在具有VPN 3000集中器的IOS路由器上使用NEM的EzVPN配置示例
目錄
簡介
本檔案將說明將Cisco IOS®路由器設定為網路擴充模式(NEM)中的EzVPN,以連線到Cisco VPN 3000集中器的程式。新的EzVPN Phase II功能支援基本網路地址轉換(NAT)配置。EzVPN Phase II源自Unity協定(VPN客戶端軟體)。 遠端裝置始終是IPsec隧道的發起方。但是,EzVPN客戶端上無法配置網際網路金鑰交換(IKE)和IPsec提議。VPN客戶端與伺服器協商提議。
要使用Easy VPN在PIX/ASA 7.x和Cisco 871路由器之間配置IPsec,請參閱將ASA 5500作為伺服器並將Cisco 871作為Easy VPN Remote配置示例的PIX/ASA 7.x Easy VPN。
要在Cisco IOS® Easy VPN遠端硬體客戶端和PIX Easy VPN伺服器之間配置IPsec,請參閱IOS Easy VPN遠端硬體客戶端到PIX Easy VPN伺服器配置示例。
要將Cisco 7200路由器配置為EzVPN,將Cisco 871路由器配置為Easy VPN Remote,請參閱7200 Easy VPN Server to 871 Easy VPN Remote配置示例。
必要條件
需求
在嘗試此配置之前,請檢查Cisco IOS路由器是否支援EzVPN Phase II功能,並且是否具有用於建立IPsec隧道的端到端連線的IP連線。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
-
Cisco IOS軟體版本12.2(8)YJ(EzVPN階段II)
-
VPN 3000集中器3.6.x
-
思科1700路由器
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
注意:此配置最近在Cisco 3640路由器上進行了測試,該路由器採用Cisco IOS軟體版本12.4(8)和VPN 3000 Concentrator 4.7.x版本。
慣例
如需文件慣例的詳細資訊,請參閱思科技術提示慣例。
配置VPN 3000 Concentrator
工作
本節提供配置VPN 3000集中器的資訊。
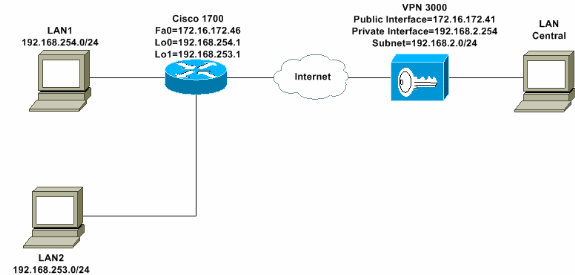
網路圖表
本檔案會使用下圖中所示的網路設定。環回介面用作內部子網,而FastEthernet 0是Internet的預設子網。
逐步說明
請完成以下步驟:
-
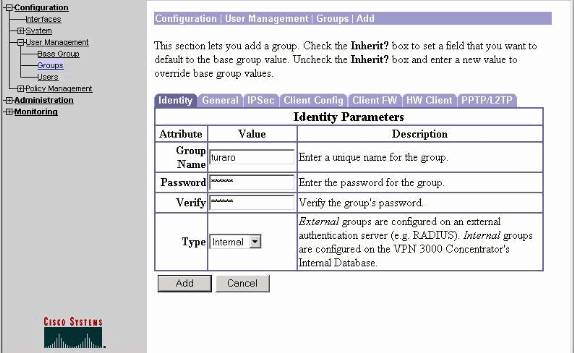
選擇Configuration > User Management > Groups > Add並定義組名稱和密碼,以便為使用者配置IPsec組。
此示例使用組名turaro和密碼/驗證tululo。
-
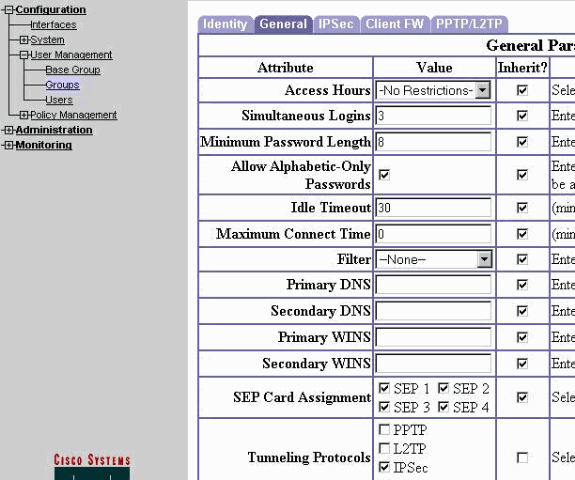
選擇Configuration > User Management > Groups > turaro > General以啟用IPSec並禁用點對點隧道協定(PPTP)和第2層隧道協定(L2TP)。
進行選擇,然後按一下Apply。
-
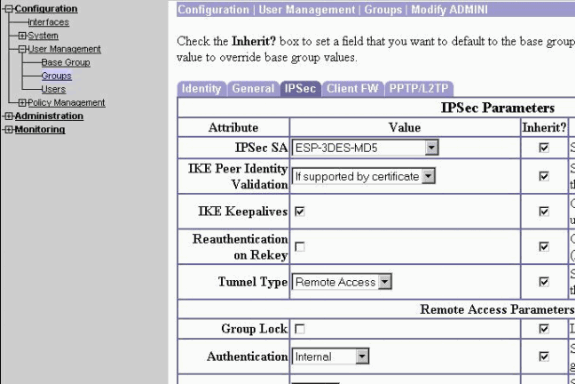
將Authentication設定為Internal for Extended Authentication(Xauth)並確保隧道型別為Remote Access,IPSec SA為ESP-3DES-MD5。
-
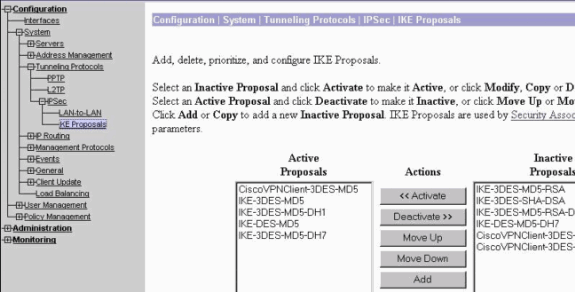
選擇Configuration > System > Tunneling Protocols > IPSec > IKE Proposals,以確保Cisco VPN客戶端(CiscoVPNClient-3DES-MD5)處於Active Proposals for IKE(Phase 1)中。
注意:從VPN集中器4.1.x中,確保Cisco VPN客戶端位於IKE活動建議清單(第1階段)中的過程有所不同。 選擇Configuration > Tunneling and Security > IPSec > IKE Proposals。
-
驗證IPsec安全關聯(SA)。
在第3步中,您的IPsec SA是ESP-3DES-MD5。如果您願意,可以建立一個新的IPsec SA,但請確保在您的組上使用正確的IPsec SA。您應該為您使用的IPsec SA禁用完全轉發保密(PFS)。通過選擇Configuration > Policy Management > Traffic Management > SA選擇Cisco VPN Client作為IKE建議。在文本框中鍵入SA名稱並進行適當的選擇,如下所示:
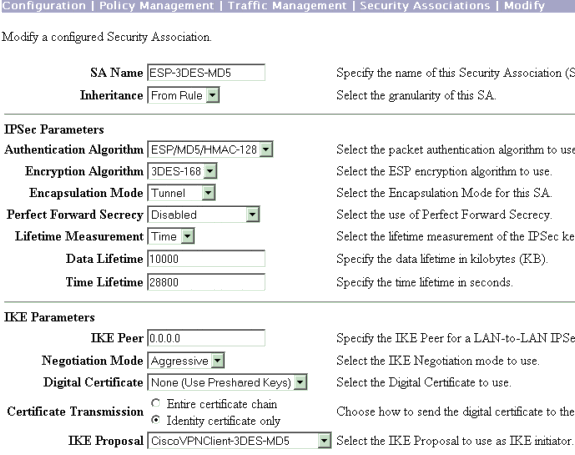
注意:如果您更喜歡選擇預定義SA,則此步驟和下一步是可選的。如果您的客戶端具有動態分配的IP地址,請在IKE對等體文本框中使用0.0.0.0。確保將IKE建議設定為CiscoVPNClient-3DES-MD5,如以下示例所示。
-
不能按一下Allow the networks in the list以繞過通道。原因是支援拆分隧道,但EzVPN客戶端功能不支援旁路功能。

-
選擇Configuration > User Management > Users以新增使用者。定義使用者名稱和密碼,將其分配給組,然後按一下Add。
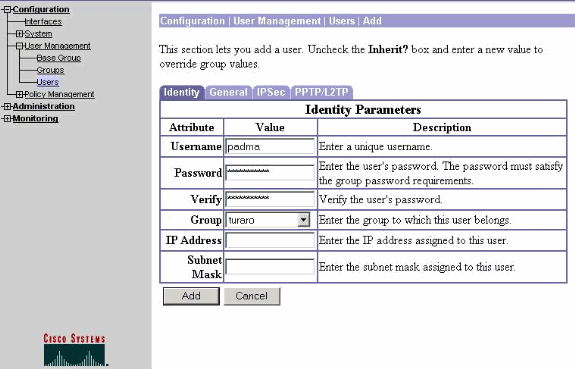
-
選擇Administration > Admin Sessions,然後檢查使用者是否已連線。在NEM中,VPN集中器不分配池中的IP地址。
注意:如果您希望選擇預定義的SA,則此步驟是可選的。
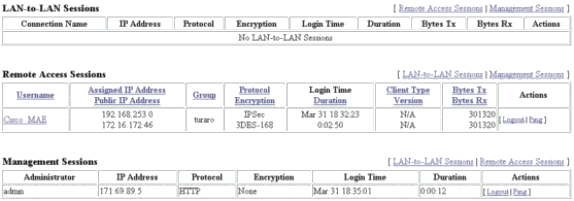
-
按一下「Save Needed」或「Save」圖示以儲存組態。
路由器配置
顯示版本輸出
show version Cisco Internetwork Operating System Software IOS (tm) C1700 Software (C1700-BK9NO3R2SY7-M), Version 12.2(8)YJ, EARLY DEPLOYMENT RELEASE SOFTWARE (fc1) 1721-1(ADSL) uptime is 4 days, 5 hours, 33 minutes System returned to ROM by reload System image file is "flash:c1700-bk9no3r2sy7-mz.122-8.YJ.bin" cisco 1721 (MPC860P) processor (revision 0x100) with 88474K/9830K bytes 16384K bytes of processor board System flash (Read/Write)
| 1721-1 |
|---|
1721-1(ADSL)#show run version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname 1721-1(ADSL) ! !--- Specify the configuration name !--- to be assigned to the interface. crypto ipsec client ezvpn SJVPN !--- Tunnel control; automatic is the default. connect auto !--- The group name and password should be the same as given in the VPN Concentrator. group turaro key tululo !--- The mode that is chosen as the network extension. mode network-extension !--- The tunnel peer end (VPN Concentrator public interface IP address). peer 172.16.172.41 ! interface Loopback0 ip address 192.168.254.1 255.255.255.0 !--- Configure the Loopback interface !--- as the inside interface. ip nat inside !--- Specifies the Cisco EzVPN Remote configuration name !--- to be assigned to the inside interface. crypto ipsec client ezvpn SJVPN inside ! interface Loopback1 ip address 192.168.253.1 255.255.255.0 ip nat inside crypto ipsec client ezvpn SJVPN inside ! interface FastEthernet0 ip address 172.16.172.46 255.255.255.240 !--- Configure the FastEthernet interface !--- as the outside interface. ip nat outside !--- Specifies the Cisco EzVPN Remote configuration name !--- to be assigned to the first outside interface, because !--- outside is not specified for the interface. !--- The default is outside. crypto ipsec client ezvpn SJVPN ! !--- Specify the overload option with the ip nat command !--- in global configuration mode in order to enable !--- Network Address Translation (NAT) of the inside source address !--- so that multiple PCs can use the single IP address. ip nat inside source route-map EZVPN interface FastEthernet0 overload ip classless ip route 0.0.0.0 0.0.0.0 172.16.172.41 ! access-list 177 deny ip 192.168.254.0 0.0.0.255 192.168.2.0 0.0.0.255 access-list 177 deny ip 192.168.253.0 0.0.0.255 192.168.2.0 0.0.0.255 access-list 177 permit ip 192.168.253.0 0.0.0.255 any access-list 177 permit ip 192.168.254.0 0.0.0.255 any ! route-map EZVPN permit 10 match ip address 177 ! ! line con 0 line aux 0 line vty 0 4 password cisco login ! no scheduler allocate end |
驗證
使用本節內容,確認您的組態是否正常運作。
輸出直譯器工具(僅供已註冊客戶使用)(OIT)支援某些show命令。使用OIT檢視show命令輸出的分析。
配置兩台裝置後,Cisco 3640路由器會嘗試使用對等IP地址聯絡VPN集中器來設定VPN隧道。交換初始ISAKMP引數後,路由器會顯示以下訊息:
Pending XAuth Request, Please enter the following command: crypto ipsec client ezvpn xauth
您必須輸入crypto ipsec client ezvpn xauth命令,該命令會提示您輸入使用者名稱和密碼。這應該與VPN集中器上配置的使用者名稱和密碼匹配(步驟7)。 一旦兩個對等體同意使用者名稱和密碼,則同意其餘引數並啟動IPsec VPN隧道。
EZVPN(SJVPN): Pending XAuth Request, Please enter the following command: EZVPN: crypto ipsec client ezvpn xauth !--- Enter the crypto ipsec client ezvpn xauth command. crypto ipsec client ezvpn xauth Enter Username and Password.: padma Password: : password
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
疑難排解指令
輸出直譯器工具(僅供註冊客戶使用)支援某些show命令,此工具可讓您檢視show命令輸出的分析。
註:發出debug指令之前,請先參閱有關Debug指令的重要資訊。
-
debug crypto ipsec client ezvpn — 顯示顯示EzVPN客戶端功能的配置和實現的資訊。
-
debug crypto ipsec — 顯示有關IPsec連線的調試資訊。
-
debug crypto isakmp — 顯示有關IPsec連線的調試資訊,並顯示由於兩端的不相容性而被拒絕的第一組屬性。
-
show debug — 顯示每個調試選項的狀態。
Debug命令的輸出
輸入crypto ipsec client ezvpn SJVPN 命令後,EzVPN Client會嘗試連線到伺服器。如果在組配置下更改connect manual命令,請輸入crypto ipsec client ezvpn connect SJVPN命令以啟動與伺服器的建議交換。
4d05h: ISAKMP (0:3): beginning Aggressive Mode exchange
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) AG_INIT_EXCH
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) AG_INIT_EXCH
4d05h: ISAKMP (0:3): processing SA payload. message ID = 0
4d05h: ISAKMP (0:3): processing ID payload. message ID = 0
4d05h: ISAKMP (0:3): processing vendor id payload
4d05h: ISAKMP (0:3): vendor ID is Unity
4d05h: ISAKMP (0:3): processing vendor id payload
4d05h: ISAKMP (0:3): vendor ID seems Unity/DPD but bad major
4d05h: ISAKMP (0:3): vendor ID is XAUTH
4d05h: ISAKMP (0:3): processing vendor id payload
4d05h: ISAKMP (0:3): vendor ID is DPD
4d05h: ISAKMP (0:3) local preshared key found
4d05h: ISAKMP (0:3) Authentication by xauth preshared
4d05h: ISAKMP (0:3): Checking ISAKMP transform 6 against priority 65527 policy
4d05h: ISAKMP: encryption 3DES-CBC
4d05h: ISAKMP: hash MD5
4d05h: ISAKMP: default group 2
4d05h: ISAKMP: auth XAUTHInitPreShared
4d05h: ISAKMP: life type in seconds
4d05h: ISAKMP: life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP (0:3): Encryption algorithm offered does not match policy!
4d05h: ISAKMP (0:3): atts are not acceptable. Next payload is 0
4d05h: ISAKMP (0:3): Checking ISAKMP transform 6 against priority 65528 policy
4d05h: ISAKMP: encryption 3DES-CBC
4d05h: ISAKMP: hash MD5
4d05h: ISAKMP: default group 2
4d05h: ISAKMP: auth XAUTHInitPreShared
4d05h: ISAKMP: life type in seconds
4d05h: ISAKMP: life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP (0:3): Encryption algorithm offered does not match policy!
4d05h: ISAKMP (0:3): atts are not acceptable. Next payload is 0
4d05h: ISAKMP (0:3): Checking ISAKMP transform 6 against priority 65529 policy
4d05h: ISAKMP: encryption 3DES-CBC
4d05h: ISAKMP: hash MD5
4d05h: ISAKMP: default group 2
4d05h: ISAKMP: auth XAUTHInitPreShared
4d05h: ISAKMP: life type in seconds
4d05h: ISAKMP: life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP (0:3): Encryption algorithm offered does not match policy!
4d05h: ISAKMP (0:3): atts are not acceptable. Next payload is 0
4d05h: ISAKMP (0:3): Checking ISAKMP transform 6 against priority 65530 policy
4d05h: ISAKMP: encryption 3DES-CBC
4d05h: ISAKMP: hash MD5
4d05h: ISAKMP: default group 2
4d05h: ISAKMP: auth XAUTHInitPreShared
4d05h: ISAKMP: life type in seconds
4d05h: ISAKMP: life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP (0:3): Encryption algorithm offered does not match policy!
4d05h: ISAKMP (0:3): atts are not acceptable. Next payload is 0
4d05h: ISAKMP (0:3): Checking ISAKMP transform 6 against priority 65531 policy
4d05h: ISAKMP: encryption 3DES-CBC
4d05h: ISAKMP: hash MD5
4d05h: ISAKMP: default group 2
4d05h: ISAKMP: auth XAUTHInitPreShared
4d05h: ISAKMP: life type in seconds
4d05h: ISAKMP: life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP (0:3): Hash algorithm offered does not match policy!
4d05h: ISAKMP (0:3): atts are not acceptable. Next payload is 0
4d05h: ISAKMP (0:3): Checking ISAKMP transform 6 against priority 65532 policy
4d05h: ISAKMP: encryption 3DES-CBC
4d05h: ISAKMP: hash MD5
4d05h: ISAKMP: default group 2
4d05h: ISAKMP: auth XAUTHInitPreShared
4d05h: ISAKMP: life type in seconds
4d05h: ISAKMP: life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP (0:3): atts are acceptable. Next payload is 0
4d05h: ISAKMP (0:3): processing KE payload. message ID = 0
4d05h: ISAKMP (0:3): processing NONCE payload. message ID = 0
4d05h: ISAKMP (0:3): SKEYID state generated
4d05h: ISAKMP (0:3): processing HASH payload. message ID = 0
4d05h: ISAKMP (0:3): SA has been authenticated with 172.16.172.41
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) AG_INIT_EXCH
4d05h: ISAKMP (0:3): Input = IKE_MESG_FROM_PEER, IKE_AM_EXCH
Old State = IKE_I_AM1 New State = IKE_P1_COMPLETE
4d05h: IPSEC(key_engine): got a queue event...
4d05h: IPSec: Key engine got KEYENG_IKMP_MORE_SAS message
4d05h: ISAKMP (0:3): Need XAUTH
4d05h: ISAKMP (0:3): Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
!--- Phase 1 (ISAKMP) is complete.
4d05h: ISAKMP: received ke message (6/1)
4d05h: ISAKMP: received KEYENG_IKMP_MORE_SAS message
4d05h: ISAKMP: set new node -857862190 to CONF_XAUTH
!--- Initiate extended authentication.
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) CONF_XAUTH
4d05h: ISAKMP (0:3): purging node -857862190
4d05h: ISAKMP (0:3): Sending initial contact.
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) CONF_XAUTH
4d05h: ISAKMP: set new node -1898481791 to CONF_XAUTH
4d05h: ISAKMP (0:3): processing transaction payload from
172.16.172.41. message ID = -1898481791
4d05h: ISAKMP: Config payload REQUEST
4d05h: ISAKMP (0:3): checking request:
4d05h: ISAKMP: XAUTH_TYPE_V2
4d05h: ISAKMP: XAUTH_USER_NAME_V2
4d05h: ISAKMP: XAUTH_USER_PASSWORD_V2
4d05h: ISAKMP: XAUTH_MESSAGE_V2
4d05h: ISAKMP (0:3): Xauth process request
4d05h: ISAKMP (0:3): Input = IKE_MESG_FROM_PEER, IKE_CFG_REQUEST
Old State = IKE_P1_COMPLETE New State = IKE_XAUTH_REPLY_AWAIT
4d05h: EZVPN(SJVPN): Current State: READY
4d05h: EZVPN(SJVPN): Event: XAUTH_REQUEST
4d05h: EZVPN(SJVPN): ezvpn_xauth_request
4d05h: EZVPN(SJVPN): ezvpn_parse_xauth_msg
4d05h: EZVPN: Attributes sent in xauth request message:
4d05h: XAUTH_TYPE_V2(SJVPN): 0
4d05h: XAUTH_USER_NAME_V2(SJVPN):
4d05h: XAUTH_USER_PASSWORD_V2(SJVPN):
4d05h: XAUTH_MESSAGE_V2(SJVPN) <Enter Username and Password.>
4d05h: EZVPN(SJVPN): New State: XAUTH_REQ
4d05h: ISAKMP (0:3): Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Old State = IKE_XAUTH_REPLY_AWAIT New State = IKE_XAUTH_REPLY_AWAIT
4d05h: EZVPN(SJVPN): Pending XAuth Request, Please enter the following command:
4d05h: EZVPN: crypto ipsec client ezvpn xauth
!--- Enter the crypto ipsec client ezvpn xauth command.
crypto ipsec client ezvpn xauth
Enter Username and Password.: padma
Password: : password
!--- The router requests your username and password that is !--- configured on the server.
