Introduction
This document describes how to configure static routes on Firepower Device Manager (FDM).
Prerequisites
Requirements
It is recommended to have knowledge of these topics:
- Cisco Secure Firewall Threat Defense initial configuration.
Components Used
The information in this document is based on the software version:
- Firepower Threat Defense version 7.0.5.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
Configurations
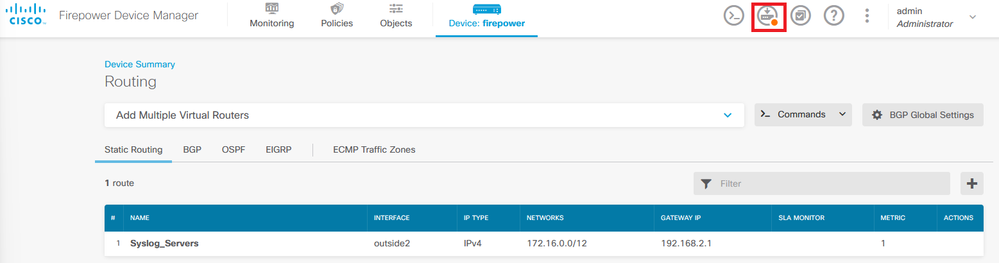
Step 1. Click Device and go to Routing.
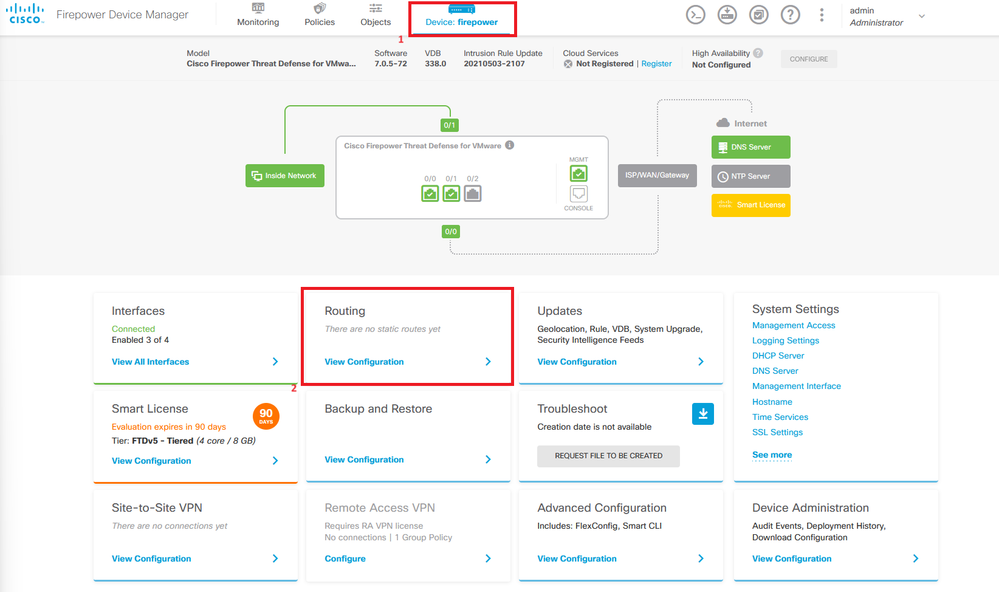
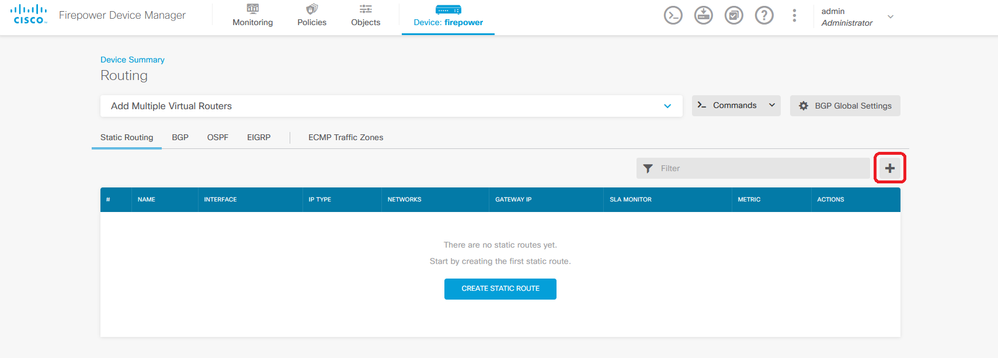
Step 2. Click on plus icon (+) to add Static route.

Note: In case you have virtual routers, ensure you have selected the correct virtual router.
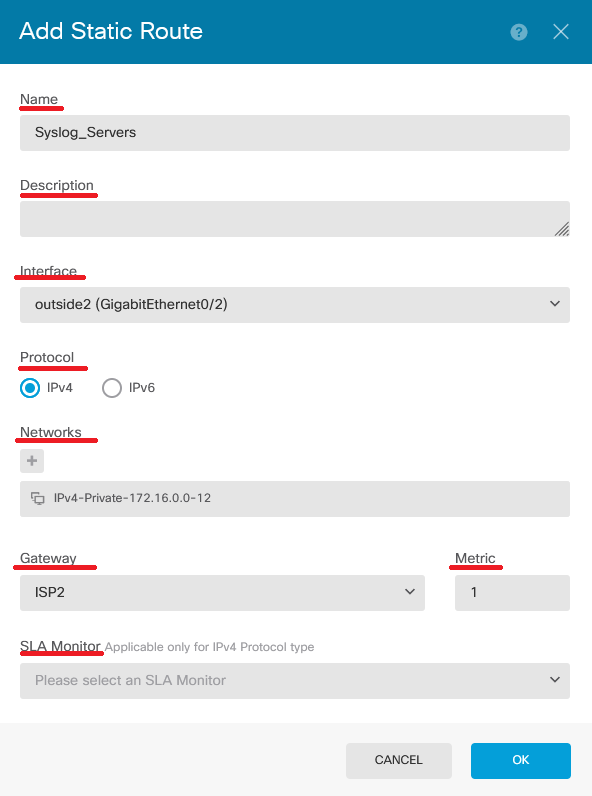
Step 3. Proceed to configure the Static Route properties.
- Name: route name.
- Description (optional): Detailed information on the route.
- Interface: Select the interface to which the traffic must be sent.
- Protocol: Specifies the routing protocol.
- Networks: In the available network list, select or create the network object of the destination networks.
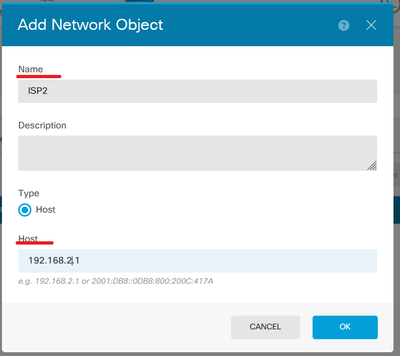
- Gateway: Select or create the network object with the IP of the host to which all traffic to be sent. Enter the values for Name and Host.
- Metric: Enter a value between 1 and 254 for the administrative distance. Remember that the lower valued, the more preferred the route is over others.
- SLA Monitor (optional): If you want to ensure that this route is always available, you must configure this field. This option only works with the IPV4 protocol.
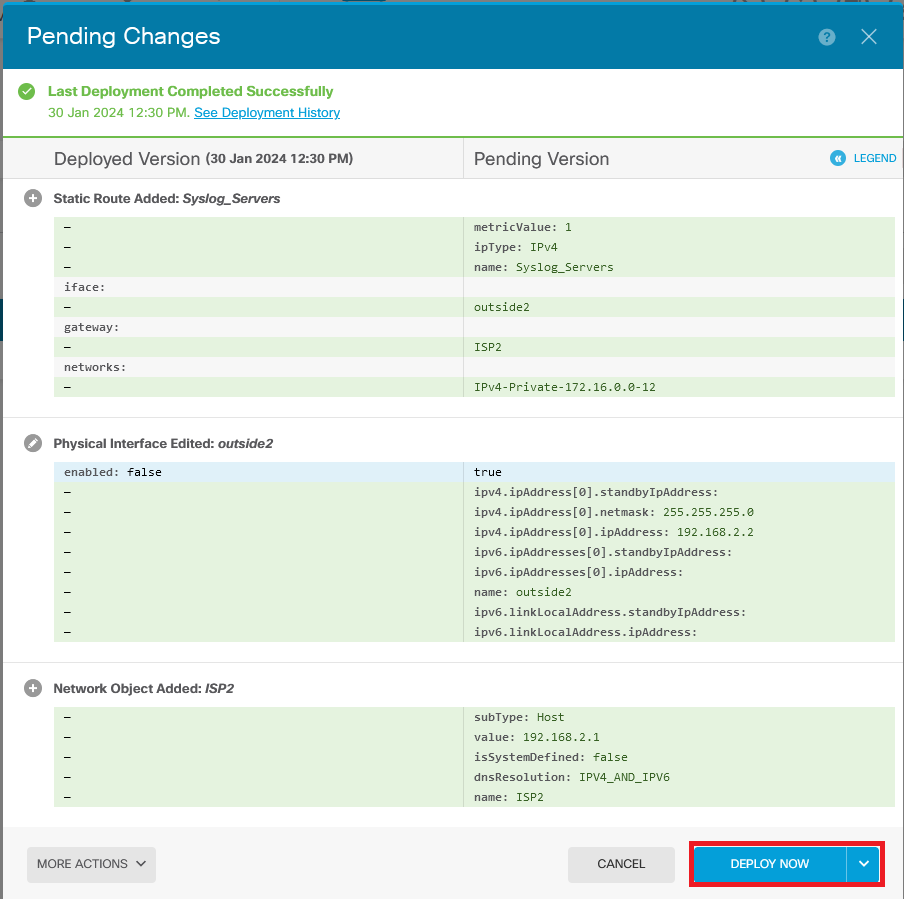
Step 4. Click on Deployment.
Step 5. Deploy the policy.
Verify
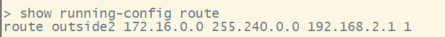
To confirm whether this setting has been applied correctly, you need to access your device via CLI.
In your CLI, run the command show running-config route.
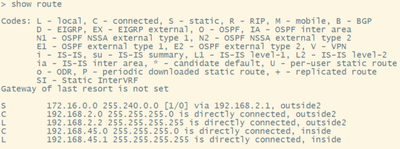
Validate if the route is in the routing table with show route.










 Feedback
Feedback