Configurar el portal de patrocinadores de ISE 3.0 con Azure AD SAML SSO
Opciones de descarga
-
ePub (2.9 MB)
Visualice en diferentes aplicaciones en iPhone, iPad, Android, Sony Reader o Windows Phone -
Mobi (Kindle) (2.7 MB)
Visualice en dispositivo Kindle o aplicación Kindle en múltiples dispositivos
Lenguaje no discriminatorio
El conjunto de documentos para este producto aspira al uso de un lenguaje no discriminatorio. A los fines de esta documentación, "no discriminatorio" se refiere al lenguaje que no implica discriminación por motivos de edad, discapacidad, género, identidad de raza, identidad étnica, orientación sexual, nivel socioeconómico e interseccionalidad. Puede haber excepciones en la documentación debido al lenguaje que se encuentra ya en las interfaces de usuario del software del producto, el lenguaje utilizado en función de la documentación de la RFP o el lenguaje utilizado por un producto de terceros al que se hace referencia. Obtenga más información sobre cómo Cisco utiliza el lenguaje inclusivo.
Acerca de esta traducción
Cisco ha traducido este documento combinando la traducción automática y los recursos humanos a fin de ofrecer a nuestros usuarios en todo el mundo contenido en su propio idioma. Tenga en cuenta que incluso la mejor traducción automática podría no ser tan precisa como la proporcionada por un traductor profesional. Cisco Systems, Inc. no asume ninguna responsabilidad por la precisión de estas traducciones y recomienda remitirse siempre al documento original escrito en inglés (insertar vínculo URL).
Contenido
Introducción
Este documento describe cómo configurar un servidor SAML de Azure Active Directory (AD) con Cisco Identity Services Engine (ISE) 3.0 para proporcionar funciones de inicio de sesión único (SSO) para usuarios patrocinadores.
Prerequisites
Requirements
Cisco recomienda que tenga conocimiento sobre estos temas:
- Cisco ISE 3.0
- Conocimientos básicos sobre implementaciones de SAML SSO
- Azure AD
Componentes Utilizados
- Cisco ISE 3.0
- Azure AD
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. Si tiene una red en vivo, asegúrese de entender el posible impacto de cualquier comando.
Diagrama de flujo de alto nivel
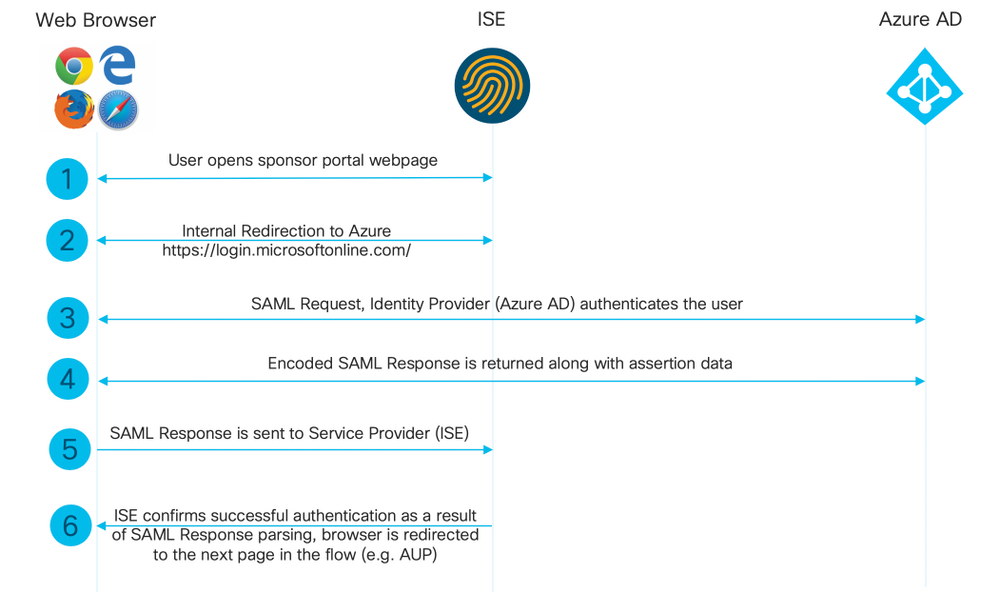
Configurar
Paso 1. Configuración de SAML Identity Provider y Sponsor Portal en ISE
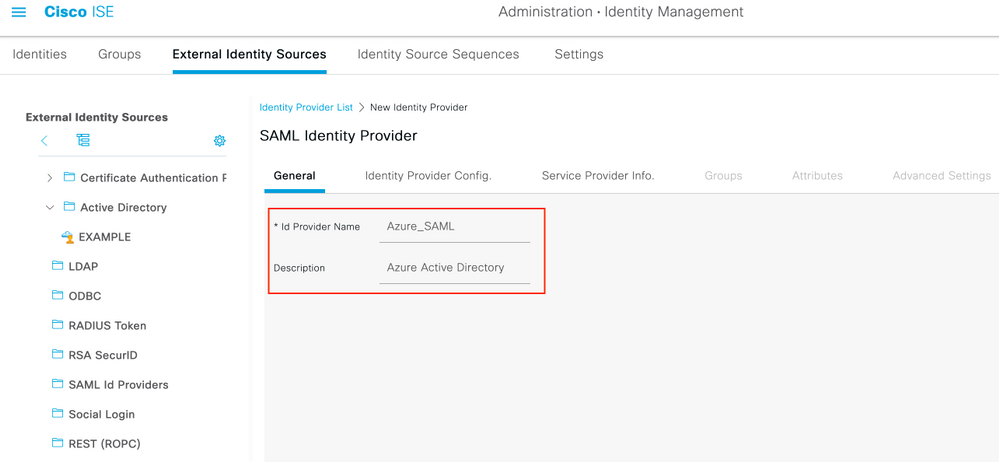
1. Configurar Azure AD como origen de identidad SAML externo
En ISE, navegue hasta Administration > Identity Management > External Identity Sources > SAML Id Providers y haga clic en el botón Add.
Ingrese el Id Provider Name y haga clic en Submit para guardarlo. El Id Provider Name es significativo sólo para ISE, como se muestra en la imagen.
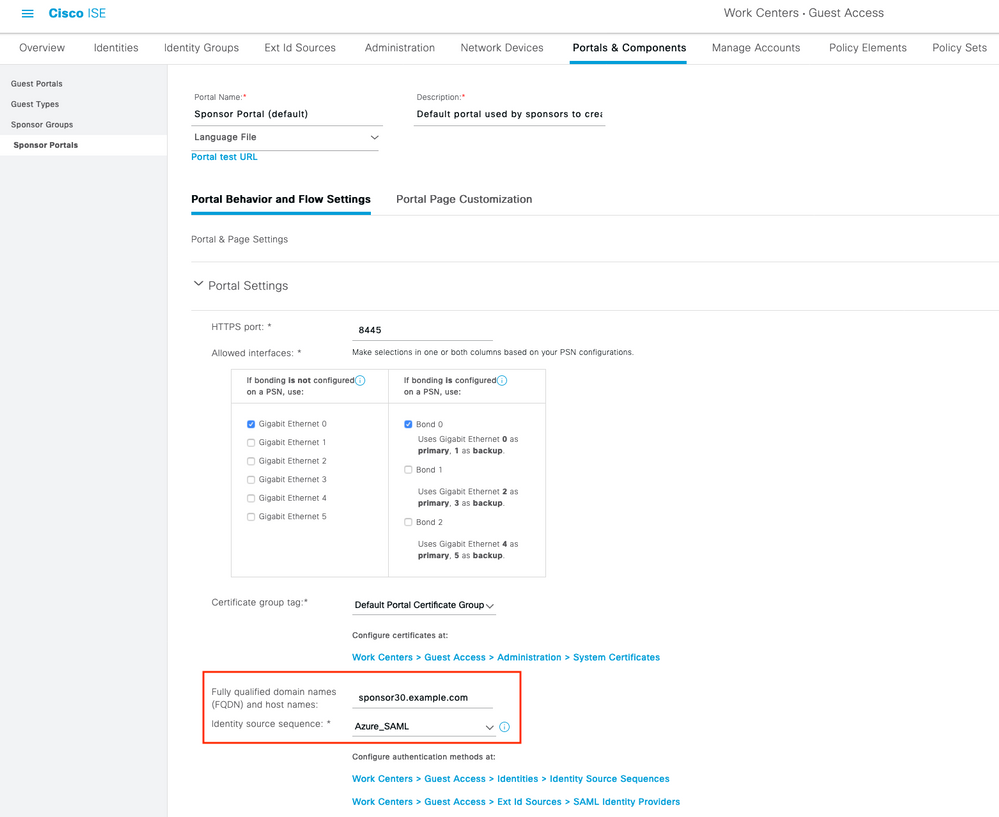
2. Configurar el portal de patrocinadores para utilizar Azure AD
Navegue hasta Centros de trabajo > Acceso de invitado > Portales y componentes > Portales patrocinadores y seleccione su Portal patrocinador. En este ejemplo se utiliza Portal del patrocinador (predeterminado).
Expanda el panel Configuración del portal y seleccione su nuevo IDP de SAML en la secuencia de origen de la identidad. Configure el nombre de dominio completamente calificado (FQDN) para el portal del patrocinador. En este ejemplo es auspiciador30.ejemplo.com. Haga clic en Guardar como se muestra en la imagen.
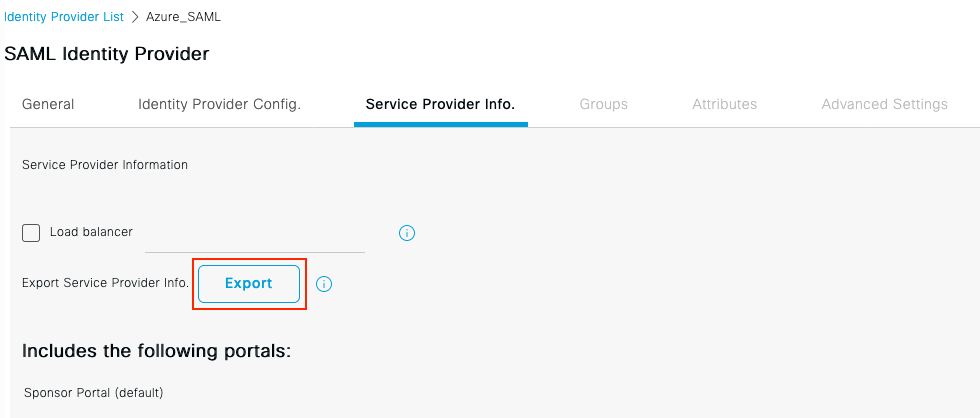
3. Exportar información del proveedor de servicios
Vaya a Administration > Identity Management > External Identity Sources > SAML Id Providers > [Your SAML Provider].
Cambie a la pestaña Información del proveedor de servicios. y haga clic en el botón Exportar como se muestra en la imagen.
Descargue el archivo zip y guárdelo. En él, puede encontrar 2 archivos. Necesita el archivo XML denominado Portal patrocinador.
Tome nota de ResponseLocation de SingleLogoutService Bindings, valor de IdDeEntidad y valores de Ubicación de AssertionConsumerService Binding.
<?xml version="1.0" encoding="UTF-8"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429">
<md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>
MIIFZjCCA06gAwIBAgIQX1oAvwAAAAChgVd9cEEWOzANBgkqhkiG9w0BAQwFADAlMSMwIQYDVQQD
ExpTQU1MX0lTRTMwLTFlay5leGFtcGxlLmNvbTAeFw0yMDA5MTAxMDMyMzFaFw0yNTA5MDkxMDMy
MzFaMCUxIzAhBgNVBAMTGlNBTUxfSVNFMzAtMWVrLmV4YW1wbGUuY29tMIICIjANBgkqhkiG9w0B
AQEFAAOCAg8AMIICCgKCAgEAt+MixKfuZvg/oAWGEs6zrUYL3H2JwvZw9yJs6sJ8/BpP6Sw027wh
FXnESXpqmmoSVrVEcQIrDdk3l8UYNn/+98PPkIi/4ftyFjZK9YdeverD6nrA2MeoLCzGlkWq/y4i
vvVcYuW344pySm65awVvro3q84x9esHqyLahExs9guiLJryD497XmNP4Z8eTHCctu777PuI1wLO4
QOYUs2sozXvR98D9Jok/+PjH3bjmVKapqAcNEFvk8Ez9x1sMBUgFwP4YdZzQB9IRVkQdIJGvqMyf
a6gn+KaddJnmIbXKFbrTaFii2IvRs3qHJ0mMVfYRnYeMql9/PhzvSFtjRe32x/aQh23j9dCsVXmQ
ZmXpZyxxJ8p4RqyM0YgkfxnQXXtV9K0sRZPFn6O+iszUw2hARRG/tE0hTuVXpbonG2dT109JeeEe
S1E5uxenJvYkU7mMamvBjYQN6qVyyogf8FOlHTSfd6TDsK3QhmzOjg50PrBvvg5qE6OrxxNvqSVZ
1dhx/iHZAZ1yYSVdwizsZMCw0PjSwrRPx/h8l03djeW0aL5R1AF1qTFHVHSNvigzh6FyjdkUJH66
JAygPe0PKJFRgYzh5vWoJ41qvdQjlGk3c/zYi57MR1Bs0mkSvkOGbmjSsb+EehnYyLLB8FG3De2V
ZaXaHZ37gmoCNNmZHrn+GB0CAwEAAaOBkTCBjjAgBgNVHREEGTAXghVJU0UzMC0xZWsuZXhhbXBs
ZS5jb20wDAYDVR0TBAUwAwEB/zALBgNVHQ8EBAMCAuwwHQYDVR0OBBYEFPT/6jpfyugxRolbjzWJ
858WfTP1MB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjARBglghkgBhvhCAQEEBAMCBkAw
DQYJKoZIhvcNAQEMBQADggIBABGyWZbLajM2LyLASg//4N6mL+xu/9IMdVvNWBQodF+j0WusW15a
VPSQU2t3Ckd/I1anvpK+cp77NMjo9V9oWI3/ZnjZHGoFAIcHnlGCoEjmC1TvLau7ZzhCCII37DFA
yMKDrXLi3pR+ONlXlTIvjpHTTzrKm1NHhkxkx/Js5Iuz+MyRKP8FNmWT0q4XGejyKzJWrqEu+bc1
idCl/gBNuCHgqmFeM82IGQ7jVOm1kBjLb4pTDbYk4fMIbJVh4V2Pgi++6MIfXAYEwL+LHjSGHCQT
PSM3+kpv1wHHpGWzQSmcJ4tXVXV95W0NC+LxQZLBPNMUZorhuYCILXZxvXH1HGJJ0YKx9lk9Ubd2
s5JaD+GN8jqm5XXAau7S4BawfvCo3boOiXnSvgcIuH9YFiR2lp2n/2X0VVbdPHYZtqGieqBWebHr
4I1z18FXblYyMzpIkhtOOvkP5mAlR92VXBkvx2WPjtzQrvOtSXgvTCOKErYCBM/jnuwsztV7FVTV
JNdFwOsnXC70YngZeujZyjPoUbfRKZI34VKZp4iO5bZsGlbWE9Skdquv0PaQ8ecXTv8OCVBYUegl
vt0pdel8h/9jImdLG8dF0rbADGHiieTcntSDdw3E7JFmS/oHw7FsA5GI8IxXfcOWUx/L0Dx3jTNd
ZlAXp4juySODIx9yDyM4yV0f
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sponsor30.example.com:8445/sponsorportal/SSOLogoutRequest.action?portal=bd48c1a1-9477-4746-8e40-e43d20c9f429" ResponseLocation="https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action" index="0"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.48.23.86:8445/sponsorportal/SSOLoginResponse.action" index="1"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.48.26.63:8445/sponsorportal/SSOLoginResponse.action" index="2"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://10.48.26.60:8445/sponsorportal/SSOLoginResponse.action" index="3"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-1ek.example.com:8445/sponsorportal/SSOLoginResponse.action" index="4"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-2ek.example.com:8445/sponsorportal/SSOLoginResponse.action" index="5"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ise30-3ek.example.com:8445/sponsorportal/SSOLoginResponse.action" index="6"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>
Según el archivo XML:
SingleLogoutService ResponseLocation="https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action"
identityID="http://CiscoISE/100d02da-9457-41e8-87d7-0965b0714db2"
AssertionConsumerService Location="https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action"
AssertionConsumerService Location="https://10.48.23.86:8445/sponsorportal/SSOLoginResponse.action"
AssertionConsumerService Location="https://10.48.23.63:8445/sponsorportal/SSOLoginResponse.action"
AssertionConsumerService Location="https://10.48.26.60:8445/sponsorportal/SSOLoginResponse.action"
AssertionConsumerService Location="https://ise30-1ek.example.com:8445/sponsorportal/SSOLoginResponse.action"
AssertionConsumerService Location="https://ise30-2ek.example.com:8445/sponsorportal/SSOLoginResponse.action"
AssertionConsumerService Location="https://ise30-3ek.example.com:8445/sponsorportal/SSOLoginResponse.action"
Paso 2. Configuración de Azure AD IdP Settings
1. Crear un usuario de Azure AD
Inicie sesión en Azure Active Directory Admin Center Dashboard y seleccione su AD como se muestra en la imagen.
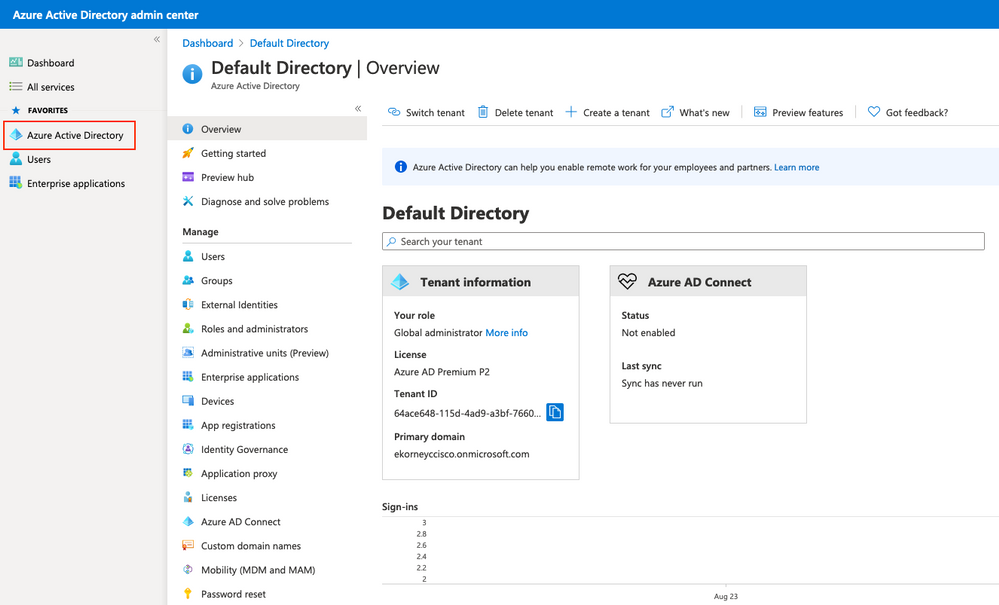
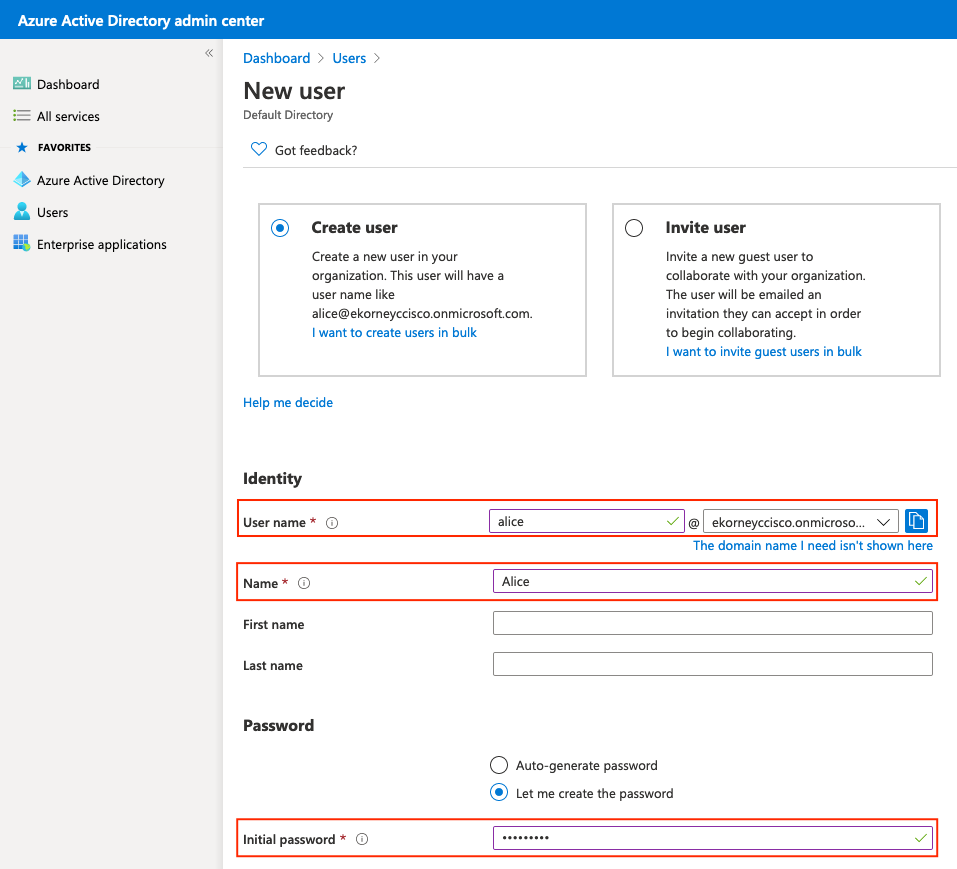
Seleccione Usuarios, haga clic en Nuevo usuario, configure Nombre de usuario, Nombre y Contraseña inicial. Haga clic en Crear como se muestra en la imagen.
