Plan the Software Upgrade
Before you upgrade the software version, prepare the router to ensure that the upgrade process is seamless.
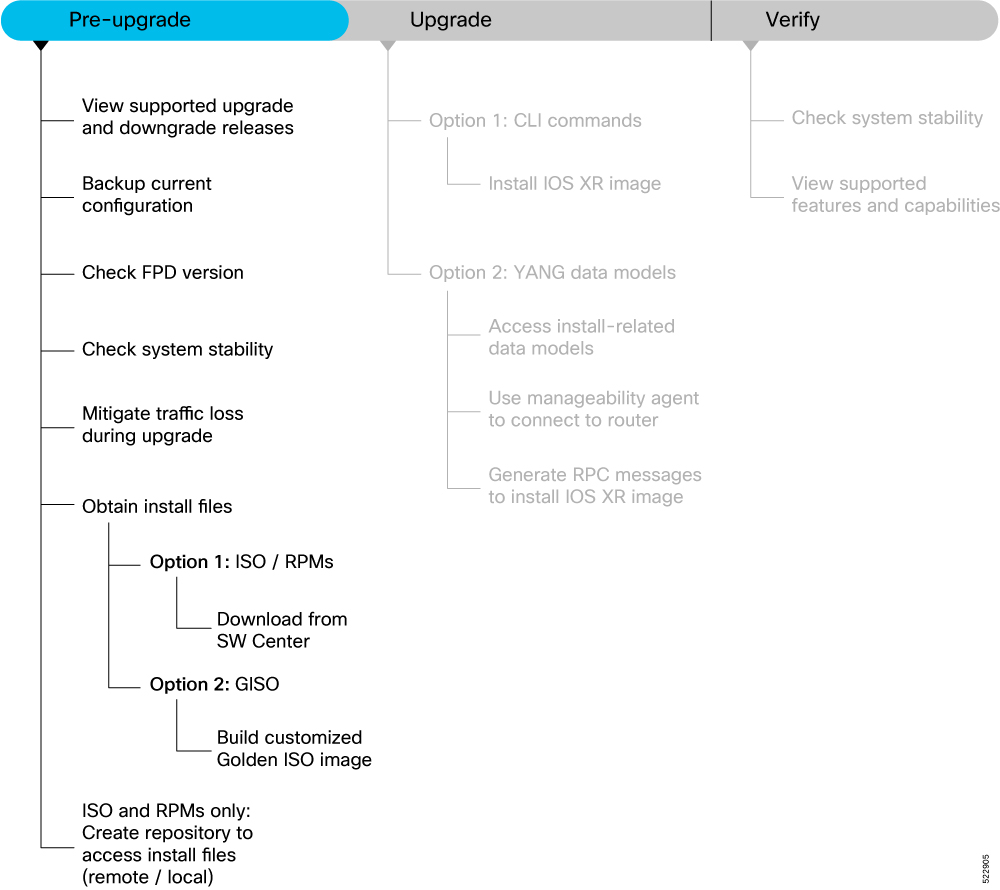
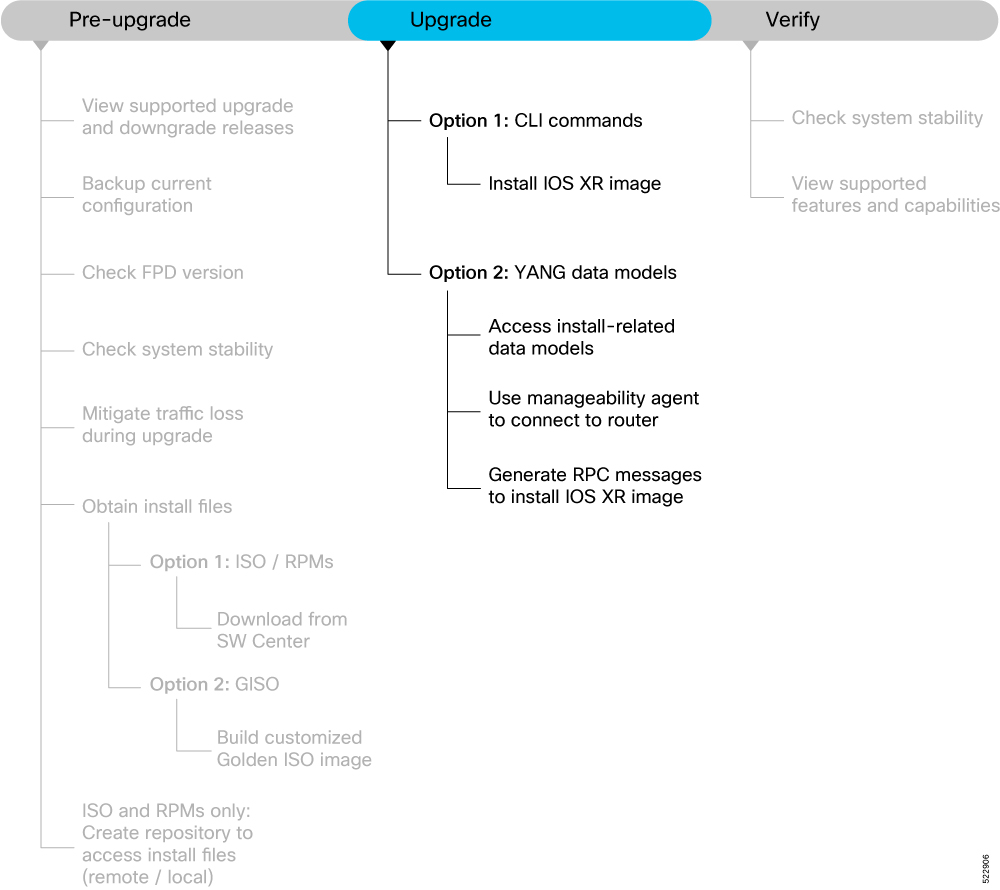
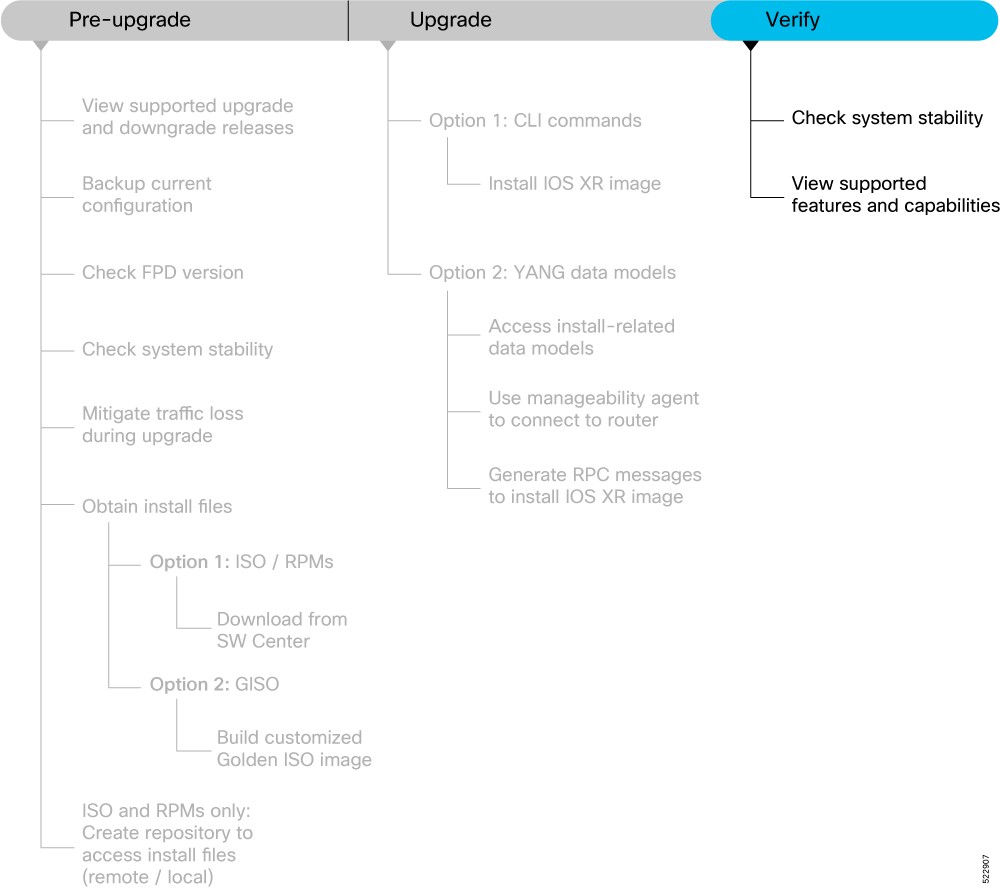
This section describes the following processes to prepare your router for an upgrade:
View Supported Upgrade and Downgrade Releases
Before you begin the upgrade, you must identify a Cisco IOS XR release that aligns with Cisco-recommended upgrade paths.
Use the show install upgrade-matrix running command to identify a supported target upgrade release, and prerequisites or limitations related to the specific software upgrade or downgrade. This command provides the following information:
-
Required bridging SMU RPMs
-
Blocking SMU RPMs
-
Unsupported hardware
-
Caveats or restrictions
In the following example, the output of the show install upgrade-matrix running command displays the upgrade restrictions.
Router#show install upgrade-matrix running
Matrix: XR version: 7.9.1, File version: 1.0
The upgrade matrix indicates that the following system upgrades are supported from the current XR version:
From To Restrictions
7.9.1 7.7.1 CSCab54345
7.9.1 7.7.2 -
7.9.1 7.7.3 -
7.9.1 7.7.4 -
7.9.1 7.7.5 -
7.9.1 7.7.6 -
7.9.1 7.8.1 -
In this example, you provide the current version and the target version that you want to upgrade the router. The output of the command displays the support information and dependencies between these two releases:
Router#show install upgrade-matrix running 7.5.2 7.3.1
Tue May 10 19:33:59.135 UTC
Upgrade matrix information for system upgrade: 7.5.2->7.3.1
XR system upgrade is supported, with the following restrictions:
The following fixes must be installed if any version of the package is installed.
-----------------------------------------
Ddts Name Version
-----------------------------------------
CSCab54345 xr-bgp 7.5.2
You can view support information using the following show commands or through the operational data.
| Command | Description |
|---|---|
show install upgrade-matrix running |
Displays all supported software upgrades from the current version according to the support data installed on the running system |
show install upgrade-matrix running v1 v2 |
Displays details about the software upgrades from version 1 to version 2 according to the support data installed on the running system |
show install upgrade-matrix running all |
Displays all supported software upgrades from any version according to the support data installed on the running system |
show install upgrade-matrix iso path-to-ISO |
Displays details about the software upgrade from the current version to the version of the target ISO according to the support data in both the running system and the ISO image |
show install upgrade-matrix iso path-to-ISO v1 v2 |
Displays details about the software upgrade from version 1 to version 2 according to the support data in the target ISO image |
show install upgrade-matrix iso path-to-ISO all
|
Displays all supported software upgrades from any version according to the support data in the target ISO image |
show install upgrade-matrix iso path-to-ISO running |
Displays details about the software upgrade from the current version to the version of ISO according to the support matrices in both the running system and the target ISO image |
show install upgrade-matrix rollback |
Displays details about the software upgrade from the current version to a version of a specific rollback point (indicated by an ID) according to the support matrices in both the running system and the rollback ID |
show install upgrade-matrix rollback ID v1 v2 |
Displays details about the software upgrade from version 1 to version 2 according to the support data in the specific rollback ID |
show install upgrade-matrix rollback ID all |
Displays all supported software upgrades from any version according to the support data in the specific rollback ID |
show install upgrade-matrix rollback running |
Displays details about the software upgrade from the current version to the version of the specific rollback ID according to the support matrices in both the running system and the rollback ID |
For release specific caveats see Release-specific Caveats and Workarounds section.
Backup Current Configuration
The ability to recover from a disaster is an essential part of any system maintenance plan. We recommend you backup the configurations in a secure remote location and verify that the transfer is a success, both before and after upgrade.
Procedure
|
Step 1 |
Create a backup of the running configuration to one of the following locations based on your requirement:
|
|
Step 2 |
Verify that the configuration is backed up. |
Check FPD Version
The router uses a number of Field Programmable Devices (FPDs) that are crucial for the function of route processors, line cards, shared port adapters (SPAs), SPA Interface Processors (SIPs), and fan trays. Before upgrading the software, check whether the latest FPDs are available on the router.
 Note |
FPD auto-upgrade is enabled by default on the Cisco 8000 series routers. However, we recommend that when updating to IOS XR Release 7.5.1, configure the fpd auto-upgrade enable command. |
Router#show hw-module fpd
FPD Versions
=================
Location Card type HWver FPD device ATR Status Running Programd
-------------------------------------------------------------------------------------------
0/RP0/CPU0 8800-RP 0.51 Bios S CURRENT 1.15 1.15
0/RP0/CPU0 8800-RP 0.51 BiosGolden BS CURRENT 1.15
0/RP0/CPU0 8800-RP 0.51 EthSwitch CURRENT 0.07 0.07
0/RP0/CPU0 8800-RP 0.51 EthSwitchGolden BP CURRENT 0.07
0/RP0/CPU0 8800-RP 0.51 TimingFpga CURRENT 0.11 0.11
0/RP0/CPU0 8800-RP 0.51 TimingFpgaGolden B CURRENT 0.11
0/RP0/CPU0 8800-RP 0.51 x86Fpga S NEED UPGD 0.23 0.23
0/RP0/CPU0 8800-RP 0.51 x86FpgaGolden BS CURRENT 0.24
0/RP0/CPU0 8800-RP 0.51 x86TamFw S CURRENT 5.05 5.05
0/RP0/CPU0 8800-RP 0.51 x86TamFwGolden BS CURRENT 5.05
In this example, x86Fpga
FPD device needs an upgrade. You must ensure that FPDs are upgraded before upgrading the router.
Procedure
|
Step 1 |
To manually upgrade FPDs, use the upgrade hw-module fpd command.
|
||||
|
Step 2 |
Reload the individual nodes that require an upgrade by using the reload location node-location command.
|
||||
|
Step 3 |
You can enable automatic upgrade of FPD by using the fpd auto-upgrade enable command. To automatically upgrade all FPDs, use: Usage Guidelines—Online Insertion of IMs When an IM with a lower FPD version is inserted, one of the following scenarios apply:
Usage Guidelines—Online Insertion of RPs When fpd auto-upgrade is enabled and a new RP is inserted, the system upgrades the RP FPDs automatically with the latest FPDs. Verify that all nodes that required an upgrade show an updated status of
|
Upgrading FPDs Using Yang Data Models
YANG is a data modeling language that helps to create configurations, retrieve operational data and execute actions. The router acts on the data definition when these operations are requested using NETCONF RPCs. The data model handles the following types of requirements on the routers for FPD:
| Operational Data | Native Data Model |
|---|---|
| Auto Upgrade: Enabling or disabling of automatic upgrade of FPD. | Cisco-IOS-XR-fpd-infra-cfg.yang |
Check System Stability
System stability checks are essential to measure the efficiency and ability of an upgrade to function over an extended period.
At the EXEC prompt, execute the following commands to assess basic system stability checks before and after the software upgrade.
|
Command |
Reason |
Workaround |
|---|---|---|
|
Verify that all nodes are in |
NA |
|
|
Verify that a standby RP is available, and the system is in |
NA |
|
|
Or Or |
Verify that all necessary interfaces are |
NA |
|
Verify that the proper set of packages are active |
NA |
|
|
Verify that the proper set of committed packages are same as active |
Execute ‘install commit’ command |
|
|
Verify/fix configuration file system |
NA |
|
|
Ensure all the FPD versions status are CURRENT |
Execute |
|
|
Display the current state of the disk storage media |
To free up space, remove older .iso image files and bug fix .tar files. |
|
|
Display the current state of the root filesystem (rootfs). By default, the following files are stored in rootfs :
|
The installation is blocked if it utilizes more than 92% of the disk space on the rootfs . To avoid this, we recommend maintaining:
To free up space in rootfs :
|
|
|
Show chassis inventory information |
NA |
|
|
Capture show logging to check for any errors |
NA |
Mitigate Traffic Loss During Upgrade
During an upgrade, any traffic routed through the device is affected. To minimize traffic loss during the upgrade, do the following:
For OSPF, configure the router to advertise a maximum metric so that other devices do not prefer the router as an intermediate hop in their SPF calculations:
Router(config-ospf)#max-metric router-lsaFor ISIS, set the overload bit for a fixed amount of time. This ensures that the router does not receive transit traffic while the routing protocol is still converging:
Router(config-isis)#set-overload-bit on-startup <timeout>Obtain Install Files
You can obtain the install files based on one of the following options that is best suited to your network:
-
Base ISO and Optional RPMs: You can upgrade the software through the standard method where you install the ISO followed by the required RPMs.
-
Golden ISO: You can build a customized golden ISO (GISO) image with the base ISO and the required RPMs to automatically upgrade the software.
Standard ISO and RPMs
Download Install Files from Cisco Software Center
Procedure
|
Step 1 |
Access the Cisco Software Download page. For optimum website experience, we recommend any of the following browsers: Google Chrome, Mozilla Firefox or Internet Explorer. |
|
Step 2 |
Select the following:
|
|
Step 3 |
From the left pane, select the release. For the selected release, the Software Download page displays the downloadable files. For more information, see . |
|
Step 4 |
Use your Cisco login credentials to download the files. |
Golden ISO
Build Customized Golden ISO Image
|
Feature Name |
Release Information |
Description |
|---|---|---|
|
Build Golden ISO (GISO) Using gisobuild.py Tool |
Release 7.5.1 |
This feature allows you to build your GISO image without support from Cisco. You can now select the install files, add your RPMs, repackage them as a custom image, and install the image. In previous releases, you had to contact Cisco to get your GISO built. |
Golden ISO (GISO) is a customized bootable ISO that you can build to suit your network’s installation requirement. You can customize the installable image to include the standard base image with the basic functional components, and add additional RPMs, SMUs and configuration files based on your requirement.
