在帶有C9124存取點的嵌入式無線控制器上配置帶有乙太網橋接的點對點網狀鏈路
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文檔介紹如何在具有C9124存取點的嵌入式無線控制器(eWC)上配置帶有乙太網橋接的P2P網狀鏈路。
必要條件
需求
思科建議您瞭解以下主題:
- 思科無線 LAN 控制器 (WLC) 9800.
- Cisco Catalyst存取點(AP)。
- Catalyst存取點上的嵌入式無線控制器。
- 網狀技術。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- EWC IOS® XE 17.12.2。
- 2個AP C9124。
- 2個電源插頭AIR-PWRINJ-60RGD1。
- 2台交換機;
- 2檯筆記型電腦;
- 1個AP C9115。
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
乙太網路橋接
網狀網路解決方案是Cisco統一無線網路解決方案的一部分,可讓兩個或多個Cisco網狀無線存取點(以下稱為Mesh存取點)透過一個或多個無線跳相互通訊,以加入多個LAN或擴展WiFi覆蓋。
透過網狀網路解決方案中部署的任何思科無線區域網控制器配置、監控和操作思科網狀無線存取點。
支援的網狀網路解決方案部署屬於以下三種常見型別之一:
-
點對點部署
-
點對多點部署
-
網狀部署
本文檔重點介紹如何在同一個裝置上配置點對點網狀部署和乙太網橋接。
在點對點網狀部署中,網狀無線存取點向無線客戶端提供無線接入和回傳,並且可以同時支援一個LAN和終端到遠端乙太網裝置或另一個乙太網LAN之間的橋接。
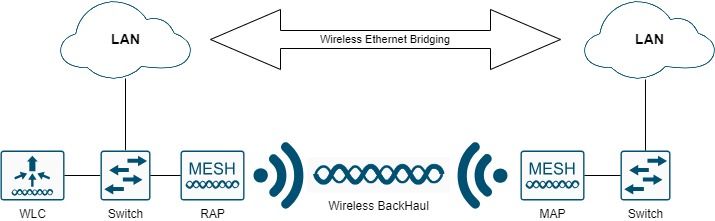 無線乙太網路橋接
無線乙太網路橋接
有關每種部署型別的詳細資訊,請參閱Cisco Catalyst 9800系列無線控制器的網狀部署指南。
Cisco Catalyst 9124系列室外網狀AP是一種無線裝置,專為無線客戶端訪問和點對點橋接、點對多點橋接以及點對多點網狀無線連線而設計。
室外存取點是一個獨立單元,可以安裝在牆壁或懸垂、屋頂柱杆或路燈柱上。
您可以以下列網狀網角色之一操作C9124:
-
屋頂存取點(RAP)
-
網狀存取點(MAP)
RAP與思科無線LAN控制器之間採用有線連線。它們使用回傳無線介面與附近的MAP通訊。RAP是任何橋接或網狀網路的父節點,將網橋或網狀網路連線到有線網路,因此任何橋接或網狀網路段只能有一個RAP。
MAP沒有到思科無線區域網控制器的有線連線。它們可以是完全無線的,並支援與其他MAP或RAP通訊的客戶端,或者可用於連線外圍裝置或有線網路。
Catalyst存取點上的嵌入式無線控制器
Catalyst存取點上的思科嵌入式無線控制器(EWC)是整合到Cisco Catalyst 9100存取點的基於軟體的控制器。
在Cisco EWC網路中,運行無線控制器功能的存取點(AP)被指定為活動AP。
由此活動AP管理的其它存取點稱為從屬AP。
活動的EWC具有兩個角色:
● 作為無線LAN控制器(WLC)起作用和運行,用於管理和控制從屬AP。從屬AP作為輕量存取點運行,為客戶端提供服務。
● 充當為客戶端提供服務的存取點。
要瞭解有關AP上的EWC的產品概述,請訪問Catalyst存取點上的思科嵌入式無線控制器資料表。
要瞭解如何在網路上部署EWC,請訪問Catalyst存取點上的思科嵌入式無線控制器(EWC)白皮書。
本文檔重點介紹C9124作為EWC,並假設EWC模式中已存在AP 9124。
設定
網路圖表
此網路中的所有裝置都位於192.168.100.0/24子網內,但位於VLAN 101且子網為192.168.101.0/25的筆記型電腦除外。
EWC AP (WLC)的管理介面未標籤,並且交換機埠上的本地VLAN設定為VLAN 100。
AP AP9124_RAP具有eWC和根存取點(RAP)的角色,而AP9124_MAP則具有Mesh存取點(MAP)的角色。
在本實驗中,MAP後面還放置了AP C9115,用於顯示我們可以讓AP透過網狀鏈路加入WLC。
此表包含網路中所有裝置的IP地址:
注意:標籤管理介面可能會導致AP加入內部WLC進程時出現問題。如果您決定標籤管理介面,請確保相應地配置有線基礎設施部分。
| 裝置 | IP 位址 |
| 預設閘道 | VLAN 100上的靜態:192.168.100.1 |
| 膝上型電腦1 | VLAN 101上的DHCP |
| 膝上型電腦2 | VLAN 101上的DHCP |
| Switch1(DHCP伺服器) | VLAN 100 SVI:VLAN 100上的靜態:192.168.100.1(DHCP伺服器) |
| Switch1(DHCP伺服器) | VLAN 101 SVI:VLAN 101上的靜態:192.168.101.1(DHCP伺服器) |
| 交換機2 | VLAN 100 SVI:VLAN 100上的DHCP |
| 交換機2 | VLAN 101 SVI:VLAN 101上的DHCP |
| 9124EWC | VLAN 100上的靜態:192.168.100.40 |
| AP9124_RAP | VLAN 100上的DHCP |
| AP9124_MAP | VLAN 100上的DHCP |
| AP9115 | VLAN 100上的DHCP |
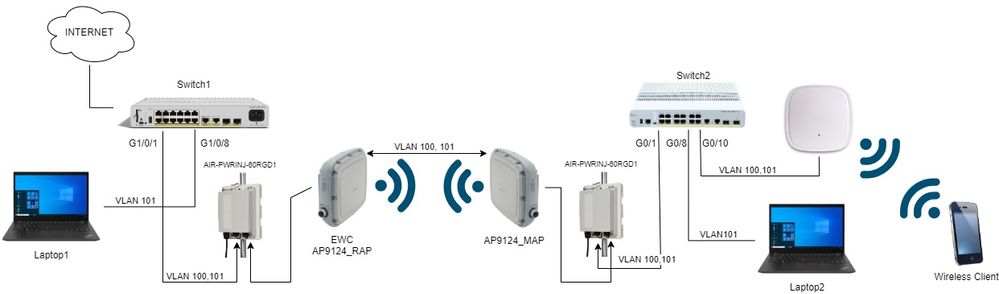 網路圖表
網路圖表

註:C9124 AP使用AIR-PWRINJ-60RGD1供電,並符合Cisco Catalyst 9124AX系列戶外存取點硬體安裝指南中的準則。
組態
本文檔假定已經有一個運行EWC的AP 9124,其初始部署按照Catalyst存取點(EWC)上的思科嵌入式無線控制器完成。
有關轉換過程的其他提示和技巧,請檢視將Catalyst 9100存取點轉換為嵌入式無線控制器文檔。
交換機配置
以下是交換機的相關配置。
連線AP的交換機埠處於中繼模式,本徵VLAN設定為100,允許VLAN 101。
在安裝AP期間,您需要將MAP配置為MAP,因此您需要使AP透過乙太網加入eWC。在這裡,我們使用Switch1埠G1/0/2執行MAP。安裝後,MAP將移動到Switch2。
連線筆記型電腦的交換機埠被配置為VLAN 101的接入埠。
交換機1:
ip dhcp excluded-address 192.168.101.1 192.168.101.10
ip dhcp excluded-address 192.168.100.1 192.168.100.10
!
