cnBR Prerequisites
The following prerequisite components are required to install, operate, and manage a Cisco cnBR. The prerequisites are:
-
The Cisco cnBR server
-
The Cisco Operations Hub server
-
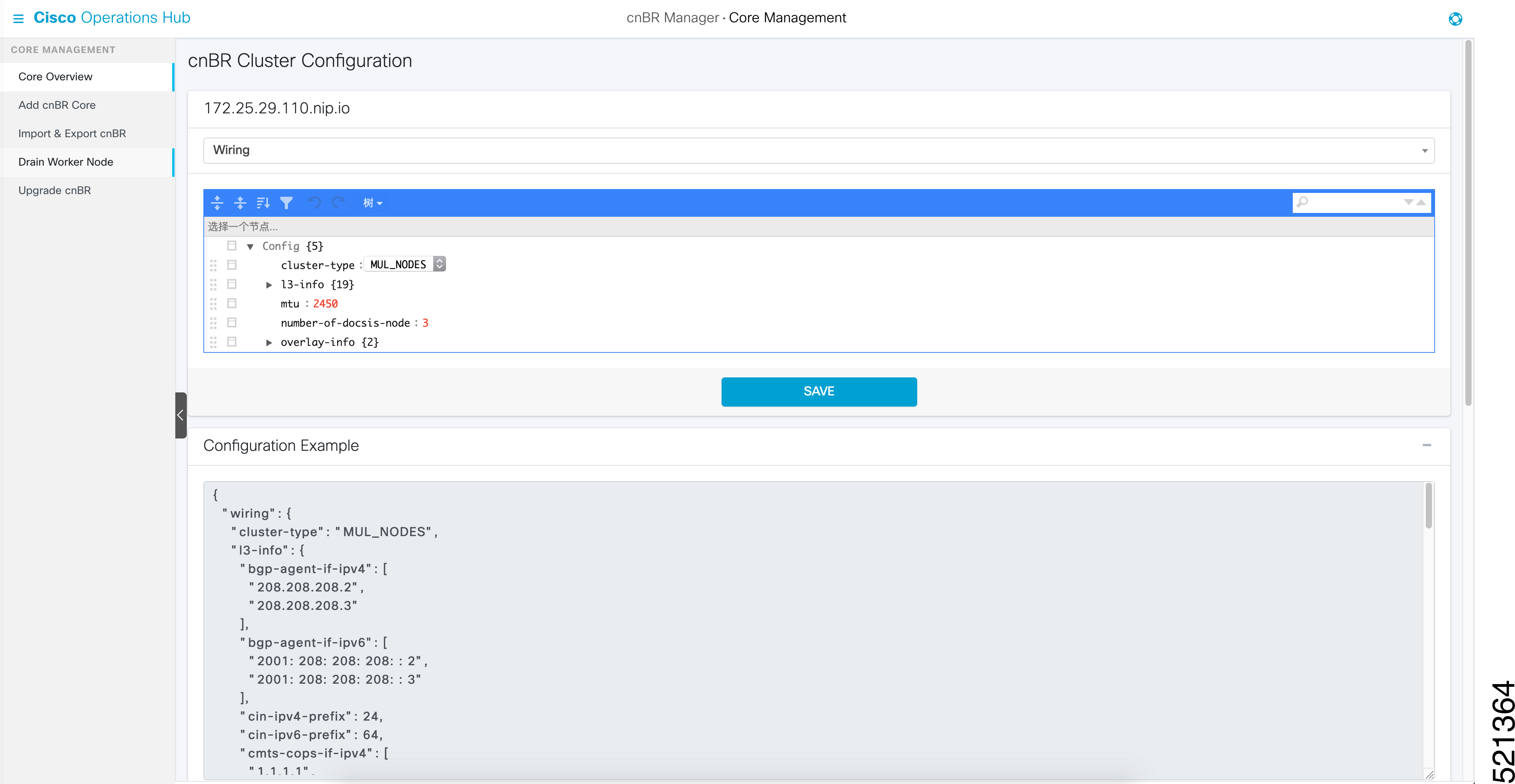
The Cisco cnBR topology
-
VMware vSphere virtualization platform
Prerequisites required for the Cisco cnBR server
The Cisco cnBR runs exclusively on a Unified Computing System (UCS) server that is imaged with an VMware ESXi hypervisor.
