is expected; configuration will dynamically change when the ISE returns the correct attribute.
Note : For support of Dot1x in IR829 dot1x code is added in IR829 for L2 interface.
IR829: LLDP (Link Layer Discovery Protocol) Support for 3rd party PoE devices
Previously, the IR829 supported PoE allocation/negotiation only for the PD (Powered Devices) which communicate using CDP (Cisco Discovery Protocol). With this release, support is added for Link Layer Discovery Protocol.
LLDP is a vendor-neutral CDP like neighbor discovery protocol that is used by network devices to advertise information about themselves to other devices on the network. LLDP supports a set of attributes that it uses to discover neighbor devices. These attributes contain type, length, and value descriptions and are referred to as TLVs. LLDP supported devices can use TLVs to receive and send information to their neighbors.
Details such as configuration information, device capabilities, and device identity can be advertised using this protocol. LLDP for Media Endpoint Devices (LLDP-MED) is an extension to LLDP that operates between endpoint devices such as IP phones and network devices such as switches. LLDP-MED specifically provides support for voice over IP (VoIP) applications and provides additional TLVs for capabilities discovery, network policy, power over Ethernet (PoE), inventory management, and location information. LLDP-MED contains power management TLV which allows PD (power device) to request power. Power TLV defines the format for power request.
Once power is applied to the port, LLDP-MED (Power TLV) is used to determine the actual power requirement of PDs and the system power budget is adjusted accordingly. The router processes the request and either grants or denies power based on the current power budget. If the request is granted, then the router simply updates the power budget. If the request is denied, the router turns OFF power to the port, generates a syslog message, and updates the power budget and LEDs.
If LLDP-MED is disabled or if the PD does not support the LLDP-MED power TLV, then the initial allocation value is used throughout the duration of the connection. No new CLIs are added and the following commands can be used to troubleshoot.
show power inline <interface> [<detail>]
Used in exec mode, this command shows inline power settings and status per interface or all respectively.
[no] lldp tlv-select power-management
Used in interface config mode, this command configures inline power support and optionally specifies a maximum inline power level in milliwatts.
show lldp {entry | interface | neighbors | traffic}
Used in exec mode, this command shows information for LLDP running status, specific neighbor entry, interface status and configuration, neighbor entries, and statistics.
Note : PoE port power priority (Critical, High, Low, default) and Power policing are not supported.
Related Documentation
The following documentation is available:
■![]() Cisco IOS 15.8M cross-platform release notes:
Cisco IOS 15.8M cross-platform release notes:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/15-8m/release/notes/15-8-3-m-rel-notes.html
■![]() All of the Cisco IR800 Industrial Integrated Services Router documentation can be found here:
All of the Cisco IR800 Industrial Integrated Services Router documentation can be found here:
http://www.cisco.com/c/en/us/support/routers/800-series-industrial-routers/tsd-products-support-series-home.html
■![]() All of the Cisco CGR 1000 Series Connected Grid Routers documentation can be found here:
All of the Cisco CGR 1000 Series Connected Grid Routers documentation can be found here:
http://www.cisco.com/c/en/us/support/routers/1000-series-connected-grid-routers/tsd-products-support-series-home.html
https://www.cisco.com/c/en/us/support/cloud-systems-management/iot-field-network-director/products-installation-and-configuration-guides-list.html
■![]() Cisco IOx Documentation is found here:
Cisco IOx Documentation is found here:
https://www.cisco.com/c/en/us/support/cloud-systems-management/iox/tsd-products-support-series-home.html
Caveats
Caveats describe unexpected behavior in Cisco IOS releases. Caveats listed as open in a prior release are carried forward to the next release as either open or resolved.
Note : You must have a Cisco.com account to log in and access the Cisco Bug Search Tool. If you do not have one, you can register for an account.
For more information about the Cisco Bug Search Tool, see the Bug Search Tool Help & FAQ.
Open Caveats
iox sched-policy 100 does not work
Symptoms : iox sched-policy setting 100 might shut down VDS and reload router.
Workaround : On a router reload with this configuration, the device mostly recovers. This is a troubleshooting only cli, not to be used often in deployments.
The command show cel 0 firmware does not show the correct output
Issue seen on IR829 with the MC7455 modem as well.
Workaround : There is no workaround.
Low power modem reset reason does not work
Symptoms : 'power_save_mode' scenario is not working as expected in 4G_LTE.
Workaround : NA, functionally the modem is fine, just the reset reason display has issue. Will be corrected in the next release.
Resolved Caveats
The following caveats are fixed with this release:
On the IR800 series, occasionally the GPS status would get stuck in "GPS location cannot be acquired" and not able to recover by itself until an IOS reboot.
■![]() CSCvm07801 - all IoT Routers
CSCvm07801 - all IoT Routers
On the IR800 series, SMS triggers a Cellular modem crash.
Symptoms : Upon receiving certain format SMS messages, modem crashes immediately.
Issue was reported on an IR829GW-LTE-VZ-AK9 with the MC7350 modem running IOS version 15.8-3M. FW version:SWI9X15C_05.05.58.01. However, this issue applies to both the MC73xx and MC74xx modems on all platforms.
■![]() CSCvm12409 - all IoT Routers
CSCvm12409 - all IoT Routers
Modem crash action set to wrong value on modem side.
Symptoms : The value was always set to 0 on the modem side.
■![]() CSCvm19614 - all IoT Routers
CSCvm19614 - all IoT Routers
The show cellular modem crash-action command displays the opposite of what is configured under the controller.
Symptoms : When "lte modem crash-action boot-and-hold" is configured under controller, the show cellular modem crash-action command displays "reset" and vice-versa.
Controller doesn't show cellular modem USB-Net Driver version.
Symptoms : The 'Driver Version' under the 'show controller cellular <interface>' command shows '<unknown>'.
Re-enable MPDN for the IR807 WP7601 sku and revert GobiUSBNet drivers to 2.50.
Symptoms : MPDN is not supported on the IR807 with the WP7601 modem running the 15.8(3)M release.
Workaround : Re-enable MPDN for the IR807 with the WP7601 modem and revert GobiUSBNet drivers to 2.50.
Ignition undervoltage millivolts is not persistent on reload
Symptoms : Ignition undervoltage threshold setting in millivolts is not persistent on reload. Volt value is intact, only the decimal value is not persistent.
Workaround : EEM to reconfigure millivolt threshold on device bootup:
[IOX-SS] Change monitrc to allow for infinite tries to restart secure storage
Symptoms : IOx came up in recovery mode because secure storage service didn’t come up.
Secure storage service log shows it failed to come up due to network connectivity to IOS. However, ping command went through fine when entered manually from Guest OS console.
Conditions : This is timing related, triggered by the missing IOS configurations needed for Guest OS networking connectivity at device power up. Secure storage service tried to connect to the server on IOS side and gave up after 5 retries.
Workaround : Restart guest OS VM after the IOS configuration change by "guest-os 1 restart". Or, save the configuration, and reload the router.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback