Provision Secure Firewall ASA to CSM
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes the process to provision Secure Firewall Adaptive Security Appliance (ASA) to Cisco Security Manager (CSM).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Secure Firewall ASA
- CSM
Components Used
The information in this document is based on these software and hardware versions:
- Secure Firewall ASA version 9.18.3
- CSM version 4.28
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
CSM helps to enable consistent policy enforcement and rapid troubleshooting of security events, offering summarized reports across the security deployment. Using its centralized interface, organizations can scale efficiently and manage a wide range of Cisco security devices with improved visibility.
Configure
In the next example, a virtual ASA is provisioned to a CSM for centralized management.
Configurations
Configure ASA for HTTPS Management
Step 1. Create a user with all privileges.
Command Line (CLI) syntax:
configure terminal
username < user string > password < password > privilege < level number >This translates into the next command example, which has the user csm-user and password cisco123 as follows:
ciscoasa# configure terminal
ciscoasa(config)# username csm-user password cisco123 privilege 15
Tip: Externally authenticated users are accepted for this integration as well.
Step 2. Enable HTTP server.
Command Line (CLI) syntax:
configure terminal
http server enableStep 3. Allow HTTPS access for the CSM server IP address.
Command Line (CLI) syntax:
configure terminal
http < hostname > < netmask > < interface name >This translates into the next command example, which allows any network to access the ASA through HTTPS on the outside interface (GigabitEthernet0/0):
ciscoasa# configure terminal
ciscoasa(config)# http 0.0.0.0 0.0.0.0 outsideStep 4. Validate that HTTPS is reachable from the CSM server.
Open any web broser and type the next syntax:
https://< ASA IP address >/This translates into the next example for the outside interface IP address that was allowed for HTTPS access on the previous step:
https://10.8.4.11/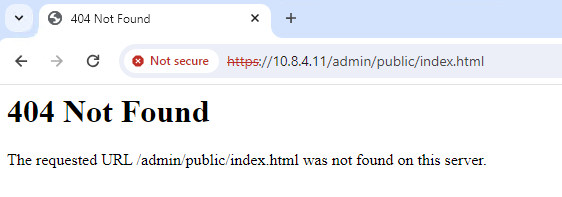 ASA HTTPS Response
ASA HTTPS Response

Tip: Error 404 Not Found is expected on this step as this ASA does not have the Cisco Adaptive Security Device Manager (ASDM) installed, but the HTTPS response is there as the page redirects to URL /admin/public/index.html.
Provision Secure Firewall ASA to CSM
Step 1. Open and Log into the CSM Client.
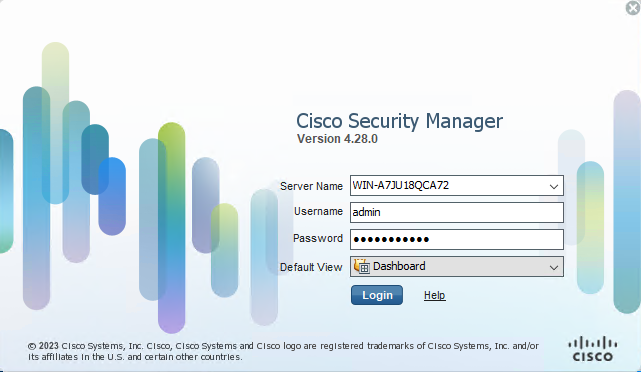 CSM Client Log In
CSM Client Log In
Step 2. Open the Configuration Manager.
