QuickVPN TCP Dump Analysis
Available Languages
Objectives
This article explain how to how to capture the packets with Wireshark to monitor client traffic when QuickVPN exists. QuickVPN is an easy way to set up VPN software on a remote computer or laptop with a simple user name and password. This will help to securely access networks based on the device used. Wireshark is a packet sniffer used to capture the packets in the network for troubleshooting.
QuickVPN is no longer supported by Cisco. This article is still available for customers using QuickVPN. For a list of routers that have used QuickVPN, click Cisco Small Business QuickVPN. For more information on QuickVPN, you can view the video at the end of this article.
Applicable Devices
• RV series (see list in link above)
Analyze QuickVPN TCP Dumps

In order to follow the steps in this article, Wireshark and QuickVPN client need to be installed on your PC.
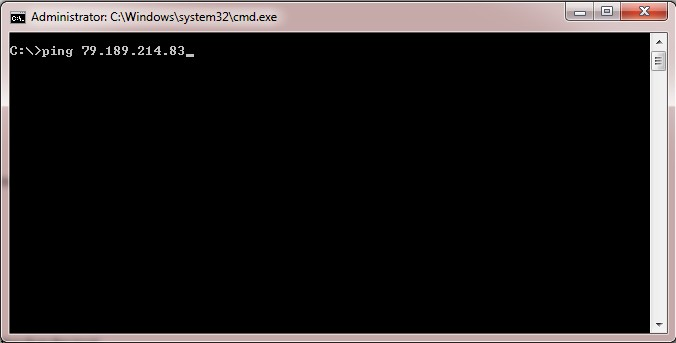
Step 1. On your computer, navigate to the search bar. Enter cmd and select the Command Prompt application from the options. Enter the command ping and the IP address you are trying to connect to. In this case, ping 79.189.214.83 was entered.
Step 2. Open the Wireshark application and choose the interface through which the packets are transmitted to the internet and capture traffic.
Step 3. Start the QuickVPN application. Enter the profile name in the Profile Name field.
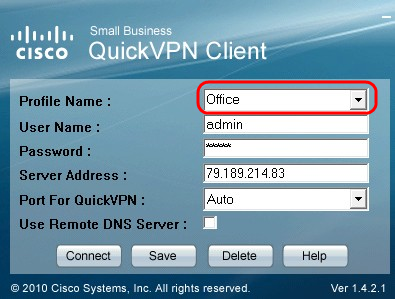
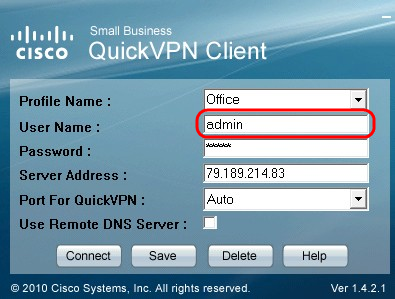
Step 4. Enter the user name in the User Name field.
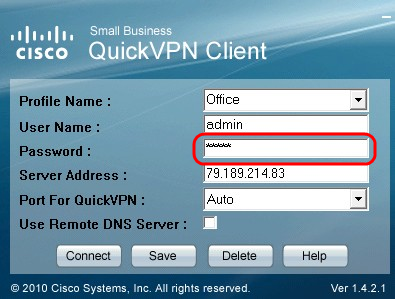
Step 5. Enter the password in the Password field.
Step 6. Enter the server address in the Server Address field.
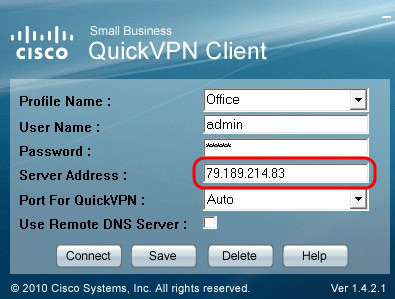
Step 7. Choose port for QuickVPN in the Port for QuickVPN drop down list.
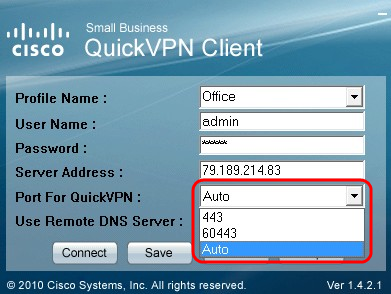
Step 8. (Optional) Check Use Remote DNS server check box to use the remote DNS server rather than the local one.
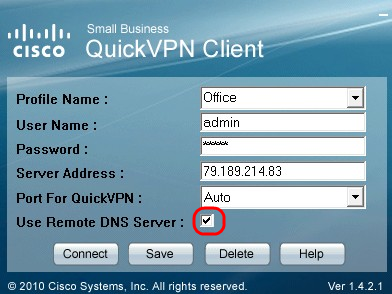
Step 9. Click Connect.
Step 10. Open the captured traffic file.
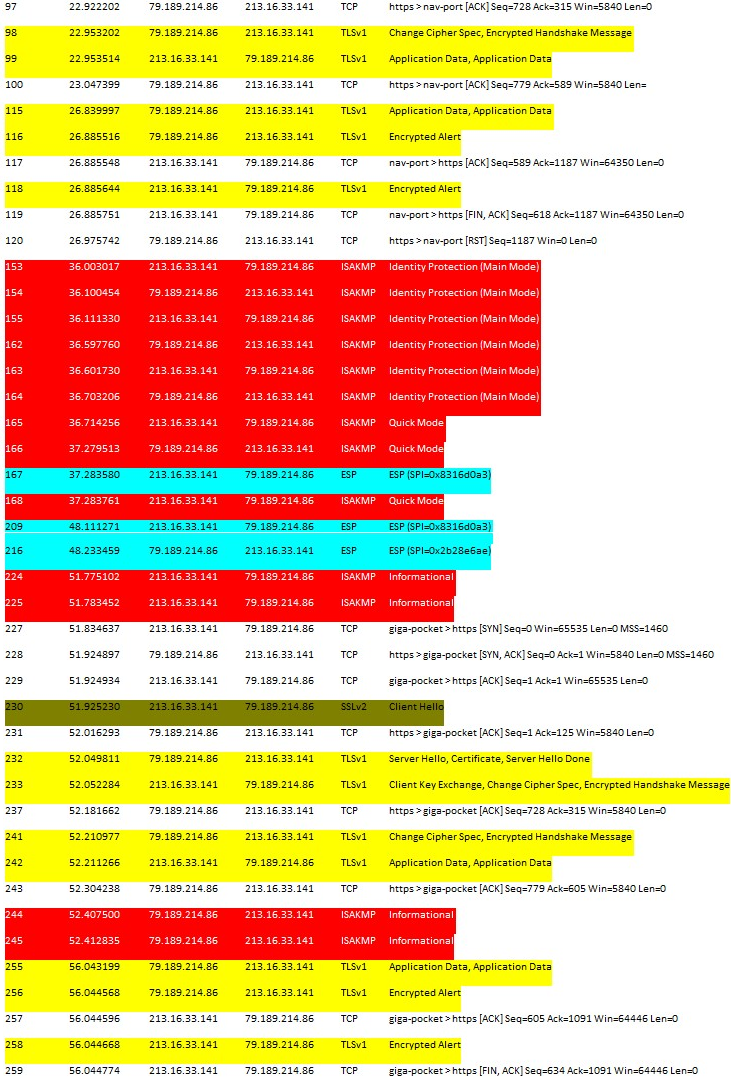
For a QuickVPN connection to happen there are three major things which needs to be checked
• Connectivity
• Activating policy (Check Certificate)
• Verify the Network
To check the connection we need to first see the Transport Layer Security (TLSv1) packets in the capture traffic along with its predecessor Secure Socket Layer(SSL). These are the cryptographic protocols which provide the security for the communication over the network.
Activating Policy can be checked with the Internet Security Association and Key Management Protocol (ISAKMP) packet in the the Wireshark captured traffic. It defines the mechanism for authentication, creation and management of Security Association (SA), key generation techniques, and threat mitigation. It uses IKE for the key exchange.
ISAKMP helps to decide the packet format to establish, negotiate, modify, and delete the SA. It has various information required for various network security services like IP layer service, including header authentication, pay load encapsulation, transport or application layer services, or self-protection of negotiation traffic. ISAKMP defines payloads for exchanging key generation and authentication data. These formats provide a consistent framework for transferring key and authentication data which is independent of the key generation technique, encryption algorithm, and authentication mechanism.
Encapsulation Security payload (ESP) is used to check the confidentiality, data origin authentication connectionless integrity, and anti-replay service and limited traffic flow. In QuickVPN, ESP is a member of the IPSec protocol. It is used to provide the authenticity, integrity and confidentiality of packets. It supports encryption and authentication separately.
Note: Encryption without authentication is not recommended.
ESP is not used to protect the IP header but in tunnel mode the entire IP Packet is encapsulated with a new packet header. It is added and is afforded to the whole inner IP packet including the inner header. It operates on top of IP and uses protocol number 50.
Conclusion
You have now learned how to capture packets with Wireshark and QuickVPN.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
11-Dec-2018 |
Initial Release |
 Feedback
Feedback