ip dhcp pool AP_VLAN100
network 192.168.100.0 255.255.255.0
default-router 192.168.100.1
dns-server 192.168.1.254
!
ip dhcp pool VLAN101
network 192.168.101.0 255.255.255.0
default-router 192.168.101.1
dns-server 192.168.1.254
!
interface GigabitEthernet1/0/1
description AP9124_RAP (EWC)
switchport trunk native vlan 100
switchport trunk allowed vlan 100,101
switchport mode trunk
end
interface GigabitEthernet1/0/2
description AP9124_MAP_Staging
switchport trunk native vlan 100
switchport trunk allowed vlan 100,101
switchport mode trunk
end
interface GigabitEthernet1/0/8
description laptop1
switchport access vlan 101
switchport mode access
spanning-tree portfast edge
end
交換機2:
interface GigabitEthernet0/1
description AP9124_MAP
switchport trunk native vlan 100
switchport trunk allowed vlan 100,101
switchport mode trunk
end
interface GigabitEthernet0/8
description laptop2
switchport access vlan 101
switchport mode access
spanning-tree portfast edge
end
interface GigabitEthernet0/1
description AP9115
switchport trunk native vlan 100
switchport trunk allowed vlan 100,101
switchport mode trunk
end
EWC和RAP配置
配置EWC AP的第0天後,嵌入式AP需要加入自身。
1. 將根AP和網格AP的乙太網MAC地址增加到裝置身份驗證。轉至Configuration > Security > AAA > AAA Advanced > Device Authentication,然後按一下Add按鈕:
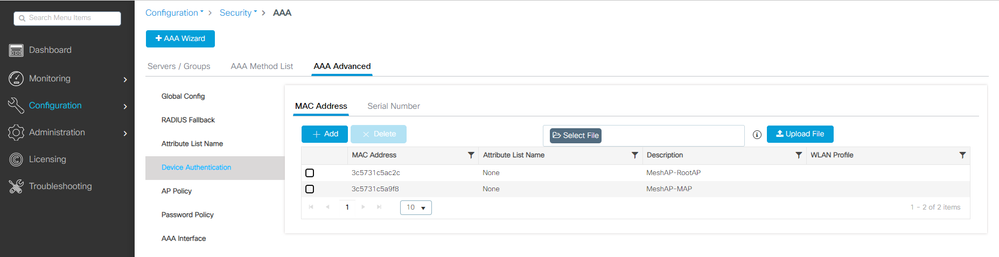 裝置身份驗證中的MAC地址
裝置身份驗證中的MAC地址
CLI命令:
9124EWC(config)#username 3c5731c5ac2c mac description MeshAP-RootAP
9124EWC(config)#username 3c5731c5a9f8 mac description MeshAP-MAP
從AP CLI運行「show controllers wired 0」命令可確認乙太網MAC地址。來自根AP的示例:
AP3C57.31C5.AC2C#show controllers wired 0
wired0 Link encap:Ethernet HWaddr 3C:57:31:C5:AC:2C
使用命令wireless ewc-ap ap shell username x可以完成基礎AP shell的訪問,如下所示:
9124EWC#wireless ewc-ap ap shell username admin
[...]
admin@192.168.255.253's password:
AP3C57.31C5.AC2C>en
Password:
AP3C57.31C5.AC2C#
AP3C57.31C5.AC2C#logout
Connection to 192.168.255.253 closed.
9124EWC#

附註:此命令等同於先前可在 Mobility Express 控制器中使用的 apciscoshell。
如果未在AP配置檔案中指定AP管理使用者名稱和口令,請使用預設使用者名稱Cisco和口令Cisco。
2. 增加身份驗證和授權方法:
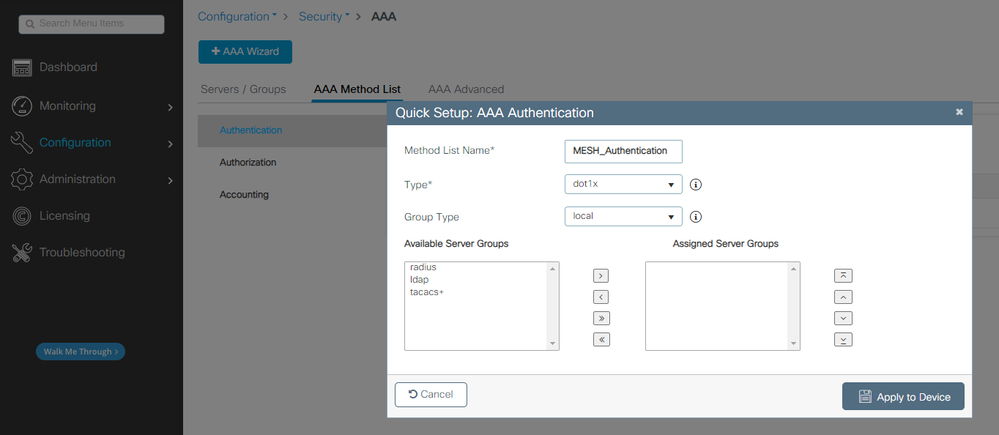 驗證方法清單
驗證方法清單
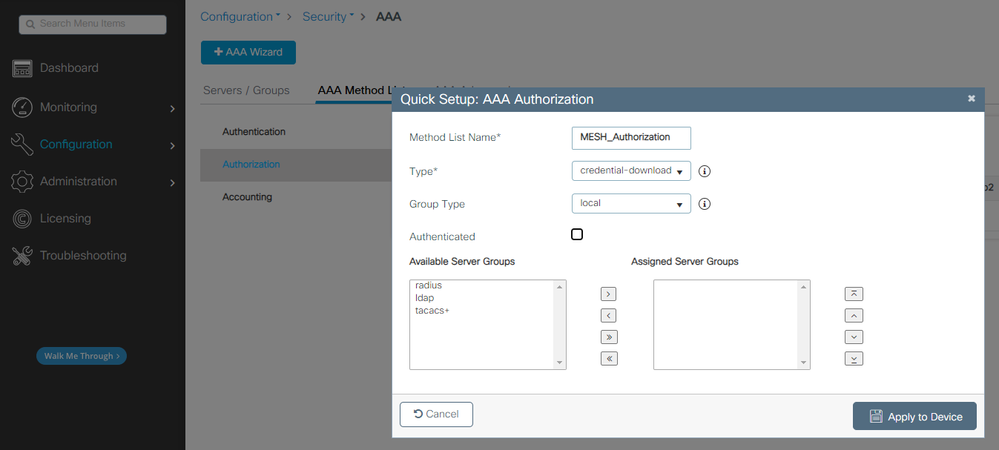 授權方法清單
授權方法清單
CLI命令:
9124EWC(config)#aaa authentication dot1x MESH_Authentication local
9124EWC(config)#aaa authorization credential-download MESH_Authorization local
3. 轉至Configuration > Wireless > Mesh。由於本文檔中的設定需要乙太網橋接,請啟用Ethernet Bridging Allow BPDUs:
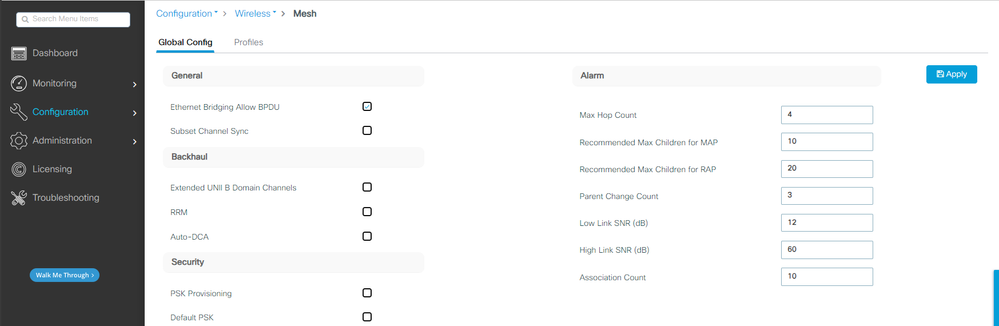 乙太網橋接允許BPDU
乙太網橋接允許BPDU
CLI命令:
9124EWC(config)#wireless mesh ethernet-bridging allow-bdpu

注意:預設情況下,網狀AP不會透過網狀鏈路轉發BPDU。
如果您在2個站點之間沒有任何冗餘鏈路,則不需要此鏈路。
如果有冗餘鏈路,則需要允許BPDU。如果不這樣做,您就有可能在網路中建立STP環路。
4. 配置default-mesh-profile,在其中選擇先前配置的AAA身份驗證和授權方法。按一下並編輯預設網格配置檔案。
轉到高級頁籤並選擇身份驗證和授權方法。啟用選項Ethernet Bridging。
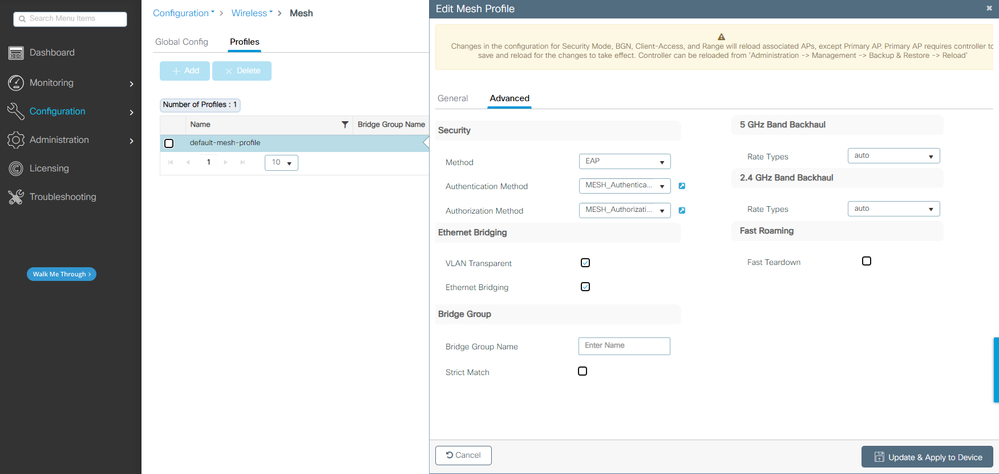 編輯預設網格配置檔案
編輯預設網格配置檔案
CLI命令:
9124EWC(config)#wireless profile mesh default-mesh-profile
9124EWC(config-wireless-mesh-profile)#description "default mesh profile"
9124EWC(config-wireless-mesh-profile)#ethernet-bridging
9124EWC(config-wireless-mesh-profile)#ethernet-vlan-transparent
9124EWC(config-wireless-mesh-profile)#method authentication MESH_Authentication
9124EWC(config-wireless-mesh-profile)#method authorization MESH_Authorization
選項VLAN Transparent的特殊標註:
此功能確定網狀無線存取點如何處理乙太網橋接流量的VLAN標籤:
- 如果啟用了VLAN透明模式,則不會處理VLAN標籤,並且會將資料包橋接為未標籤的資料包。
- 啟用VLAN透明時,不需要設定乙太網路連線埠。乙太網路連線埠會傳遞已標籤及未標籤的架構,而不會解譯架構。
- 如果VLAN透明模式已停用,則所有資料包將根據埠上的VLAN配置(中繼、訪問或正常模式)進行處理。
- 如果乙太網埠設定為中繼模式,則必須配置乙太網VLAN標籤。

提示:要使用AP VLAN標籤,必須取消選中VLAN Transparent覈取方塊。
如果不使用VLAN標籤,則表示RAP和MAP位於中繼埠上配置的本地VLAN上。在這種情況下,如果希望MAP後面的其他裝置位於本地VLAN(此處VLAN 100)上,則需要啟用VLAN透明。
5. 內部AP加入EWC,您可以使用「show ap summary」命令驗證AP加入狀態:
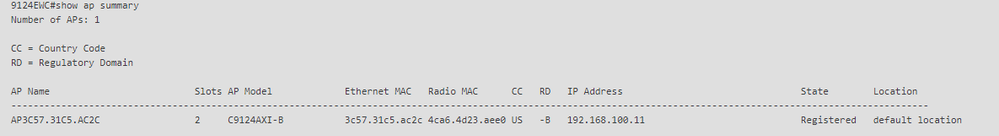 show ap summary
show ap summary
您還可以看到AP透過GUI加入,其中AP顯示為Flex+Bridge模式。為方便起見,您可以立即更改AP的名稱。在此設定中,使用名稱AP9124_RAP:
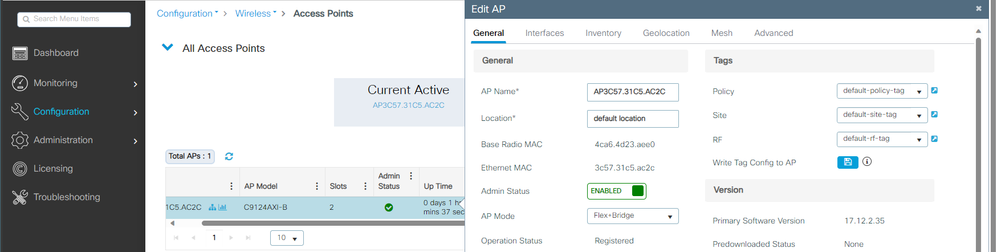 AP一般詳細資料
AP一般詳細資料
您可以編輯地理位置,然後在Mesh頁籤中,確保將其Role配置為根 AP,並且乙太網埠配置設定為trunk,並配置相應的VLAN ID:
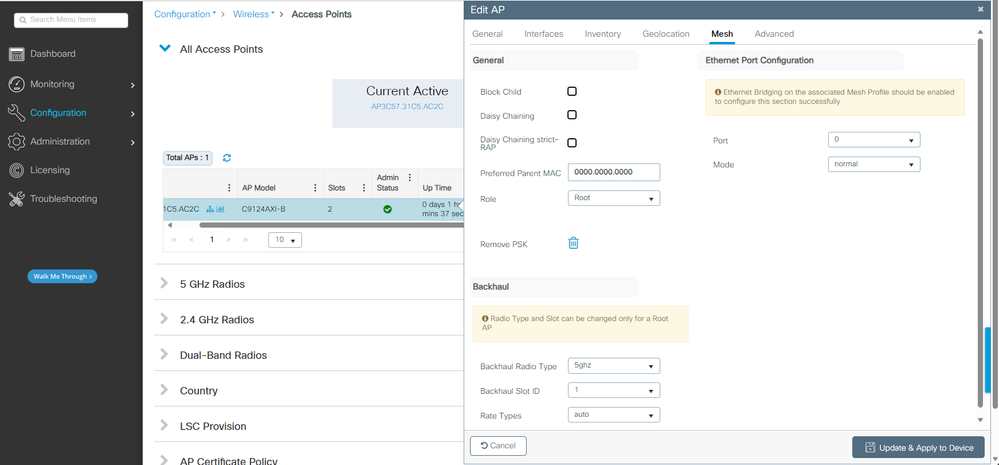 網狀角色根目錄
網狀角色根目錄
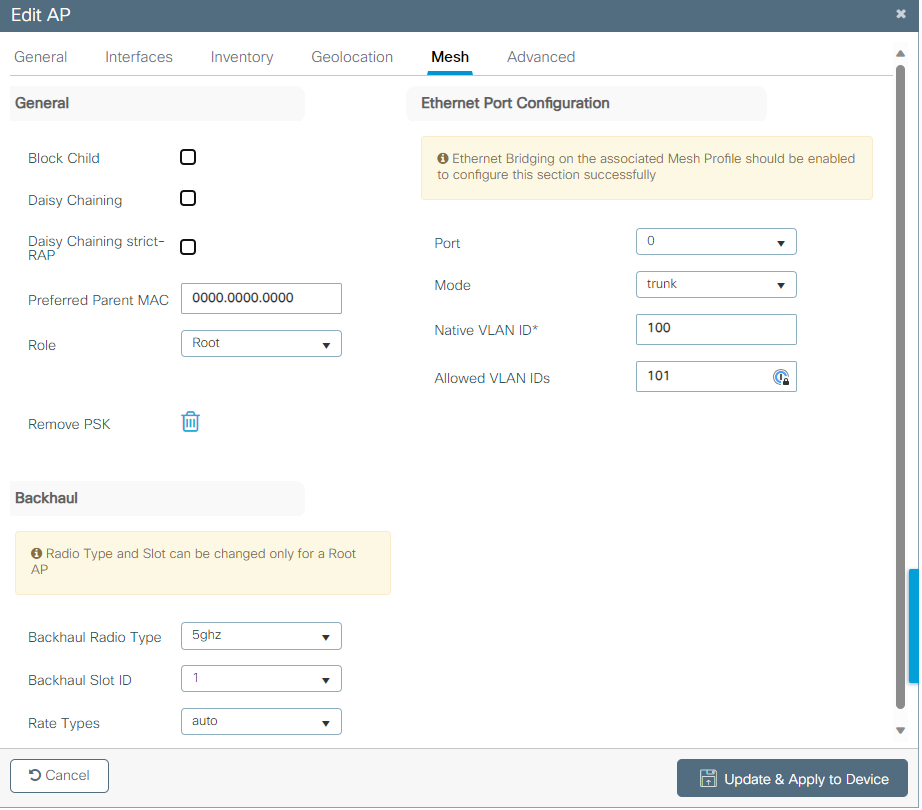 乙太網埠配置
乙太網埠配置
配置對映
現在是加入9124 MAP的時候了。
1. 將MAP AP連線到Switch1進行暫存。AP加入EWC並在AP清單中顯示。將其名稱更改為類似於AP9124_MAP的名稱,然後在Mesh頁籤中將其配置為Mesh Role。按一下Update & Apply to Device:
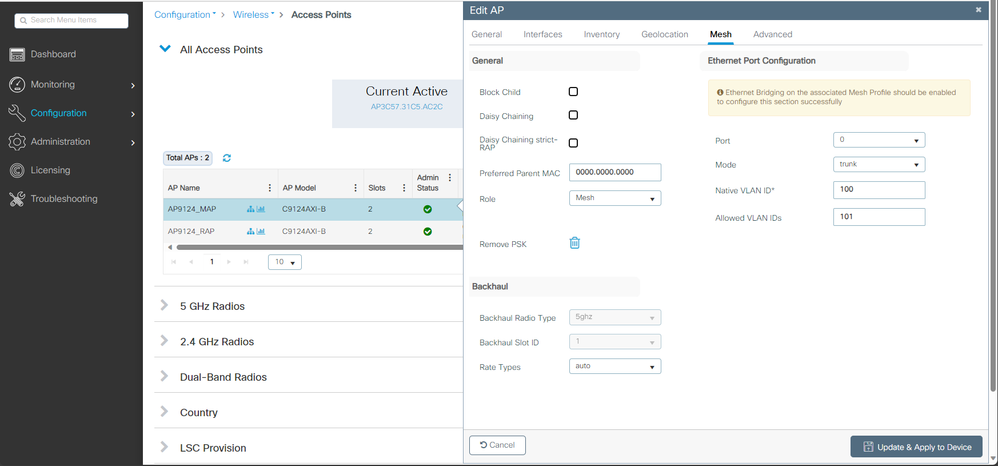 MAP配置
MAP配置
2. 從Switch1斷開AP連線,並根據網路圖連線到Switch2。MAP透過無線介面透過RAP加入EWC。

註:由於AP透過饋電器供電,AP不會關閉,並且由於設定是在受控環境中,因此交換機2在物理上關閉,因此我們只需將電纜從一台交換機移至另一台交換機即可。
您可以將控制檯電纜連線到AP並透過控制檯檢視結果。以下是一些重要訊息。

注意:從版本17.12.1,802.11AX AP的預設控制檯波特率從9600 bps更改為115200 bps。
MAP失去與EWC的連線:
AP9124_MAP#
[*01/11/2024 14:08:23.0214] chatter: Device wired0 notify state change link DOWN
[*01/11/2024 14:08:28.1474] Re-Tx Count=1, Max Re-Tx Value=5, SendSeqNum=83, NumofPendingMsgs=3
[*01/11/2024 14:08:28.1474]
[*01/11/2024 14:08:31.1485] Re-Tx Count=2, Max Re-Tx Value=5, SendSeqNum=83, NumofPendingMsgs=3
[*01/11/2024 14:08:31.1486]
[*01/11/2024 14:08:33.4214] chatter: Device wired0 notify state change link UP
[*01/11/2024 14:08:34.1495] Re-Tx Count=3, Max Re-Tx Value=5, SendSeqNum=83, NumofPendingMsgs=3
[*01/11/2024 14:08:34.1495]
[*01/11/2024 14:08:37.1505] Re-Tx Count=4, Max Re-Tx Value=5, SendSeqNum=84, NumofPendingMsgs=4
[*01/11/2024 14:08:37.1505]
[*01/11/2024 14:08:40.1515] Re-Tx Count=5, Max Re-Tx Value=5, SendSeqNum=84, NumofPendingMsgs=4
[*01/11/2024 14:08:40.1515]
[*01/11/2024 14:08:43.1524] Max retransmission count exceeded, going back to DISCOVER mode.
[...]
[*01/11/2024 14:08:48.1537] CRIT-MeshWiredAdj[0][3C:57:31:C5:A9:F8]: Blocklisting Adjacency due to GW UNREACHABLE
[*01/11/2024 14:08:48.1538] CRIT-MeshWiredAdj[0][3C:57:31:C5:A9:F8]: Remove as Parent
[*01/11/2024 14:08:48.1539] CRIT-MeshLink: Link Down Block Root port Mac: 3C:57:31:C5:A9:F8 BH Id: 0 Port:0 Device:DEVNO_WIRED0
[*01/11/2024 14:08:48.1542] CRIT-MeshWiredBackhaul[0]: Remove as uplink
MAP透過無線進入發現模式,並透過第36頻道的無線電回傳找到RAP,找到EWC並加入其中:
[*01/11/2024 14:08:51.3893] CRIT-MeshRadioBackhaul[1]: Set as uplink
[*01/11/2024 14:08:51.3894] CRIT-MeshAwppAdj[1][4C:A6:4D:23:AE:F1]: Set as Parent - (New) channel(36) width(20)
[*01/11/2024 14:08:51.3915] wlan: [0:I:CMN_MLME] mlme_ext_vap_down: VAP (mon0) is down
[*01/11/2024 14:08:51.3926] wlan: [0:I:CMN_MLME] mlme_ext_vap_down: VAP (apbhr0) is down
[*01/11/2024 14:08:51.4045] wlan: [0:I:CMN_MLME] mlme_ext_vap_up: VAP (apbhr0) is up
[*01/11/2024 14:08:51.4053] wlan: [0:I:CMN_MLME] mlme_ext_vap_up: VAP (mon0) is up
[*01/11/2024 14:08:53.3898] CRIT-MeshLink: Set Root port Mac: 4C:A6:4D:23:AE:F1 BH Id: 3 Port:70 Device:DEVNO_BH_R1
[*01/11/2024 14:08:53.3904] Mesh Reconfiguring DHCP.
[*01/11/2024 14:08:53.8680] DOT11_UPLINK_EV: wgb_uplink_set_port_authorized: client not found
[*01/11/2024 14:08:53.9232] CRIT-MeshSecurity: Mesh Security successful authenticating parent 4C:A6:4D:23:AE:F1, informing Mesh Link
[...]
[*01/11/2024 14:09:48.4388] Discovery Response from 192.168.100.40
[*01/11/2024 14:09:59.0000] Started wait dtls timer (60 sec)
[*01/11/2024 14:09:59.0106]
[*01/11/2024 14:09:59.0106] CAPWAP State: DTLS Setup
[*01/11/2024 14:09:59.0987] dtls_verify_server_cert: Controller certificate verification successful
[*01/11/2024 14:09:59.8466]
[*01/11/2024 14:09:59.8466] CAPWAP State: Join
[*01/11/2024 14:09:59.8769] Sending Join request to 192.168.100.40 through port 5264, packet size 1376
[*01/11/2024 14:10:04.7842] Sending Join request to 192.168.100.40 through port 5264, packet size 1376
[*01/11/2024 14:10:04.7953] Join Response from 192.168.100.40, packet size 1397
[...]
[*01/11/2024 14:10:06.6919] CAPWAP State: Run
[*01/11/2024 14:10:06.8506] AP has joined controller 9124EWC
[*01/11/2024 14:10:06.8848] Flexconnect Switching to Connected Mode!
[...]
MAP現在透過RAP加入EWC。
現在,AP C9115可以獲取VLAN 100上的IP地址,然後加入EWC:

警告:請記住,VLAN 100是交換機埠中繼本地VLAN。為了讓流量從VLAN 100上的AP到達VLAN 100上的WLC,網狀鏈路必須啟用VLAN Transparent。此操作在「網狀配置檔案乙太網橋接」部分完成。
[*01/19/2024 11:40:55.0710] ethernet_port wired0, ip 192.168.100.14, netmask 255.255.255.0, gw 192.168.100.1, mtu 1500, bcast 192.168.100.255, dns1 192.168.1.254, vid 0, static_ip_failover false, dhcp_vlan_failover false
[*01/19/2024 11:40:58.2070]
[*01/19/2024 11:40:58.2070] CAPWAP State: Init
[*01/19/2024 11:40:58.2150]
[*01/19/2024 11:40:58.2150] CAPWAP State: Discovery
[*01/19/2024 11:40:58.2400] Discovery Request sent to 192.168.100.40, discovery type STATIC_CONFIG(1)
[*01/19/2024 11:40:58.2530] Discovery Request sent to 255.255.255.255, discovery type UNKNOWN(0)
[*01/19/2024 11:40:58.2600]
[*01/19/2024 11:40:58.2600] CAPWAP State: Discovery
[*01/19/2024 11:40:58.2670] Discovery Response from 192.168.100.40
[*01/19/2024 11:40:58.2670] Found Configured MWAR '9124EWC' (respIdx 1).
[*01/19/2024 15:13:56.0000] Started wait dtls timer (60 sec)
[*01/19/2024 15:13:56.0070]
[*01/19/2024 15:13:56.0070] CAPWAP State: DTLS Setup
[...]
[*01/19/2024 15:13:56.1660] dtls_verify_server_cert: Controller certificate verification successful
[*01/19/2024 15:13:56.9000] sudi99_request_check_and_load: Use HARSA SUDI certificate
[*01/19/2024 15:13:57.2980]
[*01/19/2024 15:13:57.2980] CAPWAP State: Join
[*01/19/2024 15:13:57.3170] shared_setenv PART_BOOTCNT 0 &> /dev/null
[*01/19/2024 15:13:57.8620] Sending Join request to 192.168.100.40 through port 5274, packet size 1376
[*01/19/2024 15:14:02.8070] Sending Join request to 192.168.100.40 through port 5274, packet size 1376
[*01/19/2024 15:14:02.8200] Join Response from 192.168.100.40, packet size 1397
[*01/19/2024 15:14:02.8200] AC accepted previous sent request with result code: 0
[*01/19/2024 15:14:03.3700] Received wlcType 2, timer 30
[*01/19/2024 15:14:03.4440]
[*01/19/2024 15:14:03.4440] CAPWAP State: Image Data
[*01/19/2024 15:14:03.4440] AP image version 17.12.2.35 backup 17.9.4.27, Controller 17.12.2.35
[*01/19/2024 15:14:03.4440] Version is the same, do not need update.
[*01/19/2024 15:14:03.4880] status 'upgrade.sh: Script called with args:[NO_UPGRADE]'
[*01/19/2024 15:14:03.5330] do NO_UPGRADE, part2 is active part
[*01/19/2024 15:14:03.5520]
[*01/19/2024 15:14:03.5520] CAPWAP State: Configure
[*01/19/2024 15:14:03.5600] Telnet is not supported by AP, should not encode this payload
[*01/19/2024 15:14:03.6880] Radio [1] Administrative state DISABLED change to ENABLED
[*01/19/2024 15:14:03.6890] Radio [0] Administrative state DISABLED change to ENABLED
[*01/19/2024 15:14:03.8670]
[*01/19/2024 15:14:03.8670] CAPWAP State: Run
[*01/19/2024 15:14:03.9290] AP has joined controller 9124EWC
[*01/19/2024 15:14:03.9310] Flexconnect Switching to Connected Mode!
由於這是EWC AP,因此它只包含與其自身型號對應的AP映像(此處的C9124運行ap1g6a)。當您加入不同的AP型號時,就會有一個非同質網路。
在這些情況下,如果AP的版本不同,則需要下載相同的版本,因此請確保您具有有效的TFTP/SFTP伺服器和位置,並且在EWC > Administration > Software Management中配置了AP映像:
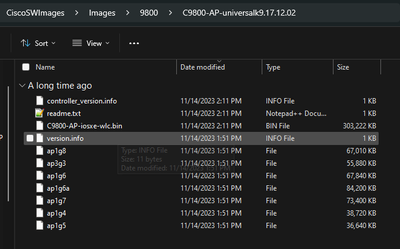 TFTP伺服器及AP映像資料夾
TFTP伺服器及AP映像資料夾
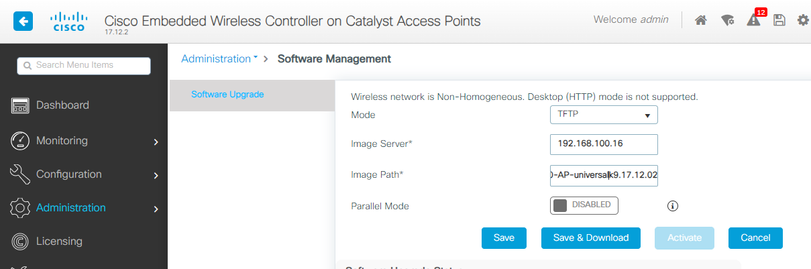 AP映像
AP映像
AP顯示在AP清單中,您可以分配策略標籤:
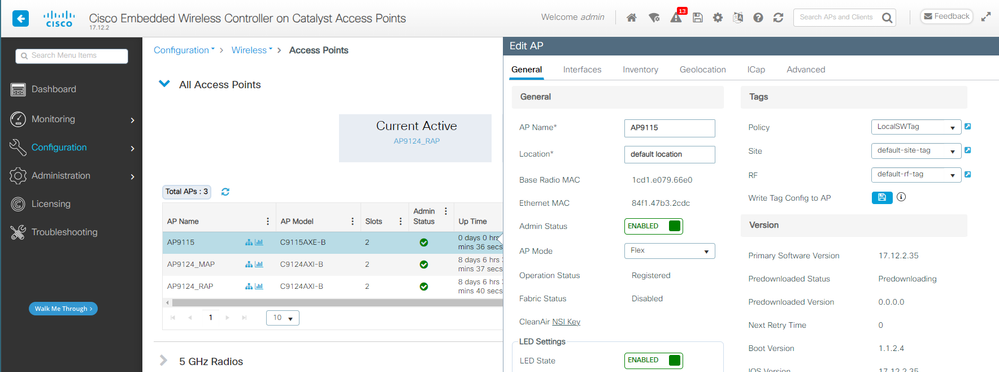 包含9115詳細資訊的AP清單
包含9115詳細資訊的AP清單
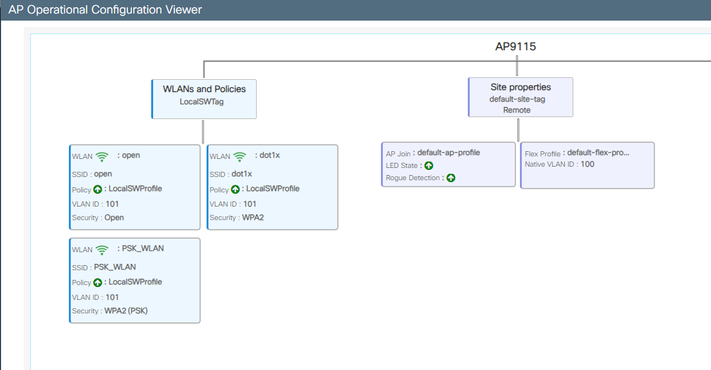 AP操作檢視
AP操作檢視
驗證
如果使用show wireless mesh ap tree命令,則可以透過GUI看到網狀樹,CLI的輸出也會顯示出來。在GUI上,轉到Monitoring > Wireless > Mesh:
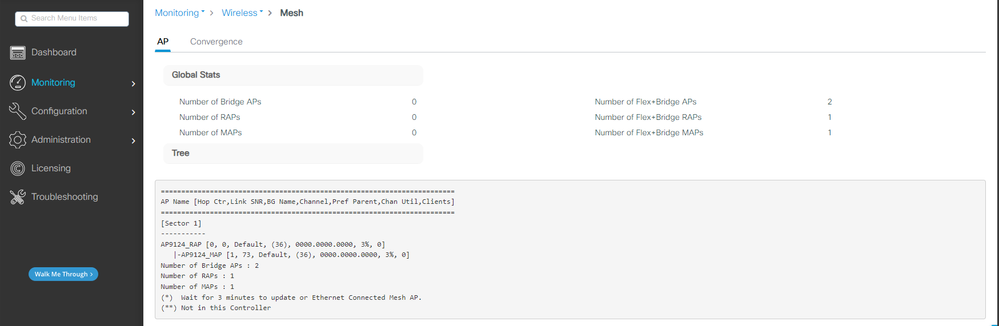 網狀AP樹
網狀AP樹
在RAP和MAP上,您可以使用命令「show mesh backhaul」驗證網狀回程:
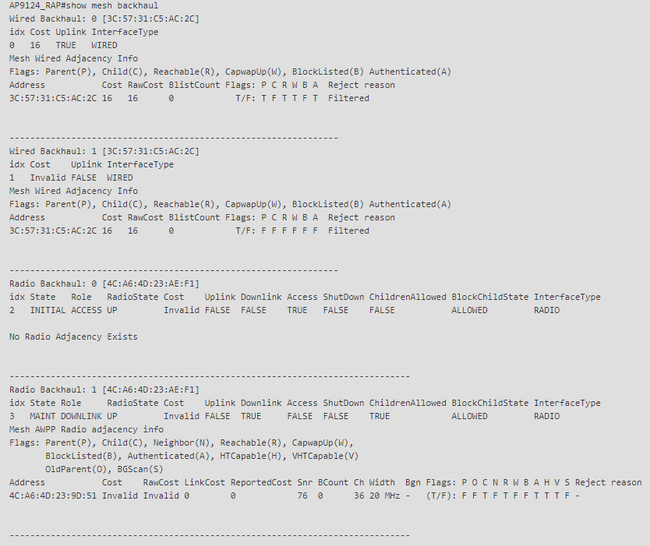 RAP show mesh backhaul
RAP show mesh backhaul
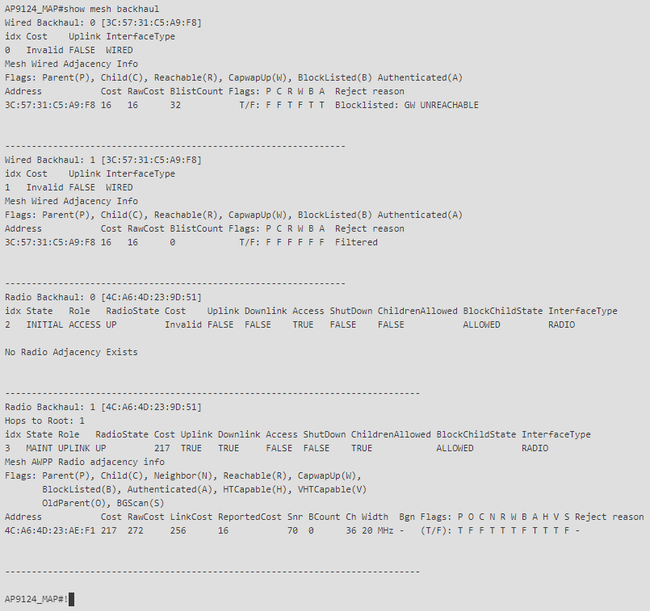 MAP show mesh backhaul
MAP show mesh backhaul
您可以在AP端驗證網狀VLAN中繼配置:
AP9124_RAP#show mesh ethernet vlan config static
Static (Stored) ethernet VLAN Configuration
Ethernet Interface: 0
Interface Mode: TRUNK
Native Vlan: 100
Allowed Vlan: 101,
Ethernet Interface: 1
Interface Mode: ACCESS
Native Vlan: 0
Allowed Vlan:
Ethernet Interface: 2
Interface Mode: ACCESS
Native Vlan: 0
Allowed Vlan:
連線到Switch2的膝上型電腦收到來自VLAN 101的IP地址:
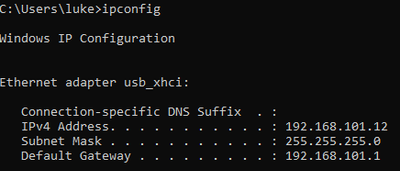
放置在Switch1上的Laptop1收到來自VLAN 101的IP:
Ethernet adapter Ethernet 6_White:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::d1d6:f607:ff02:4217%18
IPv4 Address. . . . . . . . . . . : 192.168.101.13
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.101.1
C:\Users\tantunes>ping 192.168.101.12 -i 192.168.101.13
Pinging 192.168.101.12 with 32 bytes of data:
Reply from 192.168.101.12: bytes=32 time=5ms TTL=128
Reply from 192.168.101.12: bytes=32 time=5ms TTL=128
Reply from 192.168.101.12: bytes=32 time=7ms TTL=128
Reply from 192.168.101.12: bytes=32 time=5ms TTL=128
Ping statistics for 192.168.101.12:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 5ms, Maximum = 7ms, Average = 5ms

注意:請注意,要在Windows裝置之間測試ICMP,您需要在系統防火牆上允許ICMP。預設情況下,Windows裝置在系統防火牆中阻止ICMP。
另一個檢驗乙太網橋接的簡單測試是在兩台交換機上為VLAN 101配置SVI,並將Switch2 SVI設定為DHCP。用於VLAN 101的Switch2 SVI從VLAN 101獲取IP,您可以對Switch 1 VLAN 101 SVI執行VLAN 101連線檢查:
Switch2#show ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES NVRAM up down
Vlan100 192.168.100.61 YES DHCP up up
Vlan101 192.168.101.11 YES DHCP up up
GigabitEthernet0/1 unassigned YES unset up up
[...]
Switch2#
Switch2#ping 192.168.101.1 source 192.168.101.11
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.101.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.101.11
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/4/7 ms
Switch2#
Switch1#sh ip int br
Interface IP-Address OK? Method Status Protocol
Vlan1 192.168.1.11 YES NVRAM up up
Vlan100 192.168.100.1 YES NVRAM up up
Vlan101 192.168.101.1 YES NVRAM up up
GigabitEthernet1/0/1 unassigned YES unset up up
[...]
Switch1#ping 192.168.101.11 source 192.168.101.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.101.11, timeout is 2 seconds:
Packet sent with a source address of 192.168.101.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/6/8 ms
Switch1#
本地模式AP C9115也已加入EWC:
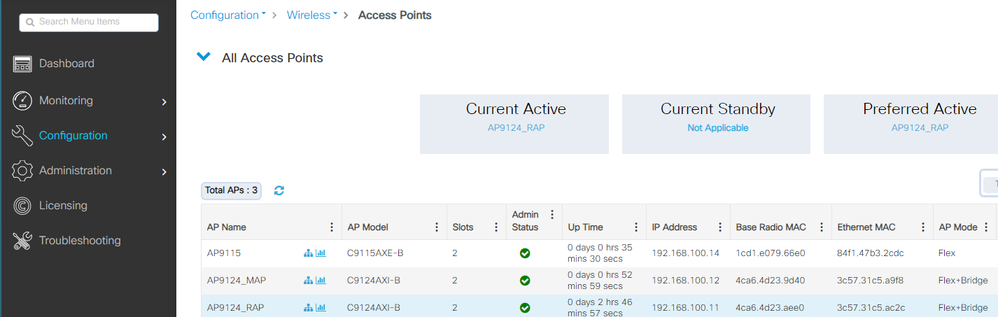 AP 9115已加入EWC
AP 9115已加入EWC
建立了3個對映到策略配置檔案的WLAN(開放、PSK和dot1x),其中VLAN 101在訪問策略中定義:
 AP9115操作配置
AP9115操作配置
無線客戶端可以連線到WLAN:
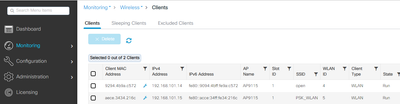
疑難排解
本節提供了有用的命令以及一些提示、技巧和建議。
有用的命令
在RAP/MAP上:
 顯示網格
顯示網格
 RAP/MAP調試網狀選項
RAP/MAP調試網狀選項
在WLC上:
 顯示無線網狀網
顯示無線網狀網
要在WLC上調試,最佳起點是使用RadioActive跟蹤和MAP/RAP的MAC地址。
示例1:RAP從MAP接收鄰接關係並成功進行身份驗證
AP9124_RAP#show debug
mesh:
adjacent packet debugging is enabled
event debugging is enabled
mesh linktest debug debugging is enabled
Jan 16 14:47:01 AP9124_RAP kernel: [*01/16/2024 14:47:01.9559] EVENT-MeshRadioBackhaul[1]: Sending ADD_LINK to MeshLink
Jan 16 14:47:01 AP9124_RAP kernel: [*01/16/2024 14:47:01.9559] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: AWPP adjacency added channel(36) bgn() snr(70)
Jan 16 14:47:01 AP9124_RAP kernel: [*01/16/2024 14:47:01.9560] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: Wcp Client Add vapId:17 AID:256
Jan 16 14:47:01 AP9124_RAP kernel: [*01/16/2024 14:47:01.9570] CLSM[4C:A6:4D:23:9D:51]: Skip key programming due to null key
Jan 16 14:47:04 AP9124_RAP kernel: [*01/16/2024 14:47:04.9588] EVENT-MeshRadioBackhaul[1]: Sending LINK_UP to MeshLink
Jan 16 14:47:04 AP9124_RAP kernel: [*01/16/2024 14:47:04.9592] EVENT-MeshLink: Add BH Radio port Mac:4C:A6:4D:23:9D:51 port:70 Device:DEVNO_BH_R1
Jan 16 14:47:04 AP9124_RAP kernel: [*01/16/2024 14:47:04.9600] EVENT-MeshSecurity: Processing ASSOC_REQ, Child(4C:A6:4D:23:9D:51) state changed to ASSOC
Jan 16 14:47:05 AP9124_RAP kernel: [*01/16/2024 14:47:05.1008] EVENT-MeshSecurity: Intermodule message ASSOC_RESP_NOTIFICATION
Jan 16 14:47:05 AP9124_RAP kernel: [*01/16/2024 14:47:05.1011] EVENT-MeshSecurity: Processing CAPWAP_MESH_ASSOC_RSP, Child(4C:A6:4D:23:9D:51) state changed to AUTH
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.1172] EVENT-MeshSecurity: Intermodule message KEY_ADD_NOTIFICATION
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.1173] EVENT-MeshSecurity: save pmk for Child(4C:A6:4D:23:9D:51) in EAP mode
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.1173] EVENT-MeshSecurity: save anonce for Child(4C:A6:4D:23:9D:51)
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2033] EVENT-MeshSecurity: Processing TGR_AUTH_REQ, Child(4C:A6:4D:23:9D:51) state changed to KEY_INIT
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2139] EVENT-MeshSecurity: decoding TGR_REASSOC_REQ frame from 4C:A6:4D:23:9D:51, no mic
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2139] EVENT-MeshSecurity: Parent(4C:A6:4D:23:AE:F1) generating keys for child 4C:A6:4D:23:9D:51
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2143] EVENT-MeshSecurity: Processing TGR_REASSOC_REQ, Child(4C:A6:4D:23:9D:51) state changed to STATE_RUN
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2143] EVENT-MeshSecurity: Mesh Security successful authenticating child 4C:A6:4D:23:9D:51, informing Mesh Link
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2143] EVENT-MeshLink: Mac: 4C:A6:4D:23:9D:51 bh_id:3 auth_result: Pass
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2143] EVENT-MeshLink: Sending NOTIFY_SECURITY_DONE to Control
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2144] EVENT-MeshLink: Mesh Link:Security success on Child :4C:A6:4D:23:9D:51
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2146] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: auth_complete Result(Pass)
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2147] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: Wcp Client Add vapId:17 AID:256
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2151] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: Reset mesh client
Jan 16 14:47:06 AP9124_RAP kernel: [*01/16/2024 14:47:06.2151] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: Wcp Client Add vapId:17 AID:256
Jan 16 14:47:19 AP9124_RAP kernel: [*01/16/2024 14:47:19.3576] EVENT-MeshRadioBackhaul[1]: Started phased mesh neigh upddate with 1 neighbors
Jan 16 14:47:19 AP9124_RAP kernel: [*01/16/2024 14:47:19.3577] EVENT-MeshRadioBackhaul[1]: Started mesh neigh update batch at index 0
Jan 16 14:47:19 AP9124_RAP kernel: [*01/16/2024 14:47:19.3577] EVENT-MeshRadioBackhaul[1]: All mesh neigh update batches completed
示例2:MAP Mac地址未增加到WLC或未正確增加
Jan 16 14:52:13 AP9124_RAP kernel: [*01/16/2024 14:52:13.6402] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7407] INFO-MeshRadioBackhaul[1]: Rx ADJ Request unicast Mac: 4C:A6:4D:23:9D:51, bgn: channel:36 snr:71
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7408] EVENT-MeshRadioBackhaul[1]: Sending LINK_UP to MeshLink
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7409] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7411] EVENT-MeshLink: Add BH Radio port Mac:4C:A6:4D:23:9D:51 port:70 Device:DEVNO_BH_R1
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7419] EVENT-MeshSecurity: Processing ASSOC_REQ, Child(4C:A6:4D:23:9D:51) state changed to ASSOC
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7583] EVENT-MeshSecurity: Intermodule message ASSOC_RESP_NOTIFICATION
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7586] EVENT-MeshSecurity: Processing CAPWAP_MESH_ASSOC_RSP, WLC blocks Child 4C:A6:4D:23:9D:51, state changed to IDLE
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7586] EVENT-MeshSecurity: Mesh Security failed to authenticate child 4C:A6:4D:23:9D:51
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7620] INFO-MeshRadioBackhaul[1]: Rx ADJ Request unicast Mac: 4C:A6:4D:23:9D:51, bgn: channel:36 snr:72
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7620] INFO-MeshRadioBackhaul[1]: APID TLV for Mac: 4C:A6:4D:23:9D:51, length:6
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7621] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: ApID: len(6):
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7621] 0x3c 0x57 0x31 0xc5 0xa9 0xf8
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7621] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: HcExt: hopcountVersion:1 capabilities: 0
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7621] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: HT CAP : width(0)
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7621] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: HT CAP MCS :
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7622] 0xff 0xff 0xff 0xff 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7622] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: VHT CAP : width(0)
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7622] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: VHT CAP MCS :
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7622] 0xaa 0xff 0x00 0x00 0xaa 0xff 0x00 0x00
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7622] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: HE CAP : width(0)
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7623] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: HE CAP MCS :
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7623] 0xaa 0xff 0xaa 0xff 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7623] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7636] EVENT-MeshRadioBackhaul[1]: Sending LINK_DOWN to MeshLink
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7637] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7642] EVENT-MeshLink: Sending NOTIFY_SECURITY_LINK_DOWN to MeshSecurity
Jan 16 14:52:15 AP9124_RAP kernel: [*01/16/2024 14:52:15.7642] EVENT-MeshSecurity: Intermodule message NOTIFY_SECURITY_LINK_DOWN
示例3:RAP丟失對映
Jan 16 14:48:58 AP9124_RAP kernel: [*01/16/2024 14:48:58.9929] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:48:59 AP9124_RAP kernel: [*01/16/2024 14:48:59.2889] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: set_distVector: vec rapHops:1 metric:13048576
Jan 16 14:48:59 AP9124_RAP kernel: [*01/16/2024 14:48:59.7894] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: set_distVector: vec rapHops:1 metric:13048576
Jan 16 14:48:59 AP9124_RAP kernel: [*01/16/2024 14:48:59.9931] INFO-MeshRadioBackhaul[1]: Rx ADJ Request unicast Mac: 4C:A6:4D:23:9D:51, bgn: channel:36 snr:71
Jan 16 14:48:59 AP9124_RAP kernel: [*01/16/2024 14:48:59.9932] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:49:00 AP9124_RAP kernel: [*01/16/2024 14:49:00.2891] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: set_distVector: vec rapHops:1 metric:13048576
Jan 16 14:49:00 AP9124_RAP kernel: [*01/16/2024 14:49:00.7891] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: set_distVector: vec rapHops:1 metric:13048576
Jan 16 14:49:00 AP9124_RAP kernel: [*01/16/2024 14:49:00.9937] INFO-MeshRadioBackhaul[1]: Rx ADJ Request unicast Mac: 4C:A6:4D:23:9D:51, bgn: channel:36 snr:69
Jan 16 14:49:00 AP9124_RAP kernel: [*01/16/2024 14:49:00.9938] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:49:01 AP9124_RAP kernel: [*01/16/2024 14:49:01.2891] INFO-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: set_distVector: vec rapHops:1 metric:13048576
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5480] EVENT-MeshAwppAdj[1][4C:A6:4D:23:9D:51]: Child Health is 0 dropping child
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5481] EVENT-MeshRadioBackhaul[1]: MeshRadioBackhaul::push_kill_adj_msg mac:4C:A6:4D:23:9D:51
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5481] EVENT-MeshRadioBackhaul[1]: Sending KILL_ADJACENCY to Self
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5488] EVENT-MeshRadioBackhaul[1]: KILL_ADJACENCY received from self Data: 0x4c 0xa6 0x4d 0x23 0x9d 0x51
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5489] INFO-MeshRadioBackhaul[1]: Tx ADJ Response to 4C:A6:4D:23:9D:51 len: 247 type: 32 ch:36 antenna:0 netname: offchan: 0
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5501] EVENT-MeshRadioBackhaul[1]: Sending LINK_DOWN to MeshLink
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5501] EVENT-MeshAdj[1][4C:A6:4D:23:9D:51]: Adjacency removed
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5502] EVENT-MeshRadioBackhaul[1]: Sending REMOVE_LINK to MeshLink
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5511] EVENT-MeshLink: Sending NOTIFY_SECURITY_LINK_DOWN to MeshSecurity
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5512] EVENT-MeshSecurity: Intermodule message NOTIFY_SECURITY_LINK_DOWN
Jan 16 14:49:25 AP9124_RAP kernel: [*01/16/2024 14:49:25.5513] EVENT-MeshLink: Delete BH3 Radio port Mac:4C:A6:4D:23:9D:51 port:70 Device:DEVNO_BH_R1
提示、技巧和建議
- 透過線上上將MAP和RAP升級到相同的映象版本,我們避免了透過空中下載映象(在「髒」RF環境中可能會出現問題)。
- 強烈建議先在受控環境中測試設定,然後再將其部署到現場。
- 如果測試乙太網橋接,在每一端使用Windows筆記型電腦進行橋接,請注意,要在Windows裝置之間測試ICMP,需要在系統防火牆上允許ICMP。預設情況下,Windows裝置在系統防火牆中阻止ICMP。
- 如果使用帶有外部天線的AP,請務必參閱部署指南,檢查哪些天線相容,以及應該插入哪個埠。
- 為了透過網狀鏈路橋接來自不同VLAN的流量,需要停用VLAN透明功能。
- 考慮在AP本地設定系統日誌伺服器,因為它可以提供除錯資訊,否則只能透過控制檯連線使用。
參考資料
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
16-Jan-2024 |
初始版本 |
由思科工程師貢獻
- Tiago AntunesTechnical Leader
 意見
意見