4d05h: EZVPN(SJVPN): Current State: XAUTH_REQ
4d05h: EZVPN(SJVPN): Event: XAUTH_PROMPTING
4d05h: EZVPN(SJVPN): New State: XAUTH_PROMPT
1721-1(ADSL)#
4d05h: EZVPN(SJVPN): Current State: XAUTH_PROMPT
4d05h: EZVPN(SJVPN): Event: XAUTH_REQ_INFO_READY
4d05h: EZVPN(SJVPN): ezvpn_xauth_reply
4d05h: XAUTH_TYPE_V2(SJVPN): 0
4d05h: XAUTH_USER_NAME_V2(SJVPN): Cisco_MAE
4d05h: XAUTH_USER_PASSWORD_V2(SJVPN): <omitted>
4d05h: EZVPN(SJVPN): New State: XAUTH_REPLIED
4d05h: xauth-type: 0
4d05h: username: Cisco_MAE
4d05h: password: <omitted>
4d05h: message <Enter Username and Password.>
4d05h: ISAKMP (0:3): responding to peer config from 172.16.172.41. ID = -1898481791
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) CONF_XAUTH
4d05h: ISAKMP (0:3): deleting node -1898481791 error FALSE reason "done with
xauth request/reply exchange"
4d05h: ISAKMP (0:3): Input = IKE_MESG_INTERNAL, IKE_XAUTH_REPLY_ATTR
Old State = IKE_XAUTH_REPLY_AWAIT New State = IKE_XAUTH_REPLY_SENT
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) CONF_XAUTH
4d05h: ISAKMP: set new node -1602220489 to CONF_XAUTH
4d05h: ISAKMP (0:3): processing transaction payload from 172.16.172.41. message ID = -1602220489
4d05h: ISAKMP: Config payload SET
4d05h: ISAKMP (0:3): Xauth process set, status = 1
4d05h: ISAKMP (0:3): checking SET:
4d05h: ISAKMP: XAUTH_STATUS_V2 XAUTH-OK
4d05h: ISAKMP (0:3): attributes sent in message:
4d05h: Status: 1
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) CONF_XAUTH
4d05h: ISAKMP (0:3): deleting node -1602220489 error FALSE reason ""
4d05h: ISAKMP (0:3): Input = IKE_MESG_FROM_PEER, IKE_CFG_SET
Old State = IKE_XAUTH_REPLY_SENT New State = IKE_P1_COMPLETE
4d05h: EZVPN(SJVPN): Current State: XAUTH_REPLIED
4d05h: EZVPN(SJVPN): Event: XAUTH_STATUS
4d05h: EZVPN(SJVPN): New State: READY
4d05h: ISAKMP (0:3): Need config/address
4d05h: ISAKMP (0:3): Need config/address
4d05h: ISAKMP: set new node 486952690 to CONF_ADDR
4d05h: ISAKMP (0:3): initiating peer config to 172.16.172.41. ID = 486952690
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) CONF_ADDR
4d05h: ISAKMP (0:3): Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Old State = IKE_P1_COMPLETE New State = IKE_CONFIG_MODE_REQ_SENT
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) CONF_ADDR
4d05h: ISAKMP (0:3): processing transaction payload from 172.16.172.41.
message ID = 486952690
4d05h: ISAKMP: Config payload REPLY
4d05h: ISAKMP(0:3) process config reply
4d05h: ISAKMP (0:3): deleting node 486952690 error FALSE reason
"done with transaction"
4d05h: ISAKMP (0:3): Input = IKE_MESG_FROM_PEER, IKE_CFG_REPLY
Old State = IKE_CONFIG_MODE_REQ_SENT New State = IKE_P1_COMPLETE
4d05h: EZVPN(SJVPN): Current State: READY
4d05h: EZVPN(SJVPN): Event: MODE_CONFIG_REPLY
4d05h: EZVPN(SJVPN): ezvpn_mode_config
4d05h: EZVPN(SJVPN): ezvpn_parse_mode_config_msg
4d05h: EZVPN: Attributes sent in message
4d05h: ip_ifnat_modified: old_if 0, new_if 2
4d05h: ip_ifnat_modified: old_if 0, new_if 2
4d05h: ip_ifnat_modified: old_if 1, new_if 2
4d05h: EZVPN(SJVPN): New State: SS_OPEN
4d05h: ISAKMP (0:3): Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-sha-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0xE6DB9372(3873149810), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0x3C77C53D(1014482237), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-sha-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0x79BB8DF4(2042334708), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-md5-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0x19C3A5B2(432252338), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: ISAKMP: received ke message (1/4)
4d05h: ISAKMP: set new node 0 to QM_IDLE
4d05h: EZVPN(SJVPN): Current State: SS_OPEN
4d05h: EZVPN(SJVPN): Event: SOCKET_READY
4d05h: EZVPN(SJVPN): No state change
4d05h: ISAKMP (0:3): sitting IDLE. Starting QM immediately (QM_IDLE )
4d05h: ISAKMP (0:3): beginning Quick Mode exchange, M-ID of -1494477527
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-sha-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0xB18CF11E(2978803998), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0xA8C469EC(2831444460), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-sha-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0xBC5AD5EE(3160069614), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-md5-hmac ,
lifedur= 2147483s and 4608000kb,
spi= 0x8C34C692(2352268946), conn_id= 0, keysize= 0, flags= 0x400C
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP (0:3): Node -1494477527, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
Old State = IKE_QM_READY New State = IKE_QM_I_QM1
4d05h: ISAKMP: received ke message (1/4)
4d05h: ISAKMP: set new node 0 to QM_IDLE
4d05h: ISAKMP (0:3): sitting IDLE. Starting QM immediately (QM_IDLE )
4d05h: ISAKMP (0:3): beginning Quick Mode exchange, M-ID of -1102788797
4d05h: EZVPN(SJVPN): Current State: SS_OPEN
4d05h: EZVPN(SJVPN): Event: SOCKET_READY
4d05h: EZVPN(SJVPN): No state change
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP (0:3): Node -1102788797, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
Old State = IKE_QM_READY New State = IKE_QM_I_QM1
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP: set new node 733055375 to QM_IDLE
4d05h: ISAKMP (0:3): processing HASH payload. message ID = 733055375
4d05h: ISAKMP (0:3): processing NOTIFY RESPONDER_LIFETIME protocol 1
spi 0, message ID = 733055375, sa = 820ABFA0
4d05h: ISAKMP (0:3): processing responder lifetime
4d05h: ISAKMP (0:3): start processing isakmp responder lifetime
4d05h: ISAKMP (0:3): restart ike sa timer to 86400 secs
4d05h: ISAKMP (0:3): deleting node 733055375 error FALSE reason
"informational (in) state 1"
4d05h: ISAKMP (0:3): Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP (0:3): processing HASH payload. message ID = -1494477527
4d05h: ISAKMP (0:3): processing SA payload. message ID = -1494477527
4d05h: ISAKMP (0:3): Checking IPSec proposal 1
4d05h: ISAKMP: transform 1, ESP_3DES
4d05h: ISAKMP: attributes in transform:
4d05h: ISAKMP: SA life type in seconds
4d05h: ISAKMP: SA life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP: SA life type in kilobytes
4d05h: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
4d05h: ISAKMP: encaps is 1
4d05h: ISAKMP: authenticator is HMAC-MD5
4d05h: ISAKMP (0:3): atts are acceptable.
4d05h: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x4
4d05h: ISAKMP (0:3): processing NONCE payload. message ID = -1494477527
4d05h: ISAKMP (0:3): processing ID payload. message ID = -1494477527
4d05h: ISAKMP (0:3): processing ID payload. message ID = -1494477527
4d05h: ISAKMP (0:3): processing NOTIFY RESPONDER_LIFETIME protocol 3
spi 1344958901, message ID = -1494477527, sa = 820ABFA0
4d05h: ISAKMP (0:3): processing responder lifetime
4d05h: ISAKMP (3): responder lifetime of 28800s
4d05h: ISAKMP (3): responder lifetime of 0kb
4d05h: ISAKMP (0:3): Creating IPSec SAs
4d05h: inbound SA from 172.16.172.41 to 172.16.172.46
(proxy 0.0.0.0 to 192.168.254.0)
4d05h: has spi 0x3C77C53D and conn_id 2000 and flags 4
4d05h: lifetime of 28800 seconds
4d05h: outbound SA from 172.16.172.46 to 172.16.172.41
(proxy 192.168.254.0 to 0.0.0.0 )
4d05h: has spi 1344958901 and conn_id 2001 and flags C
4d05h: lifetime of 28800 seconds
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP (0:3): deleting node -1494477527 error FALSE reason ""
4d05h: ISAKMP (0:3): Node -1494477527, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Old State = IKE_QM_I_QM1 New State = IKE_QM_PHASE2_COMPLETE
4d05h: ISAKMP (0:3): received packet from 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP (0:3): processing HASH payload. message ID = -1102788797
4d05h: ISAKMP (0:3): processing SA payload. message ID = -1102788797
4d05h: ISAKMP (0:3): Checking IPSec proposal 1
4d05h: ISAKMP: transform 1, ESP_3DES
4d05h: ISAKMP: attributes in transform:
4d05h: ISAKMP: SA life type in seconds
4d05h: ISAKMP: SA life duration (VPI) of 0x0 0x20 0xC4 0x9B
4d05h: ISAKMP: SA life type in kilobytes
4d05h: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
4d05h: ISAKMP: encaps is 1
4d05h: ISAKMP: authenticator is HMAC-MD5
4d05h: ISAKMP (0:3): atts are acceptable.
4d05h: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x4
4d05h: ISAKMP (0:3): processing NONCE payload. message ID = -1102788797
4d05h: ISAKMP (0:3): processing ID payload. message ID = -1102788797
4d05h: ISAKMP (0:3): processing ID payload. message ID = -1102788797
4d05h: ISAKMP (0:3): processing NOTIFY RESPONDER_LIFETIME protocol 3
spi 653862918, message ID = -1102788797, sa = 820ABFA0
4d05h: ISAKMP (0:3): processing responder lifetime
4d05h: ISAKMP (3): responder lifetime of 28800s
4d05h: ISAKMP (3): responder lifetime of 0kb
4d05h: IPSEC(key_engine): got a queue event...
4d05h: IPSEC(initialize_sas): ,
(key eng. msg.) INBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 28800s and 0kb,
spi= 0x3C77C53D(1014482237), conn_id= 2000, keysize= 0, flags= 0x4
4d05h: IPSEC(initialize_sas): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.254.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 28800s and 0kb,
spi= 0x502A71B5(1344958901), conn_id= 2001, keysize= 0, flags= 0xC
4d05h: IPSEC(create_sa): sa created,
(sa) sa_dest= 172.16.172.46, sa_prot= 50,
sa_spi= 0x3C77C53D(1014482237),
!--- SPI that is used on inbound SA.
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2000
4d05h: IPSEC(create_sa): sa created,
(sa) sa_dest= 172.16.172.41, sa_prot= 50,
sa_spi= 0x502A71B5(1344958901),
!--- SPI that is used on outbound SA.
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2001
4d05h: ISAKMP (0:3): Creating IPSec SAs
4d05h: inbound SA from 172.16.172.41 to 172.16.172.46
(proxy 0.0.0.0 to 192.168.253.0)
4d05h: has spi 0xA8C469EC and conn_id 2002 and flags 4
4d05h: lifetime of 28800 seconds
4d05h: outbound SA from 172.16.172.46 to 172.16.172.41
(proxy 192.168.253.0 to 0.0.0.0 )
4d05h: has spi 653862918 and conn_id 2003 and flags C
4d05h: lifetime of 28800 seconds
4d05h: ISAKMP (0:3): sending packet to 172.16.172.41 (I) QM_IDLE
4d05h: ISAKMP (0:3): deleting node -1102788797 error FALSE reason ""
4d05h: ISAKMP (0:3): Node -1102788797, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Old State = IKE_QM_I_QM1 New State = IKE_QM_PHASE2_COMPLETE
4d05h: ISAKMP: received ke message (4/1)
4d05h: ISAKMP: Locking CONFIG struct 0x81F433A4 for
crypto_ikmp_config_handle_kei_mess, count 3
4d05h: EZVPN(SJVPN): Current State: SS_OPEN
4d05h: EZVPN(SJVPN): Event: MTU_CHANGED
4d05h: EZVPN(SJVPN): No state change
4d05h: IPSEC(key_engine): got a queue event...
4d05h: IPSEC(initialize_sas): ,
(key eng. msg.) INBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 28800s and 0kb,
spi= 0xA8C469EC(2831444460), conn_id= 2002, keysize= 0, flags= 0x4
4d05h: IPSEC(initialize_sas): ,
(key eng. msg.) OUTBOUND local= 172.16.172.46, remote= 172.16.172.41,
local_proxy= 192.168.253.0/255.255.255.0/0/0 (type=4),
remote_proxy= 0.0.0.0/0.0.0.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-md5-hmac ,
lifedur= 28800s and 0kb,
spi= 0x26F92806(653862918), conn_id= 2003, keysize= 0, flags= 0xC
4d05h: IPSEC(create_sa): sa created,
(sa) sa_dest= 172.16.172.46, sa_prot= 50,
sa_spi= 0xA8C469EC(2831444460),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2002
4d05h: IPSEC(create_sa): sa created,
(sa) sa_dest= 172.16.172.41, sa_prot= 50,
sa_spi= 0x26F92806(653862918),
sa_trans= esp-3des esp-md5-hmac , sa_conn_id= 2003
4d05h: ISAKMP: received ke message (4/1)
4d05h: ISAKMP: Locking CONFIG struct 0x81F433A4 for
crypto_ikmp_config_handle_kei_mess, count 4
4d05h: EZVPN(SJVPN): Current State: SS_OPEN
4d05h: EZVPN(SJVPN): Event: SOCKET_UP
4d05h: ezvpn_socket_up
4d05h: EZVPN(SJVPN): New State: IPSEC_ACTIVE
4d05h: EZVPN(SJVPN): Current State: IPSEC_ACTIVE
4d05h: EZVPN(SJVPN): Event: MTU_CHANGED
4d05h: EZVPN(SJVPN): No state change
4d05h: EZVPN(SJVPN): Current State: IPSEC_ACTIVE
4d05h: EZVPN(SJVPN): Event: SOCKET_UP
4d05h: ezvpn_socket_up
4d05h: EZVPN(SJVPN): No state change
用於故障排除的相關思科IOS show命令
1721-1(ADSL)#show crypto ipsec client ezvpn
Tunnel name : SJVPN
Inside interface list: Loopback0, Loopback1,
Outside interface: FastEthernet0
Current State: IPSEC_ACTIVE
Last Event: SOCKET_UP
1721-1(ADSL)#show crypto isakmp sa
dst src state conn-id slot
172.16.172.41 172.16.172.46 QM_IDLE 3 0
1721-1(ADSL)#show crypto ipsec sa
interface: FastEthernet0
Crypto map tag: FastEthernet0-head-0, local addr. 172.16.172.46
local ident (addr/mask/prot/port): (192.168.253.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 172.16.172.41
PERMIT, flags={origin_is_acl,}
#pkts encaps: 100, #pkts encrypt: 100, #pkts digest 100
#pkts decaps: 100, #pkts decrypt: 100, #pkts verify 100
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.172.46, remote crypto endpt.: 172.16.172.41
path mtu 1500, media mtu 1500
current outbound spi: 26F92806
inbound esp sas:
spi: 0xA8C469EC(2831444460)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2002, flow_id: 3, crypto map: FastEthernet0-head-0
sa timing: remaining key lifetime (k/sec): (4607848/28656)
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x26F92806(653862918)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2003, flow_id: 4, crypto map: FastEthernet0-head-0
sa timing: remaining key lifetime (k/sec): (4607848/28647)
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
outbound pcp sas:
local ident (addr/mask/prot/port): (192.168.254.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 172.16.172.41
PERMIT, flags={origin_is_acl,}
#pkts encaps: 105, #pkts encrypt: 105, #pkts digest 105
#pkts decaps: 105, #pkts decrypt: 105, #pkts verify 105
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.172.46, remote crypto endpt.: 172.16.172.41
path mtu 1500, media mtu 1500
current outbound spi: 502A71B5
inbound esp sas:
spi: 0x3C77C53D(1014482237)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2000, flow_id: 1, crypto map: FastEthernet0-head-0
sa timing: remaining key lifetime (k/sec): (4607847/28644)
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x502A71B5(1344958901)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2001, flow_id: 2, crypto map: FastEthernet0-head-0
sa timing: remaining key lifetime (k/sec): (4607847/28644)
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
outbound pcp sas:
清除作用中通道
您可以使用以下指令清除通道:
-
clear crypto isakmp
-
clear crypto sa
-
clear crypto ipsec client ezvpn
注意:在選擇Administration > Admin Sessions時,可以使用VPN Concentrator註銷會話,在Remote Access Session中選擇使用者,然後單擊logout。
VPN 3000集中器調試
選擇Configuration > System > Events > Classes,以在發生事件連線失敗時啟用此調試。如果顯示的類不能幫助您識別問題,則您始終可以新增更多類。
要檢視記憶體中的當前事件日誌(可按事件類、嚴重性、IP地址等進行過濾),請選擇Monitoring > Filterable Event log。
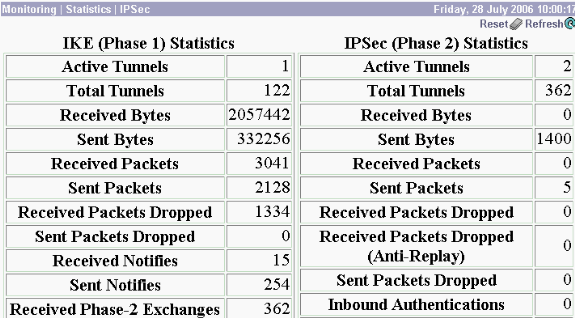
要檢視IPsec協定的統計資訊,請選擇Monitoring > Statistics > IPSec。 此視窗顯示自上次引導或重置以來VPN集中器上的IPsec活動的統計資訊,包括當前IPsec隧道。這些統計資訊符合IPsec流量監控MIB的IETF草案。Monitoring > Sessions > Detail視窗也顯示IPsec資料。
可能出錯的地方
-
Cisco IOS路由器停滯在AG_INIT_EXCH狀態。進行故障排除時,請使用以下命令開啟IPsec和ISAKMP調試:
-
debug crypto ipsec
-
debug crypto isakmp
-
debug crypto ezvpn
在Cisco IOS路由器上,您會看到:
5d16h: ISAKMP (0:9): beginning Aggressive Mode exchange 5d16h: ISAKMP (0:9): sending packet to 10.48.66.115 (I) AG_INIT_EXCH 5d16h: ISAKMP (0:9): retransmitting phase 1 AG_INIT_EXCH... 5d16h: ISAKMP (0:9): incrementing error counter on sa: retransmit phase 1 5d16h: ISAKMP (0:9): retransmitting phase 1 AG_INIT_EXCH 5d16h: ISAKMP (0:9): sending packet to 10.48.66.115 (I) AG_INIT_EXCH 5d16h: ISAKMP (0:9): retransmitting phase 1 AG_INIT_EXCH... 5d16h: ISAKMP (0:9): incrementing error counter on sa: retransmit phase 1 5d16h: ISAKMP (0:9): retransmitting phase 1 AG_INIT_EXCH 5d16h: ISAKMP (0:9): sending packet to 10.48.66.115 (I) AG_INIT_EXCH 5d16h: ISAKMP (0:9): retransmitting phase 1 AG_INIT_EXCH... 5d16h: ISAKMP (0:9): incrementing error counter on sa: retransmit phase 1 5d16h: ISAKMP (0:9): retransmitting phase 1 AG_INIT_EXCH 5d16h: ISAKMP (0:9): sending packet to 10.48.66.115 (I) AG_INIT_EXCH
在VPN 3000 Concentrator上需要Xauth。但是,所選建議不支援Xauth。驗證是否指定了Xauth的內部驗證。啟用內部身份驗證,並確保IKE建議的身份驗證模式設定為預共用金鑰(Xauth),如前面的螢幕截圖所示。按一下Modify以編輯建議。
-
-
密碼不正確。
在Cisco IOS路由器上未看到Invalid Password消息。在VPN集中器上,您可能會看到Received unexpected event EV_ACTIVATE_NEW_SA in state AM_TM_INIT_XAUTH。
確保您的密碼正確。
-
使用者名稱不正確。
如果您有錯誤的密碼,在Cisco IOS路由器上,您會看到類似以下的調試。在VPN集中器上,您會看到Authentication rejected:原因=未找到使用者。
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
12-Mar-2007 |
初始版本 |
 意見
意見