GISO image contains the following files:
-
base image (ISO) with basic functional components
-
optional packages (RPMs) with additional networking functionality
-
bug fixes (SMUs)
For Cisco IOS XR Release 7.5.1 or later, you can build your own GISO image using the gisobuild.py tool. This tool is available on the Github repository.
For releases earlier than Cisco IOS XR Release 7.5.1, contact Cisco Technical Support to build the GISO.
 Note |
The GISO build tool verifies the RPM dependencies and RPM signatures. The GISO build process fails if the RPM is unsigned or incorrectly signed. |
Before you begin
To run and invoke the gisobuild.py tool:
-
Ensure that your local environment provides all the required executables for the tool. For the list of executables and their versions, see Requirements section in gisobuild toolkit for IOS-XR available in the Github repository.
-
Alternatively, you can also run gisobuild.py tool on a Linux system using docker build mode. This method provides you the option to avoid the above setup. For more information, see the Invocation section in the gisobuild toolkit for IOS-XR available in the Github repository.
Procedure
|
Step 1 |
Download all the relevant files to the system where you build GISO image:
|
|
Step 2 |
Run the Example:The tool uses the input parameters to build the GISO image. The following example shows building a GISO image using You can specify multiple values in the For the |
Create Repository to Access Install Files
A Repository is a directory where the ISO, RPMs, and their metadata are downloaded. The package manager uses this repository to query the packages.
The repository can either be created locally on the router, or on a remote location that can be accessed through FTP, HTTP, or HTTPS. In a repository, you can create directories based on different Cisco IOS XR platforms, releases or both. You can create and use multiple repositories. The files to be installed can saved in the local repository, remote repository or a combination of both.
 Note |
The Golden ISO (GISO) method does not require you to create a repository. However, you can still install the GISO from a remote repository. |
 Important |
Each package is named based on its name, version, software release, and architecture. Hence, any packages that have these attributes in common and differ only by platform are indistinguishable. We recommend that you create different repositories for different platforms and releases. |
Create Remote Repository
We recommend that you create an external remote repository that acts as a central repository to be used across devices. This eliminates the need to copy files for future updates to each router individually. It also serves as a single source when new RPMs (bug fixes, packages, updates) are made available.
The remote repository is available only through the Management Ethernet interface of the router. The server hosting the external repository must be able to reach the router using the address of the loopback interface in the VRF. If a VRF has more than one loopback interface, the loopback with the lowest-numbered loopback name is selected. For example, Loopback1 is selected over Loopback2. When using VRF, configure the repository to be reachable using a non-default VRF table. If the repository is reachable through an address in a VRF, specify the name of the VRF.
The following instructions are applicable to Linux distribution systems.
Procedure
|
Step 1 |
Create a directory on the server and copy the ISO and all RPMs. For example, name the directory as |
||
|
Step 2 |
Extract the files if the RPM files are archived (.tar format) or compressed (.tgz or .gz format). The files hierarchically arrange in sub directories under the main directory. |
||
|
Step 3 |
Convert the directory to a repository using Example:
|
||
|
Step 4 |
Configure the remote repository on the router. Example:where:
|
||
|
Step 5 |
Verify connectivity to the server and check the contents of the repository. Example:System logs record useful information during the creation of the repository. Check the logs to verify that the repository is valid. |
Create Local Repository on the Router
The router can also serve as a repository to host the RPMs. However, you must be a root-lr user with access to the router shell. Using a local repository removes the need to set up an external server for software
installation. In this method, the image files are copied directly to the router and used to create a repository locally.
 Note |
We do not recommend creating a local repository if you are upgrading multiple routers. |
Procedure
|
Step 1 |
Create a new directory locally on the router's /harddisk:. For example, name the directory as |
|
Step 2 |
Copy the required RPMs and ISO files (using |
|
Step 3 |
Access the shell of the router and untar the RPMs. Example: |
|
Step 4 |
Exit from the shell. |
|
Step 5 |
Configure the local repository. Example:where:
|
|
Step 6 |
Check the contents of the repository. Example: |
 Feedback
Feedback