-
Cisco UCS server requirement
Three Cisco UCS C220 M5 servers are required to run Cisco cnBR. The supported Cisco UCS servers are UCSC-C220-M5SX.
The minimum compute, storage, and networking requirements for the Cisco UCS server are listed in the following table.
Table 1. Minimum Requirements Cisco UCS Server Component
Specification
Chassis
UCSC-C220-M5SX
Processor
2 x Intel 6248 2.5GHz/150W 20C/27.5MB DCP DDR4 2933 MHz
Memory
384GB DDR4-2933-MHz RDIMM
Storage
2 x 240 GB SATA M.2
4 x 800GB SSD
Storage Controller
Cisco Boot optimized M.2 RAID Controller
Cisco 12G Modular RAID controller with 2GB cache
NIC
2 x Intel XL710-QDA2 (40G)
-
VMware requirements
-
Hypervisor - VMware ESXi 6.5, minimum recommended patch release for security updates ESXi650-202006001, or VMware ESXi 6.7, minimum recommended patch release for security updates ESXi670-202006001
-
Host Management - VMware vCenter Server 6.5 or VMware vCenter Server 6.7
If the VMware ESXi 6.7 is installed on host, ensure that the vCenter version is VMware vCenter Server 6.7.
-
Prerequisites required for the Cisco Operations Hub server
-
Cisco UCS server requirement
Three Cisco UCS C220 M5 servers are required to run Cisco cnBR. The supported Cisco UCS servers are UCSC-C220-M5SX.
The minimum compute, storage, and networking requirements for the Cisco UCS server are listed in the following table.
Table 2. Minimum Requirements Cisco UCS Server Component
Specification
Chassis
UCSC-C220-M5SX
Processor
2 x Intel 6248 2.5GHz/150W 20C/27.5MB DCP DDR4 2933 MHz
Memory
384 GB DDR4-2933-MHz RDIMM
Storage
2 x 240 GB SATA M.2
4 x 800GB SSD
Storage Controller
Cisco Boot optimized M.2 RAID Controller
Cisco 12G Modular RAID controller with 2GB cache
NIC
2 x Intel XL710-QDA2 (40G)
-
VMware requirements
-
Hypervisor - VMware ESXi 6.5, minimum recommended patch release for security updates ESXi650-202006001, or VMware ESXi 6.7, minimum recommended patch release for security updates ESXi670-202006001
-
Host Management - VMware vCenter Server 6.5 or VMware vCenter Server 6.7
If the VMware ESXi 6.7 is installed on host, ensure that the vCenter version is VMware vCenter Server 6.7.
-
-
Browser support
For the Cisco cnBR, the Cisco Operations Hub functionality is supported for the following browser versions:
-
Mozilla Firefox 78.0 and later
-
Google Chrome 83 and later or Google Chrome 84 and later
-
Microsoft Edge 44 and later
-
Prerequisites required for the Cisco cnBR topology
-
Cisco cnBR Data Switch
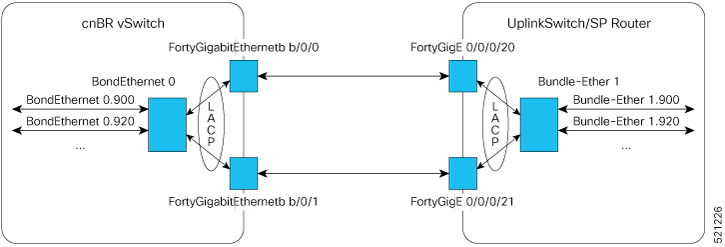
You must use a data center switch with the requisite 40G port density between the Cisco cnBR servers and the service provider router to aggregate the Cisco cnBR data path links.
-
Management Switch
A dedicated data center switch can be used for Cisco cnBR and Cisco Operations Hub management traffic. The Cisco cnBR and Cisco cnBR servers provide 1G, 10G, and 40G network interface connectivity options for the different management networks that are used in the system. The management networks can be VMware ESXi host management, Cisco cnBR and Cisco Operations Hub virtual machine cluster management, and the Cisco Integrated Management Controller (IMC) Lights-Out-Management.
-
Service Provider Router
The SP Router is responsible for forwarding L3 packets between the core network, RPHY CIN, and Cisco cnBR. The SP Router and Cisco cnBR establishes connections through BGP, SG, RPHY-core for RPD session setup and traffic forwarding.
We recommend the following Cisco Network Convergence System 5500 Series models:
-
NCS-55A1-36H-S
-
NCS-55A1-24H
The required software version must be Cisco IOS XR 6.5.3 or later.
-
-
DHCP Server
A standard Dynamic Host Configuration Protocol (DHCP) server is required, and typically included in an existing DOCSIS infrastructure. For example, the DHCP server included is the Cisco Network Registrar (CNR).
-
PTP Server Configuration
A Precision Time Protocol (PTP) server is required and typically included in an existing DOCSIS infrastructure. For example, an OSA 5420.
-
TFTP Server
A standard Trivial File Transfer Protocol (TFTP) server is required and typically included in an existing DOCSIS infrastructure.
-
RPHY CIN
A Remote PHY Converged Interconnect Network (CIN) is required. A Remote PHY Device, and Cable Modems are also required. For example, Cisco Smart PHY 600 Shelf.
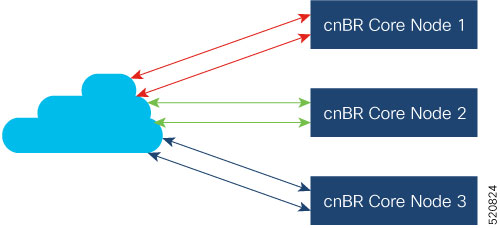
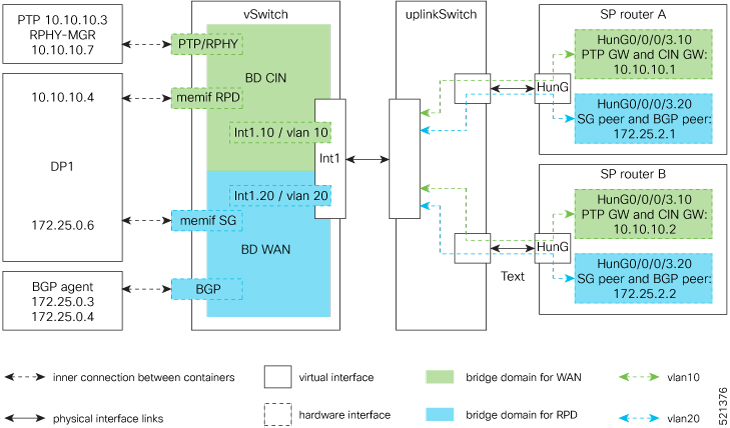
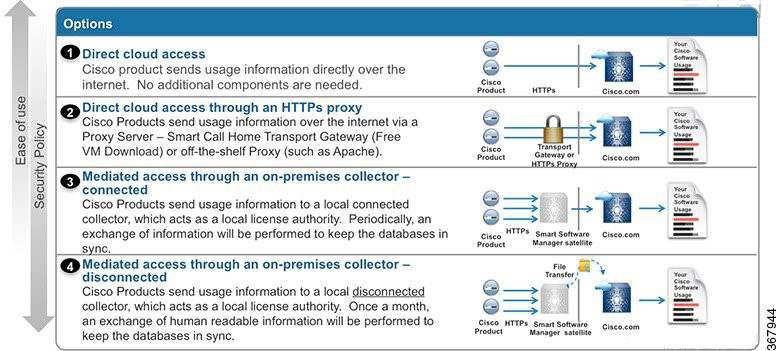
The following image is a simplified, high-level overview of an end-to-end system and shows how these Cisco cnBR components are connected in the topology with provisioning systems and a Remote PHY CIN: Figure 1. Simplified cnBR Topology 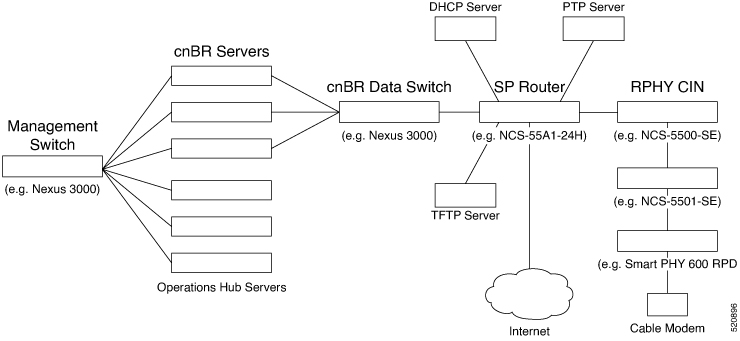
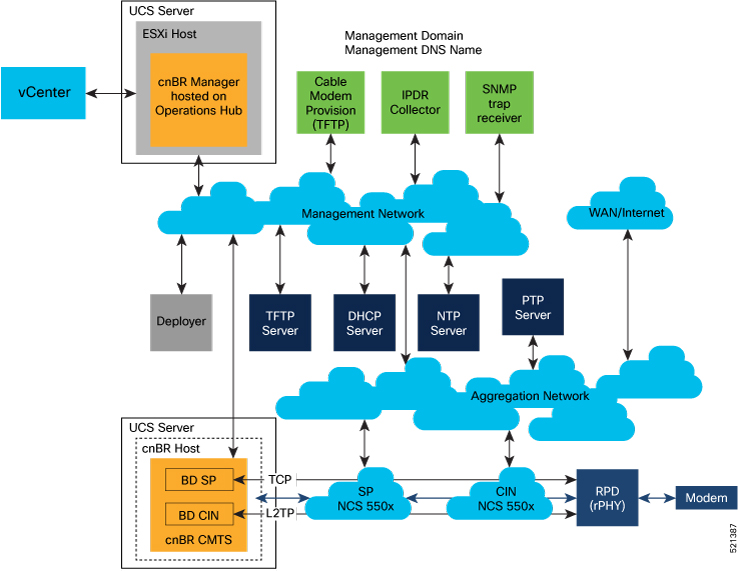
Prerequisites required for the VMware vSphere virtualization platform
VMware is a mandatory component for the Cisco Operations Hub server, and is necessary for the deployment topology. An ESXi host is required to run the cnBR Deployer VM.
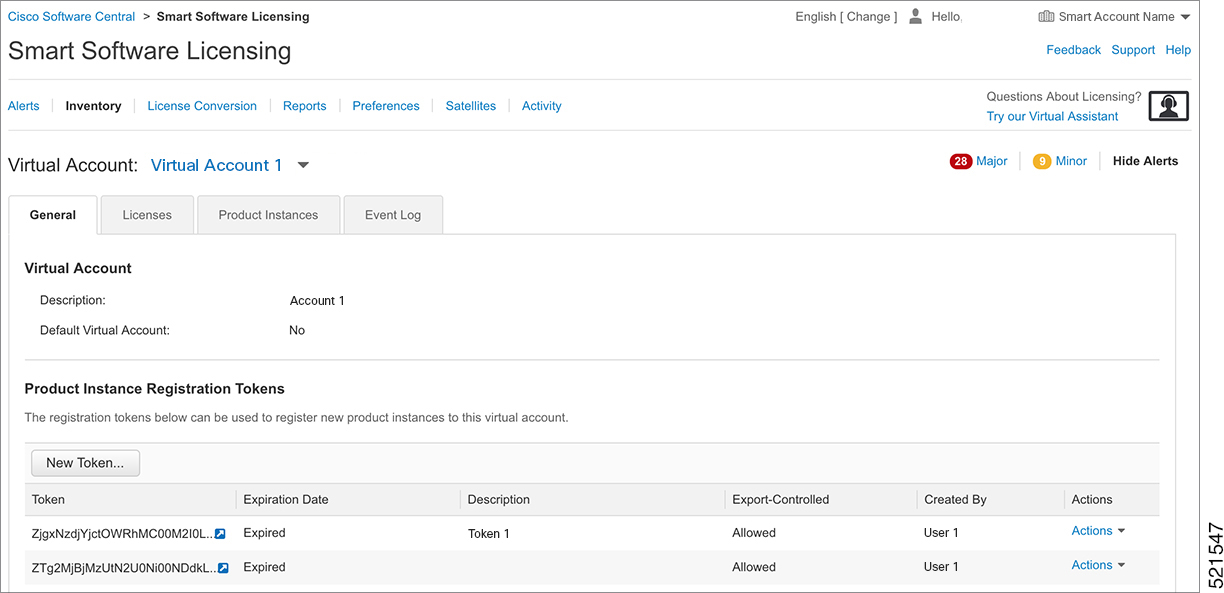
A generalized Cisco cnBR deployment with the Cisco Operations Hub and Cisco cnBR core hosted in VMware clusters is depicted in the following image:
-
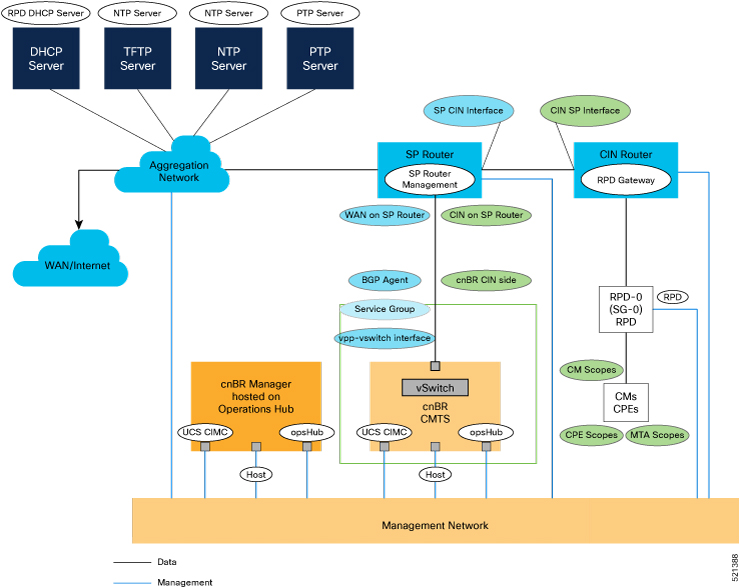
Networks
The following table provides guidance for the networks that are needed in the management, WAN, and CIN routing domains:
Table 3. Network Information for Routing Domains Name
Subnet Mask
Function
Management
-
2 addresses for each cluster
-
Operations Hub/cnBR UCS
-
1 for each cluster
-
1 for each service device
Management
CIN
Network requirements for each customer
Connection RPD and CCAP core
WAN
Network requirements for each customer
Internet access for CPE
cnBR CIN side
Network requirements for each customer
-
BGP network to SP router
Network requirements for each customer
Management
Network for data
Network requirements for each customer
-
SG IP cnBR side
Network requirements for each customer
The peer IP for Service Group on cnBR
RPD address pool
Customer selected
DHCP scope for RPD sized to cover total number of RPDs
DHCP scope for CM
Customer selected
-
DHCP scope for CPE
Customer selected
-
DHCP scope for MTA
Customer selected
-
You must provide domain and DNS name for the management network.
-
-
Device Addresses
The followings tables provide information on the IP address that is needed for device and router interfaces.
-
Management IP Address: Each management interface that is listed in the following table requires 1 IP address:
Table 4. Management Interface and Associated IP Addresses Device name
Number of Addresses
CIMC cnBR
1 per cnBR UCS
ESXi cnBR
1 per cnBR UCS
CIMC Operations Hub
1 per Operations Hub UCS
ESXi Operations Hub
1 per Operations Hub UCS
cnBR
1 per cnBR Cluster
Operations Hub
1 per Operations Hub Cluster
Deployer
1
vCenter
1
SP router
1
CIN router
1
-
DOCSIS Network Addresses: The following table lists the DOCSIS network-related information:
Table 5. DOCSIS Network-Related Information Device Name
Network Name
Description
Number of Addresses
SP router to CIN
CIN
SP connection to CIN router
1
CIN router to SP
CIN
CIN connection to SP router
1
SP router to WAN
WAN
SP connection to WAN/Internet
1
RPD Gateway
CIN
RPD gateway router Address
1
cnBR CIN side
CIN
cnBR connection to CIN
Customer specific
BGP Agent
WAN
WAN router BGP Agent IP
Customer specific
Service Group
WAN
Service Group WAN IP
Customer specific
WAN on SP Router
WAN
SP connection to WAN network
Customer specific
-
Customer Provisioned Services: The following table lists the various customer services:
Table 6. Customer Provisioned Services Service
Notes
DHCP
Needed for both RPD and subscriber devices
TFTP
RPD only uses it during software upgrade
TOD
Time of day clock
PTP
One connection that is required for the cnBR and for each RPD
NTP
Network Time Protocol Server
DNS
Domain Name Server
-

 ).
).
 Feedback
Feedback