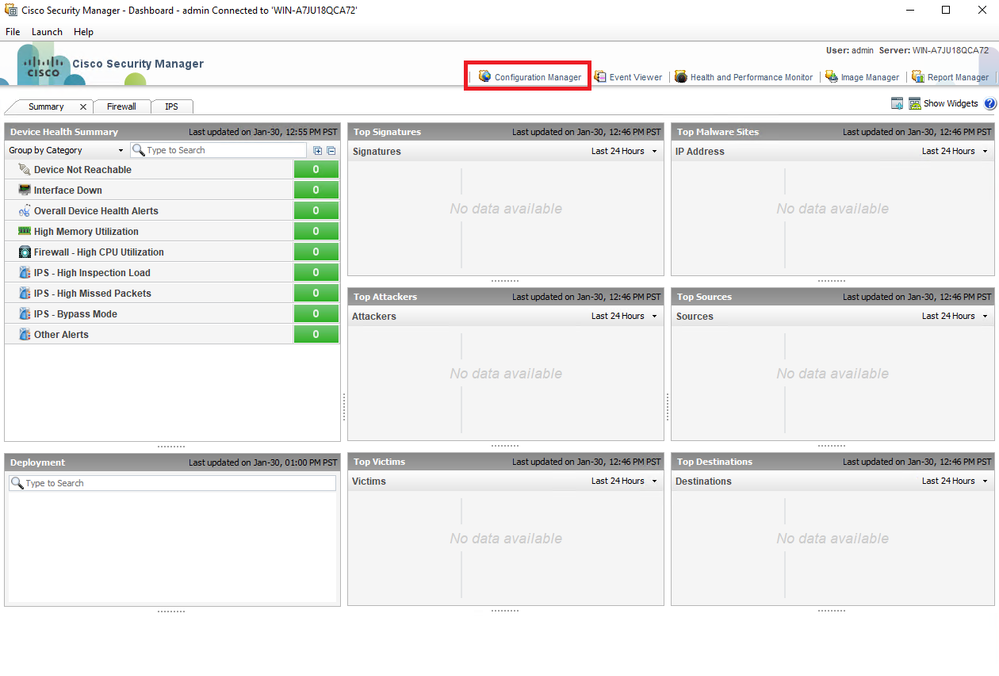 CSM Client Dashboard
CSM Client Dashboard
Step 3. Navigate to Devices > New Device.
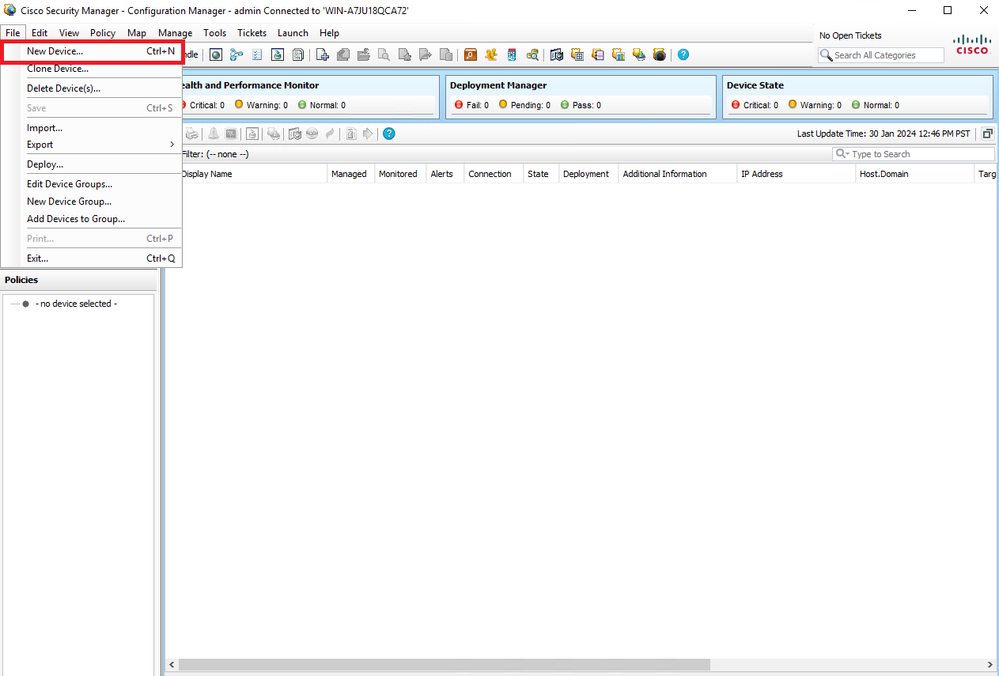 CSM Configuration Manager
CSM Configuration Manager
Step 4. Select the adding option that fills the requirement according to the desired result. As the configured ASA is already setup in the network, the best option for this example is Add Device From Network and click on Next.
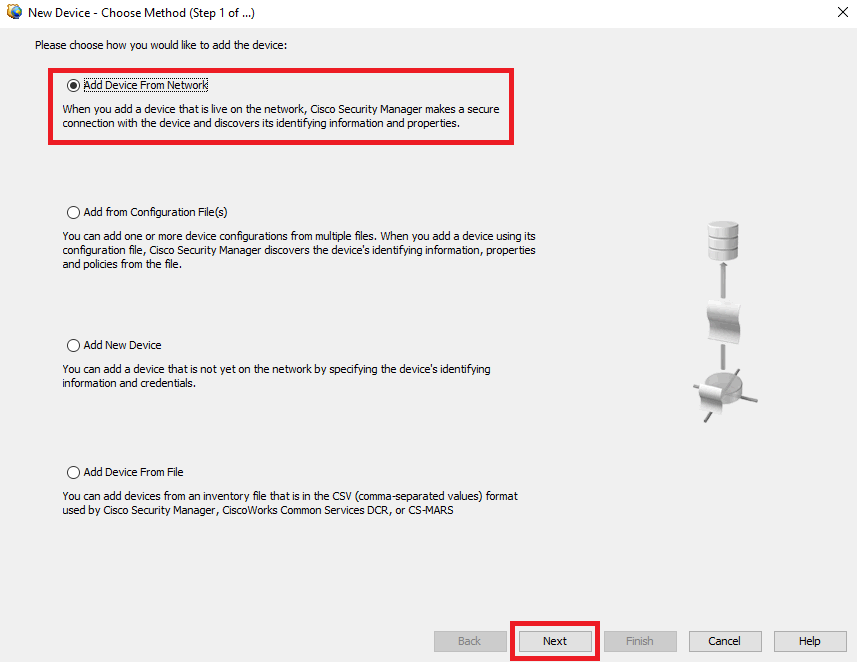 Device Add Method
Device Add Method
Step 5. Complete the required data according to the configuration on the Secure Firewall ASA, and the discovery settings. Then, click on Next.
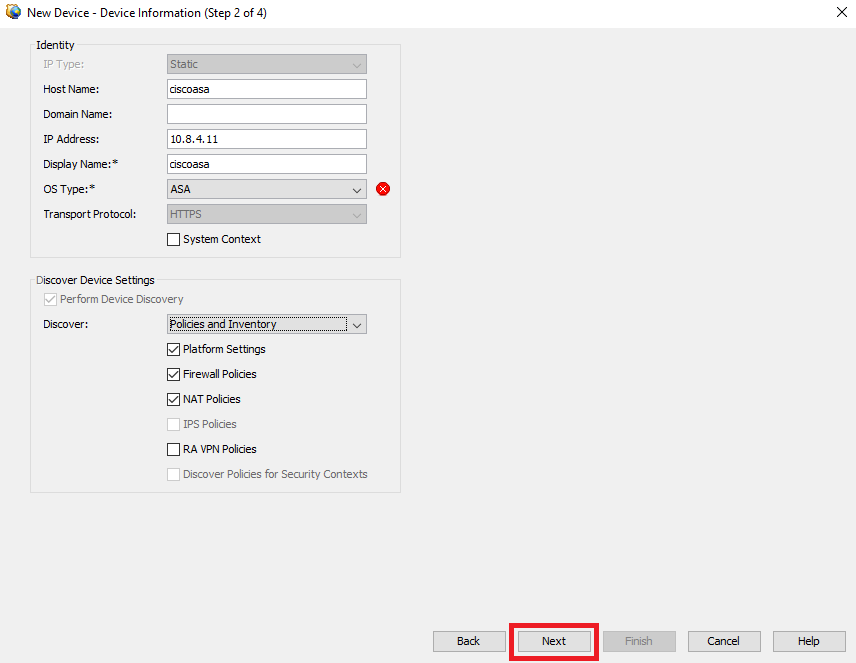 ASA Settings
ASA Settings
Step 6. Complete the required credentials from both the configured CSM user on ASA and the enable password.
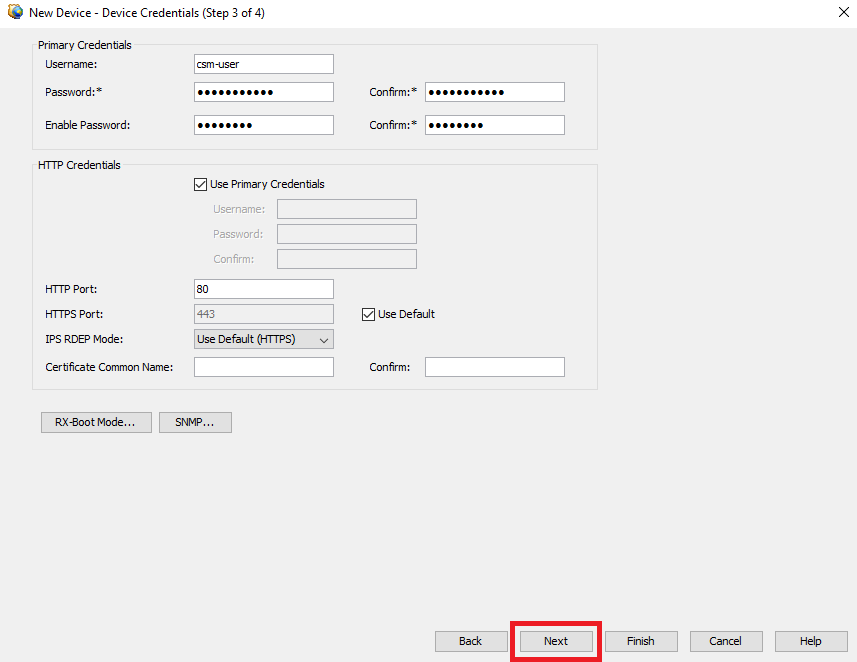 ASA Credentials
ASA Credentials
Step 7. Select the desired groups or skip this step if none is required and click on Finish.
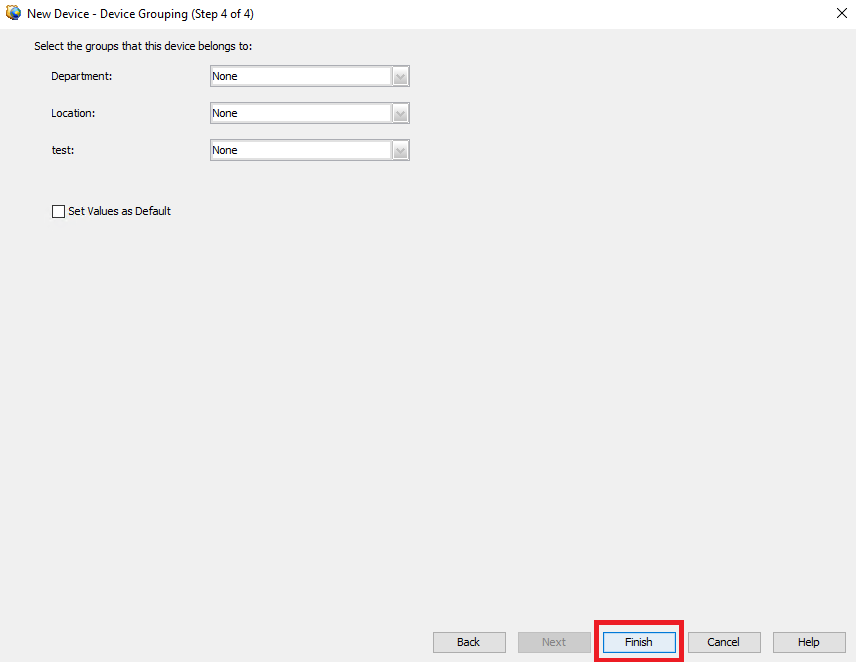 CSM Group Selection
CSM Group Selection
Step 8. A ticket request is generated for control purposes, click on OK.
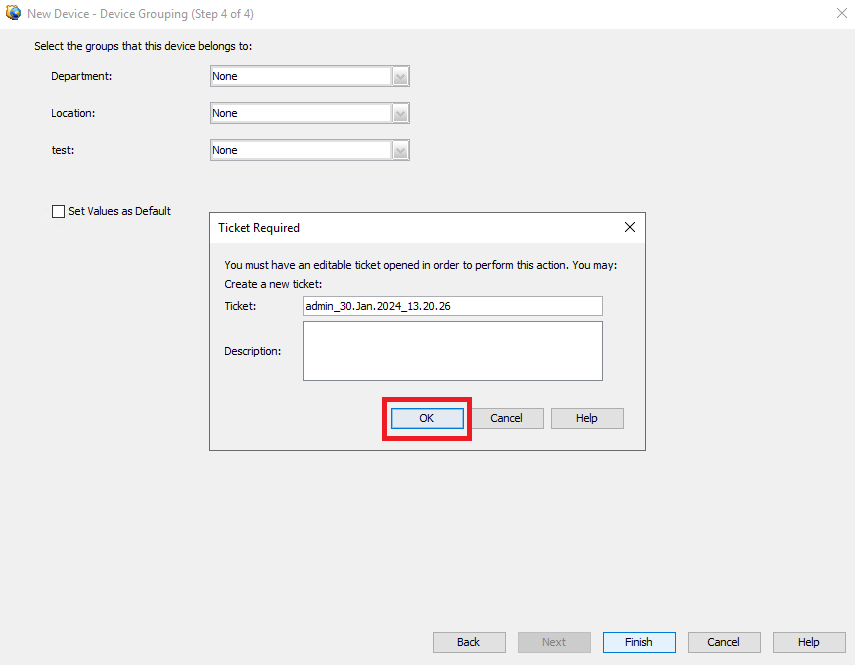 CSM Ticket Creation
CSM Ticket Creation
Step 9. Validate that discovery finishes without errors and click on Close.
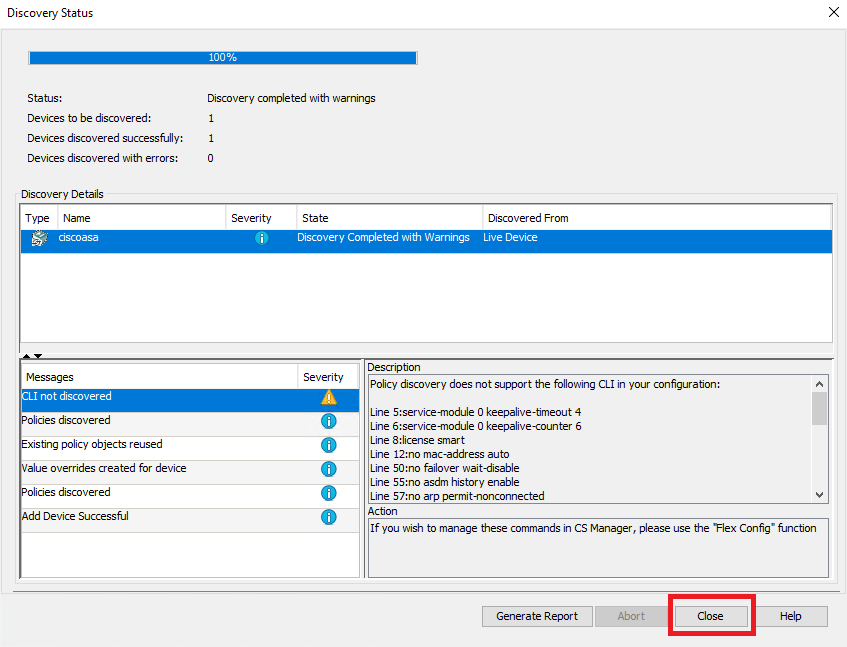 ASA Discovery
ASA Discovery

Tip: Warnings are accepted as a successful output, as not all ASA functionalities are be supported by CSM.
Step 10. Validate that the ASA now appears as registered on the CSM client and displays the correct information.
