简介
本文档介绍IKEv2加密映射备份对等体在思科安全防火墙设备上的链路故障转移期间提供的功能。
先决条件
·自适应安全设备9.14(1)版或更高版本
·防火墙威胁防御6.6版或更高版本
· Firewall Management Center 6.6或更高版本
·防火墙设备管理器6.6 - 7.0版(通过API)或7.1+(通过GUI)
要求
Cisco 建议您了解以下主题:
·对IKEv2站点到站点加密映射的基本了解
· VPN终端之间的基本底层连接
·基本了解IP服务级别协议功能
使用的组件
本文档中的信息基于以下软件版本和硬件版本:
·两个Cisco ASAv设备版本9.16(2)
·三台Cisco IOS®路由器,版本15.9(3)M4
·两个Ubuntu主机版本20.04
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
理论
IKEv2多对等体拓扑的Responder端不支持IKEv2对等体穿越。例如,拓扑中有两个VPN端点,分别称为对等体1和对等体2。对等2有两个ISP接口,对等1有1个ISP接口。在ISP发生故障切换时,如果配置到位以监控路径,对等体2会在辅助ISP接口上启动IKE。对等体1不会自动遍历IP地址以使用为加密映射列出的备份对等体来容纳对等体2的ISP故障切换。连接失败,直到流量从对等体1发起。一旦对等体1根据加密ACL启动流量,它将尝试通过主ISP路径通信,直到路径被重新传输声明为失效为止。此过程大约需要2分钟。一旦主对等体声明为非活动状态,对等体1启动与列出的备用对等体的连接,然后建立连接。当主ISP路径再次可用且对等体2切换到主ISP接口后,对等体1需要生成相关流量。此过程允许对等体1启动与加密映射中列出的主要对等体的连接,并正常建立IKE连接。
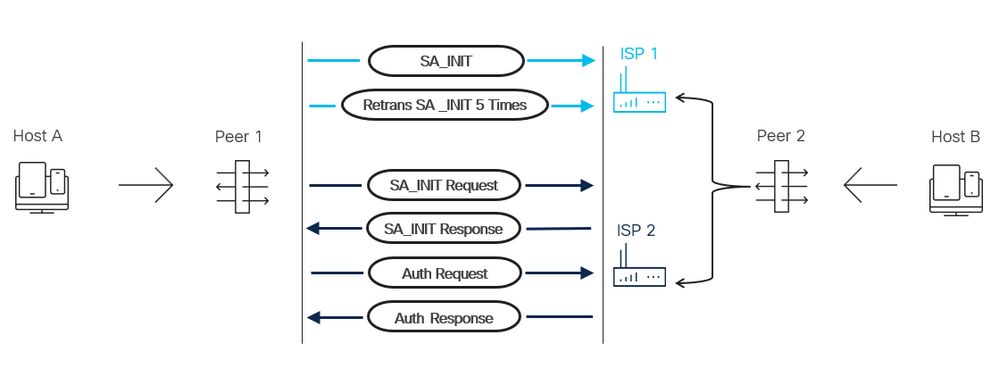
操作顺序
1. VPN对等2 SLA检测路径故障。
2. VPN对等体2具有路由表更新,以更改用于到达VPN对等体1的路径,VPN对等体1会更改其IKE身份。
3.主机A不断发起发往主机B的流量。
4. VPN对等体1尝试与VPN对等体2的主要ISP接口建立IKE连接,直到发生5次重新传输。
5.然后,VPN对等体1声明对等体失效,并移至加密映射(即VPN对等体2的辅助ISP接口)中的辅助对等体。此连接成功建立。
网络图
配置示例
VPN对等体2
Interfaces:
interface GigabitEthernet0/0
nameif PRIMARY-ISP
security-level 0
ip address 203.0.113.1 255.255.255.0
interface GigabitEthernet0/1
nameif BACKUP-ISP
security-level 0
ip address 198.51.100.1 255.255.255.0
interface GigabitEthernet0/2
nameif inside
security-level 100
ip address 192.168.10.2 255.255.255.00
SLA和路由:
sla monitor 500
type echo protocol ipIcmpEcho 209.165.200.226 interface PRIMARY-ISP
num-packets 3
frequency 5
sla monitor schedule 500 life forever start-time now
track 1 rtr 500 reachability
route PRIMARY-ISP 0.0.0.0 0.0.0.0 203.0.113.2 1 track 1
route BACKUP-ISP 0.0.0.0 0.0.0.0 198.51.100.2 254
加密:
crypto ikev2 policy 1
encryption aes-256
integrity sha256
group 21
prf sha256
lifetime seconds 86400
crypto ikev2 enable PRIMARY-ISP
crypto ikev2 enable BACKUP-ISP
crypto ipsec ikev2 ipsec-proposal PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto map MAP 1 match address CRYPTO
crypto map MAP 1 set peer 192.0.2.1
crypto map MAP 1 set ikev2 ipsec-proposal PROPOSAL
crypto map MAP interface PRIMARY-ISP
crypto map MAP interface BACKUP-ISP
隧道组:
tunnel-group 192.0.2.1 type ipsec-l2l
tunnel-group 192.0.2.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
访问列表:
access-list CRYPTO line 1 extended permit ip 192.168.10.0 255.255.255.0 10.10.10.0 255.255.255.0
VPN对等点1
Interfaces:
interface GigabitEthernet0/0
nameif OUTSIDE
security-level 0
ip address 192.0.2.1 255.255.255.0
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 10.10.10.2 255.255.255.0
路由:
route OUTSIDE 0.0.0.0 0.0.0.0 192.0.2.2
加密:
crypto ikev2 policy 1
encryption aes-256
integrity sha256
group 21
prf sha256
lifetime seconds 86400
crypto ikev2 enable OUTSIDE
crypto ipsec ikev2 ipsec-proposal PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto map MAP-2 1 match address CRYPTO-2
crypto map MAP-2 1 set peer 203.0.113.1 198.51.100.1
crypto map MAP-2 1 set ikev2 ipsec-proposal PROPOSAL
crypto map MAP-2 interface OUTSIDE
隧道组:
tunnel-group 203.0.113.1 type ipsec-l2l
tunnel-group 203.0.113.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
tunnel-group 198.51.100.1 type ipsec-l2l
tunnel-group 198.51.100.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
访问列表:
access-list CRYPTO-2 line 1 extended permit ip 10.10.10.0 255.255.255.0 192.168.10.0 255.255.255.0
主ISP
接口:
GigabitEthernet0/0 203.0.113.2 255.255.255.0
GigabitEthernet0/1 209.165.200.225 255.255.255.224
备份ISP
接口:
GigabitEthernet0/0 198.51.100.2 255.255.255.0
GigabitEthernet0/1 209.165.202.130 255.255.255.224
ISP
接口:
GigabitEthernet0/0 209.165.202.129 255.255.255.224
GigabitEthernet0/1 209.165.200.226 255.255.255.224
主机
主机2:
192.168.10.1 255.255.255.0 dev ens2
主机1:
10.10.10.1 255.255.255.0 dev ens2
配置目标
在本实验中,VPN对等体2查询主ISP的G0/1接口的可达性。此查询通过SLA监控使用ICMP完成。SLA配置绑定到路径,然后该路径又绑定到主ISP路由。如果此路由由于SLA可达性故障而变得不可用,则备用ISP路由会自动变为活动状态。这意味着现在从IP地址为198.51.100.1的BACKUP-ISP接口发起来自VPN对等体2的IKE协商。在VPN对等体1端,地址198.51.100.1在加密映射中列为辅助对等体。VPN对等体1需要发起到加密映射中主对等体的加密ACL流量。然后,在使用加密映射中的辅助对等体之前,通过重新传输声明对等体处于非活动状态。
验证
使用此部分可确认配置功能符合预期
在SLA检测到故障之前:
VPN-PEER-2# show track
Track 1
Response Time Reporter 500 reachability
Reachability is Up
12 changes, last change 05:51:34
Latest operation return code: OK
Latest RTT (millisecs) 7
Tracked by:
STATIC-IP-ROUTING 0
VPN-PEER-2# show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF
Gateway of last resort is 203.0.113.2 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 203.0.113.2, PRIMARY-ISP
C 192.168.10.0 255.255.255.0 is directly connected, inside
L 192.168.10.2 255.255.255.255 is directly connected, inside
C 198.51.100.0 255.255.255.0 is directly connected, BACKUP-ISP
L 198.51.100.1 255.255.255.255 is directly connected, BACKUP-ISP
C 203.0.113.0 255.255.255.0 is directly connected, PRIMARY-ISP
L 203.0.113.1 255.255.255.255 is directly connected, PRIMARY-ISP
VPN-PEER-2# show crypto ikev2 sa
IKEv2 SAs:
Session-id:75, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
160993547 203.0.113.1/500 192.0.2.1/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/21202 sec
Child sa: local selector 192.168.10.0/0 - 192.168.10.255/65535
remote selector 10.10.10.0/0 - 10.10.10.255/65535
ESP spi in/out: 0x30138366/0x7405d4a0
VPN-PEER-1# show crypto ikev2 sa
IKEv2 SAs:
Session-id:75, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
168559091 192.0.2.1/500 203.0.113.1/500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/21386 sec
Child sa: local selector 10.10.10.0/0 - 10.10.10.255/65535
remote selector 192.168.10.0/0 - 192.168.10.255/65535
ESP spi in/out: 0x7405d4a0/0x30138366
在SLA检测到故障后:
VPN-PEER-2# show track 1
Track 1
Response Time Reporter 500 reachability
Reachability is Down
13 changes, last change 00:05:23
Latest operation return code: Timeout
Tracked by:
STATIC-IP-ROUTING 0
VPN-PEER-2# show route
S* 0.0.0.0 0.0.0.0 [254/0] via 198.51.100.2, BACKUP-ISP
VPN-PEER-2# show crypto ikev2 sa
There are no IKEv2 SAs

注意:IKE将保持关闭状态,直到主机A启动发往主机B的流量。然后,VPN对等体1会声明加密映射中的主对等体失效,并移至备份对等体IP地址。
VPN-PEER-1# show crypto ikev2 sa
IKEv2 SAs:
Session-id:79, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
178593183 192.0.2.1/500 198.51.100.1/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/232 sec
Child sa: local selector 10.10.10.0/0 - 10.10.10.255/65535
remote selector 192.168.10.0/0 - 192.168.10.255/65535
ESP spi in/out: 0x695d6bf0/0xbefc13c

注意:VPN对等体1声明加密映射中的主对等体失效,并启动与备用对等体IP地址的连接。
故障排除
Debug crypto ikev2 platform 255
Debug crypto ikev2 protocol 255
Debug crypto ispec 255
Debug sla monitor error #
Debug sla monitor trace



 反馈
反馈