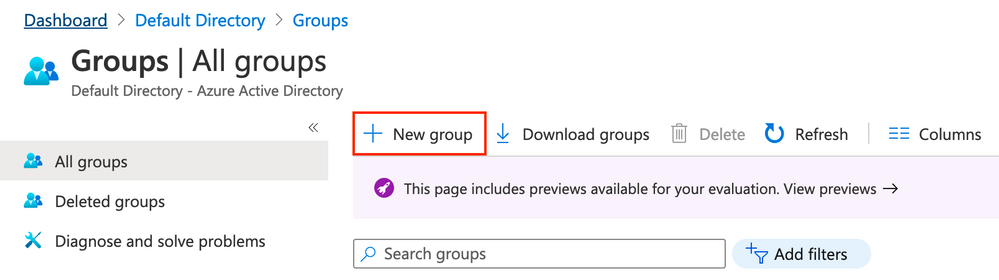
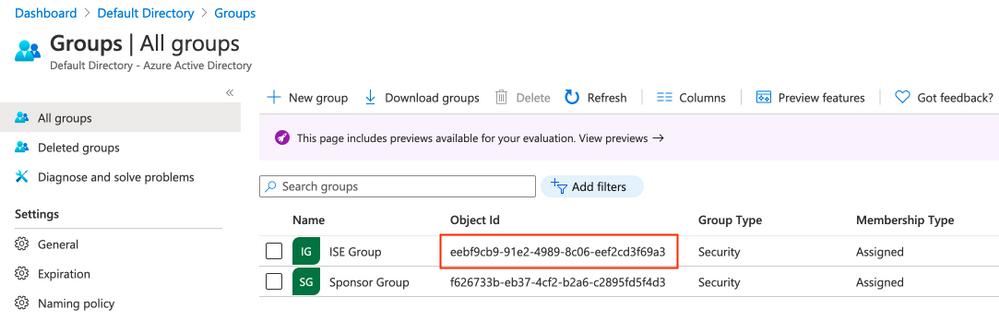
2. Crear un grupo de Azure AD
Seleccione Grupos. Haga clic en Nuevo grupo como se muestra en la imagen.
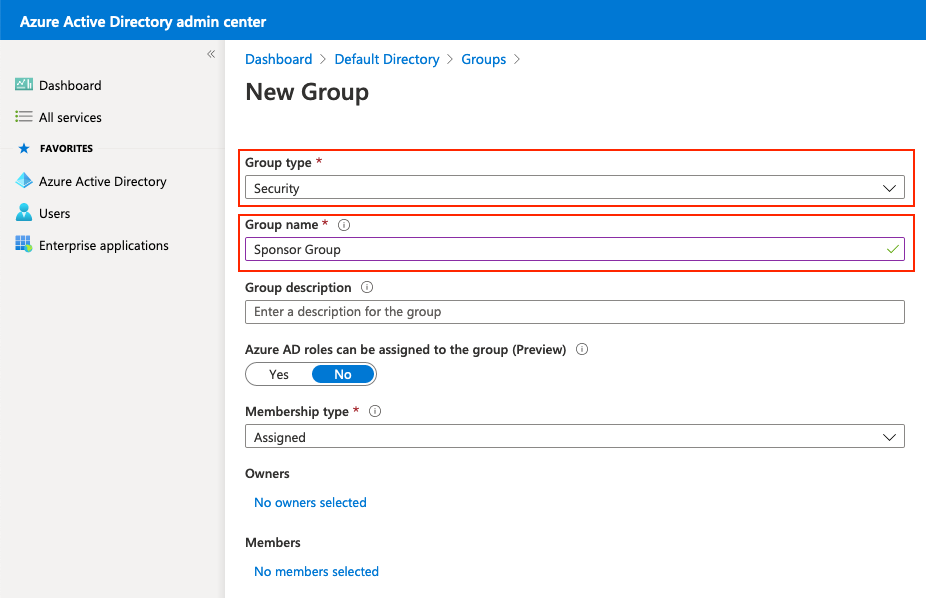
Mantener el tipo Grupo como Seguridad. Configure Group name como se muestra en la imagen.
3. Asignar usuario de Azure AD al grupo
Haga clic en No hay miembros seleccionados. Elija el usuario y haga clic en Seleccionar. Haga clic en Crear para crear el grupo con un usuario asignado.
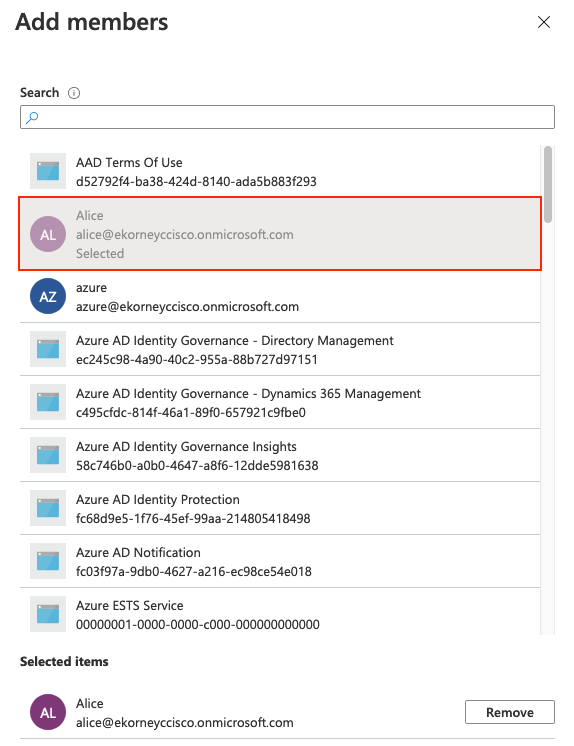
Tome nota de Group Object id, en esta pantalla es f626733b-eb37-4cf2-b2a6-c2895fd5f4d3 para Sponsor Group.
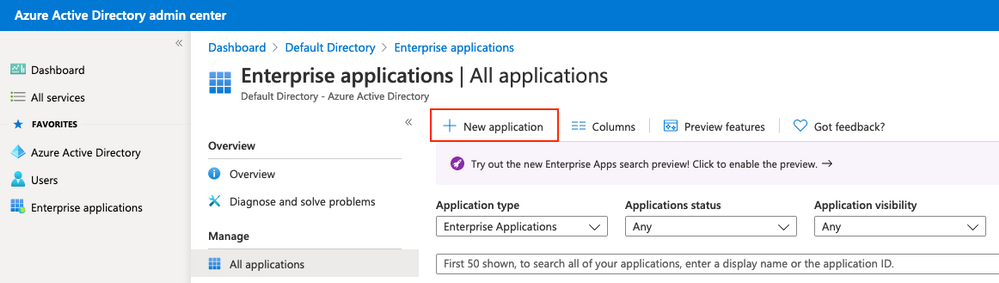
4. Crear una aplicación de Azure AD Enterprise
En AD, seleccione Aplicaciones empresariales y haga clic en Nueva aplicación como se muestra en la imagen.
Seleccione la aplicación No-galería como se muestra en la imagen.
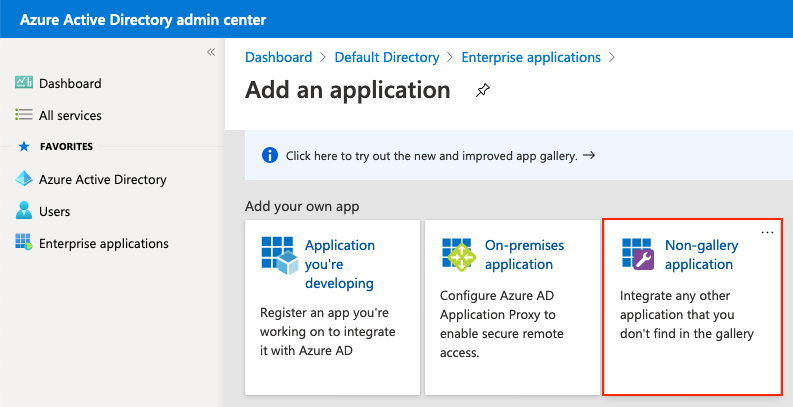
Introduzca el nombre de la aplicación y haga clic en Agregar.
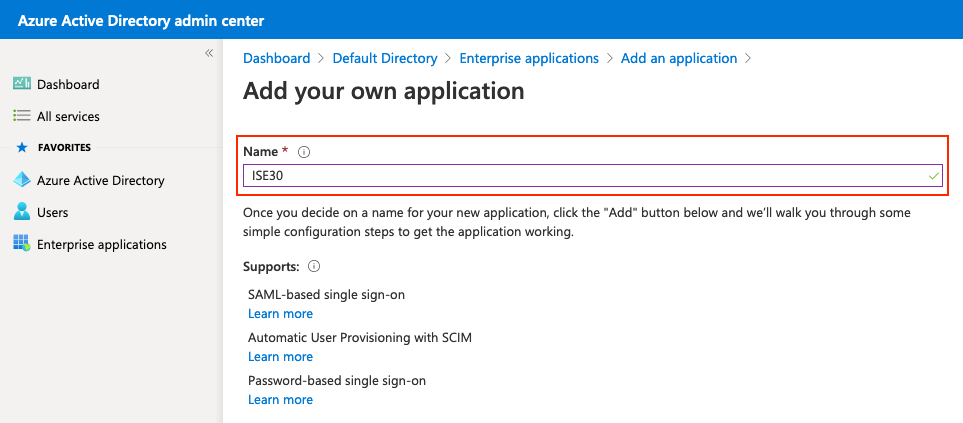
5. Agregar grupo a la aplicación
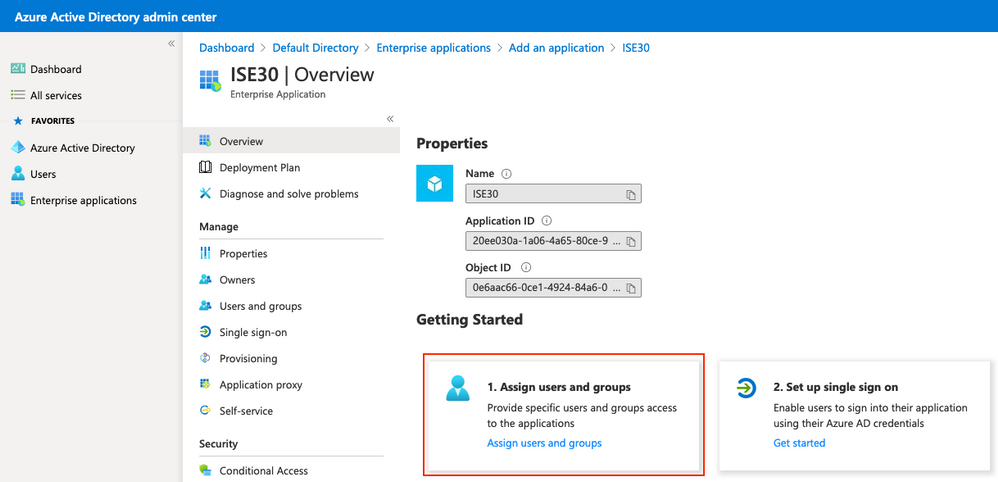
Seleccione Asignar usuarios y grupos.
Haga clic en Agregar usuario.
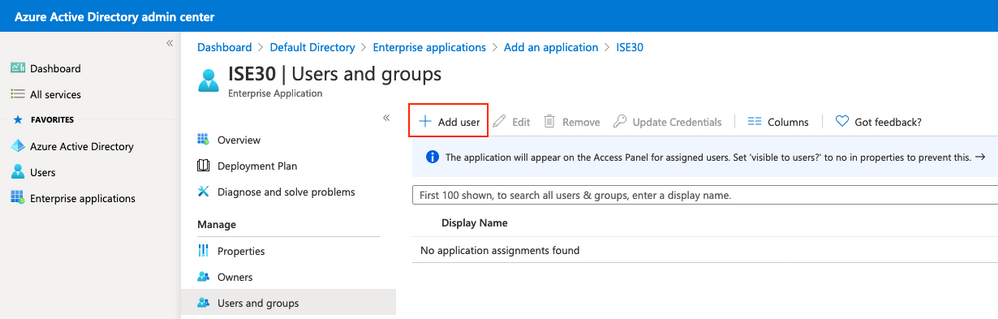
Haga clic en Usuarios y grupos.
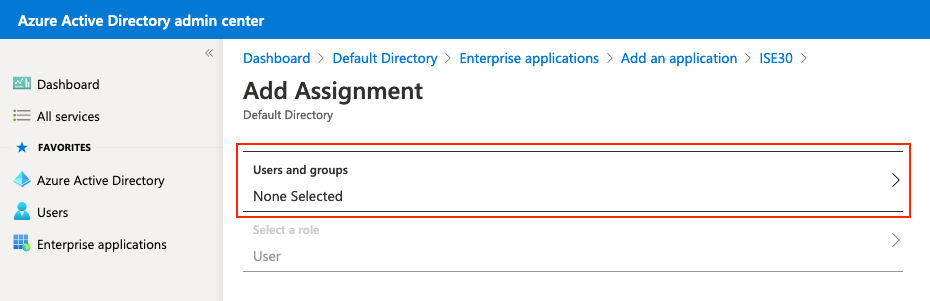
Elija el Grupo configurado previamente y haga clic en Seleccionar.
Nota: Depende de usted seleccionar el conjunto adecuado de usuarios o grupos a los que se debe obtener acceso.
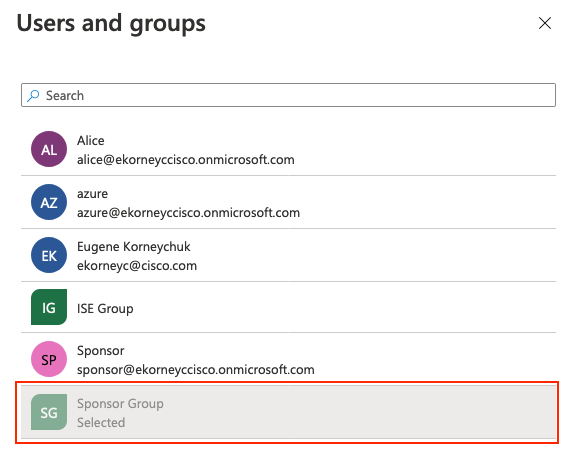
Una vez seleccionado el grupo, haga clic en Asignar como se muestra en la imagen.
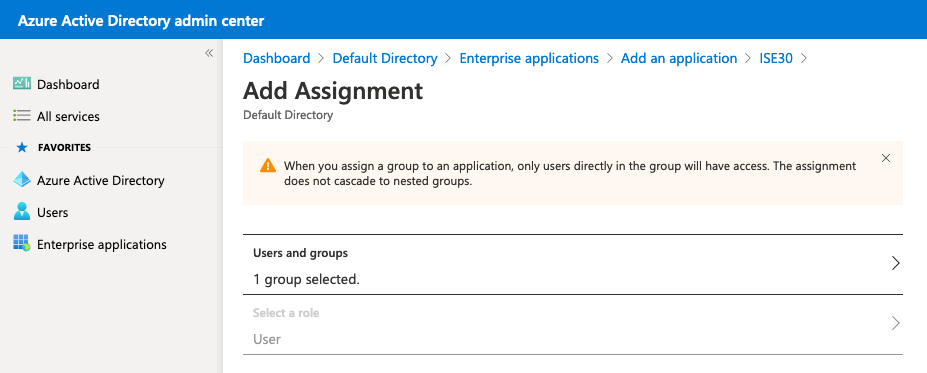
Como resultado, el menú Usuarios y grupos de su aplicación se debe rellenar con el grupo seleccionado.

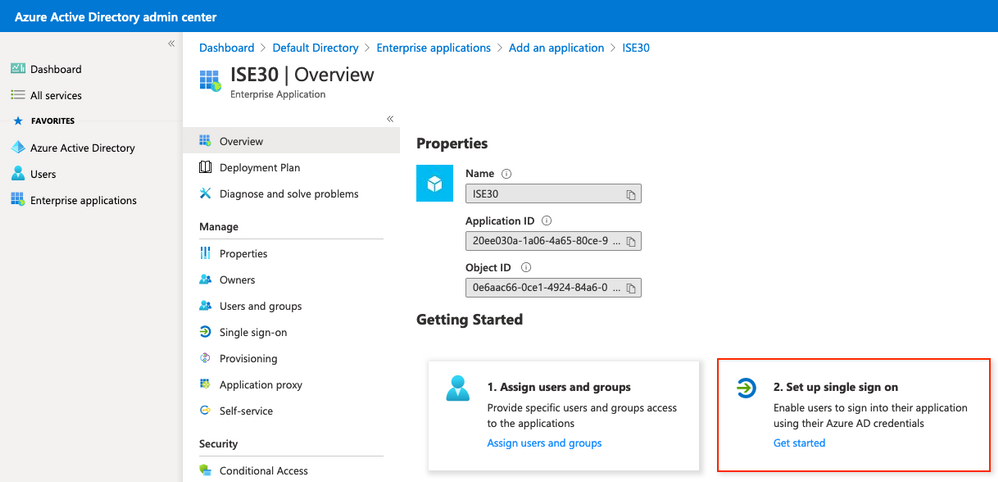
6. Configurar una aplicación Azure AD Enterprise
Vuelva a la Aplicación y haga clic en Configurar inicio de sesión único como se muestra en la imagen.
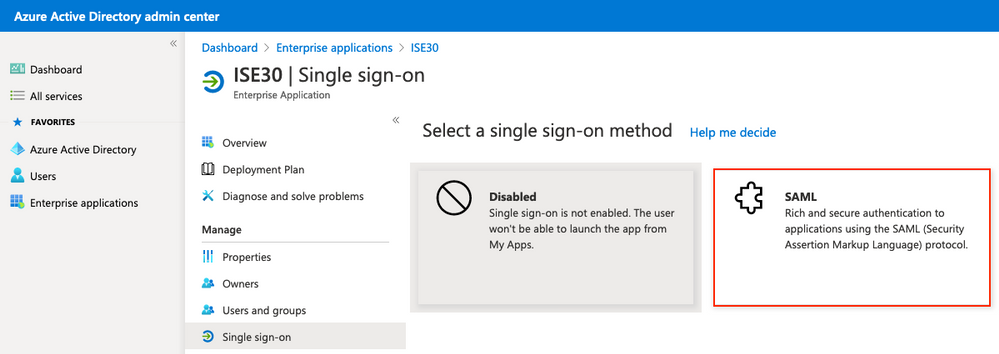
Seleccione SAML en la siguiente pantalla.
Haga clic en Editar junto a Configuración básica de SAML.
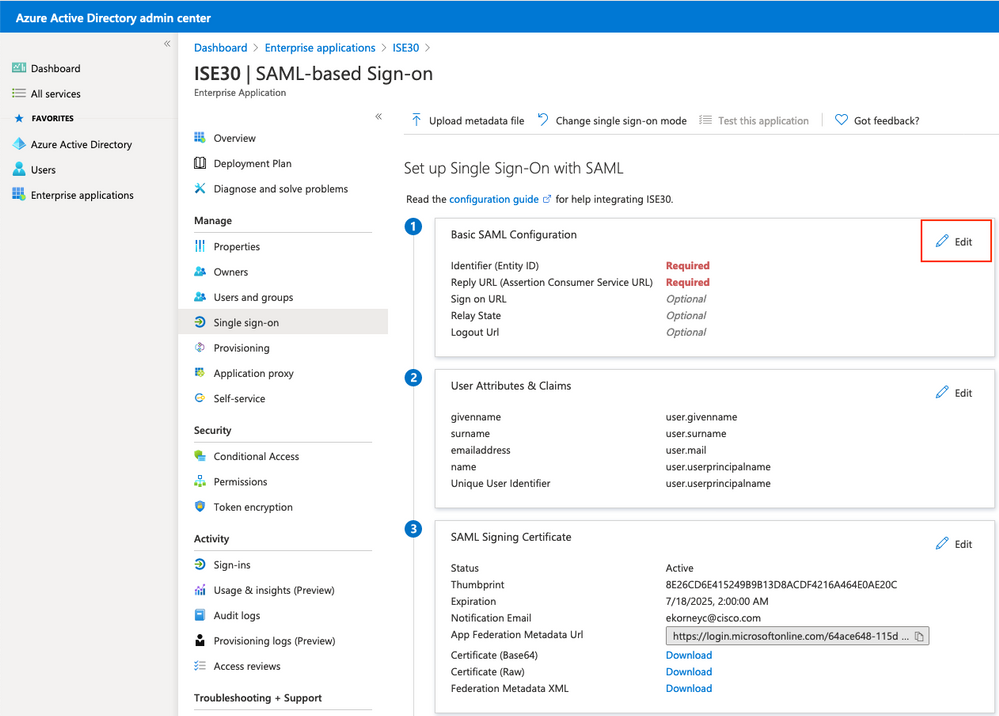
Rellene el identificador (ID de entidad) con el valor de IdEntidad del archivo XML del paso Exportar información del proveedor de servicios. Rellene la URL de respuesta (URL de servicio de consumidor de afirmación) con el valor de Ubicaciones de AssertionConsumerService. Rellene el valor Logout Url con ResponseLocation desde SingleLogoutService. Haga clic en Guardar.
Nota: La URL de respuesta actúa como una lista de paso, que permite que ciertas URL actúen como origen cuando se redirigen a la página IdP.
7. Configurar atributo de grupo de directorios activos
Para devolver el valor de atributo de grupo configurado previamente, haga clic en Editar junto a Atributos y reclamaciones de usuario.
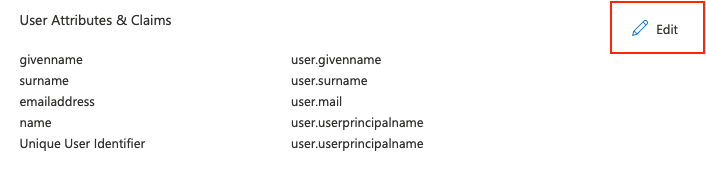
Haga clic en Agregar una reclamación de grupo.
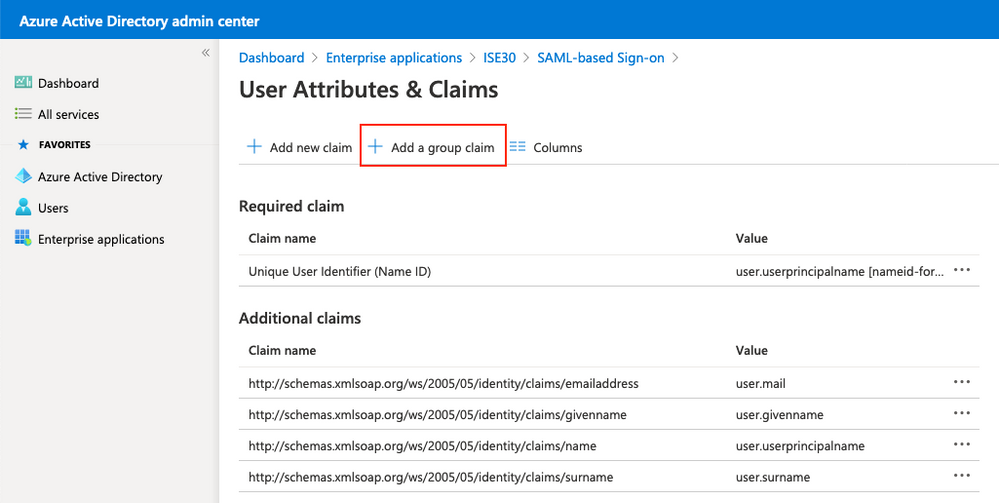
Seleccione Grupos de seguridad y haga clic en Guardar. El atributo de origen devuelto en aserción es una ID de grupo, que es una ID de objeto de grupo capturada anteriormente.
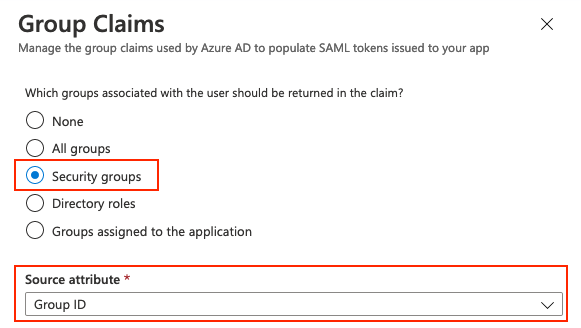
Anote el nombre de la reclamación del grupo. En este caso, es http://schemas.microsoft.com/ws/2008/06/identity/claims/groups.
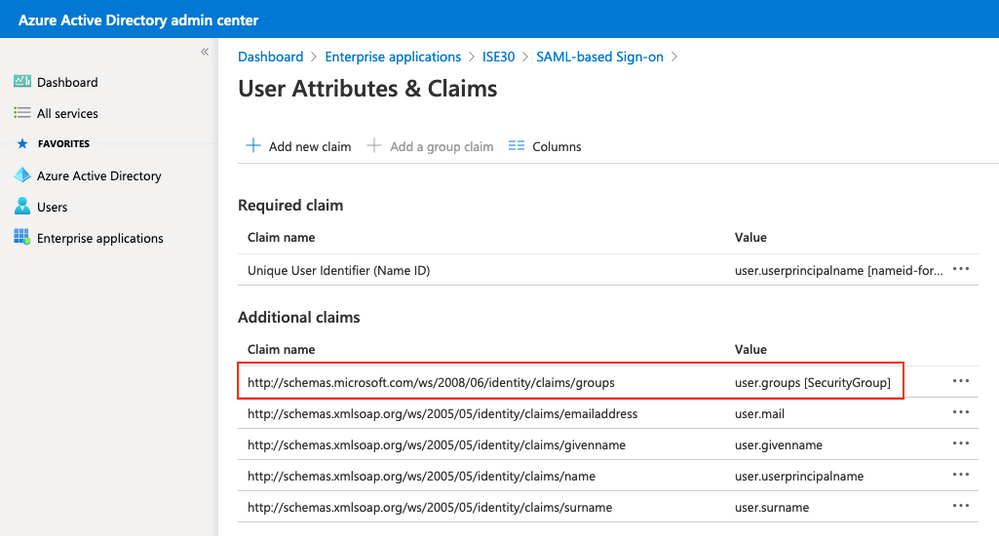
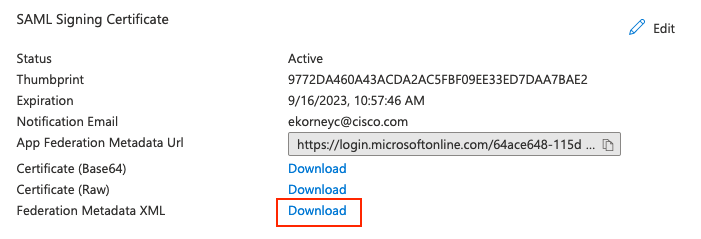
8. Descargar archivo XML de metadatos de Azure Federation
Haga clic en Descargar contra XML de metadatos de federación en Certificado de firma SAML.
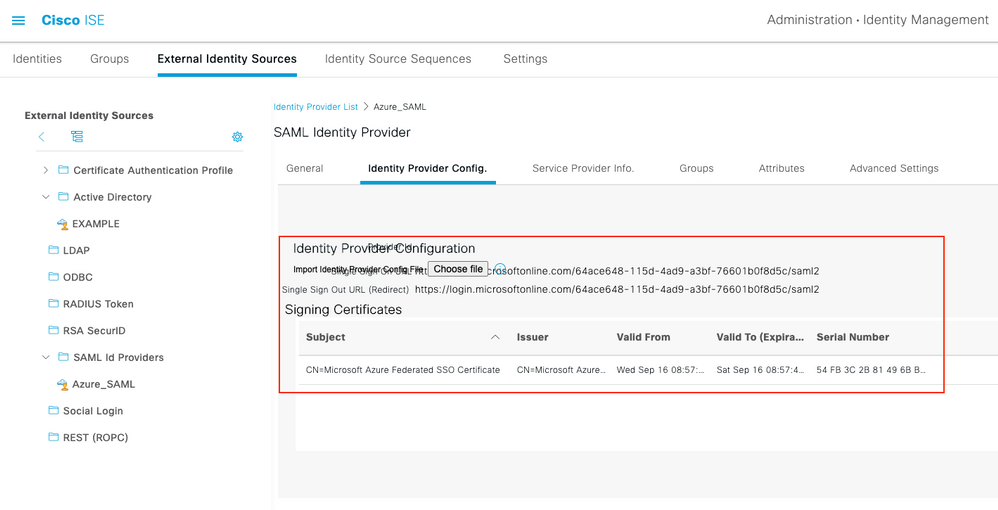
Paso 3. Cargar MetaData de Azure Active Directory en ISE
Vaya a Administration > Identity Management > External Identity Sources > SAML Id Providers > [Your SAML Provider].
Cambie a la ficha Configuración del proveedor de identidad. y haga clic en el botón Examinar. Seleccione Archivo XML de metadatos de federación en el paso Descargar XML de metadatos de federación de Azure y haga clic en Guardar.
Nota: El fallo de la interfaz de usuario con la configuración del proveedor de identidad debe resolverse en CSCvv74517.
Paso 4. Configuración de grupos SAML en ISE
Cambie a la pestaña Grupos y pegue el valor de Nombre de Reclamación del atributo Configure Active Directory Group en Atributo de Pertenencia de Grupo.
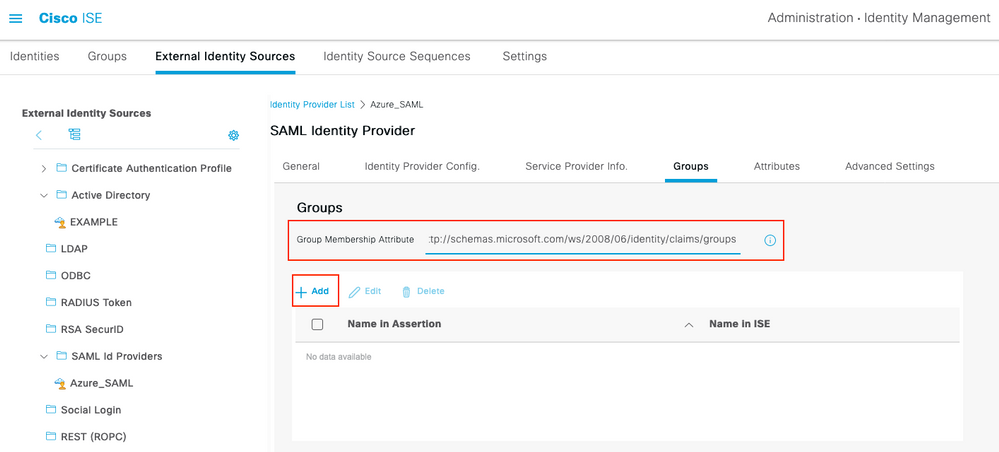
Haga clic en Agregar. Rellene Nombre en Assertion con el valor Group Object ID de Grupo de Patrocinadores capturado en Asignar usuario de Azure Active Directory al grupo. Configure Name en ISE con el valor significativo en este caso es Azure Sponsor Group. Click OK. Haga clic en Guardar.
Esto crea una asignación entre Group in Azure y Group name que se puede utilizar en ISE.
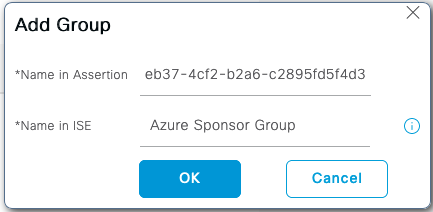
.
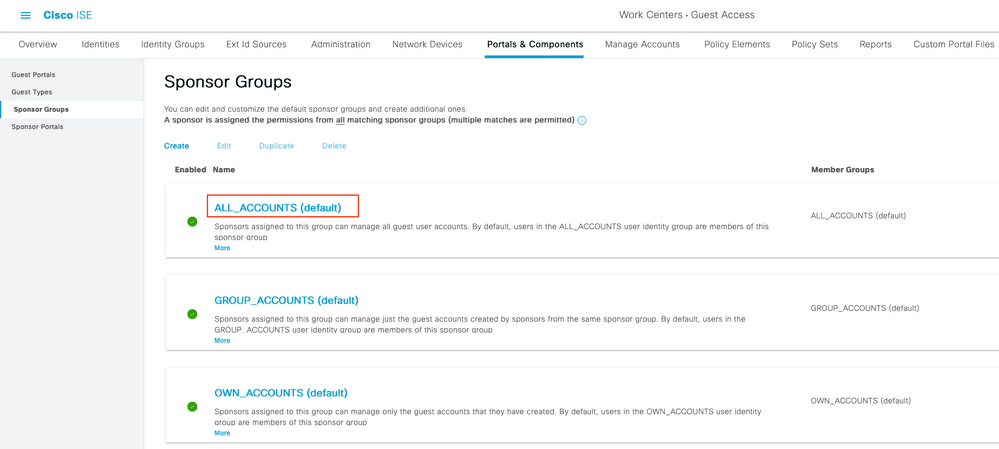
Paso 5. Configuración de la Asignación de Grupos de Patrocinadores en ISE
Vaya a Centros de trabajo > Acceso de invitado > Portals & Components > Grupos de patrocinadores y seleccione Grupo de patrocinadores que desea asignar al Grupo de Azure AD. En este ejemplo, se utilizó ALL_ACCOUNTS (valor predeterminado).
Haga clic en Miembros... y agregue Azure_SAML:Azure Sponsor Group a Selected User Groups. Esto asigna el Grupo de patrocinadores en Azure al Grupo de patrocinadores ALL_ACCOUNTS. Haga clic en Aceptar. Haga clic en Guardar.
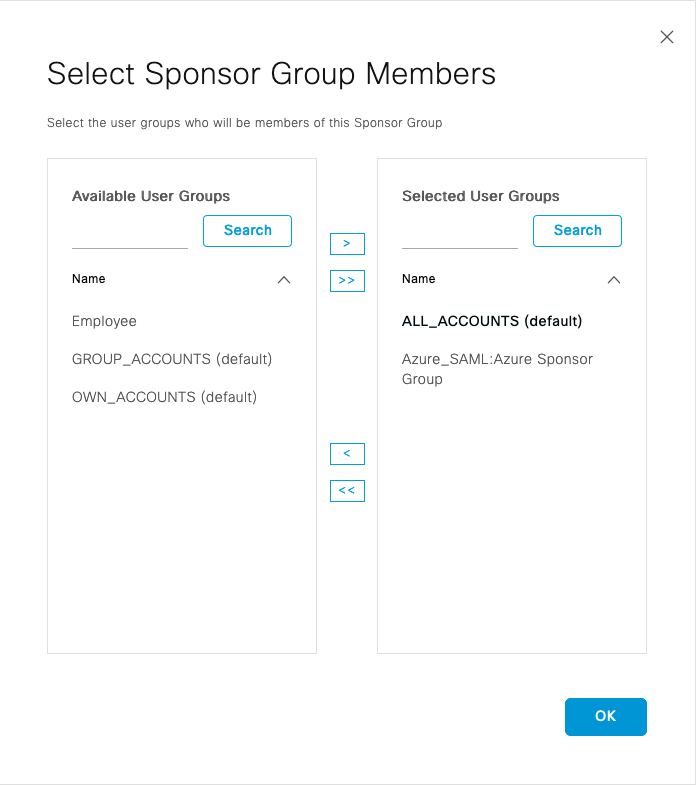
Verificación
Use esta sección para confirmar que su configuración funciona correctamente.
Nota: El nuevo usuario se ve obligado a cambiar la contraseña de usuario al iniciar sesión. Acepte los pasos de verificación AUP que no lo cubren. La verificación cubre el escenario, en el que los usuarios inician sesión por primera vez y AUP ya fue aceptado una vez por el Patrocinador (alice).
Ahora, si abre el portal de patrocinadores (por ejemplo, desde la URL de prueba), se le redirige a Azure para iniciar sesión y, a continuación, volver al portal de patrocinadores.
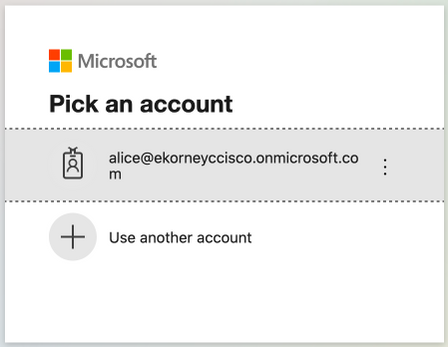
1. Inicie el portal de patrocinadores con su FQDN en el enlace URL de prueba del portal. ISE debe redirigirle a la página de inicio de sesión de Azure. Ingrese el nombre de usuario create before y haga clic en Next.
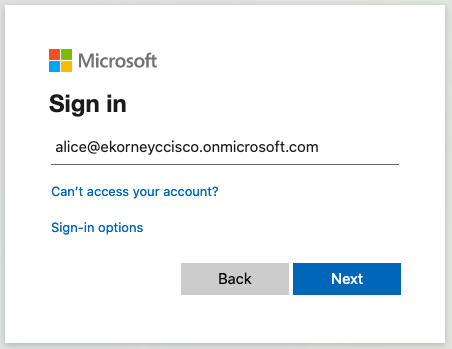
2. Introduzca la contraseña y haga clic en Iniciar sesión. La pantalla de inicio de sesión de IdP redirige al usuario al portal de patrocinadores inicial de ISE.
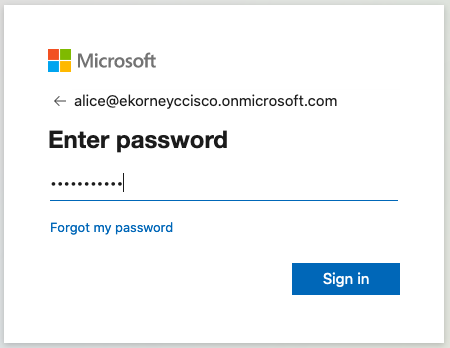
3. Acepte el AUP.
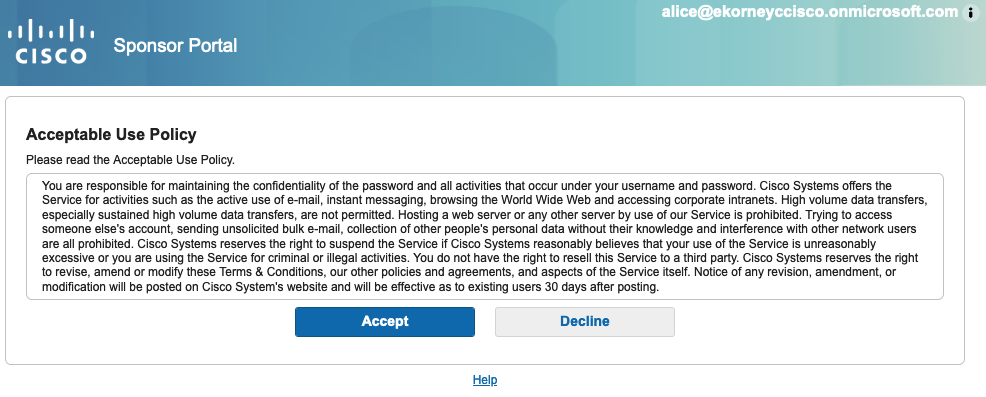
4. En este momento, el usuario patrocinador debe tener acceso completo al portal con permisos de grupo de patrocinadores ALL_ACCOUNTS.
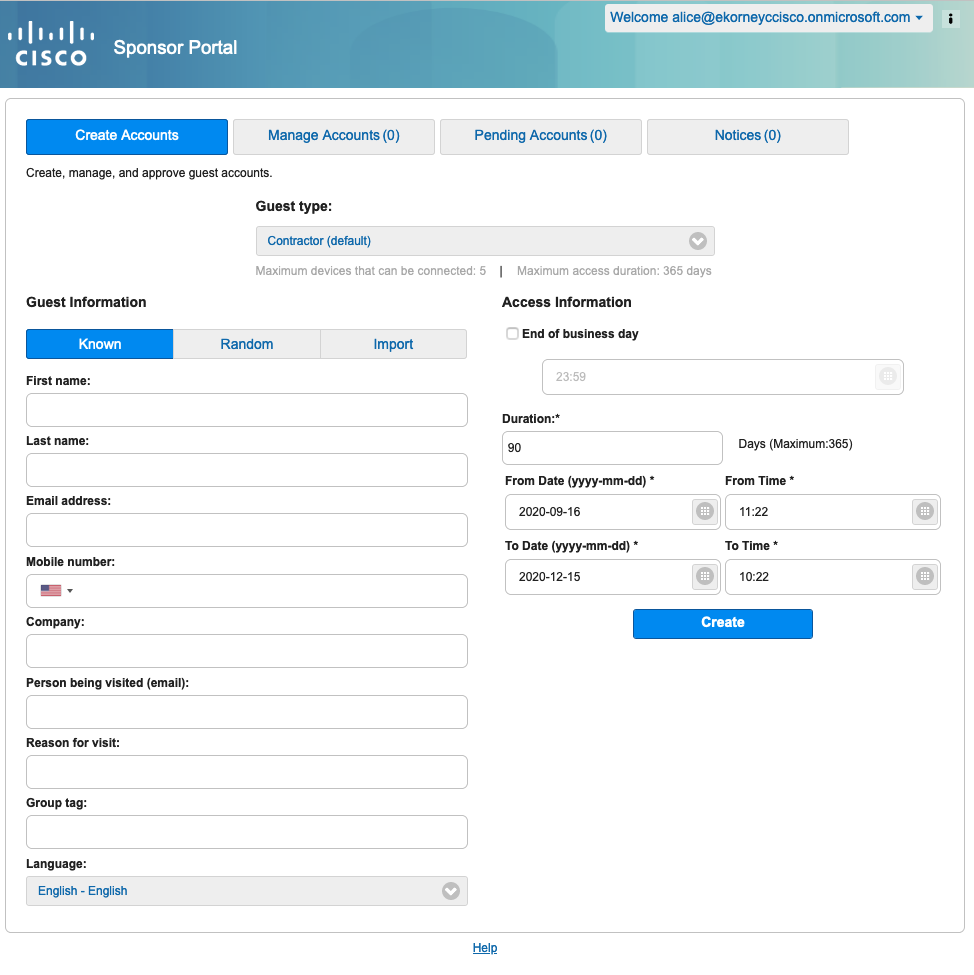
5. Haga clic en Cerrar sesión en el menú desplegable Bienvenido.
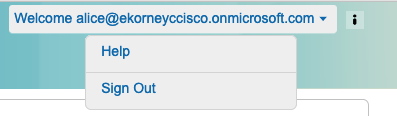
6. El usuario debe cerrar la sesión correctamente y volver a dirigirla a la pantalla de inicio de sesión.
Troubleshoot
En esta sección encontrará información que puede utilizar para solucionar problemas de configuración.
Problemas comunes
Es vital comprender que la autenticación SAML se maneja entre el explorador y Azure Active Directory. Por lo tanto, puede obtener errores relacionados con la autenticación directamente del proveedor de identidad (Azure), donde el compromiso con ISE todavía no se ha iniciado.
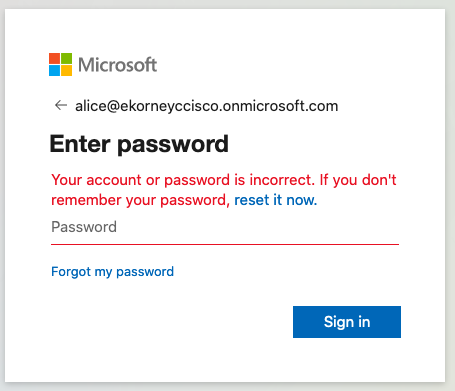
Problema 1. El usuario ingresa la contraseña incorrecta, no se procesaron los datos de usuario en ISE, el problema proviene directamente de IdP (Azure). Para corregir: Restablezca la contraseña o proporcione los datos correctos de la contraseña.
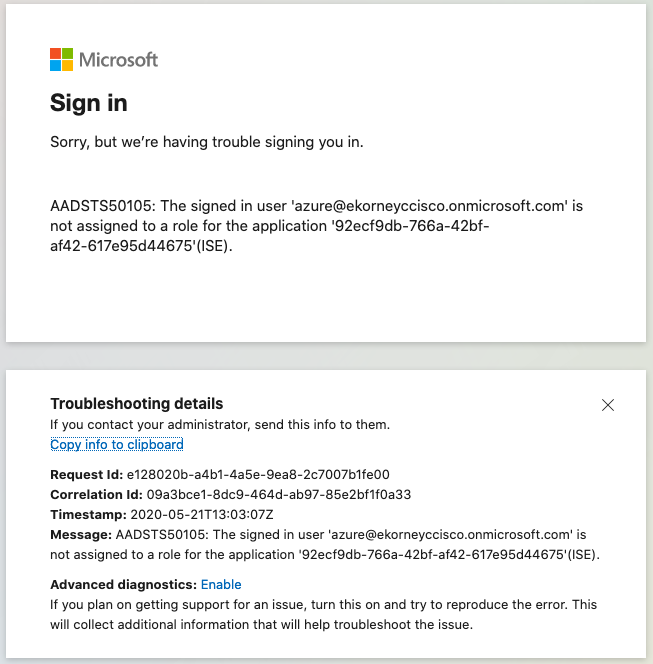
Problema 2. El usuario no forma parte del grupo al que se supone que se le permitirá acceder a SAML SSO. En este caso, no se ha procesado ningún dato de usuario en ISE, el problema proviene directamente de IdP (Azure). Para corregir: Verifique que el paso Agregar grupo al paso de configuración Aplicación se ejecute correctamente.
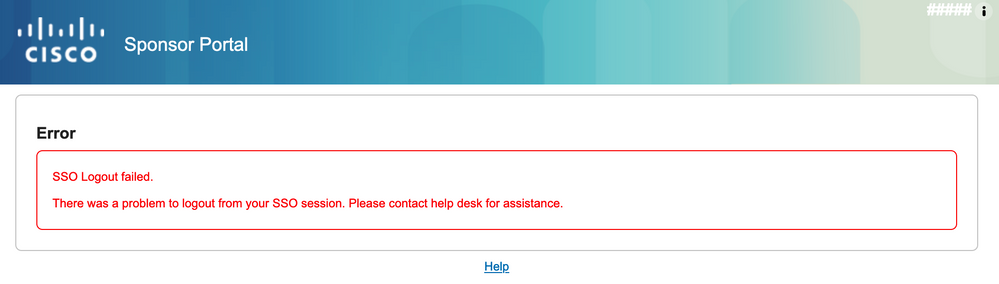
3. Sing Out no funciona como se esperaba, se ve este error - "SSO Logout failed. Se ha producido un problema al cerrar la sesión de SSO. Póngase en contacto con el soporte técnico para obtener ayuda". Se puede ver cuando la URL de cierre de sesión no está configurada correctamente en el IDP de SAML. En ese caso, esta URL se utilizó "https://sponsor30.example.com:8445/sponsorportal/SSOLogoutRequest.action?portal=100d02da-9457-41e8-87d7-0965b0714db2" mientras que debería ser "https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action" Para corregir: introduzca la URL correcta en la URL de cierre de sesión en Azure IdP.
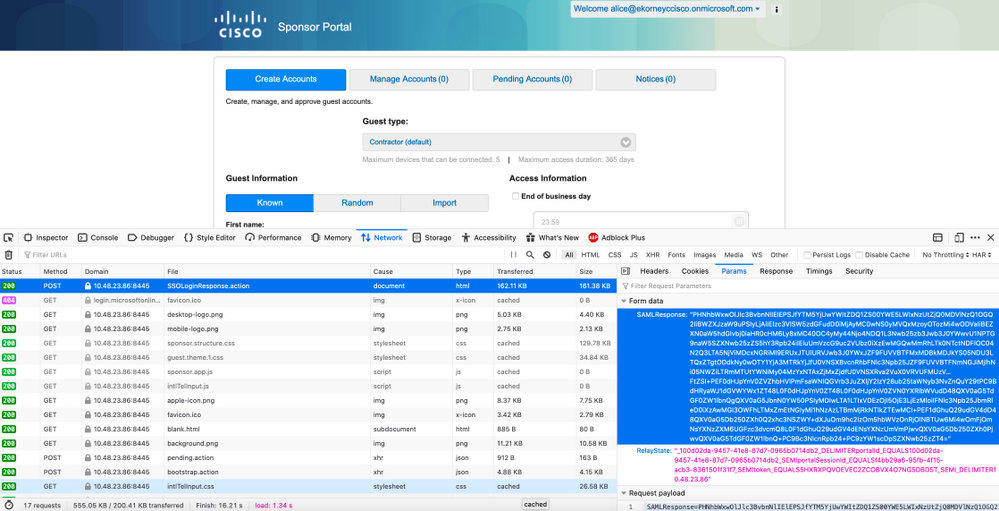
Resolución de problemas del cliente
Para verificar que se recibe la carga útil de SAML, puede utilizar Web Developer Tools. Navegue hasta Herramientas > Desarrollador Web > Red si utiliza Firefox e inicie sesión con las credenciales de Azure en el Portal. Puede ver la respuesta de SAML cifrada en la pestaña Params:
Resolución de problemas de ISE
El nivel de registro de los componentes aquí debe cambiarse en ISE. Vaya a Operaciones > Solución de problemas > Asistente de depuración > Configuración de registro de depuración.
| Nombre del componente | Nivel de registro | Nombre de archivo de registro |
| acceso de invitado | DEPURAR | guest.log |
| portal-web-action | DEPURAR | guest.log |
| opensaml | DEPURAR | ise-psc.log |
| saml | DEPURAR | ise-psc.log |
Grupo de trabajo de Depuraciones en el momento de la ejecución correcta del flujo (ise-psc.log):
1. El usuario se redirige a la URL de IdP desde el portal de patrocinadores.
2020-09-16 10:43:59,207 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL:
https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SPProviderId for Azure_SAML is: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - providerId (as should be found in IdP configuration):
http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - returnToId (relay state):
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId_EQUALSbd48c1a1-9477-4746-8e40-e43d20c9f429_SEMIportalSessionId_EQUALS8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_SEMItoken_EQUALSOA6CZJQD7X67TLYHE4Y3EM3EY097E2J_SEMI_DELIMITERsponsor30.example.com
2020-09-16 10:43:59,211 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML request - spUrlToReturnTo:
https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
2. La respuesta SAML se recibe del navegador.
2020-09-16 10:44:11,122 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,126 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,126 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State
:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,126 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,129 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,129 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,133 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:11,134 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Is redirect requiered: InitiatorPSN:sponsor30.example.com
This node's host name:ISE30-1ek LB:null request Server Name:sponsor30.example.com
2020-09-16 10:44:11,182 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- This node is the initiator (sponsor30.example.com) this node host name is:sponsor30.example.com
2020-09-16 10:44:11,184 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://javax.xml.XMLConstants/feature/secure-processing'
2020-09-16 10:44:11,187 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://apache.org/xml/features/disallow-doctype-decl'
2020-09-16 10:44:11,190 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Beginning to decode message from inbound transport of type: org.opensaml.ws.transport.http.HttpServletRequestAdapter
2020-09-16 10:44:11,190 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Decoded SAML relay state of:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId_EQUALSbd48c1a1-9477-4746-8e40-e43d20c9f429_SEMIportalSessionId_EQUALS8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_SEMItoken_EQUALSOA6CZJQD7X67TLYHE4Y3EM3EY097E2J_SEMI_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,190 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Getting Base64 encoded message from request
2020-09-16 10:44:11,191 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Parsing message stream into DOM document
2020-09-16 10:44:11,193 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Unmarshalling message DOM
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Starting to unmarshall Apache XML-Security-based SignatureImpl element
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Constructing Apache XMLSignature object
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Adding canonicalization and signing algorithms, and HMAC output length to Signature
2020-09-16 10:44:11,195 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.xml.signature.impl.SignatureUnmarshaller -::::- Adding KeyInfo to Signature
2020-09-16 10:44:11,197 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Message succesfully unmarshalled
2020-09-16 10:44:11,197 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.HTTPPostDecoder -::::- Decoded SAML message
2020-09-16 10:44:11,197 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.saml2.binding.decoding.BaseSAML2MessageDecoder -::::- Extracting ID, issuer and issue instant from status response
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- No security policy resolver attached to this message context, no security policy evaluation attempted
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Successfully decoded message.
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Checking SAML message intended destination endpoint against receiver endpoint
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Intended message destination endpoint:
https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Actual message receiver endpoint:
https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::-
SAML decoder's URIComparator - [https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action] vs. [https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action]
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::-
SAML message intended destination endpoint matched recipient endpoint
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: statusCode:urn:oasis:names:tc:SAML:2.0:status:Success
3. Se inicia el análisis de atributos (afirmación).
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/tenantid
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/tenantid> add value=<64ace648-115d-4ad9-a3bf-76601b0f8d5c>
2020-09-16 10:44:11,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object -
attribute<http://schemas.microsoft.com/identity/claims/tenantid> value=<64ace648-115d-4ad9-a3bf-76601b0f8d5c>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/objectidentifier
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/objectidentifier> add value=<50ba7e39-e7fb-4cb1-8256-0537e8a09146>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object -
attribute<http://schemas.microsoft.com/identity/claims/objectidentifier> value=<50ba7e39-e7fb-4cb1-8256-0537e8a09146>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/displayname
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/displayname> add value=<Alice>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object -
attribute<http://schemas.microsoft.com/identity/claims/displayname> value=<Alice>
4. El atributo de grupo se recibe con el valor de f626733b-eb37-4cf2-b2a6-c2895fd5f4d3, validación de firmas.
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/ws/2008/06/identity/claims/groups
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/ws/2008/06/identity/claims/groups> add value=<f626733b-eb37-4cf2-b2a6-c2895fd5f4d3>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.microsoft.com/ws/2008/06/identity/claims/groups> value=<f626733b-eb37-4cf2-b2a6-c2895fd5f4d3>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/identity/claims/identityprovider
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/identity/claims/identityprovider> add value=<https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.microsoft.com/identity/claims/identityprovider> value=<https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.microsoft.com/claims/authnmethodsreferences
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.microsoft.com/claims/authnmethodsreferences> add value=<http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.microsoft.com/claims/authnmethodsreferences> value=<http://schemas.microsoft.com/ws/2008/06/identity/authenticationmethod/password>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Found attribute name :
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Delimeter not configured,
Attribute=<http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name> add value=<alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes] Set on IdpResponse object - attribute
<http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name> value=<alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::getUserNameFromAssertion: IdentityAttribute is set to Subject Name
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::getUserNameFromAssertion: username value from Subject is=[alice@ekorneyccisco.onmicrosoft.com]
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::getUserNameFromAssertion: username set to=[alice@ekorneyccisco.onmicrosoft.com]
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: Found value for 'username' attribute assertion: alice@ekorneyccisco.onmicrosoft.com
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:readDict]
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.cfg.IdentityProviderMgr -::::- getDict: Azure_SAML
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:readDict]: read Dict attribute=<ExternalGroups>
2020-09-16 10:44:11,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/displayname> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [cacheGroupAttr] Adding to cache ExternalGroup values=<f626733b-eb37-4cf2-b2a6-c2895fd5f4d3>
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/tenantid> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/identityprovider> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/identity/claims/objectidentifier> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [parseAttributes]
Attribute <http://schemas.microsoft.com/claims/authnmethodsreferences> NOT configured in IdP dictionary, NOT caching
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [storeAttributesSessionData] idStore=<Azure_SAML> userName=alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLAttributesParser -::::- [SAMLAttributesParser:getEmail] The email attribute not configured on IdP
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: email attribute value:
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal ID:bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:
portalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:
_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId=bd48c1a1-9477-4746-8e40-e43d20c9f429;portalSessionId=8fa19bf2-9fa6-4892-b082-5cdabfb5daa1;
token=OA6CZJQD7X67TLYHE4Y3EM3EY097E2J;_DELIMITERsponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM.
IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:11,201 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SPProviderId for Azure_SAML is:
http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- ResponseValidationContext:
IdP URI: https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/
SP URI: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
Assertion Consumer URL: https://sponsor30.example.com:8445/sponsorportal/SSOLoginResponse.action
Request Id: _bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITERportalId_EQUALSbd48c1a1-9477-4746-8e40-e43d20c9f429_SEMIportalSessionId_EQUALS8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_SEMItoken_EQUALSOA6CZJQD7X67TLYHE4Y3EM3EY097E2J_SEMI_DELIMITERsponsor30.example.com
Client Address: 10.61.170.160
Load Balancer: null
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- no signature in response
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- Validating signature of assertion
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.BaseSignatureValidator -::::- Determine the signing certificate
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.BaseSignatureValidator -::::- Validate signature to SAML standard with cert:CN=Microsoft Azure Federated SSO Certificate serial:112959638548824708724869525057157788132
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.security.SAMLSignatureProfileValidator -::::- Saw Enveloped signature transform
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.security.SAMLSignatureProfileValidator -::::- Saw Exclusive C14N signature transform
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.BaseSignatureValidator -::::- Validate signature againsta signing certificate
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Attempting to validate signature using key from supplied credential
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Creating XMLSignature object
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Validating signature with signature algorithm URI: http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
2020-09-16 10:44:11,202 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Validation credential key algorithm 'RSA', key instance class 'sun.security.rsa.RSAPublicKeyImpl'
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] org.opensaml.xml.signature.SignatureValidator -::::- Signature validated with key from supplied credential
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- Assertion signature validated succesfully
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating response
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating assertion
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Assertion issuer succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Authentication statements succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Subject succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.validators.AssertionValidator -::::- Conditions succesfully validated
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: validation succeeded for alice@ekorneyccisco.onmicrosoft.com
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: found signature on the assertion
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Retrieve [CN=Microsoft Azure Federated SSO Certificate] as signing certificates
2020-09-16 10:44:11,204 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: loginInfo:SAMLLoginInfo: name=alice@ekorneyccisco.onmicrosoft.com,
format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, sessionIndex=_4b798ec4-9aeb-40dc-8bed-6dd2fdd46800, time diff=26329
2020-09-16 10:44:11,292 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - Session:null IDPResponse:
IdP ID: Azure_SAML
Subject: alice@ekorneyccisco.onmicrosoft.com
SAML Status Code:urn:oasis:names:tc:SAML:2.0:status:Success
SAML Success:true
SAML Status Message:null
SAML email:
SAML Exception:nullUserRole : SPONSOR
2020-09-16 10:44:11,292 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - about to call authenticateSAMLUser messageCode:null subject:alice@ekorneyccisco.onmicrosoft.com
2020-09-16 10:44:11,306 INFO [RMI TCP Connection(346358)-127.0.0.1][] api.services.server.role.RoleImpl -::::- Fetched Role Information based on RoleID: 6dd3b090-8bff-11e6-996c-525400b48521
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [SAMLSessionDataCache:getGroupsOnSession] idStore=<Azure_SAML> userName=<alice@ekorneyccisco.onmicrosoft.com>
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cisco.cpm.saml.framework.SAMLSessionDataCache -::::- [getAttributeOnSession] idStore=<Azure_SAML> userName=<alice@ekorneyccisco.onmicrosoft.com> attributeName=<Azure_SAML.ExternalGroups>
5. El grupo de usuarios se agrega a los resultados de autenticación para que el portal lo pueda utilizar, se pasa la autenticación SAML.
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- AuthenticatePortalUser - added user groups from SAML response to AuthenticationResult, all retrieved groups:[f626733b-eb37-4cf2-b2a6-c2895fd5f4d3]
2020-09-16 10:44:11,320 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Authenticate SAML User - result:PASSED
6. Se activa la opción Cerrar sesión. La URL de cierre de sesión se recibe en la respuesta de SAML; https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action.
2020-09-16 10:44:51,462 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:51,462 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- getLogoutMethod - method:REDIRECT_METHOD_LOGOUT
2020-09-16 10:44:51,462 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- getSignLogoutRequest - null
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.MessageComposer -:::alice@ekorneyccisco.onmicrosoft.com:- buildLgoutRequest - loginInfo:SAMLLoginInfo: name=alice@ekorneyccisco.onmicrosoft.com, format=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, sessionIndex=_4b798ec4-9aeb-40dc-8bed-6dd2fdd46800, time diff=26329
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.SAMLFacadeImpl -:::alice@ekorneyccisco.onmicrosoft.com:- SPProviderId for Azure_SAML is: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.MessageComposer -:::alice@ekorneyccisco.onmicrosoft.com:- buildLgoutRequest - spProviderId:http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:51,463 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-8][] cpm.saml.framework.impl.MessageComposer -:::alice@ekorneyccisco.onmicrosoft.com:- buildLgoutRequest - logoutURL:https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:53,199 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal ID:bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:53,200 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- Is redirect requiered: InitiatorPSN:sponsor30.example.com This node's host name:ISE30-1ek LB:null request Server Name:sponsor30.example.com
2020-09-16 10:44:53,248 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- This node is the initiator (sponsor30.example.com) this node host name is:sponsor30.example.com
2020-09-16 10:44:53,249 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,249 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:8fa19bf2-9fa6-4892-b082-5cdabfb5daa1
2020-09-16 10:44:53,250 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://javax.xml.XMLConstants/feature/secure-processing'
2020-09-16 10:44:53,251 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] org.opensaml.xml.parse.BasicParserPool -::::- Setting DocumentBuilderFactory attribute 'http://apache.org/xml/features/disallow-doctype-decl'
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Beginning to decode message from inbound transport of type: org.opensaml.ws.transport.http.HttpServletRequestAdapter
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.HTTPRedirectDeflateDecoder -::::- Decoded RelayState: _bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.HTTPRedirectDeflateDecoder -::::- Base64 decoding and inflating SAML message
2020-09-16 10:44:53,253 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Parsing message stream into DOM document
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Unmarshalling message DOM
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Message succesfully unmarshalled
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.HTTPRedirectDeflateDecoder -::::- Decoded SAML message
2020-09-16 10:44:53,256 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.saml2.binding.decoding.BaseSAML2MessageDecoder -::::- Extracting ID, issuer and issue instant from status response
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- No security policy resolver attached to this message context, no security policy evaluation attempted
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.ws.message.decoder.BaseMessageDecoder -::::- Successfully decoded message.
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Checking SAML message intended destination endpoint against receiver endpoint
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Intended message destination endpoint: https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- Actual message receiver endpoint: https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML decoder's URIComparator - [https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action] vs. [https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action]
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] opensaml.common.binding.decoding.BaseSAMLMessageDecoder -::::- SAML message intended destination endpoint matched recipient endpoint
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: statusCode:urn:oasis:names:tc:SAML:2.0:status:Success
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal ID:bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML HTTPRequest - Portal Session info:8fa19bf2-9fa6-4892-b082-5cdabfb5daa1
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML response - Relay State:_bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
2020-09-16 10:44:53,257 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML flow initiator PSN's Host name is:sponsor30.example.com
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isLoadBalancerConfigured() - LB NOT configured for: Azure_SAML
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAMLUtils::isOracle() - checking whether IDP URL indicates that its OAM. IDP URL: https://login.microsoftonline.com/64ace648-115d-4ad9-a3bf-76601b0f8d5c/saml2
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SPProviderId for Azure_SAML is: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
2020-09-16 10:44:53,258 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- ResponseValidationContext:
IdP URI: https://sts.windows.net/64ace648-115d-4ad9-a3bf-76601b0f8d5c/
SP URI: http://CiscoISE/bd48c1a1-9477-4746-8e40-e43d20c9f429
Assertion Consumer URL: https://sponsor30.example.com:8445/sponsorportal/SSOLogoutResponse.action
Request Id: _bd48c1a1-9477-4746-8e40-e43d20c9f429_DELIMITER8fa19bf2-9fa6-4892-b082-5cdabfb5daa1_DELIMITERsponsor30.example.com
Client Address: 10.61.170.160
Load Balancer: null
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- LogoutResponse signature validated succesfully
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.SAMLSignatureValidator -::::- This is LogoutResponse (only REDIRECT is supported) no signature is on assertion, continue
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating response
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.validators.WebSSOResponseValidator -::::- Validating assertion
2020-09-16 10:44:53,259 DEBUG [https-jsse-nio-10.48.23.86-8445-exec-4][] cpm.saml.framework.impl.SAMLFacadeImpl -::::- SAML Response: validation succeeded for null
Con la colaboración de ingenieros de Cisco
- Eugene KorneychukCisco TAC Engineer
Contacte a Cisco
- Abrir un caso de soporte

- (Requiere un Cisco Service Contract)
 Comentarios
Comentarios