Configure Learn-List and PfR-Map in PfRv2
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how learn lists and maps are defined and used in Performance Routing version 2 (PfRv2) in order to affect traffic flow for prefixes.
Prerequisites
Requirements
Cisco recommends that you have basic knowledge of PfR.
Components Used
This document is not restricted to specific software and hardware versions.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure
Learn-List
The learn-list feature in PfRv2 allows the router to learn and group certain traffic classes. An enterprise network is comprised of various types of traffic which includes application, voice, video and so on. Learn-list gives the flexibility to group this traffic as per network requirements. Categorize and group of traffic in learn-lists is generally achieved with an access-list that matches some specific Differentiated Services Code Point (DSCP) value, however a prefix-list can also be used to match prefixes. This is an example of learn-list that learns and groups traffic based on DSCP value "ef".
list seq 10 refname Video-Traffic
traffic-class access-list Video
throughput
!
ip access-list extended Video
permit ip any any dscp ef
A learn list can be subjected to any user defined policy. This is generally achieved with a pfr-map.
Pfr-Map
Pfr-map helps you to define a policy which comprises of a set of parameters. Traffic categorized or grouped via learn-list is then mapped to an individual sequence of a pfr-map. These are some parameters that could be defined using pfr-maps.
- Delay
- Loss
- Unreachable
- Jitter
- Mean Opinion Scores (MOS)
Note: Delay will be used as the key parameter for the rest of this document
A PfR-Map can have multiple sequence numbers like a route-map and each sequence number can reference a different learn-list.
Link-Group
Link-Groups are used to group external interfaces so the traffic could be pushed out of the exit link of the selected border router (BR). A failover link-group can also be defined to do switchover in case the primary link-group goes out of policy. For example, this configuration defines link-group in this fashion:
set link-group INET fallback MPLS
This configuration statement used in pfr-map PFR under sequence 20 defines all DATA traffic to pass through INET as long as INET is in INPOLICY state. In case of a policy breach, traffic will failover to the MPLS link.
pfr-map PFR 20
set link-group INET fallback MPLS
Network Diagram
This image provides a sample topology for the configuration examples:
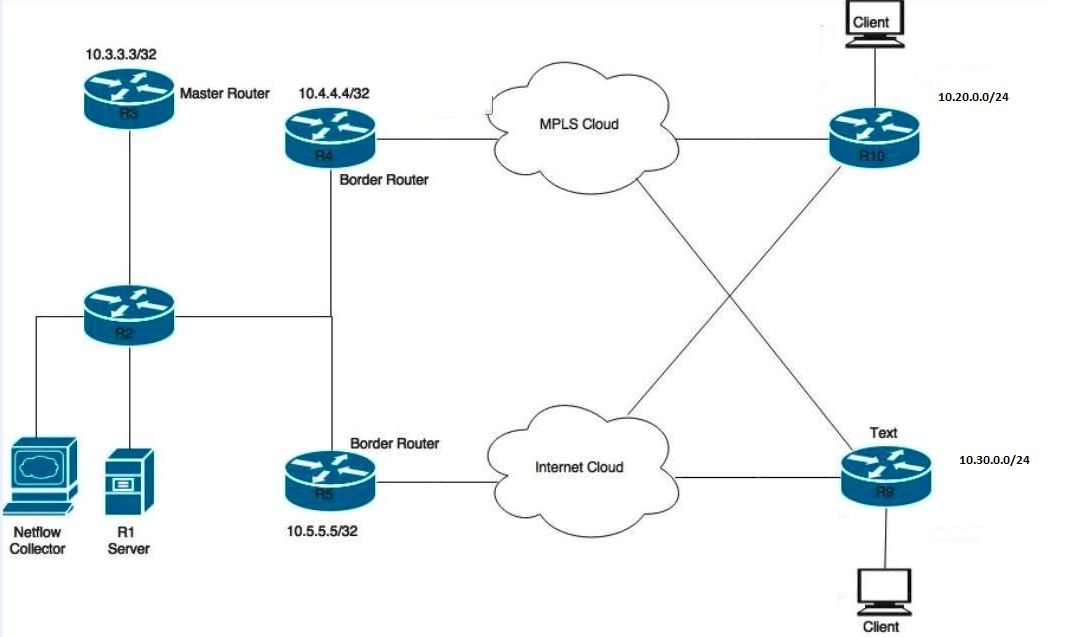
Devices shown in the diagram:
R1 Server - Initiates traffic.
R3 - PfR Master Router.
R4 & R5 - PfR Border Router.
Clients connected to R9 and R10 are devices that receive the traffic from R1 server.
Relevant Configuration
For the previous scenario two learn lists will be configured, one for application ( APPLICATION-LEARN-LIST) and the other for data (DATA-LEARN-LIST) traffic respectively. This scenario uses a prefix-list in order to define traffic. An access-list can also be used to match traffic types like TCP, UDP, Internet Control Message Protocol (ICMP) and so on. Other options like DSCP, Type of Service (ToS) and so on can also be used in order to match the traffic.
key chain pfr
key 0
key-string cisco
!
policy-rules PFR
!
border 10.4.4.4 key-chain pfr
interface Ethernet0/0 internal
interface Ethernet0/1 external
link-group MPLS
!
border 10.5.5.5 key-chain pfr
interface Ethernet0/0 internal
interface Ethernet0/1 external
link-group INET
!
learn
traffic-class filter access-list DENY-ALL
list seq 10 refname APPLICATION-LEARN-LIST
traffic-class prefix-list APPLICATION
throughput
list seq 20 refname DATA-LEARN-LIST
traffic-class prefix-list DATA
throughput
!
ip prefix-list DATA
seq 5 permit 10.30.0.0/24
!
ip prefix-list APPLICATION
seq 5 permit 10.20.0.0/24
!
pfr-map PFR 10
match pfr learn list APPLICATION-LEARN-LIST
set periodic 90
set delay threshold 25
set mode monitor active
set resolve delay priority 1 variance 10
set active-probe echo 10.20.0.12
set probe frequency 5
set link-group MPLS fallback INET
!
pfr-map PFR 20
match pfr learn list DATA-LEARN-LIST
set periodic 90
set delay threshold 25
set mode monitor both
set resolve delay priority 1 variance 10
set probe frequency 5
set link-group INET fallback MPLS
Verify
When traffic flows through the network, it matches the corresponding prefix-list and learn-list. Accordingly PfR-Map takes action on traffic as per the parameters defined for every learn-list.
Case 1: Delay on MPLS and INET Cloud is Same and Within Policy Limits
Traffic for prefix 10.20.0.0/24 (Application) is in INPOLICY state and flows via link-group MPLS. Similarly, prefix 10.30.0.0/24 (Data) is also in the INPOLICY state and flows via link-group INET.
R3#show pfr master traffic-class
OER Prefix Statistics:
Pas - Passive, Act - Active, S - Short term, L - Long term, Dly - Delay (ms),
P - Percentage below threshold, Jit - Jitter (ms),
MOS - Mean Opinion Score
Los - Packet Loss (percent/10000), Un - Unreachable (flows-per-million),
E - Egress, I - Ingress, Bw - Bandwidth (kbps), N - Not applicable
U - unknown, * - uncontrolled, + - control more specific, @ - active probe all
# - Prefix monitor mode is Special, & - Blackholed Prefix
% - Force Next-Hop, ^ - Prefix is denied
DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix
Flags State Time CurrBR CurrI/F Protocol
PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw
ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS ActSLos ActLLos
--------------------------------------------------------------------------------
10.20.0.0/24 N N N N N N
INPOLICY 50 10.4.4.4 Et0/1 BGP
N N N N N N N N
4 3 0 0 N N N N
10.30.0.0/24 N N N N N N
INPOLICY 0 10.5.5.5 Et0/1 BGP
1 2 0 0 0 0 14 1
1 1 0 0 N N N N
Case 2: Delay on MPLS and INET Cloud is Different and Crosses the Policy Limits
There is an increase in delay in the MPLS cloud of about 150 ms. This increase in delay violates the configured threshold delay value of 25 ms as per PfR-Map statementset delay threshold 25.
This causes Application traffic (10.20.0.0/24) to failover to link-group INET as per the configured statement set link-group MPLS fallback INET. After a period of time, traffic again gets into the INPOLICY state and flows over link-group INET.
Note: There is no effect seen on DATA traffic as its primary path is INET and no delay has been introduced on it.
R3#show pfr master traffic-class
OER Prefix Statistics:
Pas - Passive, Act - Active, S - Short term, L - Long term, Dly - Delay (ms),
P - Percentage below threshold, Jit - Jitter (ms),
MOS - Mean Opinion Score
Los - Packet Loss (percent/10000), Un - Unreachable (flows-per-million),
E - Egress, I - Ingress, Bw - Bandwidth (kbps), N - Not applicable
U - unknown, * - uncontrolled, + - control more specific, @ - active probe all
# - Prefix monitor mode is Special, & - Blackholed Prefix
% - Force Next-Hop, ^ - Prefix is denied
DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix
Flags State Time CurrBR CurrI/F Protocol
PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw
ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS ActSLos ActLLos
--------------------------------------------------------------------------------
10.20.0.0/24 N N N N N N
INPOLICY 72 10.5.5.5 Et0/1 BGP
N N N N N N N N
2 4 0 0 N N N N
10.30.0.0/24 N N N N N N
INPOLICY 0 10.5.5.5 Et0/1 BGP
1 1 0 0 0 0 14 1
1 1 0 0 N N N N
R3#show pfr master traffic-class performance
Traffic-class:
Destination Prefix : 10.20.0.0/24 Source Prefix : N/A
Destination Port : N/A Source Port : N/A
DSCP : N Protocol : N/A
Application Name: : N/A
General:
Control State : Controlled using BGP
Traffic-class status : INPOLICY
Current Exit : BR 10.5.5.5 interface Et0/1, Tie breaker was delay criteria
Time on current exit : 0d 0:2:40
Time remaining in current state : 31 seconds
Traffic-class type : Learned
Improper config : None
Last Out of Policy event:
Exit : BR 10.5.5.5 interface Et0/1
Reason : delay criteria
Time since Out of Policy event : 0d 0:2:52
Active Delay Performance : 1 msecs
Active Delay Threshold : 25 msecs
Average Active Performance Current Exit: (Average for last 5 minutes)
Unreachable : 0% -- Threshold: 50%
Delay : 1 msec -- Threshold: 25 msec
Last Resolver Decision:
BR Interface Status Reason Performance Threshold
--------------- ------------ ------------ ------------ ----------- ---------
10.4.4.4 Et0/1 Eliminated Delay 162 msecs 25 msecs
10.5.5.5 Et0/1 Best Exit Delay 13 msecs 25 msecs
From the output you can see up to 162 msecs of surge is seen in delay in the MPLS cloud. This causes violation of policy as threshold delay is configured to be 25 msecs.
Case 3: Delay on INET Cloud Sees Increase of 100 msec
This causes Data traffic(10.30.0.0/24) to failover to link-group MPLS as per the configured statement set link-group INET fallback MPLS. After a period of time, traffic again gets into INPOLICY state and flows over link-group MPLS.
Note: There is no effect seen on APPLICATION traffic as its primary path is MPLS and no delay has been introduced on it in this case.
R3#show pfr master traffic-class
OER Prefix Statistics:
Pas - Passive, Act - Active, S - Short term, L - Long term, Dly - Delay (ms),
P - Percentage below threshold, Jit - Jitter (ms),
MOS - Mean Opinion Score
Los - Packet Loss (percent/10000), Un - Unreachable (flows-per-million),
E - Egress, I - Ingress, Bw - Bandwidth (kbps), N - Not applicable
U - unknown, * - uncontrolled, + - control more specific, @ - active probe all
# - Prefix monitor mode is Special, & - Blackholed Prefix
% - Force Next-Hop, ^ - Prefix is denied
DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix
Flags State Time CurrBR CurrI/F Protocol
PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw
ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS ActSLos ActLLos
--------------------------------------------------------------------------------
10.20.0.0/24 N N N N N N
INPOLICY 58 10.4.4.4 Et0/1 BGP
N N N N N N N N
1 2 0 0 N N N N
10.30.0.0/24 N N N N N N
INPOLICY 0 10.4.4.4 Et0/1 BGP
1 1 0 0 0 0 14 1
2 1 0 0 N N N N
R3#show pfr master traffic-class performance
Traffic-class:
Destination Prefix : 10.30.0.0/24 Source Prefix : N/A
Destination Port : N/A Source Port : N/A
DSCP : N Protocol : N/A
Application Name: : N/A
General:
Control State : Controlled using BGP
Traffic-class status : INPOLICY
Current Exit : BR 10.4.4.4 interface Et0/1, Tie breaker was delay criteria
Time on current exit : 0d 0:2:31
Time remaining in current state : 35 seconds
Traffic-class type : Learned
Improper config : None
Last Out of Policy event:
Exit : BR 10.4.4.4 interface Et0/1
Reason : delay criteria
Time since Out of Policy event : 0d 0:2:44
Active Delay Performance : 0 msecs
Active Delay Threshold : 25 msecs
Passive Delay Performance : 9 msecs
Passive Delay Threshold : 25 msecs
Average Passive Performance Current Exit: (Average for last 5 minutes)
Unreachable : 0% -- Threshold: 50%
Delay : 9 msecs -- Threshold: 25 msecs
Loss : 0% -- Threshold: 10%
Egress BW : 4 kbps
Ingress BW : 1 kbps
Time since last update : 0d 0:0:11
Average Active Performance Current Exit: (Average for last 5 minutes)
Unreachable : 0% -- Threshold: 50%
Delay : 0 msec -- Threshold: 25 msec
Last Resolver Decision:
BR Interface Status Reason Performance Threshold
--------------- ------------ ------------ ------------ ----------- ---------
10.5.5.5 Et0/1 Eliminated Delay 96 msecs 25 msecs
10.4.4.4 Et0/1 Best Exit Delay 5 msecs 25 msecs
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Contributed by Cisco Engineers
- Amandeep SinghCisco TAC Engineer
- Hassaan AhmedCisco TAC Engineer
- Niharika GargCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback