Introduction
This document describes the behavior of MAC Access Control List (MAC ACL) on the control plane non-IP traffic on Catalyst 4500 series switches. MAC ACL can be used in order to filter non-IP traffic on a VLAN and on a physical Layer 2 (L2) port.
For more information about the supported non-IP protocols in the MAC access-list extended command, refer Catalyst 4500 Series Switch Cisco IOS® Command Reference.
Problem
Assume this configuration:
mac access-list extended udld
deny any host 0100.0ccc.cccc
permit any any
!
interface GigabitEthernet2/4
switchport mode trunk
udld port aggressive
mac access-group udld in
!
Note: This ACL does not deny L2 control plane traffic like CDP/UDLD/VTP/PAgP frames with destination MAC = 0100.0ccc.cccc that comes inbound in interface GigabitEthernet2/4.
On Catalyst 4500 switches, there is a system generated inbuilt ACL that punts L2 control plane traffic to CPU which takes precedence over a user defined ACL, in order to classify this traffic. Hence, a user defined ACL does not achieve this purpose. This behavior is specific to Catalyst 4500 platform, other platforms might have different behaviors.
Solution
This method can be used to drop the traffic at ingress port or at CPU, if there is a need to do so.
Caution: Steps here are intended to drop all the frames that have destination MAC = 0100.0ccc.cccc that comes in on a specific interface. This MAC address is used by UDLD/DTP/VTP/Pagp control plane Protocol Data Units (PDUs).
If the objective is to police this traffic and not drop all of it, control plane policing is a preferred solution. Refer Configuring Control Plane Policing on Catalyst 4500
Step 1. Enable control-packet Quality of Service (QoS) for cdp-vtp:
Catalyst4500(config)#qos control-packets cdp-vtp
This step generates a system generated ACL:
Catalyst4500#show run | begin system-control
mac access-list extended system-control-packet-cdp-vtp
permit any host 0100.0ccc.cccc
Note: A user-defined named MAC ACL (as shown here) can also be used instead of system defined ACL as generated earlier. Either use system generated or user-defined ACL in order to save Ternary Content Addressable Memory (TCAM) resources.
mac access-list extended udld
permit any host 0100.0ccc.cccc
Step 2. Create a class-map in order to match the traffic that hits this ACL:
Catalyst4500(config)#class-map cdp-vtp
Catalyst4500(config-cmap)#match access-group name system-control-packet-cdp-vtp
Catalyst4500(config-cmap)#end
Catalyst4500#
Step 3. Create a policy map and police traffic that matches Step 2 class with conform action = drop and exceed action = drop:
Catalyst4500(config)#policy-map cdp-vtp-policy
Catalyst4500(config-pmap)#class cdp-vtp
Catalyst4500(config-pmap-c)#police 32000 conform-action drop exceed-action drop
Catalyst4500(config-pmap-c-police)#end
Catalyst4500#
Step 4. Apply the policy-map inbound on the L2 port where this traffic needs to be dropped:
Catalyst4500(config)#int gigabitEthernet 2/4
Catalyst4500(config-if)#service-policy input cdp-vtp-policy
Catalyst4500(config-if)#end
!
interface GigabitEthernet2/4
switchport mode trunk
udld port aggressive
service-policy input cdp-vtp-policy
end
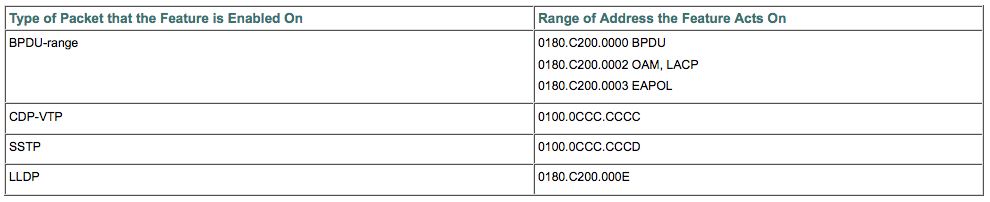
Similar system generated ACLs can be used for other L2 control frames in case they need to be policed or dropped. Refer Layer 2 Control Packet QoS for details and as shown in the image.
Catalyst4500(config)#qos control-packets ?
bpdu-range Enable QoS on BPDU-range packets
cdp-vtp Enable QoS on CDP and VTP packets
eapol Enable QoS on EAPOL packets
lldp Enable QoS on LLDP packets
protocol-tunnel Enable QoS on protocol tunneled packets
sstp Enable QoS on SSTP packets
<cr>