Field Notice: FN74214 - Cisco Firepower Management Center: Root Certificate Authority Expiration May Cause Cisco Firepower Threat Defense Devices To Become Unmanaged - Software Upgrade Recommended
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Products Affected
| Affected Software Product | Affected Release | Affected Release Number | Comments |
|---|---|---|---|
| Firepower Management Center Software | 6 | 6.2.3, 6.2.3.1, 6.2.3.10, 6.2.3.11, 6.2.3.12, 6.2.3.13, 6.2.3.14, 6.2.3.15, 6.2.3.16, 6.2.3.17, 6.2.3.18, 6.2.3.2, 6.2.3.3, 6.2.3.4, 6.2.3.5, 6.2.3.6, 6.2.3.7, 6.2.3.8, 6.2.3.9, 6.4.0, 6.4.0.1, 6.4.0.10, 6.4.0.11, 6.4.0.12, 6.4.0.13, 6.4.0.14, 6.4.0.15, 6.4.0.16, 6.4.0.17, 6.4.0.18, 6.4.0.2, 6.4.0.3, 6.4.0.4, 6.4.0.5, 6.4.0.6, 6.4.0.7, 6.4.0.8, 6.4.0.9, 6.6.0, 6.6.0.1, 6.6.1, 6.6.3, 6.6.4, 6.6.5, 6.6.5.1, 6.6.5.2, 6.6.7, 6.6.7.1, 6.6.7.2 | |
| Firepower Management Center Software | 7 | 7.0.0, 7.0.0.1, 7.0.1, 7.0.1.1, 7.0.2, 7.0.2.1, 7.0.3, 7.0.4, 7.0.5, 7.0.5.1, 7.0.6, 7.0.6.1, 7.0.6.2, 7.0.6.3, 7.1.0, 7.1.0.1, 7.1.0.2, 7.1.0.3, 7.2.0, 7.2.0.1, 7.2.1, 7.2.2, 7.2.3, 7.2.3.1, 7.2.4, 7.2.4.1, 7.2.5, 7.2.5.1, 7.2.5.2, 7.2.6, 7.2.7, 7.2.8, 7.2.8.1, 7.2.9, 7.3.0, 7.3.1, 7.3.1.1, 7.3.1.2, 7.4.0, 7.4.1, 7.4.1.1, 7.4.2, 7.4.2.1, 7.6.0 |
Defect Information
| Defect ID | Headline |
| CSCwd08098 | cacert.pem on FMC expired and all the devices showing as disabled. |
Problem Description
The Cisco Firewall Management Center (FMC) internal self-signed root Certificate Authority (CA) is valid for 10 years. Once the root CA expires, Cisco Firewall Threat Defense (FTD) devices may transition to an unmanaged and degraded state. Depending on the date of the FMC build, there may be upcoming certificate expiry that requires renewal.
Background
The validity period for the Cisco FMC self-signed root CA begins on the build date of the initially installed software release and lasts for 3650 days (10 years). This CA is used to generate and sign certificates that establish a secure management tunnel (sftunnel) connection to managed Cisco FTD devices. To avoid losing the ability to manage these devices and to prevent a more complex renewal process, a new root CA must be generated and distributed to the managed Cisco FTD devices before the current one expires.
To check the expiration date of the root CA, use the following commands:
> expert
$ sudo /usr/bin/openssl x509 -noout -startdate -enddate -in /etc/sf/ca_root/cacert.pem
notBefore=Apr 15 08:55:23 2014 GMT
notAfter=Apr 13 08:55:23 2024 GMT ---> This is the root CA expiration date.
Problem Symptom
The issue will exhibit the following three symptoms:
Symptom 1: The Devices tab in the Cisco FMC console will show that the Cisco FTD device is disconnected, indicated by a "Ø" symbol.
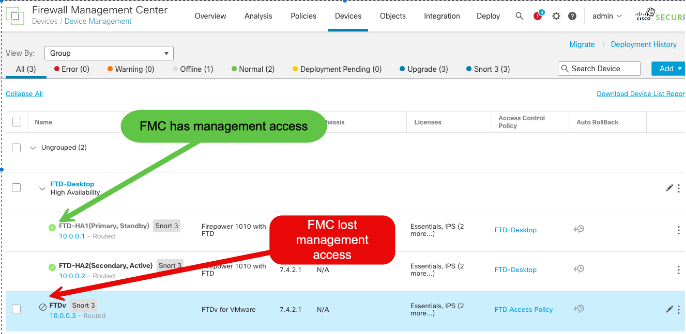
Symptom 2: Once the root CA expires, any disruption in the connection between Cisco FMC and Cisco FTD, including network issues or reboots of either device, will prevent the reconnection and result in a loss of all management capabilities. Some important functions that will stop working include, but are not limited to, the following:
- Changing the configuration of currently managed Cisco FTD devices.
- Collecting backup files from managed Cisco FTD devices.
- Registering new Cisco FTD devices with Cisco FMC.
- Analyzing traffic using Cisco FMC.
- Deploying the latest Vulnerability Database (VDB) and Secure Rule Update (SRU). This may result in a degraded security posture for future threats.
Important: While management capabilities are lost, Cisco FTD devices should continue to operate with their existing configurations.
Symptom 3: An error log similar to the following example will be present on Cisco FTD devices in the /ngfw/var/log/messages file.
> expert
$ sudo cat /ngfw/var/log/messages | grep sftunnel
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [INFO] Initiating IPv4 connection to 10.0.0.3:8305/tcp
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [INFO] Wait to connect to 8305 (IPv4): 10.0.0.3
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [INFO] Connected to 10.0.0.3 from resolved_ip_list (port 8305) (IPv4)
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [ERROR] -Error with certificate at depth: 1
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [ERROR] issuer = /title=InternalCA/OU=Intrusion Management System/CN=06f5f3ca-c77b-11e2-81bf-884d9d11f3ef/O=Sourcefire, Inc.
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [ERROR] subject = /title=InternalCA/OU=Intrusion Management System/CN=06f5f3ca-c77b-11e2-81bf-884d9d11f3ef/O=Sourcefire, Inc.
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [ERROR] err 10:certificate has expired
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [ERROR] SSL_renegotiate error: 1: error:00000001:lib(0):func(0):reason(1)
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [ERROR] Connect:SSL handshake failed
Sep 20 04:10:47 FTD SF-IMS[50792]: [51982] sftunneld:sf_ssl [WARN] SSL Verification status: certificate has expired
Workaround/Solution
This issue can be resolved without contacting Cisco TAC for these two scenarios:
- The root CA is expired or will expire soon, but Cisco FMC still has access to Cisco FTD devices. Proceed to the Solution.
- For Cisco FMC High-Availability (HA) pair configurations, the root CA on the primary Cisco FMC has expired and the root CA on the secondary Cisco FMC has not expired. Switch to the secondary Cisco FMC to maintain Cisco FTD device management and proceed to the Solution to fix the primary Cisco FMC.
Important: Do not change the Cisco FTD device manager configuration if Cisco FMC management access is lost.
Solution
Step 1: Apply the recommended hotfix to the Cisco FMC as shown in the following table. After the hotfix is applied, proceed to Steps 2 and 3 to resolve the root CA issue.
| Cisco Firepower Software Release | HotFix Release for Cisco FMC |
|---|---|
| 6.2.3 – 6.2.3.18 | Migrate to a fixed release. (End-of-Life Announcement - August 2021) |
| 6.4.0 – 6.4.0.18 | Migrate to a fixed release. (End-of-Life Announcement - August 2022) |
| 6.6.0 – 6.6.7.2 | Migrate to a fixed release. (End-of-Life Announcement - September 2021) |
| 7.0.0 – 7.0.6.3 | Apply Firepower 7.0.x Hotfix FK |
| 7.1.0 – 7.1.0.3 | Migrate to a fixed release. (End-of-Life Announcement - June 2023) |
| 7.2.0 – 7.2.9 | Apply Firepower 7.2.x Hotfix FZ |
| 7.3.0 – 7.3.1.2 | Apply Firepower 7.3.x Hotfix AE |
| 7.4.0 - 7.4.2.1 | Apply Firepower 7.4.x Hotfix AO |
| 7.6.0 |
Apply Firepower 7.6.x Hotfix B |
The hotfix links and supporting information are available in the Cisco Secure Firewall Threat Defense/Firepower Hotfix Release Notes.
Step 2: Enter expert mode in Cisco FMC and run the generate_certs.pl script to renew the root CA, as shown in the following example:
> expert
$ sudo generate_certs.pl
setting log file to /var/log/sf/sfca_generation.log
You are about to generate new certificates for FMC and devices.
After successful cert generation, device specific certs will be pushed automatically.
If the connection between FMC and a device is down,
user needs to copy the certificates onto the device manually.
For more details on disconnected devices, use sftunnel_status.pl
Do you want to continue? [yes/no]:yes
Step 3: Enter expert mode in Cisco FMC and enter the command shown in the following example to verify the new root CA expiration date:
> expert
$ sudo /usr/bin/openssl x509 -dates -noout -in /etc/sf/ca_root/cacert.pem
notBefore=Apr 15 08:55:23 2024 GMT
notAfter=Apr 13 08:55:23 2034 GMT ---> This is the renewed root CA expiration date.
The following scenarios may require contacting Cisco TAC. Before doing so, read Renewal of FMC Sftunnel CA Certificate for FTD Connectivity for additional information.
- The root CA is expired and Cisco FMC management of Cisco FTD devices is already lost.
- The root CA on the primary and secondary Cisco FMCs have expired (for Cisco FMC High-Availability (HA) pair configurations).
- Following the preceding steps in the Solution section does not fix the issue.
Additional Information
Cisco offers a guided upgrade experience through the Cisco Secure Firewall Upgrade program. This program will provide environment-specific software upgrade guidance, a customized procedure to follow, and a customized pre-upgrade checklist. For additional information and to register for the upgrade program, see Get access to Cisco Secure Firewall LevelUp.
Revision History
| Version | Description | Section | Date |
| 1.0 | Initial Release | — | 2024-NOV-18 |
For More Information
For further assistance or for more information about this field notice, contact the Cisco Technical Assistance Center (TAC) using one of the following methods:
Receive Email Notification About New Field Notices
To receive email updates about Field Notices (reliability and safety issues), Security Advisories (network security issues), and end-of-life announcements for specific Cisco products, set up a profile in My Notifications.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
This Document Applies to These Products
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback