Field Notice: FN - 70464 - ASR 900/NCS 4200 with RSP2 and ASR 920/NCS 4201/4202 Products Do Not Support Software Version Rollback from Certain Cisco IOS XE Versions - Workaround Provided
Available Languages
Notice
THIS FIELD NOTICE IS PROVIDED ON AN "AS IS" BASIS AND DOES NOT IMPLY ANY KIND OF GUARANTEE OR WARRANTY, INCLUDING THE WARRANTY OF MERCHANTABILITY. YOUR USE OF THE INFORMATION ON THE FIELD NOTICE OR MATERIALS LINKED FROM THE FIELD NOTICE IS AT YOUR OWN RISK. CISCO RESERVES THE RIGHT TO CHANGE OR UPDATE THIS FIELD NOTICE AT ANY TIME.
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
10-Dec-19 |
Initial Release |
1.01 |
20-Apr-21 |
Updated the Title, Problem Description, Background, Problem Symptom, and Workaround/Solution Sections |
Products Affected
| Affected Product ID | Comments |
|---|---|
A900-RSP2A-64 |
|
A900-RSP2A-64= |
Part Alternate |
A900-RSP2A-128 |
|
A900-RSP2A-128= |
Part Alternate |
ASR-920-10SZ-PD |
|
ASR-920-12CZ-A |
|
ASR-920-12CZ-D |
|
ASR-920-12SZ-IM |
|
ASR-920-24SZ-IM |
|
ASR-920-24SZ-M |
|
ASR-920-24TZ-M |
|
ASR-920-4SZ-A |
|
ASR-920-4SZ-D |
|
ASR-920-12SZ-A |
|
ASR-920-12SZ-D |
|
ASR-920-20SZ-M |
|
NCS4201-SA |
|
NCS4201-SA= |
Part Alternate |
NCS4202-SA |
|
NCS4202-SA= |
Part Alternate |
NCS420X-RSP-128 |
|
NCS420X-RSP-128= |
Part Alternate |
Defect Information
| Defect ID | Headline |
|---|---|
| CSCvs18851 | Router goes into a continuous boot-loop when downgraded from newer to older versions. |
Problem Description
Cisco ASR 900 Series Aggregation Services Routers (ASR 900) and Cisco Network Convergence System 4200 Series (NCS 4200) equipped with Route Switch Processor 2 (RSP2), and ASR 920/NCS 4201/NCS 4202 routers (as mentioned in the Products Affected section) do not support a software version rollback (see the Workaround/Solution section for more details) from Cisco IOS® XE Versions 17.1.1, 16.6.7, 16.9.4, 16.12.1, 3.18.7SP and later to previous versions. If a roll back is attempted by customers, the secure boot logic will detect tampering and set the router into a continuous boot loop.
Background
See the Cisco Security Advisory Secure Boot Hardware Tampering Vulnerability (CVE-2019-1649).
Cisco IOS XE Versions 17.1.1, 16.6.7, 16.9.4, 16.12.1, 3.18.7SP and later were released to address this vulnerability for the ASR 900/NCS 4200 and ASR920/NCS 4201/NCS 4202 products. After you upgrade to any version which addresses this security vulnerability, you are not allowed to roll back to a previous version where the vulnerability is exposed.
Problem Symptom
The impacted router will go into a continuous boot loop when a roll back is done from the Cisco IOS XE versions listed in the Problem Description section to previous versions. See the Workaround/Solution section for more details.
These logs will be displayed during bootup:
FPGA UPGRADE Done: System going for reboot System Bootstrap, Version 15.6(10r)S, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 2016 by cisco Systems, Inc. Compiled Ddd DD-MMM-YY HH:MM by abc Boot ROM1 Last reset cause: PowerOn UEA platform with 3670016 Kbytes of main memory
Workaround/Solution
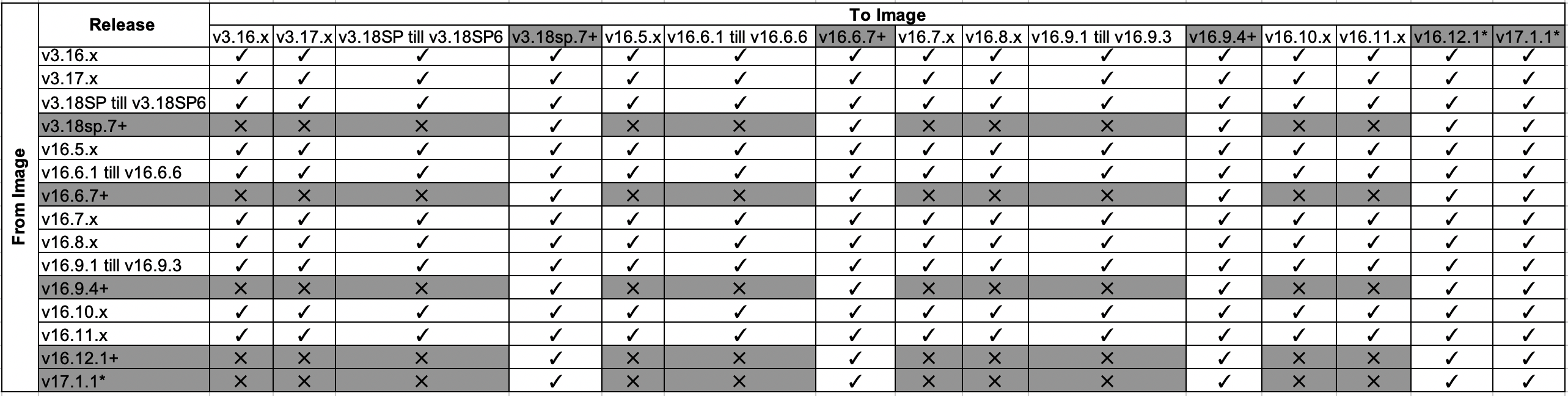
See this Software Release Migration Matrix for more details on supported/not supported migration paths.
If the router has been set with the Autoboot option with the respective Cisco IOS XE release, then the router would continuously enter the boot loop mode.
In order to stop the boot loop, the router has to be connected at the console. Press CTRL+C to stop the router at the ROM Monitor (ROMMON) prompt. Then install the latest Cisco IOS XE version image and boot the router successfully.
Note: For customers who plan to migrate to the latest Cisco IOS XE versions (as mentioned in the Problem Description section), a roll back to a previous version is not supported post upgrade.

For More Information
If you require further assistance, or if you have any further questions regarding this field notice, please contact the Cisco Systems Technical Assistance Center (TAC) by one of the following methods:
Receive Email Notification For New Field Notices
My Notifications—Set up a profile to receive email updates about reliability, safety, network security, and end-of-sale issues for the Cisco products you specify.
Unleash the Power of TAC's Virtual Assistance
 Feedback
Feedback