Configuring Inter-VLAN Routing with Catalyst 3750 Series Switches
Available Languages
Contents
Introduction
This document provides a sample configuration for inter-VLAN routing using two Catalyst 3750s series switches stacked together running EMI software in a typical network scenario. The document uses a Catalyst 2950 series switch and a Catalyst 2948G switch as Layer 2 (L2) closet switches connecting to the stack of Catalyst 3750s. The stack of Catalyst 3750s is also configured for a default route for all traffic going to the Internet with the next hop pointing to a Cisco 7200VXR router, which can be substituted by a firewall or other routers. Configuring inter-VLAN routing on a single 3750 is the same as configuring this feature on a Catalyst 3550 series switch. For information on configuring inter-VLAN routing on a single Catalyst 3750 series switch, refer to Configuring Inter-VLAN Routing with Catalyst 3550 Series Switches.
Before You Begin
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Prerequisites
Before attempting this configuration, please ensure that you meet the following prerequisites:
-
knowledge of creating VLANs; for more information, refer to Creating Ethernet VLANs on Catalyst Switches
-
knowledge of creating VLAN trunks; for more information, refer to the Configuring VLAN Trunking section of Configuring VLANs
Components Used
The information in this document is based on the software and hardware versions below.
-
Two Catalyst 3750G-24T switches running 12.1(14)EA1 EMI Software Release stacked together
-
Catalyst 2950G-48 running 12.1(12c)EA1 EI Software Release
-
Catalyst 2948G running 6.3(10) Software Release
Note: The configuration from the Cisco 7200VXR is not relevant and, therefore, is not shown in this document.
The information presented in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If you are working in a live network, ensure that you understand the potential impact of any command before using it.
Background Theory
In a switched network, VLANs separate devices into different collision domains and Layer 3 (L3) subnets. Devices within a VLAN can communicate with one another without requiring routing. On the contrary, devices in separate VLANs require a routing device to communicate with one another.
L2 only switches require a L3 routing device (either external to the switch or in another module on the same chassis). A new breed of switches, however, (for example, 3550 and 3750) incorporate routing capability within the switch. The switch receives a packet, determines that it belongs to another VLAN, and sends the packet to the appropriate port on the other VLAN.
A typical network design segments the network based on the group or function the device belongs to. For example, the engineering department VLAN would only have devices associated with the engineering department, while the finance VLAN would only have finance related devices. If routing is enabled, the devices in each VLAN can talk to one another without all the devices being in the same broadcast domain. Such a VLAN design also has the added benefit of allowing the administrator to restrict communication between VLANs using access-lists. In our example, the engineering VLAN could be restricted (using access-lists) from accessing devices on the finance VLAN.
IP Routing on a Stack of 3750s
On a stack of Catalyst 3750 switches, the software running on the master determines the capabilities of the whole stack. If the master switch is running an EMI image, the whole stack will support the full set of supported routing protocols (such as Open Shortest Path First (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), and such) even if the other stack members are just running an SMI image. However, it is advisable to have the same software running on the different stack members. If the stack master fails, you would lose the extended routing capabilities if the other members run an SMI image as opposed to the EMI image of the former master.
A stack of Catalyst 3750 switches appears to the network as a single router, independent to which of the stack switches the routing peer is connected. A router will create a single adjacency with a stack of 3750 routers.
The stack master performs the following tasks:
-
Initialization and configuration of the routing protocols
-
Generation of routing protocol messages
-
Processing of received routing protocol messages
-
Generating and distribution of the Distributed Cisco Express Forwarding (dCEF) database to the different stack members
-
The MAC address of the master is used as source MAC of routed packets
-
Packets that need process switching are handled by CPU of the master
The stack members perform the following tasks:
-
They act as routing standby switches which can take over when the stack master fails
-
Programming of the routes in the dCEF database in hardware
When the master fails, the stack members will (apart from a momentarily interruption) continue to forward the packets in hardware while no protocols are active.
After a new master has been selected following a master failure, the newly elected master will start sending gratuitous ARPs with its own MAC address in order to update the devices in the network with the new MAC address that will be used to rewrite the routed packets.
For more information regarding 3750 switch stack behavior and configuration, refer to the Managing Switch Stacks documentation.
Related Products
This configuration can also be used with the following hardware and software versions.
-
Any Catalyst 3750 switch running EMI software or SMI version 12.1(14)EA1 and later.
-
Any Catalyst 2900XL/3500XL/2950/3550 or Catalyst OS switches for access layer switch.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: To find additional information on the commands used in this document, use the Command Lookup Tool (registered customers only) .
Network Diagram
This document uses the network setup shown in the diagram below.
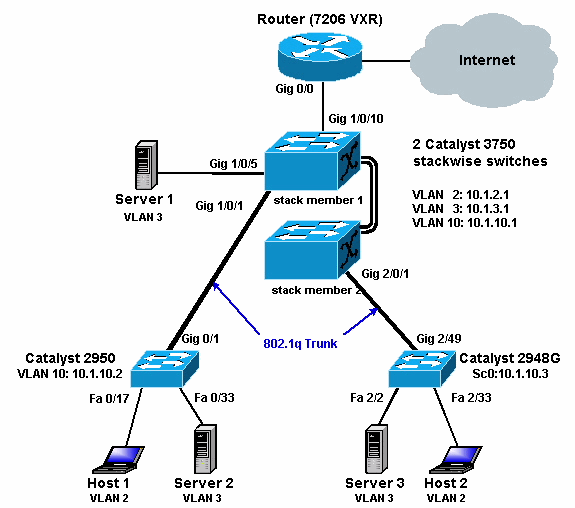
The above diagram shows a small sample network with the stack of Catalyst 3750s providing inter-VLAN routing between the various segments.
The following are the three user defined VLANs:
-
VLAN 2 - user VLAN
-
VLAN 3 - server VLAN
-
VLAN 10 - management VLAN
The default gateway configured on each server and host device should be the corresponding VLAN interface IP address on the stack of 3750s. For example, for servers, the default gateway is 10.1.3.1. The Catalyst 2950 is trunked to the top Catalyst 3750 switch (stack master) and the Catalyst 2848G is trunked to the bottom Catalyst 3750 switch (stack member).
The default route for the stack is pointing to the Cisco 7200VXR router. The stack of 3750s uses this default route to route traffic destined for the Internet. Therefore, traffic for which the 3750s does not have a routing table entry is sent to the 7200VXR for proccessing.
Practical Tips
-
In this diagram, the management VLAN is separate from the user or server VLAN. This VLAN is different from the user or server VLAN. This is done to prevent the management of switches from being affected by potential broadcast/packet storms in the user or server VLAN.
-
VLAN 1 is not used for management. All ports in Catalyst switches default to VLAN 1, and any devices connected to non-configured ports will be in VLAN 1. This may cause potential issues for the management of switches, as explained above.
-
A Layer 3 (L3) (routed) port is used to connect to the default gateway port. In this diagram, a Cisco 7200VXR router could be easily replaced by a firewall that connects to the Internet gateway router.
-
A routing protocol is not run between the stack of Catalyst 3750s and the Internet gateway router. Instead, a static default route is configured on the 3750. This setup is preferred if there is only one route to the Internet. Make sure to configure static routes (preferably summarized) on the gateway router (7200VXR) for subnets that can be reached by the Catalyst 3750s. This step is very important since routing protocols are not being used.
-
If you need additional bandwidth for the uplink ports, you can configure EtherChannel. Configuring EtherChannel also provides link redundancy in case of a link failure.
Configurations
This document uses the configurations shown below.
As you can see below, although there are two Catalyst 3750 switches stacked together, they are configured just as if they had only one switch. Both switches have twenty-four 10/100/1000 interfaces and in the configuration they show up as gigabit Ethernet 1/0/1 up to gigabit 1/0/24 for the first switch, and gigabit 2/0/1 up to gigabit 2/0/24 for the second one. So looking at the configuration, it appears as if there is just one switch with two modules that each have 24 ports.
Extending this exercise to 3, 4, 5, and so on, switches in a stack would appear similar, but for each switch that is added to the stack, it shows up in the configuration as if one module is added to the switch.
| Cat3750 (Cisco Catalyst 3750G-24T) |
|---|
C3750G-24T#show run Building configuration... Current configuration : 2744 bytes ! version 12.1 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname C3750G-24T ! ! ip subnet-zero ip routing ! no ip domain-lookup ! spanning-tree mode pvst no spanning-tree optimize bpdu transmission spanning-tree extend system-id ! ! ! interface GigabitEthernet1/0/1 description To 2950 switchport trunk encapsulation dot1q ! !--- Dot1q trunking (with negotiation) is configured on the L2 switch. !--- If DTP is not supported on the far switch, issue the !--- switchport mode trunk command !--- to force the switch port to trunk mode. !--- Note: The default trunking mode is dynamic auto. If a trunk link !--- is established using default trunking mode, it does not appear !--- in the configuration even though a trunk has been established on !--- the interface. Use the show interfaces trunk command to verify the !--- trunk has been established. ! interface GigabitEthernet1/0/2 ! !--- Output suppressed. ! interface GigabitEthernet1/0/5 description to SERVER_1 !--- Configure the server port to be in the server VLAN (VLAN 3). switchport access vlan 3 !--- Configure the port to be an access port to !--- prevent trunk negotiation delays. switchport mode access !--- Configure port-fast for initial STP delay. !--- Refer to Using PortFast and Other Commands to Fix Workstation !--- Startup Connectivity Delays for more information. spanning-tree portfast ! interface GigabitEthernet1/0/6 ! !--- Output suppressed. ! interface GigabitEthernet1/0/10 description To Internet_Router !--- Port connected to router is converted into a routed (L3) port. no switchport !--- IP address is configured on this port. ip address 200.1.1.1 255.255.255.252 ! interface GigabitEthernet1/0/21 ! !--- Output suppressed. ! interface GigabitEthernet1/0/22 ! interface GigabitEthernet1/0/23 ! interface GigabitEthernet1/0/24 ! interface GigabitEthernet2/0/1 description To 2948G switchport trunk encapsulation dot1q ! !--- Output suppressed. ! interface GigabitEthernet2/0/23 ! interface GigabitEthernet2/0/24 ! interface Vlan1 no ip address shutdown ! interface Vlan2 description USER_VLAN !--- This IP address would be the default gateway for users. ip address 10.1.2.1 255.255.255.0 ! interface Vlan3 description SERVER_VLAN !--- This IP address would be the default gateway for servers. ip address 10.1.3.1 255.255.255.0 ! interface Vlan10 description MANAGEMENT_VLAN !--- This IP address would be the default gateway for other L2 switches ip address 10.1.10.1 255.255.255.0 ! ip classless !--- This route statement will allow the 3550 to send Internet traffic to !--- its default router (in this case, 7200VXR Fe 0/0 interface). ip route 0.0.0.0 0.0.0.0 200.1.1.2 ip http server ! ! line con 0 exec-timeout 0 0 line vty 0 4 exec-timeout 0 0 login line vty 5 15 login ! end C3750G-24T# |
Note: Since the 3750 is configured as a VLAN Trunk Protocol (VTP) server, the VTP configuration is not displayed by the switch. This is standard behavior. The commands below are used on this switch to create a VTP server with the three user-defined VLANs from global configuration mode.
C3750G-24T(config)#vtp domain cisco C3750G-24T(config)#vtp mode server C3750G-24T(config)#vlan 2 C3750G-24T(config-vlan)#name USER_VLAN C3750G-24T(config-vlan)#exit C3750G-24T(config)#vlan 3 C3750G-24T(config-vlan)#name SERVER_VLAN C3750G-24T(config-vlan)#exit C3750G-24T(config)#vlan 10 C3750G-24T(config-vlan)#name MANAGEMENT
| Cat2950 (Cisco Catalyst 2950G-48 Switch) |
|---|
Cat2950#show running-config Building configuration... Current configuration : 2883 bytes ! version 12.1 no service single-slot-reload-enable no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname Cat2950 ! ! ip subnet-zero ! spanning-tree extend system-id ! ! interface FastEthernet0/1 no ip address ! !--- Output suppressed. interface FastEthernet0/16 no ip address ! interface FastEthernet0/17 description SERVER_2 switchport access vlan 3 switchport mode access no ip address spanning-tree portfast ! !--- Output suppressed. ! interface FastEthernet0/33 description HOST_1 !--- Host_1 is configured to be the user VLAN (VLAN 2). switchport access vlan 2 switchport mode access no ip address spanning-tree portfast ! !--- Output suppressed. interface GigabitEthernet0/1 switchport trunk encapsulation dot1q no ip address ! interface GigabitEthernet0/2 no ip address ! interface Vlan1 no ip address no ip route-cache shutdown ! interface Vlan10 description MANAGEMENT !--- IP address used to manage this switch. ip address 10.1.10.2 255.255.255.0 no ip route-cache ! !--- Default gateway is configured so that the switch is reachable !--- from other VLANs/sub-nets. Gateway points to VLAN 10 interface !--- on the 3750. ip default-gateway 10.1.10.1 ip http server ! ! line con 0 line vty 5 15 ! end |
Note: Since the Catalyst 2950 is configured as a VTP client, the VTP configuration is not displayed by the switch. This is standard behavior. The 2950 acquires the VLAN information from the VTP server (3750). The commands below are used on this switch to make it a VTP client in the VTP domain cisco from the global configuration mode.
Cat2950(config)#vtp domain cisco Cat2950(config)#vtp mode client
| Cat2948G (Cisco Catalyst 2948G Switch) |
|---|
Cat2948G> (enable) show config !--- This command shows non-default configurations only. !--- Use the show config all command to show both !--- default and non-default configurations. ........... .................. .. begin ! # ***** NON-DEFAULT CONFIGURATION ***** ! ! #time: Fri Jun 30 1995, 05:04:47 ! #version 6.3(10) ! ! #system web interface version(s) ! #test ! #system set system name Cat2948G ! #frame distribution method set port channel all distribution mac both ! #vtp !--- VTP domain is configured to be that same as the 3550 (VTP server). set vtp domain cisco !--- VTP mode is chosen as client for this switch. set vtp mode client ! #ip !--- The management IP address is configured in VLAN 10. set interface sc0 10 10.1.10.3/255.255.255.0 10.1.10.255 set interface sl0 down set interface me1 down !--- The default route is defined so that the switch is reachable. set ip route 0.0.0.0/0.0.0.0 10.1.10.1 ! #set boot command set boot config-register 0x2 set boot system flash bootflash:cat4000.6-3-10.bin ! #module 1 : 0-port Switching Supervisor ! #module 2 : 50-port 10/100/1000 Ethernet !--- Host_2 and SERVER_3 ports are configured in respective VLANs. set vlan 2 2/2 set vlan 3 2/23 set port name 2/2 To HOST_2 set port name 2/23 to SERVER_3 !--- Trunk is configured to 3750 with dot1q encapsulation. set trunk 2/49 desirable dot1q 1-1005 end |
Verify
This section provides information you can use to confirm your configuration is working properly.
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
Catalyst 3750
-
show switch - The show switch command tells what the stack consists of and which of stack members is the master.
C3750G-24T#show switch Current Switch# Role Mac Address Priority State -------------------------------------------------------- *1 Master 000c.30ae.6280 15 Ready 2 Slave 000c.30ae.2a80 1 Ready -
show vtp status
C3750G-24T#show vtp status VTP Version : 2 Configuration Revision : 3 Maximum VLANs supported locally : 1005 Number of existing VLANs : 8 VTP Operating Mode : Server VTP Domain Name : cisco VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0xA2 0xF4 0x9D 0xE9 0xE9 0x1A 0xE3 0x77 Configuration last modified by 200.1.1.1 at 3-1-93 03:15:42 Local updater ID is 10.1.2.1 on interface Vl2 (lowest numbered VLAN interface found) C3750G-24T#
-
show interfaces trunk
C3750G-24T#show interfaces trunk Port Mode Encapsulation Status Native vlan Gi1/0/1 desirable 802.1q trunking 1 Gi2/0/1 desirable 802.1q trunking 1 Port Vlans allowed on trunk Gi1/0/1 1-4094 Gi2/0/1 1-4094 Port Vlans allowed and active in management domain Gi1/0/1 1-3,10 Gi2/0/1 1-3,10 Port Vlans in spanning tree forwarding state and not pruned Gi1/0/1 1-3,10 Gi2/0/1 1-3,10
-
show ip route
C3750G-24T#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 200.1.1.2 to network 0.0.0.0 200.1.1.0/30 is subnetted, 1 subnets C 200.1.1.0 is directly connected, GigabitEthernet1/0/10 10.0.0.0/24 is subnetted, 3 subnets C 10.1.10.0 is directly connected, Vlan10 C 10.1.3.0 is directly connected, Vlan3 C 10.1.2.0 is directly connected, Vlan2 S* 0.0.0.0/0 [1/0] via 200.1.1.2
Catalyst 2950
-
show vtp status
Cat2950#show vtp status VTP Version : 2 Configuration Revision : 3 Maximum VLANs supported locally : 250 Number of existing VLANs : 8 VTP Operating Mode : Client VTP Domain Name : cisco VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0x54 0xC0 0x4A 0xCE 0x47 0x25 0x0B 0x49 Configuration last modified by 200.1.1.1 at 3-1-93 01:06:24
-
show interfaces trunk
Cat2950#show interfaces trunk Port Mode Encapsulation Status Native vlan Gi0/1 desirable 802.1q trunking 1 Port Vlans allowed on trunk Gi0/1 1-4094 Port Vlans allowed and active in management domain Gi0/1 1-3,10 Port Vlans in spanning tree forwarding state and not pruned Gi0/1 1-3,10
Catalyst 2948G
-
show vtp domain
Cat2948G> (enable) show vtp domain Domain Name Domain Index VTP Version Local Mode Password -------------------------------- ------------ ----------- ----------- ---------- cisco 1 2 client - Vlan-count Max-vlan-storage Config Revision Notifications ---------- ---------------- --------------- ------------- 8 1023 3 disabled Last Updater V2 Mode Pruning PruneEligible on Vlans --------------- -------- -------- ------------------------- 200.1.1.1 disabled disabled 2-1000
-
show trunk
Cat2948G> (enable) show trunk * - indicates vtp domain mismatch Port Mode Encapsulation Status Native vlan -------- ----------- ------------- ------------ ----------- 2/49 desirable dot1q trunking 1 Port Vlans allowed on trunk -------- --------------------------------------------------------------------- 2/49 1-1005 Port Vlans allowed and active in management domain -------- --------------------------------------------------------------------- 2/49 1-3,10 Port Vlans in spanning tree forwarding state and not pruned -------- --------------------------------------------------------------------- 2/49 1-3,10
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Troubleshooting Procedure
Follow the instructions below to troubleshoot your configuration.
-
If you are not able to ping devices within the same VLAN, you should check the VLAN assignment of the source and destination ports by issuing the show port mod/port command for CatOS and the show interface status command for Cisco IOS® Software, to make sure they are in the same VLAN. If they are not in the same switch, make sure that trunking is configured properly by issuing the show trunk command for CatOS and the show interfaces trunk command for Cisco IOS Software, and that the native VLAN is matching on either side. Make sure the subnet mask is matching between the source and destination devices.
-
If you are not able to ping devices in different VLANs, make sure you can ping the respective default gateway (refer to step 1 above). Also, make sure the device's default gateway is pointing to the correct VLAN interface IP address and that the subnet mask is matching.
-
If you are able to reach the Internet, make sure the default route on the 3750 points to the correct IP address, and that the subnet address matches the Internet gateway router by issuing the show ip interface interface-id and show ip route commands. Make sure that the Internet gateway router has routes to the Internet and the internal networks.
Related Information
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback