在Catalyst 9000系列交換器上實作BGP EVPN路由原則
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹如何在Catalyst 9000系列交換器上的BGP EVPN VXLAN中實作路由原則。
必要條件
需求
思科建議您瞭解以下主題:
- BGP設定和驗證
- 路由對映和基本BGP路由策略
- EVPN VxLAN
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- Catalyst 9300
- Catalyst 9400
- Catalyst 9500
- Catalyst 9600
- Cisco IOS® XE 17.11.1及更高版本
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
EVPN VxLAN路由策略使用路由對映來控制主機的流量,以及VTEP學習和處理哪些路由:
- 這是EVPN受保護網段型別設計的一個關鍵方面(不在本檔案的範圍),在該設計中,ARP流量僅傳送到中央網關(CGW),因此CGW可以使用自己的MAC地址代理應答,即使對於本地網段流量也是如此。
- 受保護網段能夠控制流量,使所有流量都能通過防火牆的流量檢測和流量策略。
思科還實施了預設網關(DEF GW)擴展社群屬性,以指示CGW擁有哪個MAC/IP字首。

註:EVPN受保護的資料段需要此步驟,此步驟不屬於本文檔的範圍。

提示:要瞭解有關自動RT和自動RD CLI簡化功能的詳細資訊,請參閱在Catalyst 9000系列交換機上為EVPN配置BGP VRF自動RD自動RT
檔案詳細資訊
有關這份檔案的重要詳細資訊:
- BUM流量的複製模式為輸入(單點傳播BUM通道)
- 使用的VLAN為201和202
- 使用的VNI是20101和20201
- 所有路由的流量都傳送到CGW(VTEP沒有自己的SVI)
- IMET路由型別3 BGP字首是中心輻射型(枝葉只接受來自CGW的IMET路由,而不接受來自彼此的IMET路由)
- 路由型別2和5為全網狀

注意:允許全網狀MAC/IP字首的設計決策是為了移動目的。如果枝葉無法看到彼此的RT2,並且主機從一個枝葉移動到另一個枝葉,則假定它是新字首,而不是增加現有RT2的序列號。
支援的路由型別
- Route-type 3(包括組播乙太網標籤路由)
- Route-type 7(IGMP加入同步路由)
- Route-type 8(IGMP離開同步路由)

注意:作為此路由策略的一部分,還支援增強路由型別7和路由型別8。本文檔僅演示如何匹配和過濾路由型別3字首,但驗證和方法適用於所有3種型別
技術
| VRF |
虛擬路由轉送 |
定義與其他VRF和全域性IPv4/IPv6路由域分離的第3層路由域 |
| AF |
地址系列 |
定義BGP處理的型別字首和路由資訊 |
| AS |
自治系統 |
一組網際網路可路由IP字首,它們屬於一個網路或一組網路,都由單個實體或組織管理、控制和監督 |
| EVPN |
乙太網路虛擬私人網路 |
允許BGP傳輸第2層MAC和第3層IP資訊的擴展是EVPN和 使用多協定邊界網關協定(MP-BGP)作為協定,以分發與VXLAN重疊網路相關的可達性資訊。 |
| VXLAN |
虛擬可擴充LAN(區域網路) |
VXLAN的用途是克服VLAN和STP的固有限制。建議採用的IETF標準[RFC 7348]提供與VLAN相同的乙太網第2層網路服務,但具有更高的靈活性。功能上,它是UDP內MAC封裝協定,在第3層底層網路上作為虛擬重疊運行。 |
| CGW |
集中式網關 |
以及網關SVI不在每個枝葉上的EVPN的實現。相反,所有路由都是由使用非對稱IRB(整合路由和橋接)的特定枝葉完成的 |
| DEF網關 |
預設閘道 |
在「l2vpn evpn」配置部分下通過命令「default-gateway advertise enable」新增到MAC/IP字首的BGP擴展社群屬性。 |
| IMET |
包含型組播乙太網標籤(路由) |
也稱為BGP type-3路由。此路由型別在EVPN中用於在VTEP之間傳送BUM(廣播/未知單點傳播/多點傳送)流量。 |
設定
網路圖表
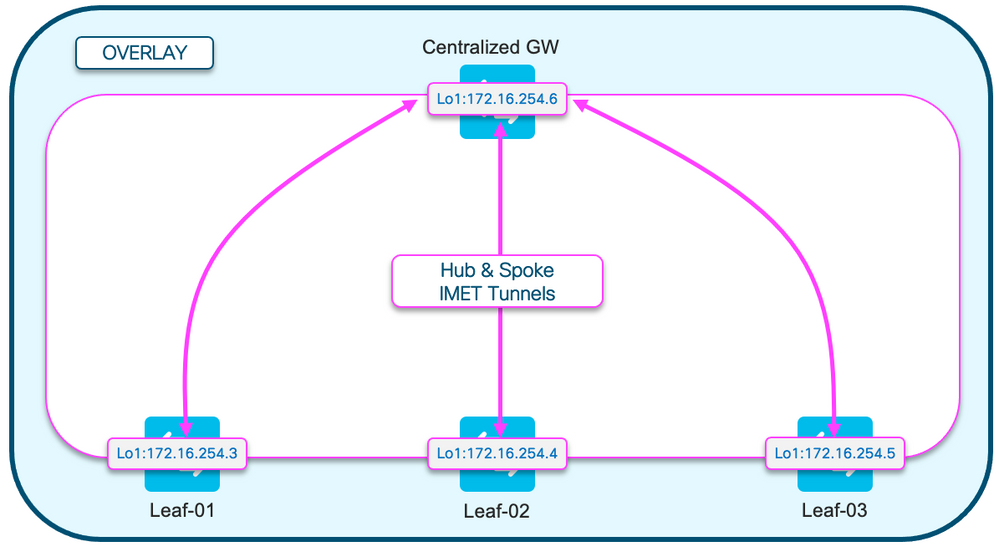
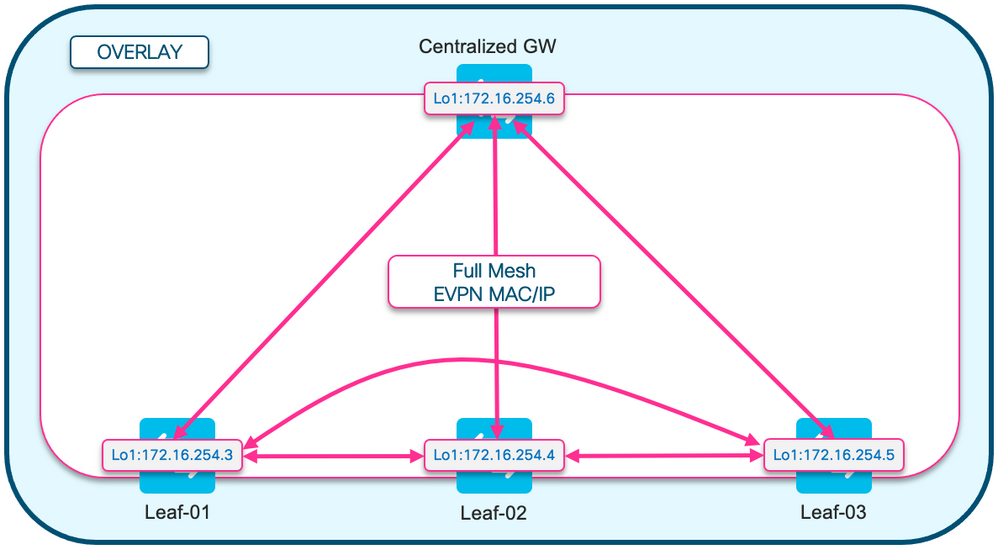
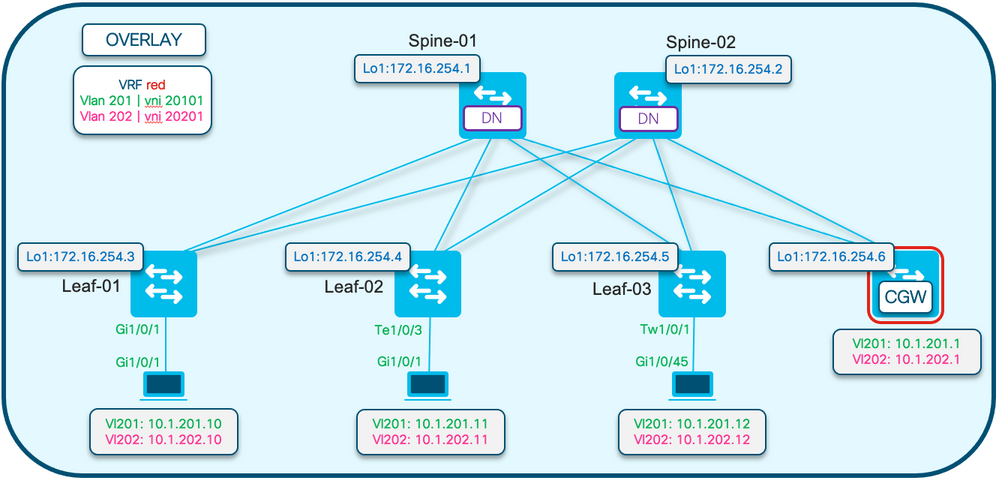
組態
本節顯示來自枝葉–01和邊界枝葉(CGW)交換機的配置示例。其他枝葉配置相同,因此此處不重複。
- 本檔案中的範例基於輸入複製,並示範了如何應用原則以控制哪些VTEP可以傳送廣播和其他泛洪流量
Leaf-01(基本EVPN配置)
Leaf-01#show run | sec l2vpn
l2vpn evpn
replication-type static
flooding-suppression address-resolution disable <-- Disables ARP caching so ARP is always sent up to the CGW
router-id Loopback1
l2vpn evpn instance 201 vlan-based encapsulation vxlan replication-type ingress multicast advertise enable l2vpn evpn instance 202 vlan-based encapsulation vxlan replication-type ingress multicast advertise enable
Leaf-01#show run | sec vlan config
vlan configuration 201 member evpn-instance 201 vni 20101 vlan configuration 202 member evpn-instance 202 vni 20201
Leaf-01#show run int nve 1 Building configuration... Current configuration : 327 bytes ! interface nve1 no ip address source-interface Loopback1 host-reachability protocol bgp member vni 20201 ingress-replication member vni 20101 ingress-replication end
ip bgp-community new-format <-- Required to see community in aa:nn format
Leaf-01(路由過濾)
確定要匹配的路由目標。
- 為簡化CLI,本文檔中的示例使用自動路由目標功能。
- 由於這是自動的,請運行此命令以瞭解如何配置社群清單
Leaf-01#show l2vpn evpn route-target Route Target EVPN Instances 65001:201 201 <-- Route-targets for the Vlan/VNI of interest 65001:202 202
ip extcommunity-list expanded ALLOW-RT2 permit 65001:20[0-9] <-- match Route-targets 65001:200 - 65001:209
!
ip community-list standard BLOCK-RT3 permit 999:999 <-- Arbitrary RT used to mark IMET prefixes as they are advertised
route-map POLICY-IN deny 5 match community BLOCK-RT3 exact-match <-- Deny prefixes that match RT 999:999 in standard community list ! route-map POLICY-IN permit 10 <-- Permit any other prefixes that do not contain 999:999 ! route-map POLICY-OUT permit 5 match extcommunity ALLOW-RT2 <-- Match the auto-RT in the extended community list match evpn route-type 3 <-- AND match route-type 3 prefixes set community 999:999 <-- Set additional standard community to advertised prefixes ! route-map POLICY-OUT permit 10 <-- Permit prefixes that are not RT3 to be sent out without additional attributes added
router bgp 65001 bgp router-id 172.16.255.3 bgp log-neighbor-changes no bgp default ipv4-unicast neighbor 172.16.255.1 remote-as 65001 neighbor 172.16.255.1 update-source Loopback0 neighbor 172.16.255.2 remote-as 65001 neighbor 172.16.255.2 update-source Loopback0 ! address-family ipv4 exit-address-family ! address-family ipv4 mvpn neighbor 172.16.255.1 activate neighbor 172.16.255.1 send-community both neighbor 172.16.255.2 activate neighbor 172.16.255.2 send-community both exit-address-family ! address-family l2vpn evpn neighbor 172.16.255.1 activate neighbor 172.16.255.1 send-community both <-- Send both standard and extended community attributes neighbor 172.16.255.1 route-map POLICY-IN in <-- Apply inbound policy to deny prefixes with 999:999 community string neighbor 172.16.255.1 route-map POLICY-OUT out <-- Apply outbound policy to match RT3 / apply standard community & permit other RT2 prefixes as normal neighbor 172.16.255.2 activate neighbor 172.16.255.2 send-community both neighbor 172.16.255.2 route-map POLICY-IN in neighbor 172.16.255.2 route-map POLICY-OUT out exit-address-family
CGW(基本配置)
CGW#show running-config | beg l2vpn evpn instance 201 l2vpn evpn instance 201 vlan-based encapsulation vxlan replication-type ingress default-gateway advertise enable <-- adds the BGP attribute EVPN DEF GW:0:0 to the MAC/IP prefix multicast advertise enable ! l2vpn evpn instance 202 vlan-based encapsulation vxlan replication-type ingress default-gateway advertise enable <-- adds the BGP attribute EVPN DEF GW:0:0 to the MAC/IP prefix multicast advertise enable
CGW#show running-config | sec vlan config vlan configuration 201
member evpn-instance 201 vni 20101 vlan configuration 202 member evpn-instance 202 vni 20201
CGW#show run int nve 1 Building configuration... Current configuration : 313 bytes ! interface nve1 no ip address source-interface Loopback1 host-reachability protocol bgp member vni 10101 mcast-group 225.0.0.101 member vni 10102 mcast-group 225.0.0.102
member vni 20101 ingress-replication local-routing <-- 'ingress-replication' (Unicast all BUM traffic) / 'local-routing' (Enables vxlan centralized gateway forwarding) member vni 20201 ingress-replication local-routing member vni 50901 vrf green end
CGW#show run interface vlan 201 Building configuration... Current configuration : 231 bytes ! interface Vlan201 mac-address 0000.beef.cafe <-- MAC is static in this example for viewing simplicity. This is not required vrf forwarding red <-- SVI is in VRF red ip address 10.1.201.1 255.255.255.0 no ip redirects ip local-proxy-arp <-- Sets CGW to Proxy reply even for local subnet ARP requests ip pim sparse-mode ip route-cache same-interface <-- This is auto added when local-proxy-arp is configured. However, this is a legacy 'fast switching' command that is not used by CEF & is not required for forwarding ip igmp version 3 no autostate end CGW#show run interface vlan 202 Building configuration... Current configuration : 163 bytes ! interface Vlan202 mac-address 0000.beef.cafe vrf forwarding red ip address 10.1.202.1 255.255.255.0
no ip redirects
ip local-proxy-arp ip pim sparse-mode
ip route-cache same-interface ip igmp version 3 no autostate end
CGW#sh run vrf red
Building configuration...
Current configuration : 873 bytes
vrf definition red rd 2:2 ! address-family ipv4 route-target export 2:2 route-target import 2:2 route-target export 2:2 stitching route-target import 2:2 stitching exit-address-family

註:在CGW上未應用BGP策略。允許CGW接收和傳送所有字首型別(RT2、RT5 / RT3)。
驗證
網路圖表
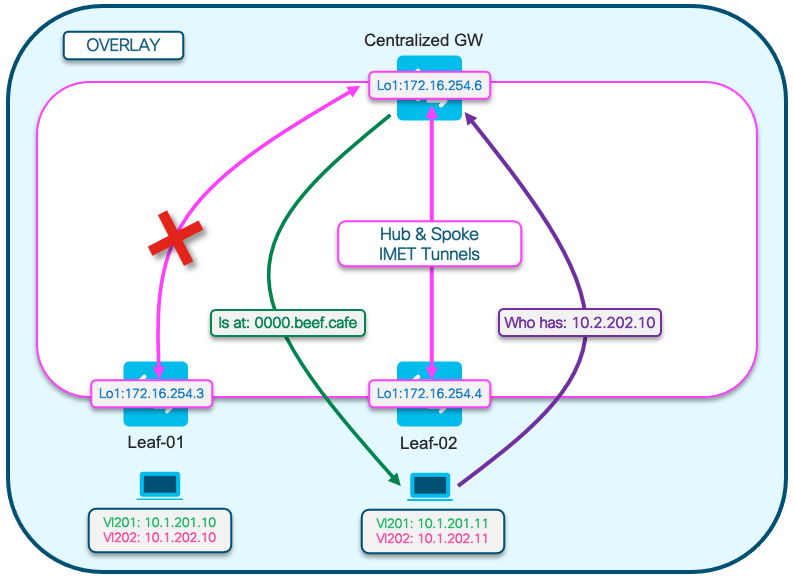
此圖有助於直觀顯示本節所述的ARP解析過程。
- ARP請求顯示為紫色。
- 此ARP請求用於解析主機10.1.202.10 Leaf-01的MAC地址
- 請注意,紫色線在CGW終止,並且未到達枝葉01
- ARP應答顯示為綠色,其中包含用於Vlan 202的CGW SVI的MAC
- 請注意,綠線來自CGW,而不是來自實際主機
- 紅色X表示此通訊不涉及向枝葉01傳送流量
Route-Type 3策略(Leaf-01)
驗證應用於枝葉的路由對映是否正確過濾。我們只應看到來自CGW的IMET字首,而不是其他枝葉。
- 此處只顯示一個枝葉,但應在所有相關枝葉上執行此檢查

註:應用路由對映後,必須清除BGP到鄰居才能使策略設定生效。
有兩種方法可以檢視安裝了哪種route-type 3:
- 檢查BGP條目
- 檢查l2route
檢查BGP條目(Leaf-01)
Leaf-01#show bgp l2vpn evpn route-type 3 | inc Tunnel End
PMSI Attribute: Flags:0x0, Tunnel type:IR, length 4, vni:20101, tunnel identifier: < Tunnel Endpoint: 172.16.254.6 > <-- No RT3 prefixes present other than the CGW 172.16.254.6
PMSI Attribute: Flags:0x0, Tunnel type:IR, length 4, vni:20201, tunnel identifier: < Tunnel Endpoint: 172.16.254.6 >
PMSI Attribute: Flags:0x0, Tunnel type:IR, length 4, vni:20101, tunnel identifier: < Tunnel Endpoint: 172.16.254.6 >
PMSI Attribute: Flags:0x0, Tunnel type:IR, length 4, vni:20201, tunnel identifier: < Tunnel Endpoint: 172.16.254.6 >
檢查l2route
Leaf-01-F241.03.23-9300#show l2route evpn imet EVI ETAG Prod Router IP Addr Type Label Tunnel ID Multicast Proxy ----- ---------- ------ --------------------------------------- ----- -------- --------------------------------------- --------------- 201 0 BGP 172.16.254.6 6 20101 172.16.254.6 No <-- Only remote IMET producer is the CGW 201 0 L2VPN 172.16.254.3 6 20101 172.16.254.3 IGMP 202 0 BGP 172.16.254.6 6 20201 172.16.254.6 No 202 0 L2VPN 172.16.254.3 6 20201 172.16.254.3 IGMP <-- Only remote IMET producer is the CGW

註:路由對映過濾器的驗證僅在訪問VTEP上完成。CGW接受所有型別3字首,因此不會實施任何路由對映。
本機路由(CGW)
驗證發生本地網段ARP解析時CGW是否使用自己的MAC進行應答。
- 除了驗證configure部分中顯示的配置之外,沒有show命令
- 我們可以驗證這一點,方法是:當主機為另一枝葉上的主機解析ARP時,確認主機上的MAC已程式設計。
捕獲從Leaf-02的主機傳送到Leaf-01的主機的ARP解析請求(這是使用EPC捕獲在面向Leaf-02主機的訪問介面上完成的)
- Leaf-01主機實際MAC:0006.f601.cd45
- 響應ARP請求的CGW MAC: 0000.beef.cafe
Leaf-02-F241.03.23-9400#show mon cap 1 buff br | i ARP 32 10.356291 00:06:f6:17:ee:c4 -> ff:ff:ff:ff:ff:ff ARP 64 Who has 10.1.202.10? Tell 10.1.202.11 <-- ARP request from Leaf-02 host 33 10.357140 00:00:be:ef:ca:fe -> 00:06:f6:17:ee:c4 ARP 68 10.1.202.10 is at 00:00:be:ef:ca:fe <-- ARP reply is the CGW MAC
Leaf-02-F241.03.23-9400#show mon cap 1 buff det | b Frame 32 Frame 32: 64 bytes on wire (512 bits), 64 bytes captured (512 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0 <...snip...> [Protocols in frame: eth:ethertype:vlan:ethertype:arp] Ethernet II, Src: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4), Dst: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff) Destination: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff) Address: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff) .... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default) .... ...1 .... .... .... .... = IG bit: Group address (multicast/broadcast) Source: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) Address: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) Type: 802.1Q Virtual LAN (0x8100) 802.1Q Virtual LAN, PRI: 0, DEI: 0, ID: 202 <-- Vlan 202 000. .... .... .... = Priority: Best Effort (default) (0) ...0 .... .... .... = DEI: Ineligible .... 0000 1100 1010 = ID: 202 Type: ARP (0x0806) Padding: 0000000000000000000000000000 Trailer: 00000000 Address Resolution Protocol (request) <-- ARP Request Hardware type: Ethernet (1) Protocol type: IPv4 (0x0800) Hardware size: 6 Protocol size: 4 Opcode: request (1) Sender MAC address: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) Sender IP address: 10.1.202.11 Target MAC address: 00:00:00:00:00:00 (00:00:00:00:00:00) Target IP address: 10.1.202.10 <-- Leaf-02 Host Frame 33: 68 bytes on wire (544 bits), 68 bytes captured (544 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0 <...snip...> Ethernet II, Src: 00:00:be:ef:ca:fe (00:00:be:ef:ca:fe), Dst: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) Destination: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) Address: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) Source: 00:00:be:ef:ca:fe (00:00:be:ef:ca:fe) Address: 00:00:be:ef:ca:fe (00:00:be:ef:ca:fe) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) Type: CiscoMetaData (0x8909) Cisco MetaData Version: 1 Length: 1 Options: 0x0001 SGT: 0 Type: ARP (0x0806) Padding: 00000000000000000000 Trailer: 0000000000000000 Address Resolution Protocol (reply) Hardware type: Ethernet (1) Protocol type: IPv4 (0x0800) Hardware size: 6 Protocol size: 4 Opcode: reply (2) Sender MAC address: 00:00:be:ef:ca:fe (00:00:be:ef:ca:fe) <-- ARP Reply is the CGW MAC 0000.beef.cafe Sender IP address: 10.1.202.10 Target MAC address: 00:06:f6:17:ee:c4 (00:06:f6:17:ee:c4) <-- MAC of host off Leaf-02 0006.f617.eec4 Target IP address: 10.1.202.11
疑難排解
調試路由對映策略(入站)
確認入站路由對映是否按預期工作
啟用L2VPN EVPN更新調試
Leaf-02#debug bgp l2vpn evpn updates
BGP updates debugging is on for address family: L2VPN E-VPN
Leaf-02#debug bgp l2vpn evpn updates events
BGP update events debugging is on for address family: L2VPN E-VPN
清除bgp address-family以例項化路由策略
Leaf-02#clear bgp l2vpn evpn *
驗證僅從CGW接受路由型別3並從所有其他枝葉拒絕
Leaf-02#show log | i rcvd \[3\] *Jul 4 06:40:41.556: BGP(10): 172.16.255.2 rcvd [3][172.16.254.6:202][0][32][172.16.254.6]/17 <-- Only accepted Type-3 is from the CGW (172.16.254.6) *Jul 4 06:40:41.557: BGP(10): 172.16.255.2 rcvd [3][172.16.254.6:201][0][32][172.16.254.6]/17 *Jul 4 06:40:41.557: BGP(10): 172.16.255.2 rcvd [3][172.16.254.3:202][0][32][172.16.254.3]/17 -- DENIED due to: route-map; *Jul 4 06:40:41.557: BGP(10): 172.16.255.2 rcvd [3][172.16.254.5:202][0][32][172.16.254.5]/17 -- DENIED due to: route-map; *Jul 4 06:40:41.557: BGP(10): 172.16.255.2 rcvd [3][172.16.254.3:201][0][32][172.16.254.3]/17 -- DENIED due to: route-map; *Jul 4 06:40:41.557: BGP(10): 172.16.255.2 rcvd [3][172.16.254.5:201][0][32][172.16.254.5]/17 -- DENIED due to: route-map;
驗證路由對映策略(出站)
通過在CGW上檢查來自枝葉的第3類字首,驗證是否已將標準社群應用於它們。
- 此輸出範例顯示來自Leaf-01和Leaf-02的BGP字首,其中為Vlan 202網段注入了團體屬性

提示:請記住,CGW不會過濾任何字首,因此我們可以從CGW角度驗證完整的BGP表。
CGW#show bgp l2vpn evpn route-type 3
BGP routing table entry for [3][172.16.254.6:202][0][32][172.16.254.3]/17, version 461855 Paths: (1 available, best #1, table evi_202) <-- The EVI context for the vlan 202 segment Not advertised to any peer Refresh Epoch 4 Local, imported path from [3][172.16.254.3:202][0][32][172.16.254.3]/17 (global) 172.16.254.3 (metric 3) (via default) from 172.16.255.2 (172.16.255.2) Origin incomplete, metric 0, localpref 100, valid, internal, best Community: 999:999 <-- Route-map logic is good. Standard community applied to the Type-3 Extended Community: RT:65001:202 ENCAP:8 EVPN Mcast Flags:1 Originator: 172.16.255.3, Cluster list: 172.16.255.2 PMSI Attribute: Flags:0x0, Tunnel type:IR, length 4, vni:20201, tunnel identifier: < Tunnel Endpoint: 172.16.254.3 > <-- Type-3 tunnel rx pathid: 0, tx pathid: 0x0 Updated on Jan 22 2025 19:02:18 UTC BGP routing table entry for [3][172.16.254.6:202][0][32][172.16.254.4]/17, version 605955 Paths: (1 available, best #1, table evi_202) Not advertised to any peer Refresh Epoch 4 Local, imported path from [3][172.16.254.4:202][0][32][172.16.254.4]/17 (global) 172.16.254.4 (metric 3) (via default) from 172.16.255.2 (172.16.255.2) Origin incomplete, metric 0, localpref 100, valid, internal, best Community: 999:999 Extended Community: RT:65001:202 ENCAP:8 EVPN Mcast Flags:1 Originator: 172.16.255.4, Cluster list: 172.16.255.2 PMSI Attribute: Flags:0x0, Tunnel type:IR, length 4, vni:20201, tunnel identifier: < Tunnel Endpoint: 172.16.254.4 > rx pathid: 0, tx pathid: 0x0 Updated on Jan 30 2025 18:50:49 UTC
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
18-Aug-2023 |
初始版本 |
由思科工程師貢獻
- Ambrose Taylor
- Saurav Dasgupta
 意見
意見