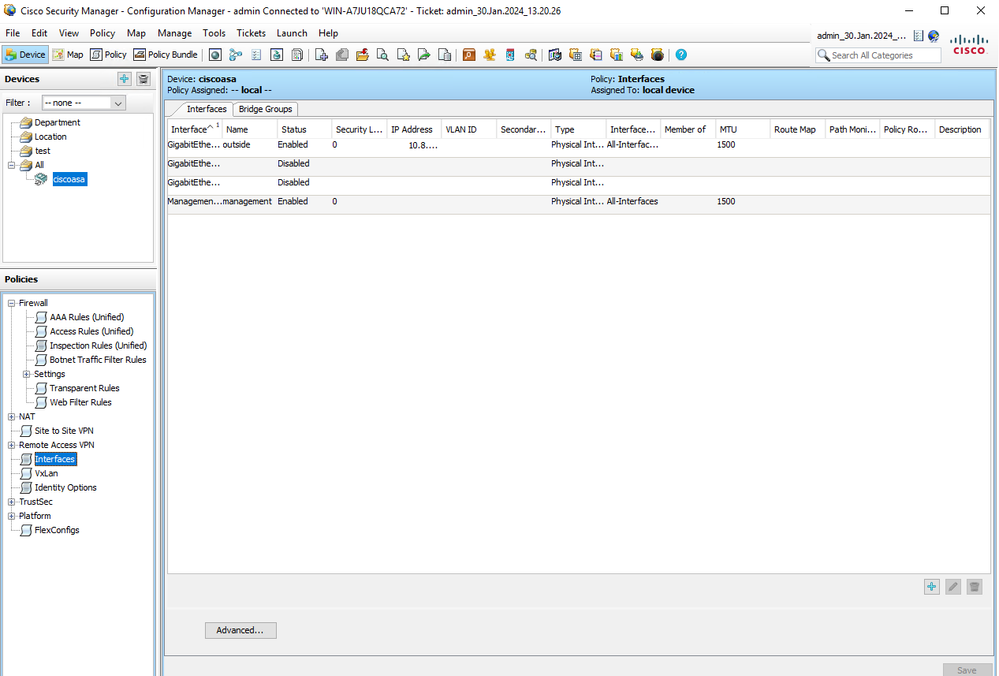 ASA Information Registered
ASA Information Registered
Verify
A HTTPS debug is available on ASA for troubleshooting purposes. The next command is used:
debug httpThis is an example of a successful CSM registration debug:
ciscoasa# debug http
debug http enabled at level 1.
ciscoasa# HTTP: processing handoff to legacy admin server [/admin/exec//show%20version]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20version HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^^u
HTTP: processing GET URL '/admin/exec//show%20version' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/config]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/config HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒e
HTTP: processing GET URL '/admin/config' from host 10.8.4.12
HTTP: Authentication username = ''
HTTP: processing handoff to legacy admin server [/admin/exec//show%20version]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20version HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^^u
HTTP: processing GET URL '/admin/exec//show%20version' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//sh%20module%20%7c%20in%20(CX%20Security%20Services%20Processor-%7ccxsc%20ASA%20CX5)]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//sh%20module%20%7c%20in%20(CX%20Security%20Services%20Processor-%7ccxsc%20ASA%20CX5) HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^2▒^aware_123▒
HTTP: processing GET URL '/admin/exec//sh%20module%20%7c%20in%20(CX%20Security%20Services%20Processor-%7ccxsc%20ASA%20CX5)' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//sh%20module%20%7c%20in%20(FirePOWER)]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//sh%20module%20%7c%20in%20(FirePOWER) HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒▒▒▒
HTTP: processing GET URL '/admin/exec//sh%20module%20%7c%20in%20(FirePOWER)' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//sh%20cluster%20info]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//sh%20cluster%20info HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^
HTTP: processing GET URL '/admin/exec//sh%20cluster%20info' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//sh%20inventory]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//sh%20inventory HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^^u
HTTP: processing GET URL '/admin/exec//sh%20inventory' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//sh%20vm]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//sh%20vm HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒
2▒^^^u
HTTP: processing GET URL '/admin/exec//sh%20vm' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/config]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/config HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒e
HTTP: processing GET URL '/admin/config' from host 10.8.4.12
HTTP: Authentication username = ''
HTTP: processing handoff to legacy admin server [/admin/exec//show%20version]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20version HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^^u
HTTP: processing GET URL '/admin/exec//show%20version' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20inventory]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20inventory HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒u
HTTP: processing GET URL '/admin/exec//show%20inventory' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20password%20encryption]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20password%20encryption HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^^
HTTP: processing GET URL '/admin/exec//show%20password%20encryption' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20running-config%20all%20tunnel-group]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20running-config%20all%20tunnel-group HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒2▒^▒^e
HTTP: processing GET URL '/admin/exec//show%20running-config%20all%20tunnel-group' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20running-config%20all%20group-policy]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20running-config%20all%20group-policy HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒2▒^▒^e
HTTP: processing GET URL '/admin/exec//show%20running-config%20all%20group-policy' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20crypto%20ca%20trustpool%20detail]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20crypto%20ca%20trustpool%20detail HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒2▒^2▒^▒^e
HTTP: processing GET URL '/admin/exec//show%20crypto%20ca%20trustpool%20detail' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20snmp-server%20engineID]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20snmp-server%20engineID HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^P_▒
HTTP: processing GET URL '/admin/exec//show%20snmp-server%20engineID' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20version]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20version HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒▒^u
HTTP: processing GET URL '/admin/exec//show%20version' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20failover]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20failover HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^u
HTTP: processing GET URL '/admin/exec//show%20failover' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//dir%20%2frecursive%20all-filesystems]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//dir%20%2frecursive%20all-filesystems HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒2▒^2▒^2▒^▒^e
HTTP: processing GET URL '/admin/exec//dir%20%2frecursive%20all-filesystems' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20asdm%20image]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20asdm%20image HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒^
2▒^^^
HTTP: processing GET URL '/admin/exec//show%20asdm%20image' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20running-config%20webvpn]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20running-config%20webvpn HTTP/1.1
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
Cache-Control: no-cache
Pragma: no-cache
Host: 10.8.4.11
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
▒▒▒P_▒
HTTP: processing GET URL '/admin/exec//show%20running-config%20webvpn' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20vpn-sessiondb%20full%20webvpn]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20vpn-sessiondb%20full%20webvpn HTTP/1.1
Host: 10.8.4.1110.8.4.11
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
▒▒▒^2▒^1
HTTP: processing GET URL '/admin/exec//show%20vpn-sessiondb%20full%20webvpn' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20vpn-sessiondb%20full%20ra-ikev1-ipsec]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20vpn-sessiondb%20full%20ra-ikev1-ipsec HTTP/1.1
Host: 10.8.4.1110.8.4.11
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
▒▒▒
HTTP: processing GET URL '/admin/exec//show%20vpn-sessiondb%20full%20ra-ikev1-ipsec' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20vpn-sessiondb%20full%20ra-ikev2-ipsec]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20vpn-sessiondb%20full%20ra-ikev2-ipsec HTTP/1.1
Host: 10.8.4.1110.8.4.11
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
▒▒▒
HTTP: processing GET URL '/admin/exec//show%20vpn-sessiondb%20full%20ra-ikev2-ipsec' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
HTTP: processing handoff to legacy admin server [/admin/exec//show%20vpn-sessiondb%20full%20anyconnect]
HTTP: admin session verified = [0]
HTTP MSG: GET /admin/exec//show%20vpn-sessiondb%20full%20anyconnect HTTP/1.1
Host: 10.8.4.1110.8.4.11
Authorization: Basic OmNpc2NvMTIz
User-Agent: CSM
▒▒▒1
HTTP: processing GET URL '/admin/exec//show%20vpn-sessiondb%20full%20anyconnect' from host 10.8.4.12
HTTP: Authentication username = ''
Exited from HTTP Cli Exec
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
12-Feb-2024 |
Initial Release |
Contributed by Cisco Engineers
- Carlos Eduardo Arteaga PortilloCisco Security Technical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback